Reading view
RondoDox Botnet Exploiting React2Shell Vulnerability
In December, the botnet’s operators focused on weaponizing the flaw to compromise vulnerable Next.js servers.
The post RondoDox Botnet Exploiting React2Shell Vulnerability appeared first on SecurityWeek.
GitHub Scanner for React2Shell (CVE-2025-55182) Turns Out to Be Malware
Google Sees 5 Chinese Groups Exploiting React2Shell for Malware Delivery
Google has also mentioned seeing React2Shell attacks conducted by Iranian threat actors.
The post Google Sees 5 Chinese Groups Exploiting React2Shell for Malware Delivery appeared first on SecurityWeek.
Critical React2Shell Vulnerability (CVE-2025-55182) Analysis: Surge in Attacks Targeting RSC-Enabled Services Worldwide
It didn’t take long: CVE-2025-55182 is now under active exploitation

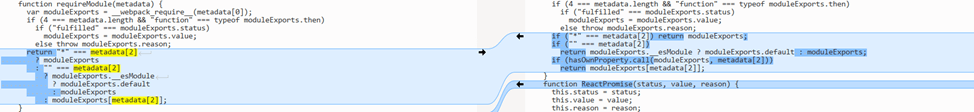
On December 4, 2025, researchers published details on the critical vulnerability CVE-2025-55182, which received a CVSS score of 10.0. It has been unofficially dubbed React2Shell, as it affects React Server Components (RSC) functionality used in web applications built with the React library. RSC speeds up UI rendering by distributing tasks between the client and the server. The flaw is categorized as CWE-502 (Deserialization of Untrusted Data). It allows an attacker to execute commands, as well as read and write files in directories accessible to the web application, with the server process privileges.
Almost immediately after the exploit was published, our honeypots began registering attempts to leverage CVE-2025-55182. This post analyzes the attack patterns, the malware that threat actors are attempting to deliver to vulnerable devices, and shares recommendations for risk mitigation.
A brief technical analysis of the vulnerability
React applications are built on a component-based model. This means each part of the application or framework should operate independently and offer other components clear, simple methods for interaction. While this approach allows for flexible development and feature addition, it can require users to download large amounts of data, leading to inconsistent performance across devices. This is the challenge React Server Components were designed to address.
The vulnerability was found within the Server Actions component of RSC. To reach the vulnerable function, the attacker just needs to send a POST request to the server containing a serialized data payload for execution. Part of the functionality of the handler that allows for unsafe deserialization is illustrated below:
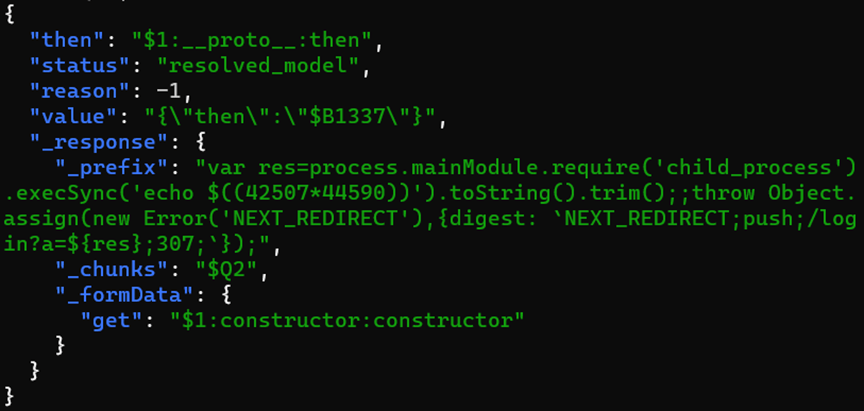
CVE-2025-55182 on Kaspersky honeypots
As the vulnerability is rather simple to exploit, the attackers quickly added it to their arsenal. The initial exploitation attempts were registered by Kaspersky honeypots on December 5. By Monday, December 8, the number of attempts had increased significantly and continues to rise.
