The hidden vulnerability: Why legacy government web forms demand urgent attention
Government agencies face a security challenge hiding in plain sight: outdated web forms that collect citizen data through systems built years — sometimes decades — ago. While agencies invest heavily in perimeter security and advanced threat detection, many continue using legacy forms lacking modern encryption, authentication capabilities and compliance features. These aging systems process Social Security numbers, financial records, health information and security clearance data through technology that falls short of current federal security standards.
The scale of this challenge is substantial. Government organizations allocate 80% of IT budgets to maintaining legacy systems, leaving modernization efforts chronically underfunded. Critical legacy systems cost hundreds of millions annually to maintain, with projected spending reaching billions by 2030. Meanwhile, government data breaches cost an average of $10 million per incident in the United States — the highest globally.
The encryption gap that persists
Despite the 2015 federal mandate establishing HTTPS as the baseline for all government websites, implementation gaps continue. The unencrypted HTTP protocol exposes data to interception, manipulation and impersonation attacks. Attackers positioned on the network can read Social Security numbers, driver’s license numbers, financial account numbers and login credentials transmitted in plain text.
Legacy government web forms that do implement encryption often use outdated protocols no longer meeting regulatory requirements. Older systems rely on deprecated hashing algorithms like SHA-1 and outdated TLS versions vulnerable to known exploits. Without proper security header enforcement, browsers don’t automatically use secure connections, allowing users to inadvertently access unencrypted form pages.
Application-layer vulnerabilities
Beyond transmission security, legacy web forms suffer from fundamental application vulnerabilities. Testing reveals that over 80% of government web applications remain prone to SQL injection attacks. Unlike private sector organizations that remediate 73% of identified vulnerabilities, government departments remediate only 27% — the lowest among all industry sectors.
SQL injection remains one of the most dangerous attacks against government web forms. Legacy forms constructing database queries using string concatenation rather than parameterized queries introduce serious vulnerabilities. This insecure practice allows attackers to inject malicious SQL code, potentially gaining unauthorized access to national identity information, license details and Social Security numbers. Attackers exploit these vulnerabilities to alter or delete identity records, manipulate data to forge official documents, and exfiltrate entire databases containing citizen information.
Cross-site scripting (XSS) affects 75% of government applications. XSS attacks enable attackers to manipulate users’ browsers directly, capture keystrokes to steal credentials, obtain session cookies to hijack authenticated sessions, and redirect users to malicious websites. Legacy forms also lack protection against CSRF attacks, which trick authenticated users into performing unwanted actions without their knowledge.
Compliance imperative
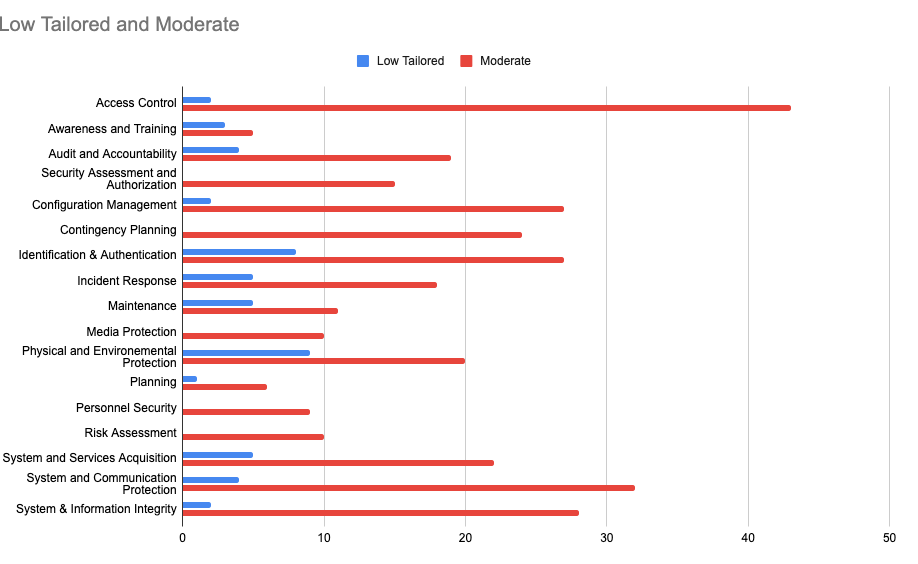
Federal agencies must comply with the Federal Information Security Management Act (FISMA), which requires implementation of National Institute of Standards and Technology SP 800-53 security controls including access control, configuration management, identification and authentication, and system and communications protection. Legacy web forms fail FISMA compliance when they cannot implement modern encryption for data in transit and at rest, lack multi-factor authentication capabilities, don’t maintain comprehensive audit logs, use unsupported software without security patches, and operate with known exploitable vulnerabilities.
