Tether tops crypto protocol revenue rankings in 2025 as stablecoins dominate


Fresh information from a reliable Chinese tipster suggests the OnePlus 15T may play it safe with the cameras, reusing familiar hardware while focusing on performance gains and battery capacity in a compact flagship form factor.
The post OnePlus 15T leak spills details on a curious camera situation appeared first on Digital Trends.

This week on You Asked, we tackle some of the most common TV buying questions right now, from choosing between LG and Samsung’s latest OLEDs to which brands handle upscaling best. We also dig into whether Dolby Vision 2 is a reason to hold off on a new TV purchase, or if today’s high-end sets are already good enough.
The post You Asked: OLED decisions, upscaling truths, and Dolby Vision 2 appeared first on Digital Trends.

Read more of this story at Slashdot.
Carrot Kheer is a yummy, creamy dessert made by simmering cooked carrots with flavored milk & garnished with nuts. Carrot Kheer is made on special occasions and is quite easy to make. Let us learn to make carrot Kheer Recipe with step by step pictures and video.

Carrot Kheer is our family favourite including mittu. This version of carrot kheer is loved by all ages as it is creamy and tasty. Carrot kheer made with sauteing carrots was not mittus favorite so tried this version and it is a instant hit with both the kids.
[feast_advanced_jump_to]Carrot Kheer is a rich creamy dessert that you can make for festivals or any special occasions. Kheer is payasam so payasam made with carrot as main ingredient is Carrot Kheer. Carrot Payasam as it is popularly known in South India is one of the unique kheer recipes that you can make from our usual rice kheer.
There are many ways this Carrot Kheer can be made - Some versions involve just sauteing carrots in ghee and simmering in milk. But this recipe I have shared is more creamy and will sure be kids favorite too.
Cardamom powder goes well with carrots and milk so do not skip it. If you like saffron you can add a pinch of it too. If your kids are not fond of carrot in sabzi form then try this recipe for them and I am sure they will love it and ask for more. So these days Carrot Kheer is something they look forward to.
This is a creamy and rich dessert that you can make it as a part of meals or as an after meal dessert. If you get Delhi red carrots you can use that too. Carrots are a rich source of Vitamin A which is very good for our eyes so try to include carrots in your diet on a regular basis.


1.To a pan add 1 tablespoon ghee let it melt.

2.Wash carrots, trim the edges and peel of the skin.Grate it using a grater and then measure it. Add 2 cups grated carrot and saute for few mins until it shrinks and raw smell leaves. It may take at least 5-7 minutes so keep sauteing in low flame.

3.Add ½ cup water to it.

4.Cook covered until the carrots turn soft yet retains its shape not too mushy.

5.Once all the water is absorbed and the carrots are cooked remove from pan and cool down.

6.Transfer to a bowl and add 6 whole cashews soaked in water to it.

9.Now this is ready to make into a paste.

10.Grind it to a fine paste and set aside. Add little water to grind it.

11.Boil 2 cups full fat milk. Let it come to a rolling boil.

12.Simmer for 2 minutes.

13.Add carrot cashew paste to it.

14.Mix it well first.

15.Add ¼ cup sugar to it.

16.Simmer for 5 minutes.

17.Now add ¼ teaspoon cardamom powder and chopped pistachio.

18.The consistency should be slightly runny as the kheer thickens with time.

Carrot Kheer is ready!
Enjoy Carrot Kheer as a dessert after meal hot or cold as per your preference. Refrigerate for later use, keeps well for a day in room temperature and in fridge for 2-3 days.