The number of CVE-2025-55182 attacks targeting Kaspersky honeypots, by day (download)
Attackers first probe their target to ensure it is not a honeypot: they run whoami, perform multiplication in bash, or compute MD5 or Base64 hashes of random strings to verify their code can execute on the targeted machine.
In most cases, they then attempt to download malicious files using command-line web clients like wget or curl. Additionally, some attackers deliver a PowerShell-based Windows payload that installs XMRig, a popular Monero crypto miner.
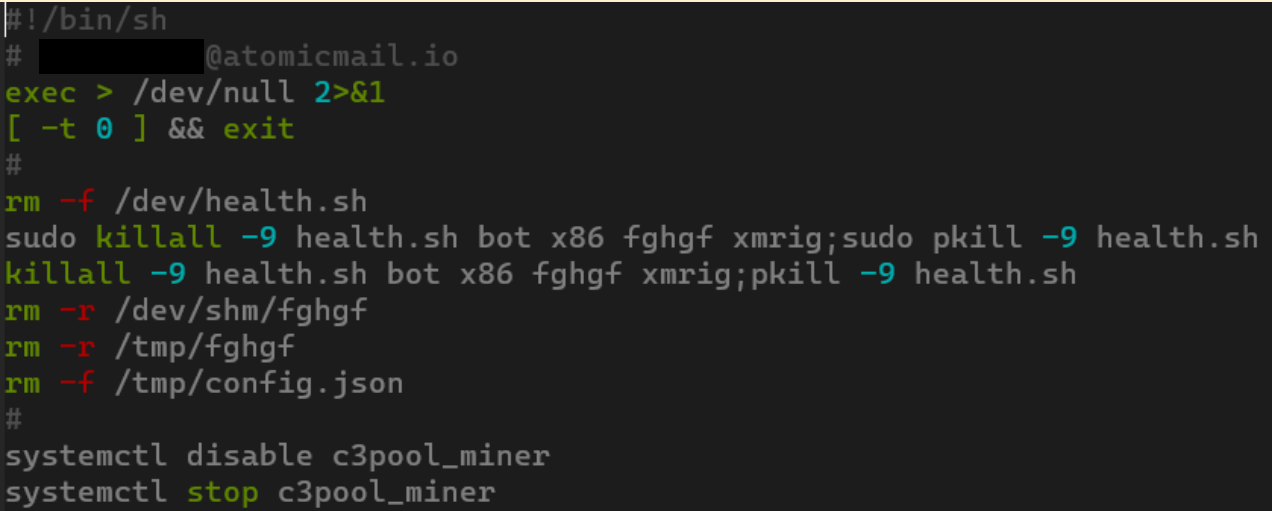
CVE-2025-55182 was quickly weaponized by numerous malware campaigns, ranging from classic Mirai/Gafgyt variants to crypto miners and the RondoDox botnet. Upon infecting a system, RondoDox wastes no time, its loader script immediately moving to eliminate competitors:
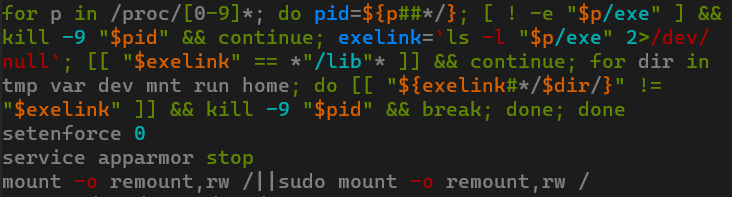
Beyond checking hardcoded paths, RondoDox also neutralizes AppArmor and SELinux security modules and employs more sophisticated methods to find and terminate processes with ELF files removed for disguise.
Only after completing these steps does the script download and execute the main payload by sequentially trying three different loaders: wget, curl, and wget from BusyBox. It also iterates through 18 different malware builds for various CPU architectures, enabling it to infect both IoT devices and standard x86_64 Linux servers.
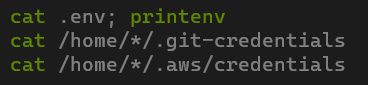
In some attacks, instead of deploying malware, the adversary attempted to steal credentials for Git and cloud environments. A successful breach could lead to cloud infrastructure compromise, software supply chain attacks, and other severe consequences.
