Reading view
Airlock Digital Announces Independent TEI Study Quantifying Measurable ROI & Security Impact
Sprocket Security Appoints Eric Sheridan as Chief Technology Officer
9 Cybersecurity Questions that Define a CISO
The Cybersecurity Vault — episode 52, with guest Wil Klusovsky.
Wil discusses the essential questions that CEOs should be asking their CISOs. He explores the importance of effective communication between technical and business perspectives, the need for investment in cybersecurity with clear ROI, and the significance of understanding risks and setting priorities.
The conversation also delves into the importance of business resilience, managing third-party risks, and preparing for future threats in the ever-evolving cybersecurity landscape. The episode emphasizes the need for CISOs to articulate their strategies in business terms to align with corporate goals and secure necessary resources.
Subscribe for more episodes of Cybersecurity Vault!
Chapters:
00:00 Introduction to Cybersecurity Questions
02:06 Importance of CEO-CISO Communication
05:03 Investment and ROI in Cybersecurity
08:17 Establishing Cybersecurity Priorities
11:12 Identifying the Biggest Risks
14:24 Understanding the Risk Register
15:41 Crafting a Compelling Risk Narrative
18:21 Blind Spots in Cybersecurity Awareness
21:27 Understanding Accepted vs. Unknown Risks
24:29 The Importance of Documentation in Risk Management
25:22 Business Resilience and Recovery Planning
27:52 Engaging Third-Party Vendors in Cybersecurity
31:09 Cybersecurity as a Business Advantage
34:44 Future Threats and Technological Advancements
38:42 Translating Cybersecurity into Business Language
40:51 The Impact of CISO Responses on Business Outcomes
Wil’s LinkedIn Profile: https://www.linkedin.com/in/wilklu/
9 CISO Questions LinkedIn Post: https://www.linkedin.com/feed/update/urn:li:activity:7394720767416107008
Keyboard Samurai Podcast: https://www.youtube.com/@KeybdSamurai
Website: https://www.wilklu.me/podcast
Follow Matthew on
· LinkedIn: https://www.linkedin.com/in/matthewrosenquist/
· SubStack: https://substack.com/@matthewrosenquist
Visit Cybersecurity Insights at https://www.cybersecurityinsights.us
Subscribe to the Cybersecurity Insights channel: https://www.youtube.com/CybersecurityInsights
The post 9 Cybersecurity Questions that Define a CISO appeared first on Security Boulevard.
Forget Predictions: True 2026 Cybersecurity Priorities From Leaders
Security leaders chart course beyond predictions with focus on supply chain, governance, and team efficiency.
The post Forget Predictions: True 2026 Cybersecurity Priorities From Leaders appeared first on SecurityWeek.
Aembit Announces Agenda and Speaker Lineup for NHIcon 2026 on Agentic AI Security
Cyber Fraud Overtakes Ransomware as Top CEO Concern: WEF
Ransomware remains the biggest concern for CISOs in 2026, according to WEF’s Global Cybersecurity Outlook 2026 report.
The post Cyber Fraud Overtakes Ransomware as Top CEO Concern: WEF appeared first on SecurityWeek.
Cyber Insights 2026: What CISOs Can Expect in 2026 and Beyond
Here we examine the CISO Outlook for 2026, with the purpose of evaluating what is happening now and preparing leaders for what lies ahead in 2026 and beyond.
The post Cyber Insights 2026: What CISOs Can Expect in 2026 and Beyond appeared first on SecurityWeek.
2026년 CISO가 반드시 피해야 할 8가지 보안 실수
사이버 보안 리더는 조직의 안전을 지키기 위해 고려해야 할 요소가 매우 많다. 다만 그중에는 다른 사안보다 더 두드러지게 중요하거나, 반대로 아직 충분히 주목받지 못한 과제도 존재한다.
새해를 맞아 2026년 CISO가 결코 소홀히 해서는 안 될 핵심 요소 6개를 짚어보았다.
AI 에이전트 확산 속 아이덴티티 통제 소홀
기업이 자동화와 효율성을 활용하기 위해 AI 에이전트 도입을 본격화하면서, 관련 기술은 빠른 속도로 확대되고 있다. 그랜드뷰리서치에 따르면 전 세계 AI 에이전트 시장 규모는 2024년 54억 달러로 추산됐으며, 2030년에는 503억 1,000만 달러까지 성장할 것으로 전망된다.
AI 에이전트 활용이 늘어나면서 기업은 새로운 사이버 보안 과제에 직면하고 있다. 특히 아이덴티티 통제 측면에서의 부담이 크다. 아이덴티티 스푸핑이나 과도한 권한 부여가 대표적인 위협이다. 사이버 범죄자는 프롬프트 인젝션이나 악성 명령을 활용해 에이전트를 악용하고, 보안 통제를 우회해 시스템과 애플리케이션에 무단 접근할 수 있다.
PwC의 사이버·데이터·기술 리스크 부문 부책임자인 모건 아담스키는 AI 에이전트를 포함한 아이덴티티를 제대로 관리하면, 누가 무엇을 할 수 있는지를 기계 속도로 통제할 수 있다고 설명했다.
아담스키는 공격자가 점점 더 침입이 아닌 로그인 방식으로 접근하고 있으며, AI 에이전트가 실제로 시스템과 데이터를 변경하는 단계에 이르렀다고 분석했다. 그는 리더가 놓쳐서는 안 될 핵심으로 모든 사람, 워크로드, 에이전트를 관리 대상 아이덴티티로 취급하는 점을 꼽았다. 각각에 개별 계정을 부여하고, 피싱에 강한 다중요소인증을 적용하며, 필요한 최소 권한만 필요한 기간 동안 부여하고, 비밀번호나 키를 자동으로 변경하는 체계를 갖춰야 한다는 설명이다. 아울러 비정상적인 권한 변경이나 세션 탈취 여부를 지속적으로 모니터링해야 한다고 강조했다.
아담스키는 기업이 통제력을 잃지 않으면서도 민첩하게 대응하려면, 일상적인 업무 흐름에 AI 에이전트 거버넌스를 내재화해야 한다고 설명했다. 예를 들어 관리자에게 하드웨어 기반 다중요소인증을 의무화하고, 상승된 권한은 기본적으로 만료되도록 설정하며, 신규 에이전트는 각각의 정책을 가진 애플리케이션으로 등록하는 방식이 필요하다고 언급했다.
글로벌 기술 리서치·자문 기업 ISG의 디렉터 제이슨 스타딩은 AI 에이전트와 AI 플랫폼에 대한 아이덴티티 및 접근 통제가 CISO에게 가장 중요한 우려 영역 중 하나라고 평가했다. 그는 현재 AI 관련 권한과 접근 권한은 많은 영역에서 여전히 블랙박스에 가깝다며, 향후 몇 년간 이 분야에서 투명성과 통제를 강화하기 위한 도구와 방법을 도입하려는 움직임이 본격화될 것이라고 전망했다.
공급망 리스크 관리 미흡
디지털 비즈니스 확산과 글로벌 시장에서의 공급망 복잡성 증가는 기업의 공급망을 주요 위험 영역으로 만들고 있다. 공급망은 이미 많은 기업에서 사이버 보안 리스크가 빠르게 커지고 있는 분야다.
