Reading view
Today’s Microsoft Outage Explained and Why it Triggers a Scam Playbook

Microsoft users across the U.S. experienced widespread disruptions Thursday after a technical failure prevented people from sending or receiving email through Outlook, a core service within Microsoft 365.
The outage occurred during U.S. business hours and quickly affected schools, government offices, and companies that rely on Outlook for daily operations. Microsoft confirmed the issue publicly and said it was working to restore service. There is no indication the disruption was caused by a cyberattack, according to company statements.
Still, McAfee warns in these situations to be wary of phishing attempts as scammers latch onto these outages to take advantage of innocent users.
“Outages like this create uncertainty, and scammers move fast to take advantage of it,” said Steve Grobman, McAfee’s Chief Technology Officer. “When people can’t get into email or the tools they use every day, it’s easy to assume something is wrong with your account — and that’s exactly the moment attackers look for.”
“Fake alerts start circulating that look like they’re coming from the real company, with logos and urgent language telling you to reset a password or verify your information,” Grobman added. “Some push fake support numbers or messages claiming they can restore access. If you’re impacted, slow down, go straight to the official source for updates, and don’t share passwords, verification codes, or payment details in response to an unexpected message.”
“Tools that can spot suspicious links and fake login pages help reduce risk — especially when people are trying to get back online quickly,” Grobman said.
Here, we break down what happened and why outages are prime time for scammers.
What happened to Microsoft Outlook?
A Microsoft infrastructure failure disrupted email delivery.
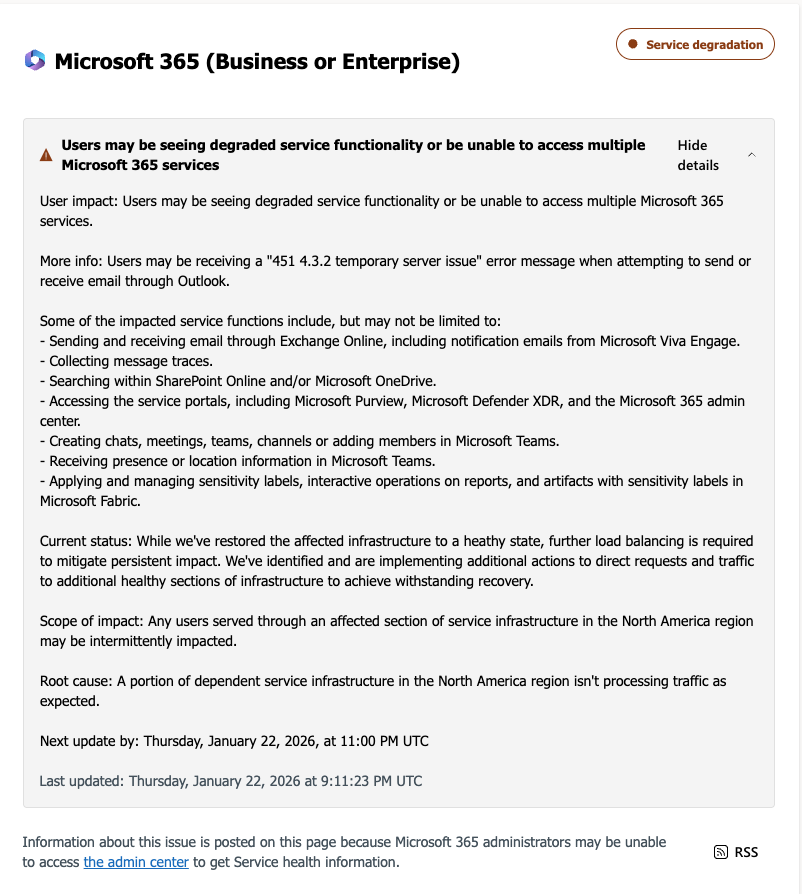
Microsoft said the outage was caused by a portion of its North American service infrastructure that was failing to properly handle traffic. Users attempting to send or receive email encountered a “451 4.3.2 temporary server issue” error message.
Microsoft also warned that related services, including OneDrive search and SharePoint Online, could experience slowdowns or intermittent failures during the incident.
When did the Microsoft outage happen?
The disruption unfolded over several hours on Thursday afternoon (ET).
Based on timelines reported by CNBC and live coverage from Tom’s Guide, the outage progressed as follows:
Around 2:00 p.m. ET: User reports spike across Microsoft services, especially Outlook, according to Down Detector data cited by Tom’s Guide.
2:37 p.m. ET: Microsoft confirms it is investigating an Outlook email issue, per CNBC.
3:17 p.m. ET: Microsoft says it identified misrouted traffic tied to infrastructure problems in North America, CNBC reports.
4:14 p.m. ET: The company announces affected infrastructure has been restored and traffic is being redirected to recover service.
Tom’s Guide reported that while outage reports declined after Microsoft’s fix, some users continued to experience intermittent access issues as systems rebalanced.
Was this a hack or cyberattack?
No. Microsoft says the outage was caused by technical infrastructure issues.
According to CNBC, Microsoft has not indicated that the outage was the result of hacking, ransomware, or any external attack. Instead, the company attributed the disruption to internal infrastructure handling errors, similar to a previous Outlook outage last July that lasted more than 21 hours.
A message sent by Microsoft about the server issue.
Why outages cause widespread disruption
Modern work depends on shared cloud infrastructure.
That sudden loss of access often leaves users unsure whether:
- Their account has been compromised
- Their data is at risk
- They need to take immediate action
That uncertainty is exactly what scammers look for.
How scammers exploit big tech outages
They impersonate the company and trick users into signing in again.
After major outages involving Microsoft, Google, or Amazon Web Services, security researchers, including McAfee, have observed scam campaigns emerge within hours.
These scams typically work by:
Impersonating Microsoft using logos, branding, and language copied from real outage notices
Sending fake “service restoration” emails or texts claiming users must re-authenticate
Linking to realistic login pages designed to steal Microsoft usernames and passwords
Posing as IT support or Microsoft support and directing users to fake phone numbers
Once credentials are stolen, attackers can access email accounts, reset passwords on other services, or launch further phishing attacks from a trusted address.
How to stay safe during a Microsoft outage
Outages are confusing. Scammers rely on urgency and familiarity.
To reduce risk:
- Do not click links in emails or texts about outages or “account recovery.”
- Go directly to official sources, such as Microsoft’s status page or verified social accounts.
- Never re-enter your password through links sent during an outage.
- Ignore urgent fixes that ask for downloads, payments, or credentials.
If you already clicked or entered information:
- Change your Microsoft password immediately
- Update passwords anywhere you reused it
- Turn on or refresh two-factor authentication
- Review recent account activity
- Run a trusted security scan to remove malicious software (check out our free trial)
How McAfee can help
Using advanced artificial intelligence, McAfee’s built-in Scam Detector automatically detects scams across text, email, and video, blocks dangerous links, and identifies deepfakes, helping stop harm before it happens.
McAfee’s identity protection tools also monitor for signs your personal information may be exposed and guide you through recovery if scammers gain access.
FAQ
| Q: Is Microsoft Outlook still down? A: Microsoft said Thursday afternoon that it had restored affected infrastructure and was redirecting traffic to recover service, according to CNBC. Some users may still experience intermittent issues. |
| Q: Was the Microsoft outage caused by hackers? A: No. Microsoft has not reported any cyberattack or data breach related to the outage, per CNBC. |
| Q: Can scammers really use outages to steal accounts? A: Yes. During major outages, scammers often impersonate companies like Microsoft and trick users into signing in again on fake websites. |
| Q: Should I reset my password after an outage? A: Only if you clicked a suspicious link or entered your credentials somewhere outside Microsoft’s official site. Otherwise, resetting passwords isn’t necessary. |
The post Today’s Microsoft Outage Explained and Why it Triggers a Scam Playbook appeared first on McAfee Blog.
In Other News: €1.2B GDPR Fines, Net-NTLMv1 Rainbow Tables, Rockwell Security Notice
Other noteworthy stories that might have slipped under the radar: Cloudflare WAF bypass, Canonical Snap Store abused for malware delivery, Curl terminating bug bounty program
The post In Other News: €1.2B GDPR Fines, Net-NTLMv1 Rainbow Tables, Rockwell Security Notice appeared first on SecurityWeek.
Someone Is Impersonating Me on Instagram — and Meta Doesn’t Give a Sh*t