If you have any more questions about this Carrot Kheer Recipe do mail me at sharmispassions@gmail.com. In addition, follow me on Instagram, Facebook, Pinterest, Youtube and Twitter .
Tried this Carrot Kheer Recipe ? Do let me know how you liked it. Also tag us on Instagram @sharmispassions and hash tag it on #sharmispassions.
The post Carrot Kheer | Carrot Payasam appeared first on Sharmis Passions.
Tether emerged as the most profitable crypto entity in 2025, generating an estimated $5.2 billion in revenue as stablecoins overtook all other protocol categories in earnings.
According to the latest Coingecko annual crypto industry report, Tether alone accounted for 41.9% of all stablecoin-related revenue in 2025, outpacing competitors such as Circle, Hyperliquid, Pump.fun, Ethena, Axiom, Phantom, and PancakeSwap.
The results show that dollar-backed digital currencies have become the most durable revenue engine in crypto, even as market conditions fluctuated throughout the year.
Among more than 168 crypto protocols tracked in 2025, stablecoin issuers collectively generated the highest revenue, with Tether firmly at the center.
INSIGHT: Stablecoins generated $5.2B in revenue in 2025, accounting for 41.9% of total protocol revenue. pic.twitter.com/fjJrAn9k7B
— CoinGecko (@coingecko) January 25, 2026
Its $5.2 billion haul placed it well ahead of Circle and other major players, reinforcing USDT’s position as the industry’s primary settlement asset.
Within the top ten revenue-generating protocols, just four entities, led by Tether and Circle, produced 65.7% of total earnings, equivalent to roughly $8.3 billion.

The remaining six protocols in the top ten were all trading-focused platforms, highlighting a sharp divide between stable revenue streams and market-dependent income.
That contrast became clear as trading revenues swung widely with investor sentiment during the year.
Phantom, for example, recorded $95.2 million in revenue in January at the height of the Solana meme coin frenzy, only to see earnings fall to $8.6 million by December as speculative activity cooled.
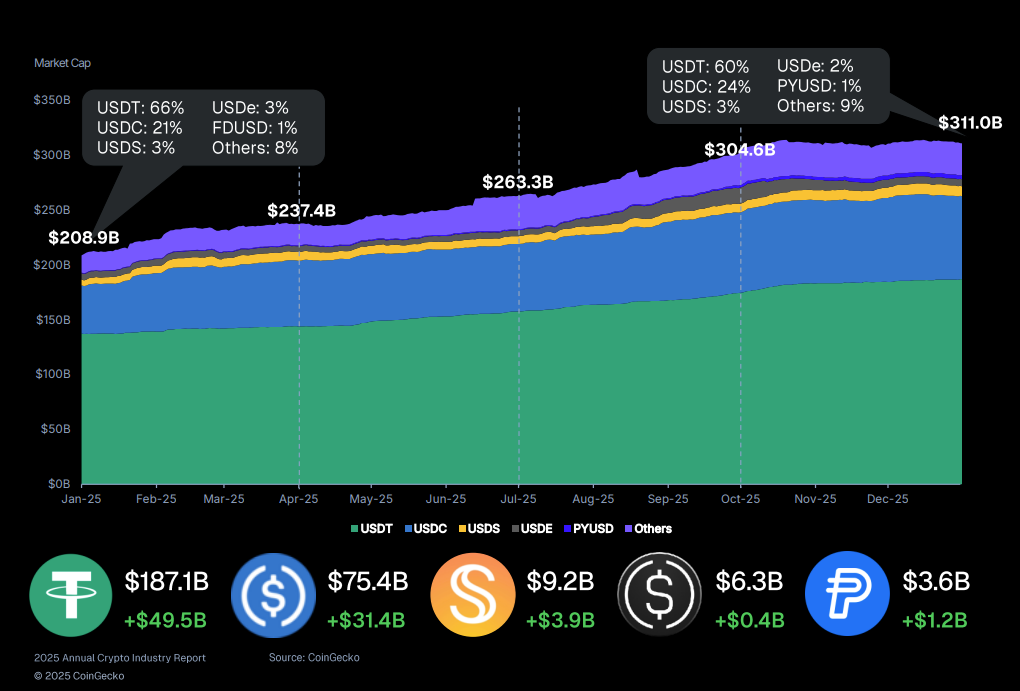
The broader stablecoin market expanded rapidly, with total market capitalization rising by $6.3 billion in the fourth quarter alone to reach a record $311.0 billion.
That marked a 48.9% year-over-year increase, adding $102.1 billion as adoption accelerated across regions.
Tether maintained clear leadership with 60.1% of the total stablecoin market cap, or about $187.0 billion, followed by Circle’s USDC at 24.2%, equivalent to $72.4 billion.
Tether is now the world’s third-largest digital asset by market value at $186.8 billion, up roughly 50% from a year earlier.
While the top players strengthened their grip, shifts within the top five reflected changing risk appetites.
Ethena’s USDe experienced the sharpest reversal, with its market cap plunging 57.3%, or $6.5 billion, after a mid-October depeg on Binance undermined confidence in high-yield looping strategies.
Other stablecoins posted mixed but notable moves as capital rotated within the sector.
PayPal’s PYUSD surged 48.4%, adding $1.2 billion to reach $3.6 billion and briefly claiming the fifth spot before World Liberty Financial’s USD1 reclaimed it by nearly $1.
Additional high-growth tokens included Ripple’s RLUSD, which expanded 61.8% to add $488.2 million, and USDD, which climbed 76.9% with a $366.8 million increase.
Looking ahead, Bitwise CIO Matt Hougan recently suggested that Tether could become the world’s most profitable company if its trajectory continues.
“There’s a chance that many emerging market countries will convert from primarily using their own currencies to using USDT,” Hougan said, pointing to Tether’s near-total dominance outside Western markets.
Based on projected interest income, calculations indicate that custody of $3 trillion in assets could generate annual revenue exceeding the $120 billion earned by Saudi Aramco last year.
Tether CEO Paolo Ardoino previously told Cryptonews he remains confident USDT will retain its lead due to the company’s deep understanding of real-world usage.
Beyond stablecoins, Tether has expanded aggressively into traditional assets and investments.
— Cryptonews.com (@cryptonews) December 13, 2025
@Tether_to has launched an all-cash bid to acquire Italy’s @juventusfcen, an offer that was reportedly swiftly turned down.#Tether #Cryptohttps://t.co/4iTBXWjo5V
The company recently became the second-largest shareholder in Italian football club Juventus and has reportedly explored raising $20 billion for a 3% stake, a deal that would imply a valuation near $500 billion and place Tether among the world’s most valuable firms.
The post Tether Posts Largest Crypto Revenue in 2025: $5.2B From Stablecoin Dominance appeared first on Cryptonews.