Risk mitigation measures
We strongly recommend updating the relevant packages by applying patches released by the developers of the corresponding modules and bundles.
Vulnerable versions of React Server Components:
- react-server-dom-webpack (19.0.0, 19.1.0, 19.1.1, 19.2.0)
- react-server-dom-parcel (19.0.0, 19.1.0, 19.1.1, 19.2.0)
- react-server-dom-turbopack (19.0.0, 19.1.0, 19.1.1, 19.2.0)
Bundles and modules confirmed as using React Server Components:
- next
- react-router
- waku
- @parcel/rsc
- @vitejs/plugin-rsc
- rwsdk
To prevent exploitation while patches are being deployed, consider blocking all POST requests containing the following keywords in parameters or the request body:
- #constructor
- #__proto__
- #prototype
- vm#runInThisContext
- vm#runInNewContext
- child_process#execSync
- child_process#execFileSync
- child_process#spawnSync
- module#_load
- module#createRequire
- fs#readFileSync
- fs#writeFileSync
- s#appendFileSync
Conclusion
Due to the ease of exploitation and the public availability of a working PoC, threat actors have rapidly adopted CVE-2025-55182. It is highly likely that attacks will continue to grow in the near term.
We recommend immediately updating React to the latest patched version, scanning vulnerable hosts for signs of malware, and changing any credentials stored on them.
Indicators of compromise
Malware URLs
hxxp://172.237.55.180/b
hxxp://172.237.55.180/c
hxxp://176.117.107.154/bot
hxxp://193.34.213.150/nuts/bolts
hxxp://193.34.213.150/nuts/x86
hxxp://23.132.164.54/bot
hxxp://31.56.27.76/n2/x86
hxxp://31.56.27.97/scripts/4thepool_miner[.]sh
hxxp://41.231.37.153/rondo[.]aqu[.]sh
hxxp://41.231.37.153/rondo[.]arc700
hxxp://41.231.37.153/rondo[.]armeb
hxxp://41.231.37.153/rondo[.]armebhf