After an Instagram impersonation, Alan Shimel reveals how Meta’s AI moderation dismissed a clear security threat—showing why identity protection is broken.
The post Someone Is Impersonating Me on Instagram — and Meta Doesn’t Give a Sh*t appeared first on Security Boulevard.
Hacking the Grid: How Digital Sabotage Turns Infrastructure into a Weapon
The darkness that swept over the Venezuelan capital in the predawn hours of Jan. 3, 2026, signaled a profound shift in the nature of modern conflict: the convergence of physical and cyber warfare. While U.S. special operations forces carried out the dramatic seizure of Venezuelan President Nicolás Maduro, a far quieter but equally devastating offensive was taking place in the unseen digital networks that help operate Caracas.
SCADA (ICS) Hacking and Security: Hacking Nuclear Power Plants, Part 1
Welcome back, aspiring cyberwarriors.
Imagine the following scene. Evening. You are casually scrolling through eBay. Among the usual clutter of obsolete electronics and forgotten hardware, something unusual appears. It’s heavy industrial modules, clearly not meant for hobbyists. On the circuit boards you recognize familiar names: Siemens. AREVA. The listing description is brief, technical, and written by someone who knows what they are selling. The price, however, is unexpectedly low.

What you are looking at are components of the Teleperm XS system. This is a digital control platform used in nuclear power plants. Right now, this class of equipment is part of the safety backbone of reactors operating around the world. One independent security researcher, Rubén Santamarta, noticed the same thing and decided to investigate. His work over two decades has covered everything from satellite communications to industrial control systems, and this discovery raised a question: what happens if someone gains access to the digital “brain” of a nuclear reactor? From that question emerged a modeled scenario sometimes referred to as “Cyber Three Mile Island,” which is a theoretical chain of events that, under ideal attacker conditions, leads to reactor core damage in under an hour.
We will walk through that scenario to help you understand these systems.
Giant Containers
To understand how a nuclear reactor could be attacked digitally, we first need to understand how it operates physically. There is no need to dive into advanced nuclear physics. A few core concepts and some practical analogies will take us far enough.
Three Loops
At its heart, a pressurized water reactor (PWR) is an extremely sophisticated and very expensive boiler. In simplified form, it consists of three interconnected loops.

The first loop is the reactor itself. Inside a thick steel vessel sit fuel assemblies made of uranium dioxide pellets. This is where nuclear fission occurs, releasing enormous amounts of heat. Water circulates through this core, heating up to around 330°C. To prevent boiling, it is kept under immense pressure (about 155 atmospheres). This water becomes radioactive and never leaves the sealed primary circuit.
The second loop exists to convert that heat into useful work. The hot water from the primary loop passes through a steam generator, a massive heat exchanger. Without mixing, it transfers heat to a separate body of water, turning it into steam. This steam is not radioactive. It flows to turbines, spins them, drives generators, and produces electricity.
Finally, the third loop handles cooling. After passing through the turbines, the steam must be condensed back into water. This is done using water drawn from rivers, lakes, or the sea, often via cooling towers. This loop never comes into contact with radioactive materials.

With this structure in mind, we can now discuss what separates a reactor from a nuclear bomb. It’s control.
Reactivity
If a car accelerates when you press the gas pedal, a reactor accelerates when more neutrons are available. This is expressed through the multiplication factor, k. When k is greater than 1, power increases. When it is less than 1, the reaction slows. When k equals exactly 1, the reactor is stable, producing constant power.
Most neutrons from fission are released instantly, far too fast for any mechanical or digital system to respond. Fortunately, about 0.7% are delayed, appearing seconds or minutes later. That tiny fraction makes controlled nuclear power possible.
There is also a built-in safety mechanism rooted in physics itself. It’s called the Doppler effect. As fuel heats up, uranium-238 absorbs more neutrons, naturally slowing the reaction. This cannot be disabled by software or configuration. It is the reactor’s ultimate brake, supported by multiple engineered systems layered on top.
Nuclear Reactor Protection
Reactor safety follows a defense-in-depth philosophy, much like a medieval fortress. The fuel pellet itself retains many fission products. Fuel rod cladding adds another barrier. The reactor vessel is the next wall, followed by the reinforced concrete containment structure, often over a meter thick and designed to withstand extreme impacts. Finally, there are active safety systems and trained operators. The design prevents a single failure from leading to a catastrophe. For a disaster to occur, multiple independent layers must fail in sequence.
From a cybersecurity perspective, attention naturally turns to safety systems and operator interfaces. Sensors feed data into controllers, controllers apply voting logic, and actuators carry out physical actions. When parameters drift out of range, the system shuts the reactor down and initiates cooling. Human operators then follow procedures to stabilize the plant. It is an architecture designed to fail safely. That is precisely why understanding its digital foundations matters.
Teleperm XS: Anatomy of The Nuclear “Brains”
The Teleperm XS (TXS) platform, developed by Framatome, is a modular digital safety system used in many reactors worldwide. Its architecture is divided into functional units. Acquisition and Processing Units (APUs) collect sensor data, like temperature, pressure, neutron flux. Actuation Logic Units (ALUs) receive this data from multiple channels and decide when to trigger actions such as inserting control rods or starting emergency pumps.
The Monitoring and Service Interface (MSI) bridges two worlds. On one side is the isolated safety network using Profibus. On the other is a conventional local area network used by engineers.