이 문제는 특히 제조, 유통, 물류 산업에서 더욱 중요하다. 금속 제품과 부품을 공급하는 AMFT의 CTO 그렉 젤로는 2026년에 복잡한 공급망과 제조 환경에서의 사이버 보안을 간과하는 CISO는 치명적인 결과에 직면할 수 있다고 설명했다.
젤로는 현대 제조 환경이 더 이상 단일 공장에 국한되지 않는다고 분석했다. 상호 연결된 공급업체, 사물인터넷 기반 설비, 클라우드 중심 생산 시스템이 얽힌 구조로 진화하면서, 하나의 취약한 연결고리만으로도 전체 운영이 마비될 수 있는 광범위한 공격 표면이 형성됐다는 설명이다.
최근 발생한 사건은 이러한 위험을 분명히 보여준다. 젤로에 따르면 2025년 9월 재규어 랜드로버는 공급망을 겨냥한 사이버 공격을 받아 영국, 슬로바키아, 인도, 브라질 전역에서 수주 동안 생산이 중단됐고, 추정 피해액은 25억 달러에 달했다. 그는 이 침해 사고가 수백 개 협력사로 확산되며 구조조정과 파산으로 이어졌다고 설명했다. 이는 단순한 IT 장애가 아니라, 글로벌 제조업이 얼마나 깊이 상호 의존적인지를 드러낸 운영 위기였다고 평가했다.
공격자는 로봇, 조립 라인, 품질 검사 등을 제어하는 운영기술(OT) 시스템을 점점 더 많이 노리고 있다. 생산을 멈추게 하면 기업이 신속하게 몸값을 지불할 수밖에 없다는 점을 악용하고 있다는 설명이다.
젤로는 재무적 손실을 넘어 지식재산권 탈취, 규제 처벌, 국가 안보 문제까지 위험이 확대된다고 지적했다. 그는 CISO에게 주는 교훈은 분명하다며, 전통적인 경계 기반 보안은 이미 한계에 도달했다고 설명했다. 복잡한 공급망을 보호하려면 IT와 OT 전반에 걸친 제로 트러스트 아키텍처 적용, 펌웨어와 소프트웨어 업데이트를 포함한 제3자 리스크의 지속적 모니터링, 핵심 시스템을 격리하기 위한 신속한 패치와 세분화, 공급업체와 계약자를 포함한 사고 대응 훈련이 필요하다고 강조했다.
지정학적 긴장에 대한 과소평가
CISO가 조직을 외부와 내부 위협으로부터 보호하는 데 지나치게 집중한 나머지 지정학적 긴장을 놓치기 쉽다. 혹은 이러한 요소를 자사 사이버 보안 이슈와 직접적인 관련이 없다고 판단해 중요성을 낮게 평가할 수도 있다. 그러나 어느 쪽이든 이는 중대한 판단 오류로 이어질 수 있다.
글로벌 기술 리서치·자문 기업 ISG의 디렉터 제이슨 스타딩은 조직의 사이버 회복탄력성 계획에 시스템적 시나리오를 반영하는 것이 매우 중요하다고 설명했다. 여기에는 비즈니스에 영향을 미칠 수 있는 글로벌 정세 변화와 지정학적 갈등도 반드시 포함돼야 한다는 것이다.
스타딩은 기업의 비즈니스와 자산에 영향을 줄 수 있는 침해 지표를 제공하기 위해 산업별 맞춤형 위협 인텔리전스에 대한 요구도 커지고 있다고 언급했다. 그는 이러한 위협 가운데 일부는 악의적인 국가 행위자로부터 비롯되는 고도 지속 공격과 연관될 수 있다고 설명했다.
IT 컨설팅 기업 노스도어의 최고상업책임자(Chief Cmmercial Officer) AJ 톰슨은 사이버 보안과 지정학의 결합이 이미 현실로 자리 잡았다고 평가했다. 그는 국가 행위자가 주도하는 사이버 공격이 핵심 인프라와 글로벌 공급망을 겨냥한 더 큰 분쟁의 일부라고 설명했다. 지정학적 인텔리전스를 위협 모델링에 반영하지 않으면, 조직은 파급력이 큰 국가 지원 사이버 공격에 과도하게 노출될 수 있다고 지적했다.
아울러 톰슨은 의도치 않게 이러한 지정학적 사건에 연루될 경우, 규제 측면과 기업 평판 측면에서 모두 심각한 후과를 초래할 수 있다고 설명했다.
조직의 클라우드 활용 통제 부재
클라우드 서비스 사용이 계속 확대되면서, 이에 수반되는 보안과 개인정보 보호 위험도 함께 커지고 있다. CISO가 이 영역을 소홀히 할 경우 조직은 각종 사이버 공격에 그대로 노출될 수 있다.
글로벌 기술 리서치·자문 기업 ISG의 디렉터 제이슨 스타딩은 클라우드 서비스와 AI 도구가 서로 긴밀하게 결합돼 활용되는 경우가 많다는 점에서 이 문제가 더욱 중요하다고 설명했다. 그는 역할과 책임에 연계된 적절하고 현대적인 보안 인식 교육이 핵심이며, 현재 업무 환경 전반에 확산된 AI 도구와 기술 사용까지 고려해야 한다고 언급했다.
스타딩은 클라우드 관리자와 엔지니어를 대상으로 한 올바른 클라우드 보안 관행과 절차에 대한 교육이 부족한 경우가 많다고 지적했다. 또한 클라우드 팀 다수가 보안 도구 도입과 활용 측면에서 개선을 시도하고 있지만, 실제로는 많은 조직이 클라우드 보안을 위해 투자한 도구를 충분히 활용하지 못하고 있다고 설명했다.
IT 컨설팅 기업 노스도어의 최고상업책임자 AJ 톰슨은 멀티클라우드 환경 확산과 함께 전통적인 보안 경계는 이미 사라졌다고 분석했다. 그는 사후 대응 중심의 클라우드 보안에 의존하는 조직은 정교한 위협을 놓치기 쉽다고 지적했다.
톰슨은 사전 대응형 클라우드 보안 태세 관리(CSPM)와 명확한 사용자 보안 가이드라인이 비용이 큰 침해 사고와 운영 중단을 예방하는 데 핵심적인 단계라고 설명했다. 복잡한 클라우드 환경에서 인적 오류로 인한 위험을 최소화하려면, 안전한 사용자 행동을 지속적으로 조직 문화에 내재화해야 한다고 강조했다.
강화되는 규제 환경에 대한 대응 부족
금융 서비스나 헬스케어처럼 규제가 엄격한 산업에 속한 일부 기업은 오래전부터 금융정보보호법(GLBA)이나 의료정보보호법(HIPAA)과 같은 데이터 보안·프라이버시 규제를 준수해야 했다.
그러나 최근에는 거의 모든 산업이 전 세계적으로 증가하는 데이터 프라이버시 및 보호 법규를 준수해야 하는 상황이다. 이러한 규제를 간과하거나 중요성을 낮게 평가할 경우, 벌금과 추가적인 제재로 이어질 수 있다.