hxxp://41.231.37.153/rondo[.]armv4l
hxxp://41.231.37.153/rondo[.]armv5l
hxxp://41.231.37.153/rondo[.]armv6l
hxxp://41.231.37.153/rondo[.]armv7l
hxxp://41.231.37.153/rondo[.]i486
hxxp://41.231.37.153/rondo[.]i586
hxxp://41.231.37.153/rondo[.]i686
hxxp://41.231.37.153/rondo[.]m68k
hxxp://41.231.37.153/rondo[.]mips
hxxp://41.231.37.153/rondo[.]mipsel
hxxp://41.231.37.153/rondo[.]powerpc
hxxp://41.231.37.153/rondo[.]powerpc-440fp
hxxp://41.231.37.153/rondo[.]sh4
hxxp://41.231.37.153/rondo[.]sparc
hxxp://41.231.37.153/rondo[.]x86_64
hxxp://51.81.104.115/nuts/bolts
hxxp://51.81.104.115/nuts/x86
hxxp://51.91.77.94:13339/termite/51.91.77.94:13337
hxxp://59.7.217.245:7070/app2
hxxp://59.7.217.245:7070/c[.]sh
hxxp://68.142.129.4:8277/download/c[.]sh
hxxp://89.144.31.18/nuts/bolts
hxxp://89.144.31.18/nuts/x86
hxxp://gfxnick.emerald.usbx[.]me/bot
hxxp://meomeoli.mooo[.]com:8820/CLoadPXP/lix.exe?pass=PXPa9682775lckbitXPRopGIXPIL
hxxps://api.hellknight[.]xyz/js
hxxps://gist.githubusercontent[.]com/demonic-agents/39e943f4de855e2aef12f34324cbf150/raw/e767e1cef1c35738689ba4df9c6f7f29a6afba1a/setup_c3pool_miner[.]sh
MD5 hashes
0450fe19cfb91660e9874c0ce7a121e0
3ba4d5e0cf0557f03ee5a97a2de56511
622f904bb82c8118da2966a957526a2b
791f123b3aaff1b92873bd4b7a969387
c6381ebf8f0349b8d47c5e623bbcef6b
e82057e481a2d07b177d9d94463a7441




North Korean Hackers Deploy EtherRAT Malware in React2Shell Exploits
From React to Remote Code – Protecting Against the Critical React2Shell RCE Exposure
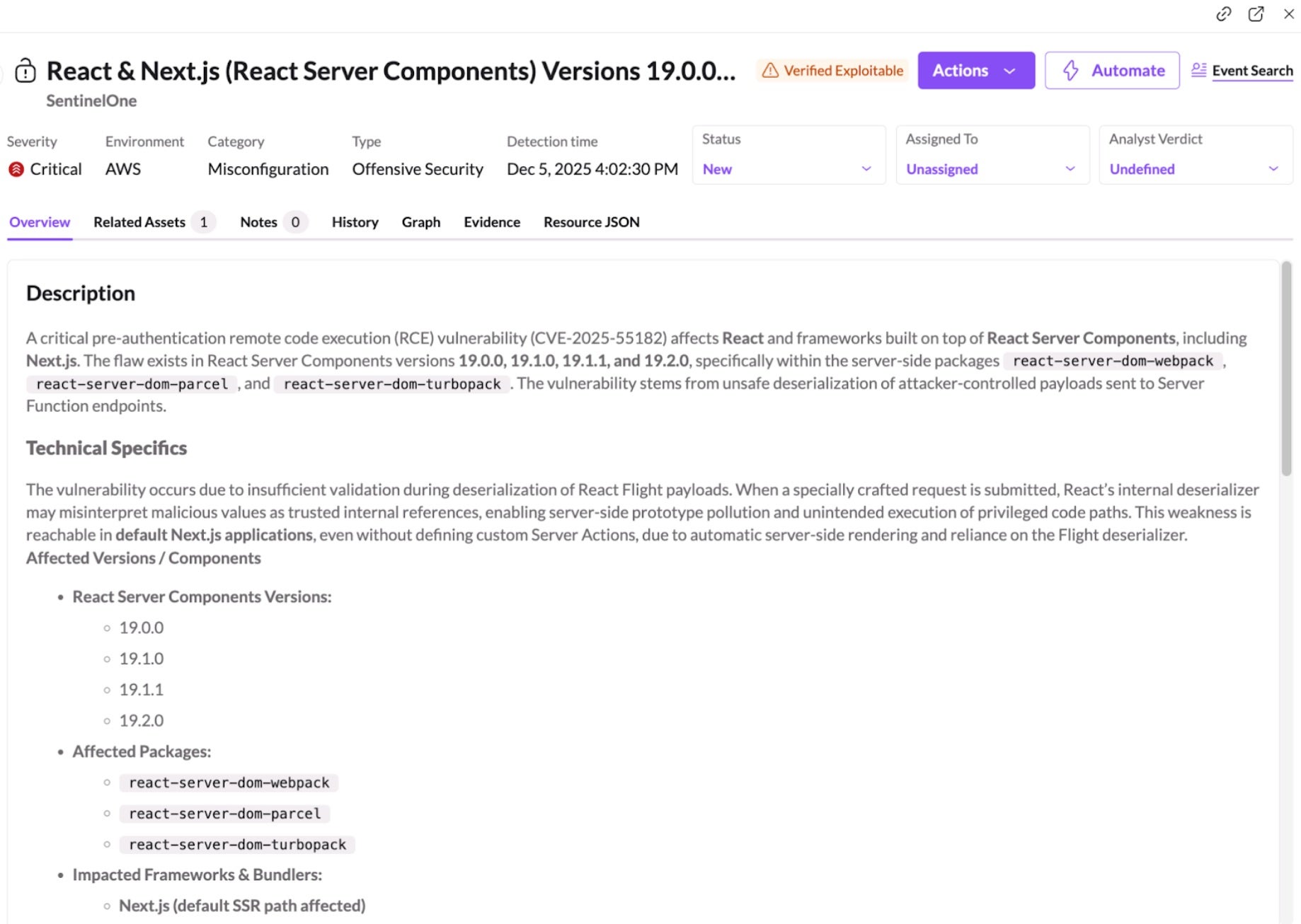
A critical remote code execution (RCE) vulnerability, dubbed ‘React2Shell’, affecting React Server Components (RSC) and Next.js, is allowing unauthenticated attackers to perform server-side code attacks via malicious HTTP requests.