The Service Unit (SU) is a standard computer running SUSE Linux. It is used for diagnostics, configuration, testing, and firmware updates. Critically, it is the only system allowed to communicate bidirectionally with the safety network through the MSI. TXS uses custom processors like the SVE2 and communication modules such as the SCP3, but it also relies on commercial components, such as Hirschmann switches, single-board computers, and standard Ethernet.

This hybrid design improves maintainability and longevity, but it also expands the potential attack surface. Widely used components are well documented, available, and easier to study outside a plant environment.
Hunting For Holes
Any attacker would be happy to compromise the Service Unit, since it provides access to the APU and ALU controllers, which directly control the physical processes in the reactor. However, on the way to this goal, you still have to overcome several barriers.
Problem 1: Empty hardware
Ruben unpacked the SVE2 and SCP3 modules, connected the programmer, and got ready to dump the firmware for reverse engineering, but a surprise was waiting for him. Unfortunately (or fortunately for the rest of the world), the devices’ memory was completely empty.
After studying the documentation, it became clear that the software is loaded into the controllers at the factory immediately before acceptance testing. The modules from eBay were apparently surplus stock and had never been programmed.

It turned out that TXS uses a simple CRC32 checksum to verify the integrity and authenticity of firmware. The problem is that CRC32 is NOT a cryptographic protection mechanism. It is merely a way to detect accidental data errors, similar to a parity check. An attacker can take a standard firmware image, inject malicious code into it, and then adjust a few bytes in the file so that the CRC32 value remains unchanged. The system will accept such firmware as authentic.
It reveals an architectural vulnerability embedded in the very design of the system. To understand it, we need to talk about the most painful issue in any security system: trust.
Problem 2: MAC address-based protection
The MSI is configured to accept commands only from a single MAC address. It’s the address of the legitimate SU. Any other computer on the same network is simply ignored. However, for an experienced hacker, spoofing (MAC address impersonation) poses no real difficulty. Such a barrier will stop only the laziest and least competent. For a serious hacking group, it is not even a speed bump, it is merely road markings on the asphalt. But there is one more obstacle called a physical key.
Problem 3: A key that is not really a key
U.S. regulatory guidance rightly insists that switching safety systems into programming mode requires physical action. A real key, a real human and a real interruption. An engineer must approach the equipment cabinet, insert a physical key, and turn it. That turn must physically break the electrical circuit, creating an air gap between the ALU and the rest of the world. Turning the key in a Teleperm XS cabinet does not directly change the system’s operating mode. It only sets a single bit (a logical one) on the discrete input board. In the system logic, this bit is called “permissive.” It signals to the processor: “Attention, the Service Unit is about to communicate with you, and it can be trusted.”
The actual command to change the mode (switching to “Test” or “Diagnostics”) arrives later over the network, from that same SU. The ALU/APU processor logic performs a simple check: “A mode-change command has arrived. Check the permissive bit. Is it set? Okay, execute.”
As a result, if malware has already been implanted in the ALU or APU, it can completely ignore this bit check. For it, the signal from the key does not exist. And if the malware resides on the SU, it only needs to wait until an engineer turns the key for routine work (such as sensor calibration) and use that moment to do its dirty work.
The lock becomes a trigger.
Summary
Part 1 establishes the foundation by explaining how nuclear power plants operate, how safety is enforced through layered engineering and physical principles, and also how digital control systems support these protections. By looking at reactor control logic, trust assumptions in safety architectures, and the realities of legacy industrial design, it becomes clear that cybersecurity risk comes not from a single vulnerability, but from the interaction of multiple small decisions over time. These elements on their own do not cause failure, but they shape an environment in which trust can be misused.
In Part 2, we shift our focus from structure to behavior. We will actively model a realistic cyber-physical attack and simulate how it unfolds in practice, tracing the entire sequence from an initial digital compromise.
NSFOCUS Enters the Global Top Tier of DDoS Security: NSFOCUS DDoS Solutions Positioned in the MarketsandMarkets™ Star Quadrant
SANTA CLARA, Calif., Jan 21, 2026 – Recently, MarketsandMarkets™, a globally recognized market research and consulting firm, released its Global DDoS Protection and Mitigation Security Market Global Forecast to 2030 report, providing a comprehensive assessment of industry trends, technology evolution, and leading vendors worldwide. Based on its mature technology stack, comprehensive solution portfolio, and strong market […]
The post NSFOCUS Enters the Global Top Tier of DDoS Security: NSFOCUS DDoS Solutions Positioned in the MarketsandMarkets™ Star Quadrant appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
The post NSFOCUS Enters the Global Top Tier of DDoS Security: NSFOCUS DDoS Solutions Positioned in the MarketsandMarkets™ Star Quadrant appeared first on Security Boulevard.
Stateful Hash-Based Verification for Contextual Data Integrity
Learn how stateful hash-based signatures like XMSS and LMS provide quantum-resistant security for AI Model Context Protocol deployments and data integrity.
The post Stateful Hash-Based Verification for Contextual Data Integrity appeared first on Security Boulevard.
생산성 도구로 위장한 크롬 확장 프로그램, 기업 HR·ERP 계정 탈취 노려
크롬 웹 스토어의 방어 체계를 우회한 조직적인 악성 브라우저 애드온 캠페인이 확인됐다. 이 캠페인은 생산성 도구로 홍보된 확장 프로그램을 무기화해 기업 세션 토큰을 탈취하고, 궁극적으로 계정 전체를 장악하려는 시도를 벌였다.
보안 기업 소켓의 위협 연구팀은 블로그를 통해 “이 확장 프로그램들은 서로 연계해 인증 토큰을 훔치고, 사고 대응 기능을 차단하며, 세션 하이재킹을 통해 완전한 계정 탈취를 가능하게 한다”라고 설명했다. 해당 캠페인은 널리 사용되는 인사관리(HR) 및 전사적자원관리(ERP) 플랫폼을 주요 표적으로 삼았다.
소켓 연구진은 이번 공격을 자격 증명을 은밀히 탈취하는 방식과 기업의 보안 대응 기능을 방해하는 수법이 함께 사용된 복합적인 기업 침해 사례로 분석했다. 공격자는 겉보기에는 신뢰감을 주는 디자인과 정상적인 용도를 내세운 크롬 확장 프로그램 5종을 게시했으며, 실제로는 기업 업무 흐름 깊숙한 지점에서 악성 행위를 수행하도록 설계했다.
설치 수 집계 결과, 연구진이 구글 보안 팀에 경고하고 삭제 요청을 제출하기 전까지 2,300명 이상이 이 도구를 설치한 것으로 추정된다. 해당 확장 프로그램은 워크데이, 넷스위트, 석세스팩터스와 같은 시스템을 겨냥했으며, 이들 환경에서는 단 하나의 세션만 탈취돼도 직원 정보, 재무 데이터, 내부 업무 프로세스 전반이 노출될 수 있다.
악성 코드를 숨긴 가짜 생산성 도구
이번에 확인된 확장 프로그램들은 모두 기업 사용자를 위한 생산성 향상 도구나 보안 보조 도구를 가장했다. 크롬 웹 스토어 등록 페이지에는 완성도 높은 대시보드 화면과 함께 HR 또는 ERP 도구 접근을 간소화해 준다는 설명이 담겼다. 요청한 권한 역시 쿠키 접근이나 페이지 수정과 같은 ‘표준적’이고 무해해 보이는 기능으로 구성돼 있었다.
그러나 설치 이후에는 전혀 다른 행위가 이어졌다. 데이터바이클라우드 액세스(DataByCloud Access), 데이터 바이 클라우드 1(Data By Cloud 1), 소프트웨어 액세스(Software Access)로 불린 세 가지 확장 프로그램은 인증 토큰이 포함된 세션 쿠키를 공격자가 통제하는 인프라로 외부 전송했다. 다수의 기업 시스템에서는 이러한 토큰만으로도 비밀번호 입력 없이 사용자 인증이 가능하다. 일부 사례에서는 최신 자격 증명을 확보하기 위해 60초마다 쿠키를 추출한 것으로 나타났다.
이미 로그인 화면과 다중 인증 절차를 통과한 세션은 탈취된 비밀번호와 동일한 역할을 할 수 있다. 이로 인해 일반적인 보안 경고를 유발하지 않은 채 계정에 직접 접근할 수 있다는 점이 문제로 지적됐다.
연구진은 “작성 시점을 기준으로 다섯 개 확장 프로그램 모두 여전히 조사 중”이라며 “구글 크롬 웹 스토어 보안 팀에 삭제 요청을 제출했다”라고 설명했다. 구글은 CSO의 논평 요청에 즉각적인 답변을 내놓지 않았다.
보안 조치 우회와 세션 하이재킹
이번 캠페인은 자격 증명 탈취에 그치지 않았다. 툴 액세스 11(Tool Access 11)과 데이터 바이 클라우드 2(Data By Cloud 2)로 불린 두 개의 확장 프로그램은 DOM 조작 기능을 포함하고 있었으며, 이를 통해 표적 플랫폼 내 보안 및 관리 페이지 접근을 적극적으로 차단했다. 이로 인해 기업 관리자는 비밀번호 변경, 로그인 이력 확인, 침해된 계정 비활성화와 같은 화면에 접근할 수 없었고, 의심스러운 활동을 인지하더라도 즉각적인 대응이 어려운 상황에 놓였다.
다섯 개 가운데 가장 고도화된 것으로 분석된 소프트웨어 액세스는 쿠키 탈취 외에도 양방향 쿠키 주입 기능을 제공했다. 탈취한 세션 토큰을 공격자가 제어하는 브라우저에 다시 주입하는 방식으로, chrome.cookies.set()과 같은 API를 활용해 유효한 인증 쿠키를 직접 심는 구조다. 이를 통해 피해 사용자의 추가적인 조작 없이도 공격자는 인증된 세션을 확보할 수 있었다.
이 기법은 로그인 화면과 다중 인증 절차를 사실상 우회하며, 즉각적인 계정 탈취를 가능하게 한다.
연구진은 “네 개의 확장 프로그램은 databycloud1104 계정으로, 나머지 하나는 다른 브랜드로 게시됐지만, 다섯 개 모두 동일한 인프라 패턴을 공유하고 있어 단일 조직이 주도한 협력된 작전으로 보인다”라고 분석했다.
소켓은 기업을 대상으로 브라우저 확장 프로그램 사용을 엄격히 감사하고 제한할 것을 권고했다. 또한 권한 요청을 면밀히 검토하고, 쿠키나 기업용 사이트에 불필요하게 접근하는 애드온은 제거해야 한다고 조언했다. 이와 함께 비정상적인 세션 활동을 지속적으로 모니터링하고, 사용자에게 배포되기 전에 악성 확장 프로그램 행위를 탐지할 수 있는 도구를 활용할 필요가 있다고 제시했다.
dl-ciokorea@foundryco.com

