How to Grow Plants in a Wine Barrel Successfully
Wine barrels are the ultimate planter. Made of wood, they add a rustic and homey look to your ... Read More
The post How to Grow Plants in a Wine Barrel Successfully appeared first on Garden Therapy.
Wine barrels are the ultimate planter. Made of wood, they add a rustic and homey look to your ... Read More
The post How to Grow Plants in a Wine Barrel Successfully appeared first on Garden Therapy.
Session 10A: Confidential Computing 2
Authors, Creators & Presenters: Byeongwook Kim (Seoul National University), Jaewon Hur (Seoul National University), Adil Ahmad (Arizona State University), Byoungyoung Lee (Seoul National University)
PAPER
Secure Data Analytics in Apache Spark with Fine-grained Policy Enforcement and Isolated Execution
Cloud based Spark platform is a tempting approach for sharing data, as it allows data users to easily analyze the data while the owners to efficiently share the large volume of data. However, the absence of a robust policy enforcement mechanism on Spark hinders the data owners from sharing their data due to the risk of private data breach. In this respect, we found that malicious data users and cloud managers can easily leak the data by constructing a policy violating physical plan, compromising the Spark libraries, or even compromising the Spark cluster itself. Nonetheless, current approaches fail to securely and generally enforce the policies on Spark, as they do not check the policies on physical plan level, and they do not protect the integrity of data analysis pipeline. This paper presents Laputa, a secure policy enforcement framework on Spark. Specifically, Laputa designs a pattern matching based policy checking on the physical plans, which is generally applicable to Spark applications with more fine-grained policies. Then, Laputa compartmentalizes Spark applications based on confidential computing, by which the entire data analysis pipeline is protected from the malicious data users and cloud managers. Meanwhile, Laputa preserves the usability as the data users can run their Spark applications on Laputa with minimal modification. We implemented Laputa, and evaluated its security and performance aspects on TPC-H, Big Data benchmarks, and real world applications using ML models. The evaluation results demonstrated that Laputa correctly blocks malicious Spark applications while imposing moderate performance overheads.
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Secure Data Analytics appeared first on Security Boulevard.

This week on the GeekWire Podcast: Newly unsealed court documents reveal the behind-the-scenes history of Microsoft and OpenAI, including a surprise: Amazon Web Services was OpenAI’s original partner. We tell the story behind the story, explaining how it all came to light.
Plus, Microsoft CEO Satya Nadella debuts a new AI catchphrase at Davos, startup CEO Dave Clark stirs controversy with his “wildly productive weekend,” Elon Musk talks aliens, and the latest on Seattle-area physical AI startups, including Overland AI and AIM Intelligent Machines.
Subscribe to GeekWire in Apple Podcasts, Spotify, or wherever you listen.
With GeekWire co-founders John Cook and Todd Bishop; edited by Curt Milton.
Session 10A: Confidential Computing 2
Authors, Creators & Presenters: Weili Wang (Southern University of Science and Technology), Honghan Ji (ByteDance Inc.), Peixuan He (ByteDance Inc.), Yao Zhang (ByteDance Inc.), Ye Wu (ByteDance Inc.), Yinqian Zhang (Southern University of Science and Technology)
PAPER
WAVEN: WebAssembly Memory Virtualization for Enclaves
The advancement of trusted execution environments (TEEs) has enabled the confidential computing paradigm and created new application scenarios for WebAssembly (Wasm). "Wasm+TEE" designs achieve in-enclave multi-tenancy with strong isolation, facilitating concurrent execution of untrusted code instances from multiple users. However, the linear memory model of Wasm lacks efficient cross-module data sharing and fine-grained memory access control, significantly restricting its applications in certain confidential computing scenarios where secure data sharing is essential (e.g., confidential stateful FaaS and data marketplaces). In this paper, we propose WAVEN (WebAssembly Memory Virtualization for ENclaves), a novel WebAssembly memory virtualization scheme, to enable memory sharing among Wasm modules and page-level access control. We implement WAVEN atop WAMR, a popular Wasm runtime for TEEs, and empirically demonstrate its efficiency and effectiveness. To the best of our knowledge, our work represents the first approach that enables cross-module memory sharing with fine-grained memory access control in Wasm.