스타딩은 규제가 많은 조직이 컴플라이언스 활동으로 인해 상당한 추가 부담을 안고 있으며, 이로 인한 피로감도 적지 않다고 설명했다. 다만 최근 몇 년간 CISO 역할이 컴플라이언스에 대한 책임과 권한까지 확대된 만큼, 이를 소홀히 하거나 과소평가할 여지는 없다고 강조했다.
특히 글로벌 기업의 CISO는 최신 규제 동향을 면밀히 파악해야 한다. 톰슨은 영국과 유럽에서 사이버 보안 규제 환경이 빠르게 강화되고 있다고 설명했다. 그는 GDPR(General Data Protection Regulation)과DORA(Digital Operational Resilience Act)과 같은 프레임워크가 문서화된 통제뿐 아니라, 실증적으로 검증 가능한 사이버 보안 효과를 조직에 요구하고 있다고 분석했다.
톰슨은 규제 당국이 사이버 보안과 운영 회복탄력성이 단순한 규정 준수 항목이 아니라, 비즈니스 프로세스 전반의 모든 계층에 깊이 내재화돼 있는지를 확인하려 한다고 설명했다.
그는 제3자 리스크 관리 역시 그에 못지않게 중요하다고 지적했다. 공급망이 점점 더 복잡하고 분산될수록 외부 제공업체로 인한 취약점은 심각한 규제 및 보안 책임으로 이어질 수 있다는 것이다. 이러한 규제 요구를 보안 전략에 선제적으로 반영하지 않을 경우, 막대한 재무적 제재는 물론 운영 중단과 장기적인 평판 훼손으로 이어질 수 있다고 경고했다.
AI 챗봇 도입에 따른 법적 책임 인식 미흡
사이버 보안 보험 제공업체 코얼리션의 수석 연구원 다니엘 우즈는 AI 챗봇이 데이터 프라이버시 측면에서 새롭게 부상한 위험 요소라고 설명했다. 코얼리션이 약 200건의 프라이버시 관련 청구 사례와 5,000개 기업 웹사이트를 분석한 결과, 전체 청구의 5%가 챗봇 기술을 겨냥한 것이었다.
우즈는 이들 청구가 AI 도구가 등장하기 훨씬 이전에 제정된 주(州) 도청 방지법을 근거로, 고객 대화를 불법적으로 가로챘다고 주장한 사례라고 설명했다. 모든 챗봇 관련 청구는 대화 시작 시 해당 대화가 녹음되고 있다는 사실을 고지했어야 한다는 동일한 구조를 따랐다는 분석이다.
해당 청구는 수십 년 전에 제정된 플로리다 통신 보안법 위반을 주장한 것이었다고 우즈는 전했다. 그는 전체 웹사이트 가운데 약 5%가 챗봇 기술을 도입하고 있으며, 이 비율이 챗봇을 중심으로 제기된 웹 프라이버시 청구 비중과 정확히 일치한다고 설명했다.
우즈는 IT 산업과 금융 산업에서 챗봇 활용이 특히 두드러졌다고 설명했다. 해당 산업 웹사이트의 각각 9%와 6%가 챗봇을 사용하고 있었으며, 향후 챗봇 활용이 늘어날 가능성이 큰 만큼 관련 청구 역시 증가할 수 있다고 전망했다.
그는 챗봇을 잘못 설계하거나 운영할 경우의 위험으로, 프롬프트 인젝션과 같은 기법을 통해 시스템이 쉽게 조작될 수 있다는 점을 꼽았다. 이러한 방식으로 고객 데이터가 유출된 사례가 이미 수십 차례 문서화돼 있다고 경고했다.
클라우드 보안 체계 관리 공백
이제는 거의 모든 기업이 최소한 일부 운영을 클라우드 서비스에 의존하고 있다. 이러한 서비스의 보안을 소홀히 하는 것은 문제를 자초하는 것과 다름없다.
PwC의 아담스키는 클라우드와 SaaS 확산이 계속될 것이라며, 아이덴티티, 암호화, 로깅, 외부 통신을 위한 가드레일을 갖춘 표준 랜딩 존을 사전에 설계해야 한다고 설명했다. 또한 정책을 코드로 구현해 규정 준수 설정이 기본값이 되도록 하는 접근이 필요하다고 언급했다.
아담스키는 CISO가 자산을 지속적으로 파악하고, 설정 오류를 식별하며, 이상 행위를 탐지하고, 필요할 경우 자동으로 조치할 수 있는 도구를 활용해야 한다고 설명했다.
그는 모든 방향에서 쏟아지는 경고에 일일이 대응하는 방식으로는 멀티클라우드 확산과 아이덴티티 중심 공격을 따라가기 어렵다고 지적했다. 클라우드 전반의 신호를 연계하고 경고 소음을 줄이기 위해 자동화와 AI를 활용해 보안 관제 센터를 현대화해야 한다고 강조했다.
사이버 보안에서 인적 요인 경시
다양한 사이버 보안 도구와 서비스가 구축돼 있다 보니, 사이버 보안에서 사람의 역할을 간과하기 쉽다. 그러나 이러한 인식은 여러 형태의 보안 사고로 이어질 수 있다.
로펌 CM로의 기술·사이버 보안 파트너인 베스 펄커슨은 실제 경험상 보안 침해의 직접적인 원인은 대부분 인적 오류라고 설명했다. 그는 대체로 누군가가 사기에 속아 악성 코드가 유입되는 통로를 열게 된다고 분석했다.
사람은 메시지에 즉각 반응하거나 문서를 열어보고 싶어 하는 경향이 있으며, 이러한 행동이 문제를 키운다. 펄커슨은 근본적인 해법은 더 많은 기술 도입이 아니라, 직원이 자신의 기기 접근이나 정보 제공 요청에 대해 거절할 수 있도록 돕는 교육에 있다고 설명했다.
그는 프린터나 팩스 장비가 네트워크에 연결돼 있다는 사실을 잊고 보안 설정을 적용하지 않거나, 네트워크에서 분리하지 않는 것 역시 대표적인 인적 오류 사례라고 언급했다.
또 다른 문제로는 이미 도입돼 있거나 사용 가능한 보안 기술을 제대로 활용하지 않는 점을 꼽았다. 펄커슨이 최근 담당한 소송 사례에서는 결제카드산업 데이터 보안 표준(PCI DSS)에 따라 파일 무결성 관리 소프트웨어를 사용하고 있다고 주장했지만, 실제로는 경고를 설정하지 않았거나 경고를 무시한 경우가 포함돼 있었다.
펄커슨은 아무리 강력한 보안 소프트웨어를 갖추고 있더라도, 이를 올바르게 설정하고 지속적으로 관리하지 않으면 의미가 없다고 지적했다.
dl-ciokorea@foundryco.com

8 things CISOs can’t afford to get wrong in 2026
Cybersecurity leaders have a lot to consider when trying to keep their organizations safe. But some things stand out more than others — or might be under the radar.
As a new year dawns, here are some things CISOs should avoid falling short on in 2026.
Get complacent about identity controls in the face of rising AI agents
The deployment of AI agents is growing rapidly, as enterprises look to take advantage of the automation and efficiency they offer. The global AI agents market size was estimated at $5.40 billion in 2024 and is projected to reach $50.31 billion by 2030, according to Grand View Research.