Granular Policy Enforcement for Decentralized Model Context Resources
Secure your Model Context Protocol (MCP) deployments with granular policy enforcement and post-quantum cryptography. Prevent tool poisoning and puppet attacks.
The post Granular Policy Enforcement for Decentralized Model Context Resources appeared first on Security Boulevard.
Ring’s Facial Recognition Feature: Convenience or Privacy Nightmare?
In this episode, we explore Amazon Ring’s newly introduced Familiar Faces feature that utilizes AI for facial recognition. We discuss the convenience of identifying familiar people at your doorstep, the privacy concerns it raises, and the legal implications surrounding biometric data. Learn about how this feature works, potential inaccuracies, and privacy laws in certain U.S. […]
The post Ring’s Facial Recognition Feature: Convenience or Privacy Nightmare? appeared first on Shared Security Podcast.
The post Ring’s Facial Recognition Feature: Convenience or Privacy Nightmare? appeared first on Security Boulevard.
Hardware Security Module Integration for Quantum-Safe Model Contexts
Learn how to integrate Quantum-Safe HSMs with Model Context Protocol (MCP) to secure AI infrastructure against Shor's algorithm and context injection.
The post Hardware Security Module Integration for Quantum-Safe Model Contexts appeared first on Security Boulevard.
JFrog Researchers Uncover RCE Exploit for Existing Redis Database Vulnerability

JFrog this week published an analysis of a vulnerability in Redis databases that may be more serious than initially thought following the discovery of a remote code execution (RCE) exploit. Researchers found that a stack buffer overflow vulnerability in Redis (CVE-2025-62507) can be used to run the XACKDEL command with multiple IDs to trigger a..
The post JFrog Researchers Uncover RCE Exploit for Existing Redis Database Vulnerability appeared first on Security Boulevard.
This Week in Scams: Fake Brand Messages and Account Takeovers