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – WAVEN: WebAssembly Memory Virtualization For Enclaves appeared first on Security Boulevard.
Session 9D: Github + OSN Security
Authors, Creators & Presenters: Jan-Ulrich Holtgrave (CISPA Helmholtz Center for Information Security), Kay Friedrich (CISPA Helmholtz Center for Information Security), Fabian Fischer (CISPA Helmholtz Center for Information Security), Nicolas Huaman (Leibniz University Hannover), Niklas Busch (CISPA Helmholtz Center for Information Security), Jan H. Klemmer (CISPA Helmholtz Center for Information Security), Marcel Fourné (Paderborn University), Oliver Wiese (CISPA Helmholtz Center for Information Security), Dominik Wermke (North Carolina State University), Sascha Fahl (CISPA Helmholtz Center for Information Security)
PAPER
Attributing Open-Source Contributions is Critical but Difficult: A Systematic Analysis of GitHub Practices and Their Impact on Software Supply Chain Security
Critical open-source projects form the basis of many large software systems. They provide trusted and extensible implementations of important functionality for cryptography, compatibility, and security. Verifying commit authorship authenticity in open-source projects is essential and challenging. Git users can freely configure author details such as names and email addresses. Platforms like GitHub use such information to generate profile links to user accounts. We demonstrate three attack scenarios malicious actors can use to manipulate projects and profiles on GitHub to appear trustworthy. We designed a mixed-research study to assess the effect on critical open-source software projects and evaluated countermeasures. First, we conducted a large-scale measurement among 50,328 critical open-source projects on GitHub and demonstrated that contribution workflows can be abused in 85.9% of the projects. We identified 573,043 email addresses that a malicious actor can claim to hijack historic contributions and improve the trustworthiness of their accounts. When looking at commit signing as a countermeasure, we found that the majority of users (95.4%) never signed a commit, and for the majority of projects (72.1%), no commit was ever signed. In contrast, only 2.0% of the users signed all their commits, and for 0.2% of the projects all commits were signed. Commit signing is not associated with projects' programming languages, topics, or other security measures. Second, we analyzed online security advice to explore the awareness of contributor spoofing and identify recommended countermeasures. Most documents exhibit awareness of the simple spoofing technique via Git commits but no awareness of problems with GitHub's handling of email addresses.
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Attributing Open-Source Contributions Is Critical But Difficult appeared first on Security Boulevard.
Heading into President Donald Trump’s second term, coal looked like an industry nearing the end of its life. Utilities planned to retire more than half of the nation’s coal-fired power plants by 2028, no new facilities were coming online, and production had been flat for years.
Session 9D: Github + OSN Security
Authors, Creators & Presenters: Aditya Sirish A Yelgundhalli (New York University), Patrick Zielinski (New York University), Reza Curtmola (New Jersey Institute of Technology), Justin Cappos (New York University)
PAPER
Rethinking Trust In Forge-Based Git Security
Git is the most popular version control system today, with Git forges such as GitHub, GitLab, and Bitbucket used to add functionality. Significantly, these forges are used to enforce security controls. However, due to the lack of an open protocol for ensuring a repository's integrity, forges cannot prove themselves to be trustworthy, and have to carry the responsibility of being non-verifiable trusted third parties in modern software supply chains. In this paper, we present gittuf, a system that decentralizes Git security and enables every user to contribute to collectively enforcing the repository's security. First, gittuf enables distributing of policy declaration and management responsibilities among more parties such that no single user is trusted entirely or unilaterally. Second, gittuf decentralizes the tracking of repository activity, ensuring that a single entity cannot manipulate repository events. Third, gittuf decentralizes policy enforcement by enabling all developers to independently verify the policy, eliminating the single point of trust placed in the forge as the only arbiter for whether a change in the repository is authorized. Thus, gittuf can provide strong security guarantees in the event of a compromise of the centralized forge, the underlying infrastructure, or a subset of privileged developers trusted to set policy. gittuf also implements policy features that can protect against unauthorized changes to branches and tags i.e., pushes as well as files/folders i.e., commits. Our analysis of gittuf shows that its properties and policy features provide protections against previously seen version control system attacks. In addition, our evaluation of gittuf shows it is viable even for large repositories with a high volume of activity such as those of Git and Kubernetes (less than 4% storage overhead and under 0.59s of time to verify each push).