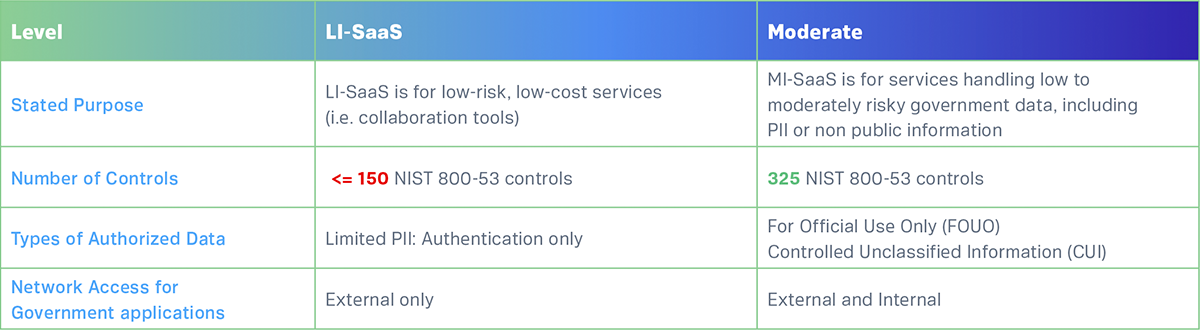
Federal agencies using third-party web form platforms must ensure vendors have appropriate FedRAMP authorization. FedRAMP requires security controls compliance incorporating NIST SP 800-53 Revision 5 controls, impact level authorization based on data sensitivity, and continuous monitoring of encryption methods and security posture. Legacy government web forms implemented through non-FedRAMP-authorized platforms represent unauthorized use of non-compliant systems.
Real-world transmission failures
The gap between policy and practice is stark. Federal agencies commonly require contractors to submit forms containing Social Security numbers, dates of birth, driver’s license numbers, criminal histories and credit information via standard non-encrypted email as plain PDF attachments. When contractors offer encrypted alternatives, badge offices often respond with resistance to change established procedures.
Most federal agencies lack basic secure portals for PII submission, forcing reliance on email despite policies requiring encryption. Standard Form 86 for national security clearances and other government forms are distributed as fillable PDFs that can be completed offline, saved unencrypted, and transmitted through insecure channels — despite containing complete background investigation data for millions of federal employees and contractors.
Recent breaches highlight ongoing vulnerabilities. Federal departments have suffered breaches where hackers accessed networks through compromised credentials. Congressional offices have been targeted by suspected foreign actors. Private contractors providing employee screening services have confirmed massive data breaches affecting millions, with unauthorized access lasting months before detection.
What agencies must do now
Government agencies must immediately enforce HTTPS encryption for all web form pages using HTTP strict transport security, deploy server-side input validation to prevent SQL injection and XSS attacks, implement anti-CSRF tokens for each form session, add bot protection, enable comprehensive access logging, and conduct regular vulnerability scanning for Open Worldwide Application Security Project Top 10 vulnerabilities.
Long-term security requires replacing legacy forms with FedRAMP-authorized platforms that provide end-to-end encryption using AES-256 for data at rest and TLS 1.3 for data in transit, multi-factor authentication for both citizens and government staff, role-based access control with granular permissions, comprehensive audit trails capturing all data access events, and automated security updates addressing emerging vulnerabilities.
Secure data collection
The real question is not whether government agencies can afford to modernize outdated web forms, but whether they can afford the consequences of failing to do so. Every unencrypted submission, each SQL injection vulnerability, and each missing audit trail represents citizen data at risk and regulatory violations accumulating. Federal mandates established the security standards years ago. Implementation can no longer wait.
The technology to solve these problems exists today. Modern secure form platforms offer FedRAMP authorization, end-to-end encryption, multi-factor authentication, comprehensive audit logging, and automated compliance monitoring. These platforms can replace legacy systems while improving user experience, reducing operational costs, and meeting evolving security requirements.
Success requires more than technology adoption — it demands organizational commitment. Agency leadership must prioritize web form security, allocate adequate budgets for modernization, and establish clear timelines for legacy system replacement. Security and IT teams need the resources and authority to implement proper controls.
Government web forms represent the primary interface between citizens and their government for countless critical services. When these forms are secure, they enable efficient, trustworthy digital government services. When they’re vulnerable, they undermine public confidence in government’s ability to protect sensitive information. The path forward is clear: Acknowledge the severity of legacy web form vulnerabilities, commit resources to address them systematically, and implement modern secure solutions. The cost of action is significant, but the cost of inaction — measured in breached data, compromised systems, regulatory penalties and lost public trust — is far higher.
Frank Balonis is chief information security officer and senior vice president of operations and support at Kiteworks.
The post The hidden vulnerability: Why legacy government web forms demand urgent attention first appeared on Federal News Network.

© Getty Images/iStockphoto/Traitov