This week in scams, social engineering sits at the center of several major headlines, from investment platform breaches to social media account takeovers and new warnings about AI-driven fraud.
Every week, this roundup breaks down the scam and cybersecurity stories making news and explains how they actually work, so readers can better recognize risk and avoid being manipulated.
Let’s get into it:
Betterment Warns Customers of Breach
The big picture:
Attackers accessed third-party systems used by Betterment, then used the information they stole to impersonate the company, contact customers, and promise scam crypto investment opportunities with too-good-to-be-true returns.
What happened:
- Attackers used social engineering to compromise third-party tools Betterment uses for marketing and operations, as reported by TechCrunch.
- With access to internal systems, they sent messages to customers that appeared legitimate.
- The messages promised to triple crypto holdings if recipients sent $10,000 to a wallet controlled by the attackers, a classic “send money to get more back” lure, later detailed by The Verge.
- Betterment says no account logins or passwords were compromised, but personal data like names, contact details, and dates of birth were exposed, enough to make the messages feel real.
Red flags to watch for:
- Promises of guaranteed or multiplied crypto returns
- Requests to send money first to “unlock” a benefit
- Messages tied to a breach but asking for immediate action outside the app
How the breach happened:
Social engineering is a type of scam that targets people rather than software or security systems. Instead of hacking code, scammers focus on tricking someone into giving them access.
Attackers research how a company operates, which tools it uses, and who is likely to have permissions. They then impersonate a trusted source, such as a vendor, coworker, or automated system, and send a realistic message asking for a routine action.
That action might be approving a login, resetting credentials, sharing a file, or clicking a link. Once the person complies, the scammer gains legitimate access and can move through systems using real permissions. Social engineering works because it exploits trust, familiarity, and urgency, making normal workplace behavior the pathway to a breach.
Social Engineering Scams Fueled by AI On the Rise
Big picture:
Fraud is increasingly driven by impersonation, automation, and trust abuse rather than technical hacking, according to new industry forecasts.
What happened:
A new Future of Fraud Forecast from Experian warns that fraudsters are rapidly weaponizing AI and identity manipulation. The report highlights agentic AI systems committing fraud autonomously, deepfake job candidates passing live interviews, cloned websites overwhelming takedown efforts, and emotionally intelligent bots running scams at scale.
The scope of the problem is already visible. Federal Trade Commission data shows consumers lost more than $12.5 billion to fraud in 2024, while nearly 60% of companies reported rising fraud losses between 2024 and 2025. Experian’s forecast suggests these losses will accelerate as fraud becomes harder to attribute, trace, and interrupt.
Red flags to watch:
- Requests or actions initiated without clear human ownership
- Identity verification steps that feel automated or unusually frictionless
- Transactions triggered by AI systems with unclear accountability
Phishing Scam Locks Users Out of X Accounts
Big picture: Officials are warning of increasing phishing attacks that steal X users’ accounts and then use their profile to sell crypto.
What happened: The Better Business Bureau issued a warning about phishing messages targeting users on X, particularly accounts with large followings. Victims receive direct messages that appear to come from colleagues or professional contacts, often asking them to click a link to support a contest, event, or opportunity.
Once the link is clicked, victims are locked out of their accounts. The compromised accounts are then used to promote cryptocurrency and other products, while automatically sending the same phishing message to additional contacts.
Red flags to watch:
- Unsolicited direct messages containing links
- Requests framed as favors, votes, or professional support
- Sudden loss of account access after clicking a link
How this happened and what to learn:
The scam relies on account impersonation and lateral spread. Instead of reaching strangers, attackers move through existing trust networks, using one compromised account to reach the next.
The takeaway is that familiarity does not equal legitimacy. Even messages from known contacts should be treated with caution when links or logins are involved.
McAfee’s Safety Tips for This Week
- Learn more about spotting phishing emails. Don’t accidentally expose yourself, your friends, family, or workplace to scammers. Our ultimate phishing guide has real world examples and more practical tips.
- Verify inside official apps or sites. If you get a security email, don’t click any links. Instead, open the official app or type the website address yourself for more information.
- Watch your exposed data. With tools like Google’s Dark Web Monitoring going away, ongoing identity monitoring matters more than ever.
- Stay alert to trending scams. Weight-loss drug fraud like Ozempic offers is already surging in the new year, and awareness is your first defense.
McAfee will be back next week with another roundup of the scams making headlines and the practical steps you can take to stay safer online.
The post This Week in Scams: Fake Brand Messages and Account Takeovers appeared first on McAfee Blog.
McAfee and Pat McAfee Turn a Name Mix-Up Into a Push for Online Safety

If a message popped up in your feed tomorrow promising a cash refund, a surprise giveaway, or a limited-time crypto opportunity, would you pause long enough to question it?
That split second matters more than ever.
Most modern scams don’t rely on panic or obvious red flags. They rely on familiarity. On things that feel normal. On moments that seem too small to question.
And those moments are exactly what scammers exploit.
Why Today’s Scams Are So Easy to Fall For
There was a time when spotting a scam was relatively straightforward. The emails were badly written. The websites looked rushed. The warnings were obvious.
Scammers don’t just rely on obvious spam or panic-driven messages. Instead, many now use:
- Friendly, natural language
- Faces of celebrities and figures you trust
- Messages that arrive through trusted apps
- Conversations that unfold gradually
- Requests that feel routine instead of suspicious
McAfee’s Celebrity Deepfake Deception research shows how common and convincing these scams have become: 72% of Americans say they’ve seen a fake or AI-generated celebrity endorsement, and 39% say they’ve clicked on one that turned out to be fraudulent. When scam content shows up in the same feeds, apps, and formats people use every day, it feels normal.
That’s the danger zone. It’s also why McAfee chose to use a familiar, culturally recognizable moment to talk about a much bigger issue.
Why McAfee Partnered with Pat McAfee
Whether you’ve been saying mack-uh-fee or mick-affy, the long-running name mix-up is harmless in everyday conversation.
Online, though, small moments of confusion can have outsized consequences.
Scammers rely on quick assumptions: that a familiar name means legitimacy, that a recognizable face means trust, that a message arriving in the right place must be real. They move fast, hoping people act before stopping to verify
Pat McAfee knows firsthand how scammers exploit familiarity and trust.
In recent months, fake social media giveaways promising cash and prizes have circulated using Pat’s likeness, and even a fraudulent “American Heart Association fundraiser” made the rounds, falsely claiming he was collecting donations.
Pat wants his fans to know: if you ever see a giveaway, fundraiser, or message claiming to be from him, double-check it on his official channels first. If it feels off, it probably is.
Unfortunately, these scams work because people trust Pat. Scammers exploit that trust to lower people’s guard and make fraudulent requests feel legitimate.
It’s the same tactic used across countless impersonation scams today: borrow the authority of a familiar face, add a sense of urgency, and move fast before anyone stops to verify, “is this legit?” We’ve seen it happen with Taylor Swift, Tom Hanks, Al Roker, Brad Pitt, and numerous others.
Remember, no legitimate giveaway will ask for payment, banking details, login credentials, or account access. And no nonprofit fundraiser tied to a celebrity should ever come from a personal message or unfamiliar social account.
Watch: Pat McAfee Explains How McAfee Is More Than an Antivirus
In the video below, Pat McAfee playfully demonstrates how easily familiar moments online can turn into risk, and why digital safety today can’t rely on perfect judgment alone.
How to Protect Yourself Right Now
You don’t have to stop using your favorite platforms. But you do have to change how you verify online threats.
Before You Trust Any Urgent Message or Offer:
- Be skeptical of sudden financial opportunities
- Assume giveaways that require payment or credentials are scams
- Never connect accounts, wallets, or payment methods from social links
- Verify claims on official websites, not just inside apps
- Be cautious of messages that replace clear context with urgency
If a video or message feels real but the request feels extreme, that’s a red flag.
McAfee offers more than traditional antivirus, combining multiple layers of digital protection in one app
- Scam Detector to help flag suspicious messages and links
- Safe Browsing tools to help block risky websites
- VPN to keep your connection private on public Wi-Fi
- Identity Monitoring and Alerts to notify you if your personal information appears where it shouldn’t
- Personal Data Cleanup to help remove your information from high-risk data broker sites
- Device and Account Security to help protect the things you use most
Final Takeaway
If a scam looks obvious, most people won’t fall for it.
But modern scams don’t look obvious. They look familiar. They use your favorite faces. They look normal. They look safe. And that’s where people get hurt.
Staying safe now means slowing down, verifying independently, and having protection work quietly in the background while you stay focused on what you actually came online to do.
McAfee’s built-in Scam Detector, included in all core plans, automatically detects scams across text, email, and video, blocks dangerous sites, and identifies deepfakes, stopping harm before it happens.
And because today’s risks aren’t just about what you click, a VPN and Personal Data Cleanup add additional layers of defense by helping protect your connection and limit how much personal information is available to be exploited in the first place.
Ready to get Pat’s Picks? Learn more here.
FAQs
For clarity, and because these questions come up often, here’s the straightforward explanation:
| Q: Is Pat McAfee the founder of McAfee antivirus? A: No. Pat McAfee is not associated with the founding or leadership of McAfee. McAfee was founded by John McAfee and operates independently. |
| Q: Are Pat McAfee and McAfee the same company? A: No. Pat McAfee is a sports media personality. McAfee is a cybersecurity company. They are separate entities. |
| Q: Why does McAfee work with Pat McAfee? A: McAfee partnered with Pat McAfee to raise awareness about online scams, impersonation fraud, and digital safety using culturally relevant examples. |
The post McAfee and Pat McAfee Turn a Name Mix-Up Into a Push for Online Safety appeared first on McAfee Blog.
Project Eleven Raises $20 Million for Post-Quantum Security
The startup is building the necessary infrastructure and tools to help organizations transition to post-quantum computing.
The post Project Eleven Raises $20 Million for Post-Quantum Security appeared first on SecurityWeek.
Why Traditional Firewalls Fail Against Today’s High-Volume DDoS Attacks

