U.S. Bitcoin Custody Concerns Rise After Alleged Insider Stole $40 Million In Digital Assets
Bitcoin Magazine

U.S. Bitcoin Custody Concerns Rise After Alleged Insider Stole $40 Million In Digital Assets
All of the bitcoin held by the U.S. government has come under scrutiny after allegations surfaced that tens of millions of dollars in seized crypto were stolen through insider access at a federal custody contractor.
Blockchain investigator ZachXBT alleged over the weekend that more than $40 million in digital assets was siphoned from wallets linked to the U.S. Marshals Service (USMS), reportedly by the son of an executive at a firm contracted to manage seized crypto.
The alleged theft centers on Command Services & Support (CMDSS), a Virginia-based technology firm awarded a USMS contract in October 2024 to manage and dispose of certain categories of seized digital assets.
Those assets include crypto not supported by major exchanges and tied to high-profile criminal cases, including funds seized from the 2016 Bitfinex hack.
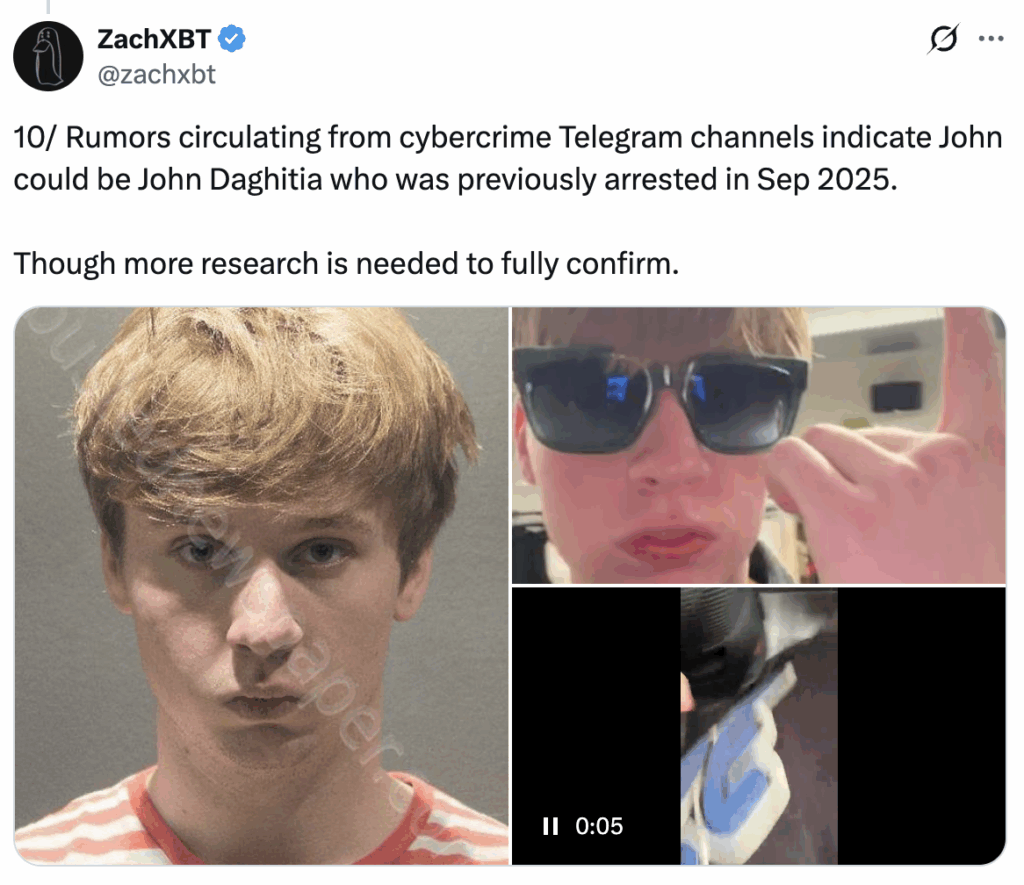
According to ZachXBT, an individual identified online as “Lick,” whom he claims is John Daghita, gained access to government-controlled wallets through insider channels. ZachXBT has further alleged that Daghita is the son of Dean Daghita, CMDSS’s president and chief executive.
The investigation began after a recorded dispute in a private Telegram chat surfaced online. During the exchange, the individual screen-shared a wallet showing millions of dollars in crypto and appeared to move funds in real time.
On-chain analysis later linked those wallets to addresses known to hold government-seized assets.
A conflict of interest involving U.S. bitcoin
One transaction trail cited by ZachXBT points to a government address that received roughly $24.9 million in bitcoin tied to Bitfinex-related seizures earlier in 2024.
Additional blockchain data suggests that around $20 million was removed from USMS-linked wallets in October 2024. Most of those funds were returned within a day, though about $700,000 routed through instant exchanges was not recovered.
ZachXBT estimates that total suspected thefts could exceed $90 million when accounting for other wallet activity observed in late 2025. Some of the funds remain in compromised wallets, raising concerns that further losses could occur.
Neither the U.S. Marshals Service nor CMDSS has issued a public statement addressing the allegations.
Rightfully so, the investigation has renewed criticism on how the U.S. government manages its growing stockpile of seized crypto — especially its bitcoin.
David Bailey, CEO of bitcoin-focused firm Nakamoto, posted on X after the report, “The son of the CEO of the company hired by the US Marshalls to safeguard the nation’s Bitcoin, stole $40m from it and now appears to be running. Treasury must secure the private keys from the Justice Department ASAP before more is stolen.”
The U.S. government holds a massive amount of Bitcoin seized through law enforcement actions, with some blockchain analytics estimating roughly 198,000 BTC under federal control with others projecting more than 300,000 BTC, worth tens of billions of dollars.
If insiders can allegedly move millions from custodial wallets with minimal detection, it suggests current custody practices may leave portions of the government’s Bitcoin reserves exposed.
Previous reports have found that the Marshals Service relied on manual tracking systems and struggled to provide precise estimates of its crypto holdings. CMDSS’s contract award also faced a protest in 2024 from a competing firm, which raised concerns about licensing and potential conflicts of interest.
JUST IN: David Bailey says, “The son of the CEO of the company hired by the US Marshalls to safeguard the nation’s Bitcoin, stole $40m from it”
— Bitcoin Magazine (@BitcoinMagazine) January 26, 2026
“Treasury must secure the private keys from the Justice Department ASAP”pic.twitter.com/6UroPNzqJY
Did the United States sell bitcoin destined for the Strategic Bitcoin Reserve?
Earlier this year, journalist Frank Corva published an investigation exploring the fact that prosecutors in the Southern District of New York and the U.S. Marshals Service may have sold bitcoin forfeited in the Samourai Wallet case, potentially in violation of President Trump’s Executive Order 14233, which dictates seized bitcoin be held in the U.S. Strategic Bitcoin Reserve rather than liquidated.
There was on-chain evidence showing 57.55 BTC tied to the Samourai plea agreement moving through a Coinbase Prime address and later showing a zero balance, raising questions about whether the assets were improperly disposed of.
Shortly afterward, U.S. officials denied that any sale took place, affirming that the Samourai Wallet bitcoin will remain on the government’s balance sheet as part of the Strategic Bitcoin Reserve under the executive order.
U.S. officials failed to show blockchain evidence but the reports and overall sentiment relay controversy over how the U.S. handles seized bitcoin. The allegations from ZachXBT further push this sentiment.
This post U.S. Bitcoin Custody Concerns Rise After Alleged Insider Stole $40 Million In Digital Assets first appeared on Bitcoin Magazine and is written by Micah Zimmerman.