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Rethinking Trust In Forge-Based Git Security appeared first on Security Boulevard.
So it's come to this: Apple is reportedly working on a wearable AI pin. According to The Information, it is going to be a small device with "multiple cameras, a speaker, microphones and wireless charging." It sounds like the perfect gadget to pair with the long-awaited AI-powered Siri update, which will also reportedly work as a chatbot. But while many Apple rumors conjure up an air of excitement, the notion of an Apple AI pin sounds downright baffling. Worse, it just seems desperate.
Apple, the company known for taking its time to jump into new categories with more thoughtful solutions than its competitors, is reportedly chasing the specter of OpenAI's unreleased AI pin. Never mind that OpenAI has never actually produced any hardware, and that it arguably stumbled into its position as a leading AI player. And never mind that Humane's AI pin was a notorious failure that barely worked, and seemed pointless from the start.
Sure, Apple doesn't want more AI eggs on its face, after the delay of its Siri revamp and the underwhelming (and error-prone) debut of Apple Intelligence. Beyond OpenAI, there's also competition from Meta's Ray-Ban smart glasses, which lean heavily on the company’s AI. There’s also the looming threat of whatever AI hardware Meta is cooking up next, following the layoffs from its virtual reality division. And while Google doesn’t have much to show from its Android XR platform, which aims to bring its Gemini AI to your face, Samsung’s Galaxy XR is a start. We’ve also recently seen compelling demos of Google’s AR glasses prototypes and Xreal’s Project Aura glasses.
If Apple's AI pin serves as a conduit to Siri, is it really that much more convenient than using an iPhone, AirPods or even an Apple Watch to do the same? The company has reportedly nixed plans to put cameras in the Apple Watch, and Bloomberg suggests it’s opting instead to focus on delivering its own smart glasses this year. But it’s not hard to imagine that faster hardware could let the Apple Watch handle more Siri and AI-related tasks on its own. It’s already a fairly self-sufficient device, allowing you to ask basic Siri queries, run apps and listen to music without an iPhone — the cellular models are even more capable since they can take calls and send messages.
Rumors also point to infrared cameras coming to the next AirPods and AirPod Pros. Instead of taking photos, they could enable hand gestures and environmental awareness, which might be useful for Apple Intelligence down the line. The addition of heart rate tracking in the AirPods Pro 3 shows that there are still new features Apple can bring to its buds, beyond listening to music.
At best, an Apple AI pin could just be a simple way for someone to access Siri if they don’t want to wear an Apple Watch, plug in AirPods or have their iPhone within shouting distance. But at least those devices do other things beyond talking to Siri. The same is true for Meta’s Ray-Bans and future smart glasses. Even without accessing AI, they’ll still let you listen to music, take calls and, well, be glasses for those who need prescription frames.
Given the vocal pushback against Meta's Ray-Ban smart glasses, which are also being banned on cruises, clubs and other venues, I'm also not convinced many people would be eager to prominently display a surveillance device throughout the day. Wired’s Julian Chokkattu was questioned about wearing a camera while he was testing the Humane AI Pin, and I’ve also had to explain to curious people why I was wearing Xreal’s smart glasses, which feature a prominent camera accessory.
Sure, we're already living in a panopticon of smartphone cameras, but it's also obvious when someone is using their phone to capture photos and video. An AI pin just dangling off of your clothes is a constant threat, an unblinking eye. Even if Apple implements some sort of capture notification, someone will always try to circumvent it.
While The Information notes Apple's AI pin may never actually see the light of day, I wouldn't be surprised if it does. This is the company that partnered with OpenAI just to make Siri appear slightly smarter with the debut of Apple Intelligence. And instead of building its own home-brewed AI models, it's banking on Google's Gemini to power Siri's big AI upgrade, as well as its future foundation models. When it comes to AI, Apple will do almost anything to avoid being seen as a straggler (and to avoid even more stock declines).
It’s genuinely strange that Apple, the company that let Samsung and Google get a multi-year head start on foldable smartphones and hasn't yet jumped into the world of smart rings, could fast-track an AI pin for 2027. It’s yet another example of how the AI hype cycle has warped priorities throughout the tech industry. But at least Apple’s fortunes don’t depend on standalone AI hardware as much as OpenAI.