Discovered by Lachlan Davidson, the flaw stems from insecure deserialization in the RSC ‘Flight’ protocol and impacts packages including react-server-dom-webpack, react-server-dom-parcel, and react-server-dom-turbopack. Exploitation is highly reliable, even in default deployments, and a single request can compromise the full Node.js process. The flaw is being tracked as CVE-2025-55182. Originally tagged as a CVE for Next.js, NIST subsequently rejected CVE-2025-66478, as it is a duplicate of CVE-2025-55182.
This blog post includes the critical, immediate actions recommended to secure your environment, new and existing Platform Detection Rules designed to defend against this vulnerability, and information on how SentinelOne Offensive Security Engine, a core component of the Singularity Cloud Security solution, allows our customers to quickly identify potentially vulnerable workloads.
Cloud Security solution, allows our customers to quickly identify potentially vulnerable workloads.
What is React2Shell? Background & Impact
On December 3, 2025, the React and Next.js teams disclosed two related vulnerabilities in the React Server Components (RSC) Flight protocol: CVE-2025-55182 (React) and CVE-2025-66478 (Next.js), with the latter CVE now marked by NIST as a duplicate.
Both enable unauthenticated RCE, impacting applications that use RSC directly or through popular frameworks such as Next.js. These vulnerabilities are rated critical (CVSS 10.0) because exploitation requires only a crafted HTTP request. No authentication, user action, or developer-added server code is needed for an attacker to gain control of the underlying Node.js process.
The vulnerability exists because RSC payloads are deserialized without proper validation, exposing server functions to attacker-controlled inputs. Since many modern frameworks enable RSC as part of their default build, some teams may be exposed without being aware that server-side RSC logic is active in their environment.
Security testing currently shows:
- Exploitation can succeed with near 100% reliability
- Default configurations are exploitable, including a standard
Next.jsapp created with create-next-app and deployed with no code changes - Applications may expose RSC endpoints even without custom server functions
- A single malicious request can escalate to full
Node.jsprocess compromise
Security researchers warn that cloud environments and server-side applications using default React or Next.js builds are particularly at risk. Exploitation could allow attackers to gain full control over servers, access sensitive data, and compromise application functionality. Reports have already emerged of China-nexus threat groups “racing to weaponize” the flaw.
Available Vendor Mitigations & Immediate Actions
Fixes are available in React 19.0, 19.1.0, 19.1.1, and 19.2.0, and Next.js 5.x, Next.js 16.x, Next.js 14.3.0-canary.77 and later canary releases. Administrators are urged to audit environments and update affected packages immediately.
Companies are advised to review deployments, restrict unnecessary server-side exposure, and monitor logs for anomalous RSC requests. Securing default configurations, validating deserialized input, and maintaining a regular patch management schedule can prevent attackers from exploiting framework-level vulnerabilities in production applications.
- Update React by installing the patched versions of React as listed above.
- Update
Next.jsand other RSC-enabled frameworks as listed above. Ensure the latest framework and bundler releases are installed so they ship the patched React server bundles. - Review deployment behavior by checking whether your organization’s workloads expose RSC server function endpoints. These may exist regardless of whether developers added custom server functions.
How SentinelOne Protects Our Customers
Cloud Native Security – Offensive Security Engine
SentinelOne’s Offensive Security Engine (OSE), core component of its Singularity Cloud Security solution, proactively distinguishes between theoretical risks and actual threats by simulating an attacker’s methodology. Rather than relying solely on static scans that flag every potential misconfiguration or vulnerability, this engine automatically conducts safe, harmless simulations against your cloud infrastructure to validate exploitability.