The increased use of AI agents presents a cybersecurity challenge for enterprises, especially in terms of identity controls. Potential threats include identity spoofing and over-permissioned access. Cyber criminals can exploit agents through prompt injection or malicious instructions to bypass controls and gain unauthorized access to systems and applications.
“Get identity — including AI agents — right and you control who can do what at machine speed,” says Morgan Adamski, deputy leader for cyber, data, and tech risk at consulting firm PwC.

How to Avoid Phishing Incidents in 2026: A CISO Guide
CISO Communities – Cybersecurity’s Secret Weapon
Closed CISO communities act as an information exchange, advice center, pressure valve, and safe haven from critical oversight.
The post CISO Communities – Cybersecurity’s Secret Weapon appeared first on SecurityWeek.
Building Up to Code: Cybersecurity Risks to the UK Construction Sector
PinnacleOne recently partnered with a leading UK construction company to analyze the cybersecurity risks shaping the sector in 2025. This new report explores how evolving threats intersect with the construction industry’s unique challenges, including tight project timelines, complex supply chains, sensitive data, and high-value transactions. Aimed at CISOs and security leaders, it provides actionable guidance to balance opportunity with resilience, ensuring construction firms stay secure while building the nation’s future.
Report Overview
The UK construction sector is a vital part of the national economy, contributing approximately 5.4% of GDP and employing around 1.4 million people. However, this critical industry is increasingly the target of cyber threat actors seeking financial gains and espionage.
PinnacleOne recently collaborated with a UK construction company to review these trends and bolster their cyber strategy. In a new report, PinnacleOne synthesizes key recommendations for construction sector cyber strategy to help CISOs stay ahead of the threat.
The construction industry’s core characteristics make it a uniquely enticing target for cyber threat actors:
- Money: Construction companies frequently handle high-value transactions, making them susceptible to financial fraud via business email compromise (BEC). Attackers can achieve significant gains by intercepting even a single large transaction.
- Sensitive Data: Construction firms often possess a variety of sensitive data, including personal, sensitive personal, and client data, some of which is regulated by mandates like the Building Safety Act. This data is valuable to both threat actors and regulators, incentivizing attacks and regulatory scrutiny.
- Time Sensitivity: Construction projects operate on tight schedules and budgets. Cyberattacks causing delays can lead to reputational damage and liquidity issues, as rapid payment for invoices is often mandated.
- Broad Attack Surface: The industry’s reliance on numerous contractors, subcontractors, suppliers, and a wide array of IoT/OT devices creates multiple avenues for threat actor infiltration, presenting significant cybersecurity challenges.
For construction companies, cyber risk is inherently business risk. Cyber incidents can directly impact project timelines, budgets, and even the safety and structural integrity of the built environment. The interconnected nature of the construction ecosystem means that attackers can leverage any exposed point of entry. This, combined with slim profit margins and inconsistent cybersecurity investments, elevates the risk profile for the entire industry.
By adopting a proactive, risk-based cybersecurity approach, construction firms can strengthen their resilience and protect operational continuity and client trust. Read the full report here.

Beyond the Buzz: Is Your Security Platform Delivering AI Value or Just Hype?
The era of evaluating AI on its potential is over. For CISOs, the only conversation about AI worth having in cybersecurity is about proven performance. The executive mandate is clear – every leader is being asked how they are using AI to get better, faster, and more profitable. For CISOs, this pressure transforms the conversation from if they should adopt AI to how to do it right. The right AI investment is one that strengthens the business by delivering faster threat containment, creating more efficient security teams, and providing a quantifiable reduction in overall risk.
In a landscape where every vendor claims AI supremacy, the measure of a platform’s worth is not its model size or an arbitrary LLM benchmark, but its ability to deliver on those business imperatives. It’s time to move beyond the hype and focus on the results of implementing AI for security operations.
Security teams face unprecedented pressure from a growing volume, complexity, and speed of cyberattacks – it’s more noise, more work, more risk. Tried-and-true security methods and manual workflows are struggling to keep pace, resulting in overwhelmed analysts, overlooked alerts, and greater organizational risk. In response, security teams not only need new tools, but also a fundamental shift in how they approach security.
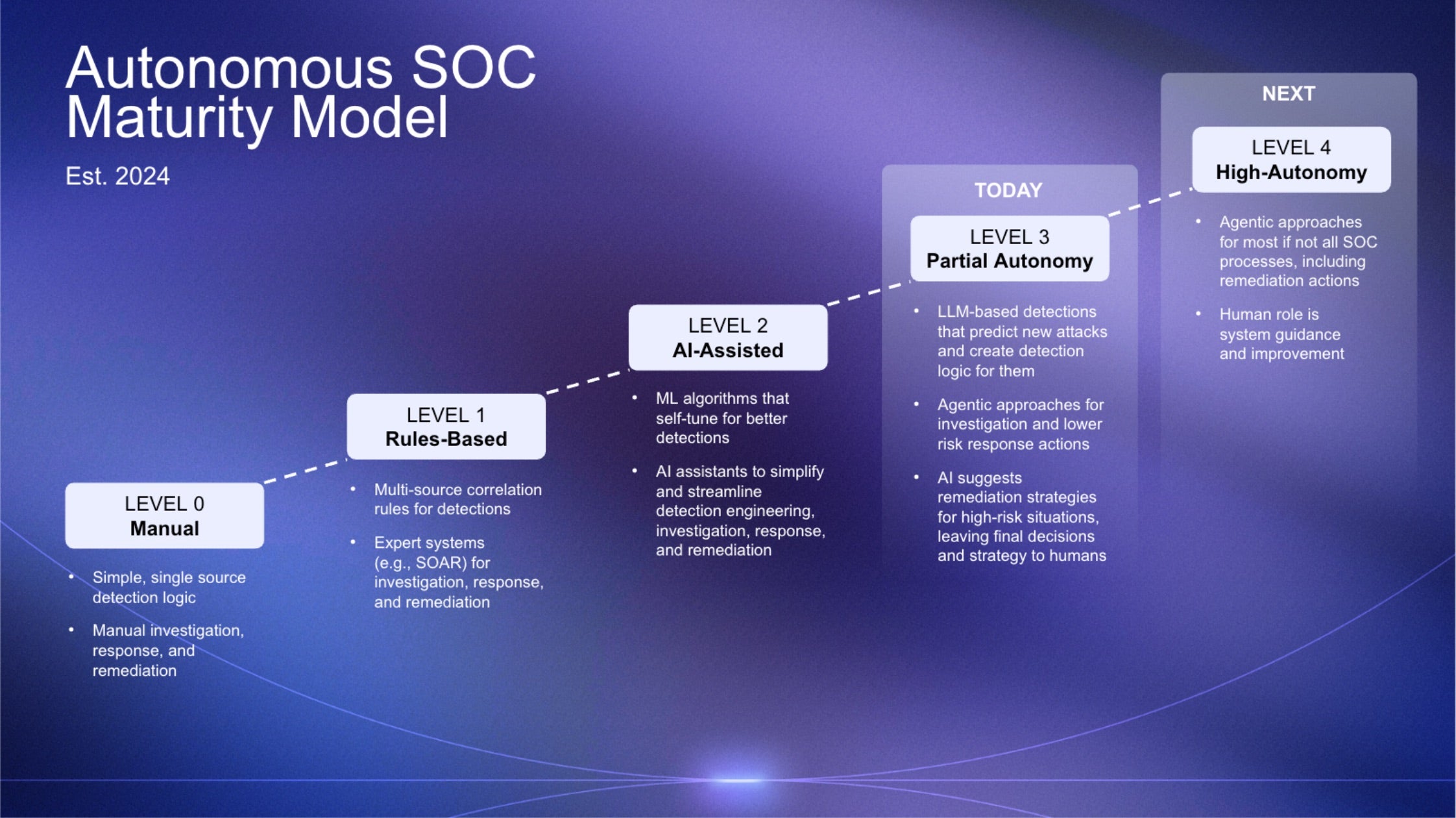
To guide this transformation, SentinelOne created the Autonomous SOC Maturity Model, a framework showing how advanced generative and agentic AI are essential to augment human expertise, analyze data, and automate workflows to counter threats at machine speed.