Traditional firewalls can’t stop modern DDoS attacks. Learn why high-volume, multi-layer attacks overwhelm perimeter defenses—and how to build real DDoS resilience.
The post Why Traditional Firewalls Fail Against Today’s High-Volume DDoS Attacks appeared first on Security Boulevard.
Quantum-resistant zero trust architecture for MCP hosts
Learn how to build a quantum-resistant zero trust architecture for MCP hosts. Protect AI infrastructure with lattice-based crypto and 4D access control.
The post Quantum-resistant zero trust architecture for MCP hosts appeared first on Security Boulevard.
Google Ends Dark Web Report. What That Means and How to Stay Safe

Google has officially discontinued its Dark Web Report, the tool that alerted users when their personal information appeared in dark web breach databases. New scans stop on January 15, 2026, and on February 16, 2026, Google will permanently delete all data associated with the feature.
This does not mean Google.com or Google Accounts are going away. It means Google is no longer scanning the dark web for leaked data tied to your account, and it is no longer storing or updating any breach information that was collected for the report.
For people who relied on Google’s alerts, this change creates a real gap. After January 16, you will no longer get new notifications if your information shows up in breach databases. That is why it is worth taking a few minutes now to lock down the basics.
According to reporting from TechCrunch, Google said it ended the service after concluding that it did not give users enough clarity about what to do once their data was found.
That decision highlights a much larger shift in online security: Finding leaked data is no longer enough. Protecting identity is now the real challenge.
What did Google’s Dark Web Report do?
The Dark Web Report was a Google Account feature that searched known data breach dumps and dark web marketplaces for personal information tied to a user, such as email addresses, phone numbers, and other identifiers.
If Google found a match, it sent an alert.
What it did not do was show which accounts were at risk, whether financial or government ID data was involved, or how to prevent fraud from happening next. That gap is why some users said the tool fell short.
What is the dark web, and why does stolen data end up there?
The internet has three layers:
- The surface web is what search engines index.
- The deep web includes anything behind a login, like email, banking, and medical portals.
- The dark web is a hidden part of the deep web that is not indexed by search engines and is accessed through specialized networks or browsers like Tor.
The dark web is where data from breaches is commonly sold, traded, and packaged for scams. When a company is hacked, stolen files often end up in dark web databases that include email addresses, passwords, Social Security numbers, bank details, and full identity profiles.
Scammers use this data to commit account takeovers, financial fraud, tax fraud, and identity theft.
Even without passwords, this personal information can be enough for scammers to target you with convincing phishing and social engineering scams.
How to check if your personal information is on the dark web:
Looking up an email address is no longer enough. Modern identity theft relies on things like Social Security numbers, government IDs, bank and credit card numbers, tax records, insurance data, usernames, and phone numbers.
To understand whether any of that is exposed, people need to monitor the dark web for identity-level data, not just logins.
Here is what that looks like in practice:
- Scan breach databases for government ID numbers and financial data
- Look for full identity profiles being sold or traded
- Match leaked records back to real people
Tools like McAfee’s Identity Monitoring are designed to look for those types of data so you can act before fraud happens.
Have 30 minutes right now? Do this:
Been meaning to bolster your security? Here are three quick ways you can enhance your identity protection and reduce real-world damage in a breach:
Freeze your credit
Estimated time: 10 minutes
This is a powerful free protection option that many forget about. A credit freeze blocks anyone from opening new loans, credit cards, or accounts in your name, even if they have your Social Security number and full identity profile.
You can do this for free with any of the major credit bureaus. If you do it with one, the others are notified.
Why this matters: Most identity theft today is not account hacking. It is criminals opening accounts in your name. A credit freeze stops that cold.
Set up fraud and login alerts on your financial accounts
Estimated time: 10 minutes
Go into your main bank and credit card apps and turn on:
- Login alerts
- Transaction alerts
- Password or profile change alerts
- These are not the same as marketing notifications. They tell you when someone is trying to access or move money.
You’ll find these somewhere under Settings>Alerts.
Why this matters: Identity thieves often test stolen data with small charges or login attempts before stealing larger amounts. These alerts are how you catch it early.
Lock down account recovery paths
Estimated time: 10 minutes
This is one of the most overlooked vulnerabilities.
Go into:
- Your email account
- Your Apple ID or Google account
Check and update:
- Recovery email
- Recovery phone number
- Backup codes
- Trusted devices
Remove anything you do not recognize.
Why this matters: Even if you change your password, attackers can still take over accounts through recovery systems if those are compromised. This closes that back door.
FAQ:
| Is Google deleting my Google Account data? No. Google is only deleting the data it collected specifically for the Dark Web Report feature. Your Gmail, Drive, Photos, and other Google Account data are not affected. |
| Is Google still protecting my account from hackers? Yes. Google continues to offer security features like two-factor authentication, login alerts, and account recovery tools. What it removed is the dark web scanning and alert system tied to breach data. |
| Does the dark web report website still exist? No. After February 16, 2026, Google no longer operates or updates the Dark Web Report feature. There is no active scanning, no dashboard, and no stored breach data tied to it. |
| Does this mean dark web monitoring is useless? No. It means email-only monitoring is not enough. Criminals use far more than emails to commit fraud, which is why identity-level monitoring is now more important. |
| What kind of information is most dangerous if it appears on the dark web? Social Security numbers, government IDs, bank and credit card numbers, tax records, insurance IDs, usernames, and phone numbers are the data types most commonly used for identity theft and financial fraud. |
| How can I check if my information is exposed right now? You can use an identity monitoring service like McAfee that scans dark web sources for sensitive personal data, not just email addresses. That is how people can see whether their identity is being traded or abused today. |
The post Google Ends Dark Web Report. What That Means and How to Stay Safe appeared first on McAfee Blog.
How to Spot a Fake GLP-1 Weight-Loss Drug Before You Buy