©
Session 9D: Github + OSN Security
Authors, Creators & Presenters: Aditya Sirish A Yelgundhalli (New York University), Patrick Zielinski (New York University), Reza Curtmola (New Jersey Institute of Technology), Justin Cappos (New York University)
PAPER
Rethinking Trust In Forge-Based Git Security
Git is the most popular version control system today, with Git forges such as GitHub, GitLab, and Bitbucket used to add functionality. Significantly, these forges are used to enforce security controls. However, due to the lack of an open protocol for ensuring a repository's integrity, forges cannot prove themselves to be trustworthy, and have to carry the responsibility of being non-verifiable trusted third parties in modern software supply chains. In this paper, we present gittuf, a system that decentralizes Git security and enables every user to contribute to collectively enforcing the repository's security. First, gittuf enables distributing of policy declaration and management responsibilities among more parties such that no single user is trusted entirely or unilaterally. Second, gittuf decentralizes the tracking of repository activity, ensuring that a single entity cannot manipulate repository events. Third, gittuf decentralizes policy enforcement by enabling all developers to independently verify the policy, eliminating the single point of trust placed in the forge as the only arbiter for whether a change in the repository is authorized. Thus, gittuf can provide strong security guarantees in the event of a compromise of the centralized forge, the underlying infrastructure, or a subset of privileged developers trusted to set policy. gittuf also implements policy features that can protect against unauthorized changes to branches and tags i.e., pushes as well as files/folders i.e., commits. Our analysis of gittuf shows that its properties and policy features provide protections against previously seen version control system attacks. In addition, our evaluation of gittuf shows it is viable even for large repositories with a high volume of activity such as those of Git and Kubernetes (less than 4% storage overhead and under 0.59s of time to verify each push).
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Rethinking Trust In Forge-Based Git Security appeared first on Security Boulevard.
Session 9D: Github + OSN Security
Authors, Creators & Presenters: Jian Cui (Indiana University), Hanna Kim (KAIST), Eugene Jang (S2W Inc.), Dayeon Yim (S2W Inc.), Kicheol Kim (S2W Inc.), Yongjae Lee (S2W Inc.), Jin-Woo Chung (S2W Inc.), Seungwon Shin (KAIST), Xiaojing Liao (Indiana University)
PAPER
Tweezers: A Framework For Security Event Detection Via Event Attribution-Centric Tweet Embedding
Twitter is recognized as a crucial platform for the dissemination and gathering of Cyber Threat Intelligence (CTI). Its capability to provide real-time, actionable intelligence makes it a indispensable tool for detecting security events, helping security professionals cope with ever-growing threats. However, the large volume of tweets and inherent noises of human-crafted tweets pose significant challenges in accurately identifying security events. While many studies tried to filter out event-related tweets based on keywords, they are not effective due to their limitation in understanding the semantics of tweets. Another challenge in security event detection from Twitter is the comprehensive coverage of security events. Previous studies emphasized the importance of early detection of security events, but they overlooked the importance of event coverage. To cope with these challenges, in our study, we introduce a novel event attribution-centric tweet embedding method to enable the high precision and coverage of events. Our experiment result shows that the proposed method outperforms existing text and graph-based tweet embedding methods in identifying security events. Leveraging this novel embedding approach, we have developed and implemented a framework, Tweezers, that is applicable to security event detection from Twitter for CTI gathering. This framework has demonstrated its effectiveness, detecting twice as many events compared to established baselines. Additionally, we have showcased two applications, built on Tweezers for the integration and inspection of security events, i.e., security event trend analysis and informative security user identification.
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Tweezers appeared first on Security Boulevard.
The federal government is preparing to undertake one of the most ambitious IT transformations in decades: Modernizing and unifying human resources information technology across agencies. The technology itself is not the greatest challenge. Instead, success will hinge on the government’s ability to establish an effective, authoritative and disciplined governance structure capable of making informed, timely and sometimes difficult decisions.
The central tension is clear: Agencies legitimately need flexibility to execute mission-specific processes, yet the government must reduce fragmentation, redundancy and cost by standardizing and adopting commercial best practices. Historically, each agency has evolved idiosyncratic HR processes — even for identical functions — resulting in one of the most complex HR ecosystems in the world.