Discerning Genuine AI Value from Market Noise
For CISOs, the challenge lies in cutting through the deafening market noise to identify actual AI-driven value. True AI value manifests when organizations can accelerate their threat detection and response times while reducing critical metrics such as MTTD and MTTR. By automating routine and repetitive tasks, AI enables experienced analysts to focus their expertise on proactive threat hunting and deeper investigation.
Organizations implementing AI in their security programs aim for substantial gains in efficiency, demonstrably lower risk, and a reduction in the probability and severity of security incidents. Tools driven by AI become essential to security teams when they improve the analyst workflow and provide security professionals of all levels with amplified capabilities. Most people are now familiar with generative AI: tools that help assist you with work.
In security, that means generating readable content from raw data (incident summaries, queries, investigative insights) to help an analyst understand what’s happening faster. It’s about speeding up comprehension. Agentic AI goes further. This isn’t about just providing assistance, it’s about systems that can do the work. Advanced AI systems, particularly those that leverage agentic capabilities, can now handle data recall and correlation, and even initiate decision-making steps with precision, enabling teams to respond faster and more accurately.
The most effective AI complements and amplifies human expertise and vice versa, driving towards a more resilient security posture. Ultimately, the goal of a well-designed AI system is where the human role is elevated to strategic oversight and supervision of AI actions, applying their expertise and deep institutional knowledge of tools and processes in a more effective way. The role of the analyst shifts from manually triaging and investigating a queue of alerts to applying their expertise for the supervision of an autonomous system. AI agents can reason through multi-step tasks, decide on next actions, prioritize what matters most, and move workflows forward autonomously, while maintaining transparency and keeping a human in the loop.
Navigating the AI Maze: What CISOs Should Look For In AI Tools
Navigating the AI vendor landscape is challenging. Use this checklist to prioritize solutions that deliver smarter, faster, and more integrated security, ensuring you invest in true value, not just hype.
 1. Does It Deliver Unified, Actionable Visibility?
1. Does It Deliver Unified, Actionable Visibility?
- Can the AI break down data silos by ingesting and correlating intelligence from my entire security landscape, including endpoints, cloud workloads, identities, firewall, SASE, and threat intelligence feeds?
- Does it provide a single, unified view to turn disparate data points into actionable insights?
 2. Does It Support Open Standards for Better Detection?
2. Does It Support Open Standards for Better Detection?
- Does the platform adopt open standards for data normalization, like the Open Cybersecurity Schema Framework (OCSF)?
- Will this result in more accurate, context-rich threat detection by ensuring all my security tools speak the same language?
 3. Does It Drive Action and Containment?
3. Does It Drive Action and Containment?
- Does the AI move beyond simply identifying issues to actively helping my team contain them?
- Can it transform raw telemetry into clear intelligence that drives automated response actions or provides prioritized, guided pathways to remediation?
 4. Does It Empower Analysts and Foster Autonomy?
4. Does It Empower Analysts and Foster Autonomy?
- Is the AI designed to simplify complexity and empower analysts of all skill levels, reducing alert fatigue and freeing up human talent for the most critical threats?
- Does it help my team move towards a more autonomous operational model?
 5. Does It Act as a True Force Multiplier?
5. Does It Act as a True Force Multiplier?
- Does the platform leverage both generative AI (for insights and understanding) and agentic AI (for autonomous actions and decision-making)?
- Is there clear evidence that the AI continuously learns, adapts, and enhances the capabilities and efficiency of my security team?
From Anecdote to Evidence: Outcomes of AI Deployments
Confronted with these challenges and choices, how can security leaders separate credible AI solutions from the hype? The answer lies in data-driven evaluations and an honest look at real-world implementations. Security leaders should evaluate solutions that demonstrate how advanced AI capabilities translate into measurable security and business outcomes.
A recent IDC white paper, “The Business Value of SentinelOne Purple AI” [1] offers precisely this kind of quantitative evaluation. IDC conducted in-depth interviews with organizations using SentinelOne’s Purple AI, a solution that leverages cutting-edge generative AI and agentic AI to accelerate workflows like investigation, hunting, triage, and response.
The findings from these real-world deployments provide compelling insights into the tangible benefits AI can deliver when aligned with the needs of security leaders for speed, efficiency, and risk reduction. With the Singularity Platform and Purple AI, customers experienced significant improvements:
- 63% faster to identify and 55% faster to resolve security threats, meaning incidents are contained in minutes, not hours.
- Security teams became 38% more efficient, allowing them to support 61% more endpoints per team member.
- A 338% three-year ROI with a payback period of just four months.
These customer outcomes are attributed to Purple AI’s capabilities, including natural language querying, automated event summarization, suggested next investigation steps, and the automation provided by its agentic AI features like Auto-Triage. Organizations found that Purple AI enabled them to enhance their security operations, become more operationally efficient, and improve overall security outcomes, reducing operational risk and increasing business confidence.
Don’t just take our word for it – hear from existing Purple AI customers featured in the report about how they:
- Enhanced Security Operations: “Being able to ask a native question with SentinelOne Purple AI without needing to know specific keywords or learn new syntax is a massive force multiplier, saving us a lot of time.”
- Improved Operational Efficiency: “With Purple AI, we don’t have to scale our security expert team. At this point, we are avoiding hiring and we’ll be able to leverage our existing application teams.”
- Realized Risk Reduction: “Having Purple AI has been instrumental in improving our operational maturity. It allows us to conduct investigations with specificity, making informed decisions around security posture and ensuring nothing sneaks into our environment.”
- Increased Business Confidence: “In terms of innovation, I think it will potentially help us take more risks in the future because we’ll have more confidence.”
Beyond the Buzz: Judge for Yourself
When AI – incorporating both generative and agentic strengths – is thoughtfully implemented to address the demands of security teams, it moves the needle for security operations in a very real and measurable way. The key is to look past the marketing slogans and focus on validated outcomes. Generative and agentic AI will undoubtedly shape the future of the security operations center, and CISOs must move from cautious curiosity to strategic adoption.