For certain high-security devices, such as card readers, ATMs, and hardware security modules, normal physical security isn’t enough – they need to wipe out their sensitive data if someone starts drilling through the case. Such devices, therefore, often integrate circuit meshes into their cases and regularly monitor them for changes that could indicate damage. To improve the sensitivity and accuracy of such countermeasures, [Jan Sebastian Götte] and [Björn Scheuermann] recently designed a time-domain reflectometer to monitor meshes (pre-print paper).
Many meshes are made from flexible circuit boards with winding traces built into the case, so cutting or drilling into the case breaks a trace. The problem is that most common ways to detect broken traces, such as by resistance or capacitance measurements, aren’t easy to implement with both high sensitivity and low error rates. Instead, this system uses time-domain reflectometry: it sends a sharp pulse into the mesh, then times the returning echoes to create a mesh fingerprint. When the circuit is damaged, it creates an additional echo, which is detected by classifier software. If enough subsequent measurements find a significant fingerprint change, it triggers a data wipe.
The most novel aspect of this design is its affordability. An STM32G4-series microcontroller manages the timing, pulse generation, and measurement, thanks to its two fast ADCs and a high-resolution timer with sub-200 picosecond resolution. For a pulse-shaping amplifier, [Jan] and [Björn] used the high-speed amplifiers in an HDMI redriver chip, which would normally compensate for cable and connector losses. Despite its inexpensive design, the circuit was sensitive enough to detect when oscilloscope probes contacted the trace, pick up temperature changes, and even discern the tiny variations between different copies of the same mesh.
It’s not absolutely impossible for an attacker to bypass this system, nor was it intended to be, but overcoming it would take a great deal of skill and some custom equipment, such as a non-conductive drill bit. If you’re interested in seeing such a system in the real world, check out this teardown of a payment terminal. One of the same authors also previously wrote a KiCad plugin to generate anti-tamper meshes.
Thanks to [mark999] for the tip!
Swiss banking giant UBS, with assets under management (AuM) of up to $7 trillion, is set to launch Bitcoin trading for some of its clients. This comes amid predictions that regulatory clarity and broader adoption could send the BTC price to as high as $200,000.
Bloomberg reported that UBS is planning to launch crypto trading for some of its wealth clients, starting with its private bank clients in Switzerland. The bank will reportedly begin by offering these clients the opportunity to invest in Bitcoin and Ethereum. At the same time, the crypto offering could further expand to clients in the Pacific-Asia region and the U.S.
The banking giant is currently in discussions with potential partners, and there is no clear timeline for when it could launch Bitcoin and Ethereum trading for clients. This move is said to be partly due to increased demand from wealth clients for crypto exposure. UBS also faces increased competition as other Wall Street giants are working to offer crypto trading.
Morgan Stanley, in partnership with Zerohash, announced plans to launch crypto trading in the first half of this year, starting with Bitcoin, Ethereum, and Solana. The banking giant may soon also be able to offer its crypto products, as it has filed with the SEC to launch spot BTC, ETH, and SOL ETFs.
Furthermore, JPMorgan, another of UBS’ competitors, is considering offering crypto trading to institutional clients, although this plan is still in the early stages. The bank already accepts Bitcoin and Ethereum as collateral from its clients. Last year, it also filed to offer BTC structured notes that will track the performance of the BlackRock Bitcoin ETF.
Kevin O’Leary predicted that Bitcoin could rally to between $150,000 and $200,000 this year, driven by the passage of the CLARITY Act. His prediction came just as White House Crypto Czar David Sacks said banks would fully enter crypto once the bill passes. As such, there is a possibility that BTC could reach this $200,000 psychological level in anticipation of the amount of new capital that could flow into BTC from these banks once the bill passes.
BitMine’s Chairman, Tom Lee, also predicted during a CNBC interview that Bitcoin could reach between $200,000 and $250,000 this year, partly due to growing institutional adoption by Wall Street giants. Meanwhile, Binance founder Changpeng “CZ” Zhao said that a BTC rally to $200,000 is the “most obvious thing in the world” to him.
At the time of writing, the Bitcoin price is trading at around $89,600, up in the last 24 hours, according to data from CoinMarketCap.