“I thought I was getting a trusted weight-loss medication, but instead, I ended up sick and scammed. I never imagined something like this could happen to me.”
Fiona, like many others, turned to Ozempic as a way to lose weight. With high demand making it difficult to find and prices soaring, she turned to an online pharmacy she found on social media. After placing an order, she received the medication and began taking it, only to experience severe side effects, including migraines, dizziness, and nausea.
“When my symptoms got worse, I knew something was wrong,” she told McAfee. Concerned, she sought professional advice. “A doctor friend showed me what real Ozempic packaging looks like—and it was nothing like what I had received.”
“I was putting something in my body that I thought was safe. Instead, I was taking an unknown substance that made me seriously ill,” she told McAfee. “That’s terrifying.”
When she reached out to the pharmacy for a refund, they cut off all communication. Nearly a year later, Fiona still avoids online shopping altogether and hopes her experience will warn others to research online pharmacies carefully before making a purchase.
“As soon as I questioned the pharmacy about the product, they vanished. No refund, no explanation. Just silence. That’s when I knew I had been completely scammed.”
Unfortunately, Fiona’s story is one of many as surging interest in GLP-1 medications spurs scammers into action.
If you’ve searched for GLP-1 medications online, you’ve probably noticed how crowded and confusing it’s become. Between ads, telehealth offers, and social media posts promising easy access, it can be hard to tell what’s real.
That confusion isn’t accidental. McAfee’s researchers previously reported a wave of fake pharmacy sites and scam messages designed to catch people in exactly that moment of uncertainty.
What are GLP-1 medications?
GLP-1 (glucagon-like peptide-1) medications are prescription drugs that help regulate blood sugar and appetite. Doctors have used them to treat Type 2 diabetes for nearly two decades, and some have also been approved to support weight management.
Because these medications affect insulin levels and digestion, they require medical supervision and a valid prescription. There is currently no legitimate over-the-counter version that works the same way.
Why GLP-1 scams are exploding
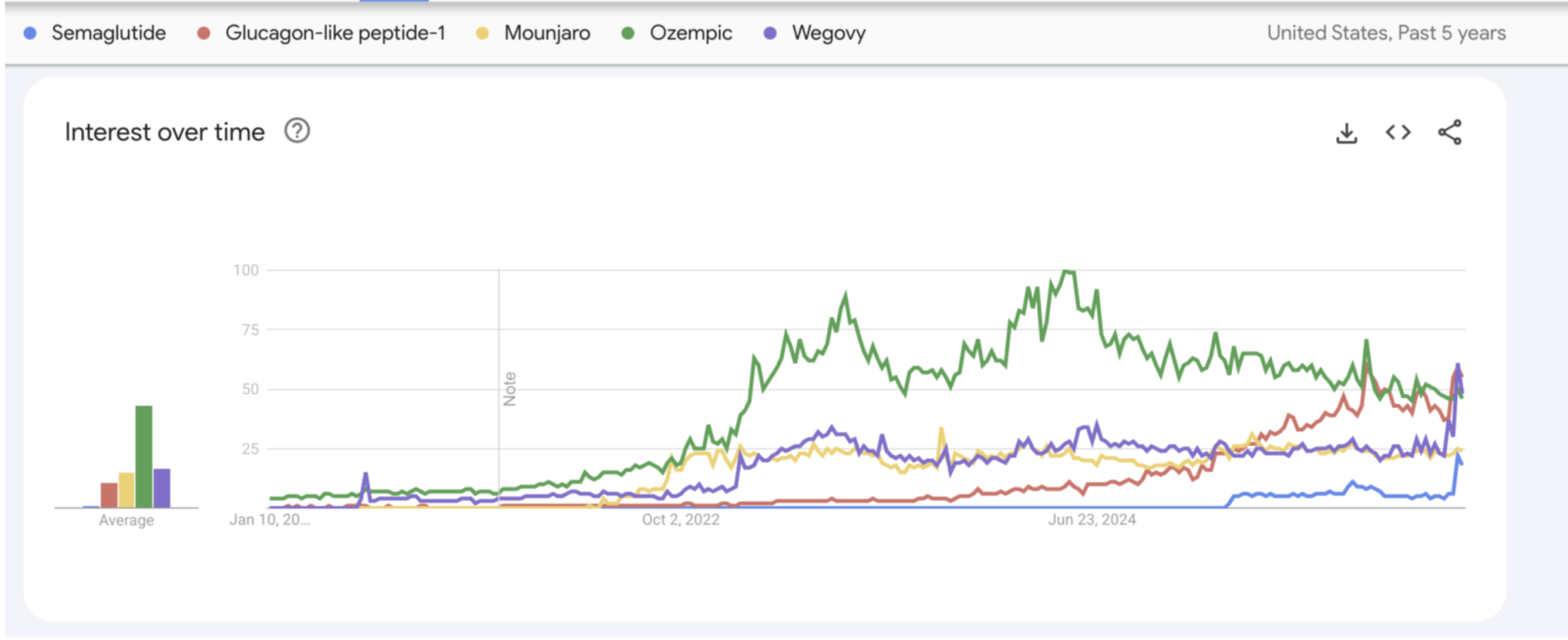
GLP-1 drugs have moved from a specialized medical treatment to a mainstream topic almost overnight, with a recent poll finding that 1 in 8 U.S. adults say they are currently taking a GLP-1 for weight loss.
Whenever high demand, high prices, and limited supply collide online, scammers move in
McAfee’s threat researchers have previously found that phishing attempts and fake websites tied to GLP-1 drugs increased by more than 180% during periods when interest in these medications surged. Hundreds of risky domains and hundreds of thousands of scam messages have been linked to searches for weight-loss drugs.
At the same time, consumer watchdogs such as the Better Business Bureau (BBB) report a spike in complaints from people who clicked on fake ads, visited fraudulent pharmacies, or received scam texts promising instant access to GLP-1 prescriptions.
Common GLP-1 scams to watch out for
1. AI-generated celebrity and doctor endorsements
Scammers are using artificial intelligence to create realistic-looking videos and images of public figures and medical professionals promoting weight-loss products. One recent incident saw a fake, AI Oprah selling scam weight loss drugs
These ads often appear in social media feeds and look legitimate, but the endorsements are fabricated.
The goal is to build trust quickly with a familiar face and then push people toward a purchase page. From there, you’re left with a fake product, or no product at all, and your information exposed.
Red flag: Any ad claiming a celebrity or doctor is selling GLP-1 drugs through a link or social media page.
2. Fake prescription texts and emails
Some scams arrive as urgent messages saying you are “approved” or “eligible” for GLP-1 treatment. These messages typically include a link to a fake medical website that collects personal, insurance, or payment information.
Red flag: Real prescriptions are not issued through unsolicited texts, emails, or DMs.
3. Fake online pharmacies
Fraudulent websites advertise GLP-1 medications at discounted prices. After payment, victims may receive nothing, diluted products, or face repeated unauthorized charges.
Consumer reports describe sites that look professional but provide only chat-box support and ignore cancellation requests.
Red flag: Pharmacies that don’t require a prescription or don’t list a physical U.S. address and phone number.
4. Subscription traps
Some scam offers quietly enroll buyers in recurring billing. Be wary of a “company” trying to offer a minimal “membership” or free “trial” with plans locking you into larger, more expensive future subscription plan without your clear consent.
Red flag: Vague billing terms or hidden subscription language.
5. Missing or fake shipments
Some scam sites provide tracking numbers that never update, claim packages were lost, or ask for more shipping fees … while continuing to charge customers.