Is AI a distraction or your next competitive advantage? Get the definitive answer in our on-demand webinar, Beyond the Buzz: Separating AI Hype from Security Outcomes. We present IDC’s quantitative evaluation of real AI implementations and feature insights from current Purple AI customers, IDC Research Vice President Chris Kissel, and SentinelOne’s Senior Director of Product Management Adriana Corona.
To learn more about how to transform security operations with Purple AI’s revolutionary approach to the Autonomous SOC, visit our web page or request a demo from a product expert.
[1] IDC Business Value White Paper, sponsored by SentinelOne, The Business Value of SentinelOne’s Purple AI, #US53337725, July 2025

A preview of the upcoming Black Hat conference…
EXECUTIVE SUMMARY:
One of the leading cyber security conferences globally, Black Hat USA is where intellect meets innovation. The 2024 event is taking place from August 3rd – 8th, at the Mandalay Bay Convention Center in Las Vegas.
The conference is highly regarded for its emphasis on cutting-edge cyber security research, high-caliber presentations, skill development workshops, peer networking opportunities, and for its Business Hall, which showcases innovative cyber security solutions.
Although two other cyber security conferences in Las Vegas will compete for attention next week, Black Hat is widely considered the main draw. Last year, Black Hat USA hosted roughly 20,000 in-person attendees from 127 different countries.
Event information
The Black Hat audience typically includes a mix of cyber security researchers, ethical hackers, cyber security professionals – from system administrators to CISOs – business development professionals, and government security experts.
On the main stage this year, featured speakers include Ann Johnson, the Corporate Vice President and Deputy CISO of Microsoft, Jen Easterly, Director of the Cybersecurity and Infrastructure Security Agency (CISA), and Harry Coker Jr., National Cyber Director for the United States Executive Office of the President.
The Black Hat CISO Summit, on Monday, August 5th through Tuesday, August 6th, caters to the needs and interests of CISOs and security executives. This track will address topics ranging from the quantification of cyber risk costs, to supply chain security, to cyber crisis management.
Professionals who are certified through ISC2 can earn 5.5 Continuing Professional Education (CPE) credits for CISO Summit attendance.
Why else Black Hat
- Access to thousands of industry professionals who have similar interests, who can discuss challenges and who can provide new product insights.
- Access to the latest cyber research, which may not yet be widely available, helping your organization prevent potential attacks before they transform into fast-moving, large-scale issues.
- Cyber security strategy development in partnership with experts and vendors.
- Check Point is offering exclusive 1:1 meetings with the company’s cyber security executives. If you plan to attend the event and would like to book a meeting with a Check Point executive, please click here.
- Community building. Connect with others, collaborate on initiatives and strengthen everyone’s cyber security in the process.
Must-see sessions
If you’re attending the event, plan ahead to make the most of your time. There’s so much to see and do. Looking for a short-list of must-see speaking sessions? Here are a handful of expert-led and highly recommended talks:
- Enhancing Cloud Security: Preventing Zero-Day Attacks with Modernized WAPs: Wednesday, August 7th, at 11:00am, booth #2936
- How to Train your AI Co-Pilot: Wednesday, August 7th, at 12:30pm, booth #2936
- Key Factors in Choosing a SASE Solution: Thursday, August 8th, at 10:45am, booth #2936
Further details
Be ready for anything and bring the best version of yourself – you never know who you’ll meet. They could be your next software developer, corporate manager, business partner, MSSP, or cyber security vendor. Meet us at booth #2936. We can’t wait to see you at Black Hat USA 2024!
For more event information, click here. For additional cutting-edge cyber security insights, click here. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
The post A preview of the upcoming Black Hat conference… appeared first on CyberTalk.
SEC charges against SolarWinds largely dismissed
EXECUTIVE SUMMARY:
In a landmark case, a judge dismissed most of the charges against the SolarWinds software company and its CISO, Timothy Brown.
On July 18th, U.S. District Judge Paul Engelmayer stated that the majority of government charges against SolarWinds “impermissibly rely on hindsight and speculation.”
The singular SEC allegation that the judge considered credible concerns the failure of controls embedded in SolarWinds products.
For its part, SolarWinds has consistently maintained that the SEC’s allegations were fundamentally flawed, outside of its area of expertise, and a ‘trick’ designed to allow for a rewrite of the law.
Why it matters
For some time, the SEC has pursued new policies intended to hold businesses accountable for cyber security practices; an understandable and reasonable objective.
In this instance, the SEC said that claims made to investors in regards to cyber security practices had been misleading and false – across a three year period.
The SEC’s indictment also mentioned falsified reports on internal controls, incomplete disclosure of the cyber attack, negligence around “red flags” and existing risks, and more.
But what caught the attention of many in the cyber security community was that, in an unprecedented maneuver, the SEC aimed to hold CISO Timothy Brown personally liable.
This case has been closely watched among cyber security professionals and was widely seen as precedent-setting for future potential software supply chain attack events.
Timothy Brown’s clearance
In the end, the court ruling does not hold CISO Timothy Brown personally liable for the breach.
“Holding CISOs personally liable, especially those CISOs that do not hold a position on the executive committee, is deeply flawed and would have set a precedent that would be counterproductive and weaken the security posture of organizations,” says Fred Kwong, Ph.D, vice president and CISO of DeVry University.
Despite the fact that this court ruling may loosen some CISO constraints, “you need to be honest about your security posture,” says Kwong.
The remaining claim against the company, which will be scrutinized further in court, indicates that there is a basis on which to conclude that CISOs do have certain disclosure obligations under the federal securities laws.
Further details
The SolarWinds incident, as its come to be known, has cost SolarWinds tens of millions of dollars. In 2023, the company settled a shareholder lawsuit to the tune of $26 million.
A spokesperson for SolarWinds has stated that the company is “pleased” with Judge Engelmayer’s decision to dismiss most of the SEC’s claims. The company plans to demonstrate why the remaining claim is “factually inaccurate” at the next opportunity.
For expert insights into and analyses of the SolarWinds case, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
The post SEC charges against SolarWinds largely dismissed appeared first on CyberTalk.
What CISOs Should Know About Hacking in 2023
The art of cyber crime is in a constant state of flux and evolution. Simply staying on pace with these trends is a significant part of the CISO’s job.
Today’s modern CISO must ensure they are always prepared for the next big trend and remain ahead of adversaries.
As we begin to navigate 2023, the security landscape has transformed from a year ago, let alone a decade ago. The Russian invasion of Ukraine, emerging technologies like Web3 and AI, and new, post-pandemic ways of organizing the workforce have all led to significant shifts in the world of hacking.
In this article, we’ll look at how hacking is different in 2023, some of the key threats CISOs must contend with and some of the best defenses available.
What Does Modern Hacking Look Like?
Before we start, it’s worth noting that even the term “hacker” has undergone some evolution over the years. Once largely associated with hostile actors, many security professionals now refer to themselves as hackers. The term “white hat hacker” also exists; this refers to hackers using the same methods as cyber criminals to carry out ethical tasks like pressure-testing security systems.
So what are the concrete ways hacking has changed today compared to five, ten and even twenty years ago? There are several significant trends to highlight that look set to dominate the cybersecurity conversation in 2023.