We live in a golden age for MIDI controllers. [rheslip]’s contribution to the milieu is a twisty take on the format, in that it’s covered in an array of knobs. Thus the name—Twisty 2.
The controller can be built using the Raspberry Pi Pico or Pico 2. It’s set up to read a 4×4 array of clickable encoders, plus two bonus control knobs to make 18 in total, which are read via a 74HC4067 analog mux chip. There’s also an SK6812 RGB LED for each encoder, and an OLED display for showing status information. MIDI output is via USB, or, if you purchased the W variant of the Pi Pico/Pico 2, it can operate wirelessly over Bluetooth MIDI instead. The controller is set up to send MIDI CC messages, program changes, or note on/off messages depending on its configuration. Flipping through different modes is handled with the bottom set of encoders and the OLED display.
Few musicians we’ve ever met have told us they learned how to play the encoders, and yet. The cool thing about building your own MIDI controller is you can tune it to suit whatever method of performance strikes your fancy. If the name of this build alone has you inspired, you could always whip up a MIDI controller out of a Twister mat.
The XRP Ledger has entered a new phase of innovation as Ripple integrates to bring together two of the most powerful technology trends shaping the global economy. Long known for its speed, low transaction costs, and enterprise-grade reliability, the Ledger is now expanding beyond payments to data-driven and automated financial applications. By merging AI with decentralized settlement, Ripple is positioning the Ledger to support smarter workflows and more efficient liquidity management.
An analyst known as SMQKE on X has shared a case study of an AI implementation in the cross-border payment, in which Ripple has successfully combined blockchain technology and artificial intelligence to enhance the efficiency, speed, and cost-effectiveness of global transactions. As a leading provider of real-time cross-border payment solutions, Ripple leverages the XRP Ledger, a decentralized blockchain that enables real-time cross-border settlement.
Related Reading: Surge In XRP Transactions: 1.45 Million Daily Users Could Signal Price Rally Ahead, Says Expert
What sets this integration apart is the use of AI to optimize transaction flows and routing decisions in real time. Ripple AI-powered systems continuously process large volumes of payment data in real time, allowing financial institutions to make dynamic decisions on the most effective payment paths.
BlackRock is now using Ripple’s RLUSD as collateral, which is extremely bullish for XRP. JackTheRippler revealed that the altcoin is being positioned as the future infrastructure, which is being built with the potential to hit over $10,000 per coin. With the REAL token launching on January 26th, trillions in global capital could flood into the XRP Ledger. According to JackTheRippler, some projections suggest up to $800 billion could flow into the REAL token on XRP Ledger, potentially sparking a powerful supply shock.
The rise of the phoenix XRP is here. Crypto analyst Xfinancebull highlighted that Caroline Pham isn’t just another name in crypto. Pham played a role in pushing utility regulation into the Commodity Futures Trading Commission (CFTC), helping shift policy toward real-world use cases. Currently, she is at MoonPlay and posting about the phoenix on X.
Related Reading: How Donald Trump’s Latest Crypto Move Will Boost Demand For XRP
Years ago, Brad Garlinghouse drew that same phoenix, and it became one of the biggest pieces of XRP lore. While the market chased narratives, Ripple has been building institutional-grade crypto products for years. Meanwhile, the token, RLUSD, and the XRP Ledger are now live operating, and recognized among the most compliant blockchain assets in the crypto world.
This is the same asset that survived the SEC’s biggest regulatory battles in crypto history, and is now on the other side with legal clarity, growing integration, and increasing relevance to government infrastructure in its favor. Xfinancebull concluded that Caroline has helped clear the regulatory path, Brad and Ripple built what actually runs on that path, and they have been aligning all along, which is how the real adoption happens.