This approach delivers differentiated outcomes by radically reducing alert fatigue and focusing security teams on immediate, confirmed dangers. By providing concrete evidence of exploitability—such as screenshots or code snippets of the successful simulation—it eliminates the need for manual validation and “red teaming” of every alert. Shift from chasing hypothetical vulnerabilities to remediating verified attack vectors, ensuring resources are always deployed against the risks that pose a genuine threat to their environment.
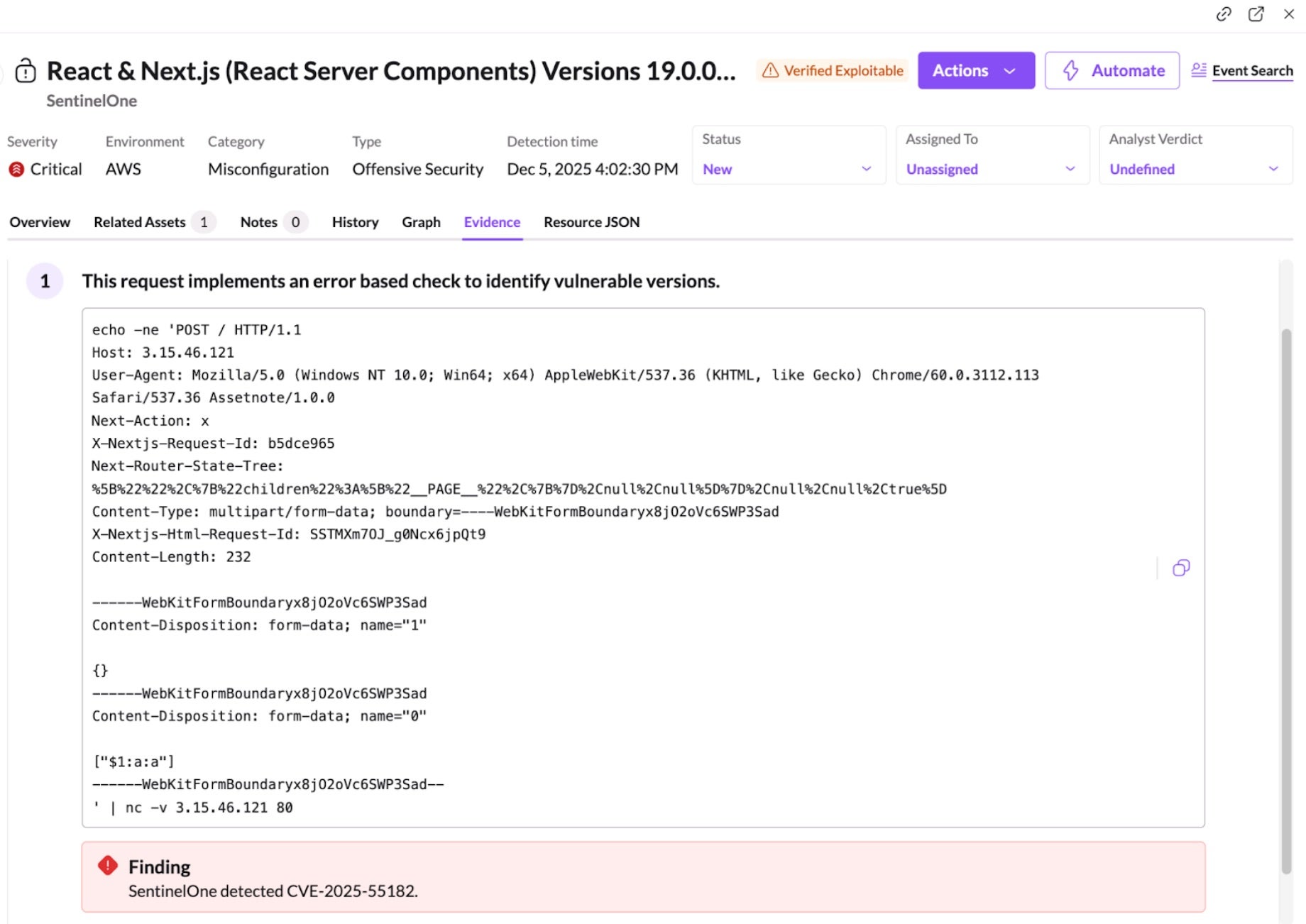
In response to this vulnerability, SentinelOne released a new OSE plugin which can verify exploitability of these vulnerabilities for publicly accessible workloads using a defanged (i.e., harmless) HTTP payload.