A Lower Barrier to Entry
In the past, threat actors needed highly developed skill sets honed over many years. Hacking, especially targeting high-level organizations with valuable assets, wasn’t something just anyone could do — the bar was set high.
Today, with the emergence and growth of DIY hacking kits and services — available in places like the dark web — even fairly low-skilled cyber criminals can inflict damage and successfully commit crimes. This is concerning news because it means the pool of potential attackers is soaring.
Taking Advantage of the Shift to Remote Work
Although the COVID-19 pandemic is now receding, many effects still linger. One of the most notable is the sustained shift to remote working patterns. While more remote work options come with great employee benefits such as work-life balance and productivity, this style of working also carries inherent security risks.
With millions of companies now operating either partially or fully remote, along with escalating levels of cloud adoption, security teams have the challenging task of defending sensitive information and assets. Employees access all this data from a wide range of locations — including unsafe wireless networks and even public places.
Emerging Technologies Will Play a Greater Role
Emerging technologies like blockchain, the internet of things and artificial intelligence are expected to play a more prominent role in our lives in 2023, making them a more attractive target for attackers.
We’ve already seen a number of high-profile attacks on Web3 infrastructures, like the 2022 hacking of the Binance exchange for $570 million. Threat actors can also turn new technologies to their own advantage; for example, by harnessing AI tools to automate their attacks and quickly identify easy targets.
Bigger Targets and Heavyweight Players
The invasion of Ukraine in early 2022 sparked a new era of geopolitics, shifting the cybersecurity landscape. Russia has been targeting critical infrastructure in Ukraine with cyberattacks. As tensions between the West and its adversaries reach the highest point in decades, it’s realistic to expect more such attacks against Western targets.
CISOs at all levels must prepare for attacks by nation-state actors, which could even target assets like regional power grids.
What Will Be the Most Popular Hacking Methods of 2023?
Which techniques will malicious actors use to achieve their goals in 2023? While it’s difficult to predict, we’ll likely see a continuation of recent trends.
- Phishing. Despite — or perhaps because of — its simplicity, phishing remains an extremely effective method for threat actors of all types. Tricking victims into sharing sensitive data, including company information, is a tried-and-tested attack vector that organizations must prepare for with widespread employee education and more robust password policies.
- DDoS attacks. Distributed Denial of Service attacks work by overwhelming the target’s servers with traffic, causing them to crash. In many cases, attackers are using cloud infrastructure to bolster their DDoS attacks.
- Ransomware. This method has been skyrocketing year over year and will probably trend upward in 2023. During an attack, malicious actors seize an organization or individual’s data, encrypt it and demand a ransom for its return. Ransomware can be devastating, leading to enormous financial losses and irreparable reputation damage.
- Targeting missing patches. Many threat actors are actively searching for security patches that organizations have failed to keep up to date. Then, they take advantage of those vulnerabilities.
What Does Defense Against Hacking Look Like in 2023?
As hacking continues to evolve, so do the methods cybersecurity teams are deploying to combat those threats.
Here are some of the key trends in defense against hacking to be aware of in 2023:
Automation and AI
AI is being harnessed by cyber criminals more and more, but when used correctly, it can also be a powerful tool for defense. AI algorithms are excellent at analyzing huge datasets and making accurate predictions about when and where attacks will take place, giving security teams a valuable advantage.
According to research by IBM, companies that use AI and automation to defend against data breaches save an average of $3.05 million compared to those that don’t — a difference of 65.2%.
Secure Cloud Assets
As cloud assets and infrastructure become increasingly popular targets, companies will focus on defending in this area. Stricter security controls, greater enforcement of access requirements and better education and coordination between teams are all excellent places to start.
Make Cybersecurity a Priority
The past few years have seen a growing trend of organizations taking a much more focused approach to cybersecurity with company-wide education policies and growing cyber spending.
As we enter 2023 and beyond, companies look certain to continue along this path, emphasizing security responsibility for everyone in the organization, not just security teams.
The post What CISOs Should Know About Hacking in 2023 appeared first on Security Intelligence.
Bridging the 3.4 Million Workforce Gap in Cybersecurity
As new cybersecurity threats continue to loom, the industry is running short of workers to face them. The 2022 (ISC)2 Cybersecurity Workforce Study identified a 3.4 million worldwide cybersecurity worker gap; the total existing workforce is estimated at 4.7 million. Yet despite adding workers this past year, that gap continued to widen.
Nearly 12,000 participants in that study felt that additional staff would have a hugely positive impact on their ability to perform their duties. More hires would boost proper risk assessment, oversight, patching of critical systems and proper system configuration.
Many factors have contributed to this gap in essential cybersecurity workers. Some of the top reasons the survey identified were a lack of internal promotion opportunities, struggles with turnover and attrition, budget issues and a lack of qualified talent. But what defines “qualified talent” in cybersecurity today?
The industry has two options. The first is to cut the pie by continuing to focus on degree and certification holders. The other is to make a bigger pie by widening the talent pool and offering on-the-job training to applicants with the passion and mindset to succeed.
Looking for Talent in All the Wrong Places?
The term “cybersecurity” has been overly mystified. Does it involve a reclusive hoodie-wearing night owl? A math whiz writing complex code or working with cryptography?
Unfortunately, misconceptions and complexity have built a wall around the industry. This, at least in part, may explain the high percentage of people with university degrees working in cybersecurity fields. In fact, 82% of the workforce have a Bachelor’s or Master’s degree.
That level of formal education may have been necessary in the past, but the industry requires all types of workers right now. The first step to closing that worker gap will be to ensure that the public understanding of “cybersecurity” is demystified. Core skills aren’t coding or highly advanced math; core skills are problem-solving, investigative thinking, dedication and hard work.
The Making of a Cybersecurity Specialist
Recently, the Australian Signals Directorate (ASD) identified that a “cybersecurity specialist” is “just your average person” that can come from varying backgrounds. This is completely true, especially when key cybersecurity tasks today revolve around monitoring, detection and the ability to spot anomalies. Contrary to popular thinking, cybersecurity is not a bunch of blinking lights and super-secret artificial intelligence — though there are elements of that.
The cybersecurity industry could be morphing into a 21st Century version of manufacturing and assembly lines. Yes, there are still skilled labor requirements. But there is still no substitute for “hands-on keyboard” or “taking live fire” during an incident response case. That comes through experience.
Therefore, this begs the question: Who is better suited for a cybersecurity position? Somebody with a high school diploma but has managed computers and IT systems since they were a teenager, making mistakes along the way but solving them with passion and curiosity? Or a person with a cybersecurity degree who read about the field in a book, spending limited time with hands on a keyboard?
Focus on the Person, Not the Paper
Let’s return to the (ISC)2 study. Participants are trending towards practical skills and experience as more important qualifications. Certification, degrees and training are nice, but problem-solving abilities and related work experience are what employers are looking for. Interestingly, certifications are seen to be more valuable for skills growth than a means to jump into a career in cybersecurity.
It almost feels as though there is an elephant in the room: are we considering the right people for cybersecurity jobs, especially for entry-level jobs?
Granted, some positions require a strong mix of experience, paper qualification and/or validation, and years of battle hardening. For instance, a CISO or senior-level SOC analyst will almost certainly have done time in the trenches.