Read more of this story at Slashdot.
A recent statement from an XRP Ledger (XRPL) developer suggests that XRP could be the key to an early retirement shortcut. Unlike steady paychecks or slow-growing investments in traditional assets, cryptocurrencies have the ability to create generational wealth rapidly, due to their penchant for sudden and explosive price moves. Among the thousands of digital assets on the market, the developer highlighted the token as his primary choice for investors seeking substantial returns, even sharing strategies for how the coin can help them retire in a few years.
A DropCoin XRPL developer, identified as ‘Bird’ on X, announced on Thursday, January 22, that buying and holding XRP at current prices could help investors retire within a few years. The bold claim quickly caught the attention of many in the crypto community, with some asking the developers to elaborate on the strategies involved and the expected timeline for achieving such wealth.
Related Reading: XRP Price Obliteration Is Not A Matter Of If, New All-Time Highs Are Coming
Not stopping there, Bird claimed that investing in the token could eliminate the need for a job, suggesting that long-term investors may eventually rely on the potential profits from their holdings as a primary source of income. His statements were in response to a post by Watcher.Guru, which the developer directly referenced to support his optimistic long-term outlook.
In that post, Watcher Guru quoted a statement reportedly made by Binance’s founder ChangPeng Zhao, who also agreed that holding crypto assets over time could make jobs unnecessary and allow investors to retire sooner than planned. The Ledger developer shared a screenshot of Zhao making similar remarks about Artificial Intelligence, suggesting that the Binance founder views both crypto and AI as powerful tools for achieving long-term financial freedom.
A crypto community member who responded to Bird’s post questioned how long an investor has to hold XRP before retiring early. The developer answered humorously that it could be held indefinitely, adding that some investors could reach early retirement this year, while others may need a few more years. He emphasized that the timeline ultimately depends on how many tokens an investor holds.
Addressing questions from the crypto community members, Bird shared his outlook on how high he believes XRP’s price could rise, helping investors achieve early retirement. He predicted that within the next few years, the cryptocurrency could rise to $100 and beyond—a significant jump from its current market price of around $1.90.
Related Reading: How Donald Trump’s Latest Crypto Move Will Boost Demand For XRP
The Ledger developer suggested that reaching $100 could be a gradual process for the altcoin, forecasting an initial rally to $10 in the First Quarter (Q1) of 2026. Notably, Bird’s remarks reflect a classic buy-the-dip and hold strategy, where investors accumulate during downtrends and patiently wait for the price to rally explosively before taking profits.