Red flag: No real customer service and no way to cancel or dispute orders.
What makes these scams especially dangerous
Unlike many online scams, GLP-1 fraud carries real health risks.
Some victims report receiving substances that do not match what was advertised, including mislabeled or unverified injectables.
Because GLP-1 medications affect blood sugar and metabolism, taking the wrong substance or dosage can be dangerous.
In addition to the medical risks, illegitimate storefronts pose a real threat to your private information. During your purchase, you may be tricked into sharing our address, contact info, payment details, and insurance information.
How to safely pursue GLP-1 treatment
If you’re considering GLP-1 medications for health or weight management, these steps can help reduce risk:
Step 1: Start with a licensed healthcare provider
Only a doctor or licensed medical professional can determine if GLP-1 treatment is appropriate for you.
Step 2: Use verified pharmacies
If you use telehealth or online pharmacies, confirm they are properly licensed and require a prescription.
Step 3: Research before you pay
Look up unfamiliar pharmacies through trusted consumer-protection resources before entering payment or insurance information. If you’re in doubt, it’s better not to share any personal info.
Step 4: Be skeptical of miracle claims
There is no over-the-counter or legal “natural GLP-1,” patch, salt trick, or supplement that produces the same effect as prescription medication.
What to do if you think you were targeted:
If you clicked a link, entered information, or made a purchase:
- Stop communicating with the seller
- Monitor your bank and credit accounts for unusual activity
- If you notice suspicious charges, contact your bank directly
- Change any passwords you shared
- Run a security scan on your device (here’s our free trial)
- Report the incident to consumer-protection agencies
Reporting helps stop the same scams from spreading to others. This is where you can get more information from the FDA and report scams.
How to Spot a Fake GLP-1 Weight-Loss Drug If You’ve Already Bought One
If you’ve already ordered a GLP-1 weight-loss drug and something feels off, trust that instinct. Counterfeit GLP-1 products are increasingly convincing at first glance, but many show clear warning signs once you look closely.
Here’s what to check:
Packaging and Label Red Flags
Poor print quality or spelling errors
Examine the carton, label, and insert carefully. Misspelled words, inconsistent fonts, blurry printing, or incorrect manufacturer details are common signs of counterfeit medication.
Packaging that looks tampered with or unfamiliar
Authentic GLP-1 medications come in sealed, tamper-resistant packaging. If the box appears opened, resealed, relabeled, or noticeably different from what you’ve received from a legitimate pharmacy before, stop using it and contact a pharmacist.
Incorrect or missing language
Medications sold legally in the U.S. should include labeling and instructions in English. Missing inserts or foreign-language packaging can be a red flag.
Unusual product form
Be especially cautious of GLP-1 products sold as powders in vials that require mixing. These formulations are not authorized and have been linked to serious health risks.
Check Lot and Serial Numbers
Most legitimate GLP-1 medications include lot numbers or serial information that can be verified.
If your product includes these details, compare them against information published by the manufacturer or alerts from regulators. If the numbers don’t match, or are missing entirely, that’s a warning sign.
What to Do If You’re Unsure
If anything about your medication doesn’t match what you expect:
- Stop using the product
- Contact a licensed pharmacist or healthcare provider
- Avoid purchasing refills from the same source
When it comes to injectable medications, uncertainty isn’t something to push through. If you can’t confidently verify what you have, it’s safer to assume it may not be real.
Final Thoughts
Wanting to get healthier in the new year is a good thing. Falling for fake prescriptions, AI-generated endorsements, or fraudulent pharmacies is not.
McAfee is here to help keep your devices, identity, and finances safe while you focus on your goals in 2026.
Frequently Asked Questions
For clarity, and because these questions come up often, here’s the straightforward explanation:
| Are GLP-1 drugs available without a prescription? No. Legitimate GLP-1 medications require a prescription and medical oversight. |
| Are social media GLP-1 ads real? It depends. While there are certainly real ads out there, many are fake. AI-generated celebrity and doctor endorsements are commonly used in scams. So be wary and verify who is behind a post. |
| Are GLP-1 patches, gummies, or “salt tricks” legitimate? No over-the-counter product works the same way as prescription GLP-1 medication. |
| Why do scammers use crypto or payment apps? These payment methods are harder to reverse, which makes them attractive for fraud. |
The post How to Spot a Fake GLP-1 Weight-Loss Drug Before You Buy appeared first on McAfee Blog.