Viewing Misconfigurations in the SentinelOne Console
SentinelOne customers can quickly identify potentially vulnerable workloads using the Misconfigurations page in the SentinelOne Console.
Search for:
React & Next.js (React Server Components) Versions 19.0.0–19.2.0 Vulnerable to Pre-Authentication Remote Code Execution via Unsafe Deserialization (CVE-2025-55182)
This highlights Node.js workloads that are exposing RSC-related server function endpoints. Once identified, affected assets can be patched or temporarily isolated. SentinelOne CWS also detects suspicious Node.js behaviors associated with exploitation attempts, including downloaders and reverse shells, and provides Live Security Updates to maintain protection as new detections are deployed.
It identifies verified exploitable paths on your publicly exposed assets, confirming which systems are truly at risk. By validating exploitability rather than simply flagging theoretical vulnerabilities, Singularity Cloud Security minimizes noise and provides concrete evidence so security teams can focus on what matters.
Wayfinder Threat Hunting
The Wayfinder Threat Hunting team is proactively hunting for this emerging threat by leveraging comprehensive threat intelligence. This includes, but is not limited to, indicators and tradecraft associated with known active groups such as Earth Lamia and Jackpot Panda.
Our current operational coverage includes:
- Atomic IOC Hunting: We have updated our atomic IOC library to include known infrastructure and indicators from these threat actors, as well as broader intelligence regarding this campaign.
- Behavioral Hunting: We are actively building and executing hunts designed to detect behavioral TTP matches that identify suspicious activity beyond static indicators.
Notification & Response All identified true positive findings will generate alerts within the console for the affected sites. For clients with MDR, the MDR team will actively review these alerts and manage further escalation as required.
Platform Detection Rules
SentinelOne’s products provide a variety of detections for potential malicious follow-on reverse shell behaviors and other actions which may follow this exploit. As of December 5, 2025, SentinelOne released new Platform Detection Rules specifically to detect observed in-the-wild exploit activity. We recommend customers apply the latest detection rule, Potential Exploitation via Insecure Deserialization of React Server Components (RSC), urgently to ensure maximum protection.
Additionally, SentinelOne recommends customers verify the following existing rules have also been enabled:
- Potential Reverse Shell via Shell Processes
- Potential Reverse Shell via Node
- Potential Reverse Shell via Python
- Reverse Shell via Perl Utility
- Potential Reverse Shell via AWK Utility
- Potential Reverse Shell via GDB Utility
- Potential Reverse Shell via Lua Utility
- Potential Reverse Shell via Netcat
- Potential Reverse Shell using Ruby Utility
- Potential Reverse Shell via Socat Utility
Conclusion
CVE-2025-55182 and CVE-2025-66478 represent critical risks within the React Server Components Flight protocol. Because frameworks like Next.js enable RSC by default, many environments may be exposed even without intentional server-side configuration. Updating React, updating dependent frameworks, and verifying whether RSC endpoints exist in your organization’s workloads are essential steps.
Singularity Cloud Security helps organizations reduce risk by identifying vulnerable workloads, flagging misconfigurations, and detecting malicious Node.js behavior linked to RCE exploitation. This provides immediate visibility and defense while patches are applied.
Learn more about SentinelOne’s Cloud Security portfolio here or book a demo with our expert team today.
Third-Party Trademark Disclaimer:
All third-party product names, logos, and brands mentioned in this publication are the property of their respective owners and are for identification purposes only. Use of these names, logos, and brands does not imply affiliation, endorsement, sponsorship, or association with the third-party.