Researchers on Friday said that Poland’s electric grid was targeted by wiper malware, likely unleashed by Russia state hackers, in an attempt to disrupt electricity delivery operations.
A cyberattack, Reuters reported, occurred during the last week of December. The news organization said it was aimed at disrupting communications between renewable installations and the power distribution operators but failed for reasons not explained.
On Friday, security firm ESET said the malware responsible was a wiper, a type of malware that permanently erases code and data stored on servers with the goal of destroying operations completely. After studying the tactics, techniques, and procedures (TTPs) used in the attack, company researchers said the wiper was likely the work of a Russian government hacker group tracked under the name Sandworm.


© Getty Images
Crypto analyst CryptoBull has highlighted targets that XRP could reach as it eyes double digits. The analyst is confident the altcoin could reach these targets, noting that current price action is mirroring the previous bull run.
In an X post, Crypto Bull stated that the next impulse will take XRP to $11 and that the last wave will take the altcoin to $70. This came as he noted that the price pattern is mirroring the previous bull run, with the only difference being time, which he claimed makes sense, as the altcoin needs longer accumulation to reach higher prices.
The analyst also indicated that it could take a year of accumulation for XRP to reach the $11 price target, meaning the last wave to $70 could take much longer. This prediction comes despite the current decline in the crypto market, with XRP trading below the psychological $2 price level.
Despite the current bearish sentiment, crypto analyst CW has also declared that the XRP rally is about to begin and that the road to $21.5 is just the beginning. He noted that this is the Phase 4 peak while the first goal is for the altcoin to break its current all-time high (ATH).
His accompanying chart showed that XRP could reach this $21 target by year-end. Meanwhile, there is the possibility of the altcoin rallying above $100 in the next Phase 1, which could happen next year. Crypto Pundit X Finance Bull recently highlighted the CLARITY Act and Trump’s tariffs as factors that could boost XRP’s demand and lead to higher prices for the altcoin.
He expects the CLARITY Act to boost XRP’s demand, especially with Trump’s Crypto Czar predicting that more banks will enter into crypto once the bill passes. X Finance Bull predicts that XRP will be the token of choice for these banks based on his belief that Ripple will provide the rails to onboard them.
Crypto analyst XForce revealed in an X post that XRP is breaking out of the largest 6+ year triangle in history, yet people are calling it a fakeout. He added that he is not a permabull or permanbear on the altcoin but that he follows trends and plays macro breakout patterns. His accompanying chart indicated that XRP was on the verge of a move to the upside, with a potential rally above $11.50.
On the lower timeframe, crypto analyst Chart Nerd stated that XRP is currently breaking out of a two-week falling wedge structure. He noted that this is a bullish reversal pattern that could send the altcoin back to $2.40 in the short term, as this is where the wedge formed. He highlighted a key resistance between $2.13 and $2.20, which the altcoin will need to break above to confirm a reversal.
At the time of writing, the XRP price is trading at around $1.92, up in the last 24 hours, according to data from CoinMarketCap.