But some positions grant some low-risk, hands-on experience. If an organization finds a candidate with sincere curiosity, problem-solving skills and the appropriate soft skills, their paper qualifications may not matter. Rather, what will determine success is the organization’s ability to train the individual on the necessary tools and the core technical competencies required to complete the job. A curious person with problem-solving skills can figure out the rest. Just do not leave them hanging because they may suffer from burnout.
Training Can Bridge the Gap
Back to the assembly line analogy: Let’s say you are new to the machinery or protocols in a manufacturing shop. If you can be trained, shadow somebody more experienced for a period of time and have the right work ethic you can pick up the skills and excel. It’s the same principle in cybersecurity.
This is how to bridge the gap, especially in the short term. Waiting three to seven years for individuals to complete advanced degrees may no longer be practical, given the high demand. Technologies will change and there is no guarantee of “hands on keyboard” battle scars.
It’s time to start thinking outside the box. Pitch these two scenarios to a hiring manager today:
- Individual A works on IT systems and remotely manages a SIEM. They have no certifications or paper qualifications but have worked like this for a couple of years, come highly referred as a dedicated worker, are dependable and require little oversight.
- Individual B completed a Bachelor’s degree in computer science and a Master’s degree in cybersecurity. They also have completed some basic cybersecurity certifications but have no previous work experience or references.
Based on these surface descriptions, who are you inclined to interview first for a cybersecurity job?
The Pathway to Filling Future Needs
The above example is not a knock on those seeking university degrees or certifications; rather, it is a reality check. If 80% of workers in the industry have university degrees and there are not enough people to meet the need, well, you need to start looking elsewhere to fill the gap. Otherwise, expect retention problems.
For hiring managers, that will mean carefully crafting your requisitions and keeping your expectations in check. These new hires will be your apprentices for a while. Know that if you get them early, reward them with the opportunity and treat them right, you may also be filling a long-term need.
The post Bridging the 3.4 Million Workforce Gap in Cybersecurity appeared first on Security Intelligence.
Unconsidered benefits of a consolidation strategy every CISO should know
Pete has 32 years of Security, Network, and MSSP experience and has been a hands-on CISO for the last 17 years and joined Check Point as Field CISO of the Americas. Pete’s cloud security deployments and designs have been rated by Garter as #1 and #2 in the world and he literally “wrote the book” and contributed to secure cloud reference designs as published in Intel Press: “Building the Infrastructure for Cloud Security: A Solutions View.”
In this interview, Check Point’s Field CISO, Pete Nicoletti, shares insights into cyber security consolidation. Should your organization move ahead with a consolidated approach? Or maybe a workshop would be helpful. Don’t miss Pete Nicoletti’s perspectives.
What kinds of struggles and challenges are the organizational security leaders that you’re working with currently seeing?
Many! As members of the World Economic Forum Council for the Connected World, we drilled into this exact question and interviewed hundreds of executives and created a detailed report. The key findings are: Economic Issues, IoT risks, increase in ransomware, and security personnel shortages all impacting budgets. Given these issues, our council recommended that security spend remain a priority, even in challenging times, since we all know that security incidents cost 10x to 100x verses budgeted expenditures.
How are CISOs currently building out or transitioning their information security programs? What kinds of results are they seeing?
In challenging times, CISO’s are looking hard at their tool set and seeing if there is overlap, or redundant tools, or underutilized tools. CISO’s are also evaluating their “play-books” to ensure that the tools in-use are efficient and streamlined. CISO’s are also keen to negotiate ELA’s that give them lower costs with flexibility to choose from a suite of tools to support the “speed of business.”
Security teams need to be trained and certified on their tools in use, and those budgets are under pressure. All these drivers lead to tool consolidation projects. Our customers are frequently very pleased with the normally mutually exclusive benefits: Costs Savings and better efficacy once a consolidation program is launched.
What are the key considerations for CISOs in deciding on whether or not to consolidate information security solutions? Can CISOs potentially lose capabilities when consolidating security and if so, how can this be addressed, if at all?
Losing features when consolidating is a valid concern, however, typically we find more advantages after consolidation: Lower training costs, higher staff satisfaction, fewer mistakes made, and the real gem: higher security program efficacy. We also see our customers leveraging the cloud and needing to extend their security protections quickly and easily, and our Check Point portfolio supports this using one console. With all the news of our peers experiencing exploited security vulnerabilities and other challenges, we are continuing to gain market share and happy customers.
How should CISOs go about deciding on whether or not to consolidate cyber security? Beyond cost, what should CISOs think about?
The number one consideration should be efficacy of the program. CISO’s are realizing that very small differences in efficacy lead to very large cost savings. The best security tool for the job should always be selected knowing this. An inventory of tools and the jobs they are doing should be created and maintained. Frequently, CISO’s find dozens of tools that are redundant, overlap with others, add unnecessary complexity, and that are poorly deployed or managed and not integrated into the program. Once the inventory is completed, work with your expert consultant or reseller to review and find redundancies or overlaps and kick-off a program to evaluate technical and cost benefits.
What can organizations achieve with a consolidated cyber security solution?
As mentioned previously, the number one goal of the program should be improving efficacy and our customers do report this. Efficacy lowers the number of false positives, lowers the number of real events and decreases overall risk. Other savings are found with lower training costs, faster run book execution, fewer mistakes and the ability to free up security analysts from wasting time on inefficient processes. Those analysts can now be leveraged into more productive efforts and ensure that the business growth and strategies are better supported.
As a seasoned professional, when you’ve worked with CISOs and security teams in moving to a consolidated solution, what’s gone right, what’s gone wrong, and what lessons can you share with newbie security leaders?
Any significant change in your tool set needs careful consideration and evaluation. Every new tool needs to be tested in lab and moved, as appropriate, into production. You need to find all the gotcha’s with any new tool going inline before they cost impact.
Don’t rush this testing step! Ensure that you have good measurements of your current program so you can easily determine improvements with new tools or consolidation efforts.
If CISOs decide against consolidation, how can they drive better value through existing solutions?
Ensure that the solutions you are using are fully deployed and optimized. We frequently uncover many tools that are underutilized and ineffective. Sit with your staff and watch their work. If they are cutting and pasting, logging into and out of multiple tools, not having the time to address every alert, or are making excessive mistakes, it may be time to have Check Point come in and do a workshop. Our very experienced team will review the current program and provide thoughts and ideas to improve the program. Even if consolidation is not selected, other findings may help improve the program!
Are there any other actionable insights that you would like to share with cyber security leaders?
Every security program is different, and your challenges are unique. But, you can’t know everything, so, consider working with your trusted partners and invite Check Point in to do a free discovery workshop. Cloud maturity, consolidation program consideration, Zero Trust program formulation, and many others are available. As a CISO, you may have some initiatives that need extra validation, and we are standing by to help propel your program.
And for an even stronger security strategy, be sure to attend Check Point’s upcoming CPX 360 event. Register here.
Lastly, to receive cutting-edge cyber security news, best practices and resources in your inbox each week, please sign up for the CyberTalk.org newsletter.
The post Unconsidered benefits of a consolidation strategy every CISO should know appeared first on CyberTalk.