We need a governance framework that can break this cycle. It has to be a structured requirements-evaluation process, a systematic approach to modernizing outdated statutory constraints, and a rigorous mechanism to prevent “corner cases” from derailing modernization. The framework is based on a three-tiered governance structure to enable accountability, enforce standards, manage risk and accelerate decision making.
Modernizing HR IT across the federal government requires rethinking more than just systems — it requires rethinking decision making. Technology will only succeed if governance promotes standardization, manages statutory and regulatory constraints intelligently, and prevents scope creep driven by individual agency preferences.
Absent strong governance, modernization will devolve into a high-cost, multi-point, agency-to-vendor negotiation where each agency advocates for its “unique” variations. Commercial vendors, who find arguing with or disappointing their customers to be fruitless and counterproductive, will ultimately optimize toward additional scope, higher complexity and extended timelines — that is, unless the government owns the decision framework.
The root causes of this central challenge are structural. Agencies with different missions evolved different HR processes — even for identical tasks such as onboarding, payroll events or personnel actions. Many “requirements” cited today are actually legacy practices, outdated rules or agency preferences. And statutes and regulations are often more flexible than assumed, but in order to avoid any risk of perceived noncompliance or litigation.
Without centralized authority, modernization will replicate fragmentation in a new system rather than reduce it. Governance must therefore act as the strategic filter that determines what is truly required, what can be standardized and what needs legislative or policy reform.
Regardless of the rigor associated with the requirements outlined at the outset of the program, implementers will encounter seemingly unique or unaccounted for “requirements” that appear to be critical to agencies as they begin seriously planning for implementation. Any federal HR modernization effort must implement a consistent, transparent and rigorous method for evaluating these new or additional requirements. The framework should classify every proposed “need” across two dimensions:
This line of thinking leads to a decision matrix of sorts. For instance, identified needs that are found to be universal and well-codified are likely legitimate requirements and solid candidates for productization on the part of the HR IT vendor. For requirements that apply to a group of agencies or a single agency, or that are really based on practice or tradition, there may be a range of outcomes worth considering.
Prior to an engineering discussion, the applicable governance body must ask of any new requirement: Can this objective be achieved by conforming to a recognized commercial best practice? If the answer is yes, the governance process should strongly favor moving in that direction.
This disciplined approach is crucial to keeping modernization aligned with cost savings, simplification and future scalability.
A common pitfall in federal IT is the tendency to view outdated laws and regulations as immutable engineering constraints. There are in fact many government “requirements” — often at a very granular and prescriptive level — embedded in written laws and regulations, that are either out-of-date or that simply do not make sense when viewed in a larger context of how HR gets done. The tendency is to look at these cases and say, “This is in the rule books, so we must build the software this way.”
But this is the wrong answer, for several reasons. And reform typically lags years behind technology. Changing laws or regulations is an arduous and lengthy process, but the government cannot afford to encode obsolete statutes into modern software. Treating every rule as a software requirement guarantees technical debt before launch.
The Office of Management and Budget and the Office of Personnel Management have demonstrated the ability to manage simple, business-case-driven exception processes. This capability should be operationalized as a core component of HR IT modernization governance:
This approach flips the traditional model. Instead of software lagging behind policy, the modernization effort drives policy evolution.
In large-scale HR modernization, “corner cases” can become the silent destroyer of budgets and timelines. Every agency can cite dozens of rare events — special pay authorities, unusual personnel actions or unique workforce segments — that occur only infrequently.
The risk is that building system logic for rare events is extraordinarily expensive. These edge cases disproportionately consume design and engineering time. And any customization or productization can increase testing complexity and long-term maintenance cost.
Governance should enforce a strict return-on-investment rule: If a unique scenario occurs infrequently and costs more to automate than to handle manually, it should not be engineered into the system.
For instance, if a unique process occurs only 50 times a year across a 2-million-person workforce, it is cheaper to handle it manually outside the system than to spend millions customizing the software. If the government does not manage this evaluation itself, it will devolve into a “ping-pong” negotiation with vendors, leading to scope creep and vulnerability. The government must hold the reins, deciding what gets built based on value, not just request.
To operationalize the ideas above, the government should implement a three-tiered governance structure designed to separate strategy from technical execution.
The ESC establishes the foundation for policy, ensures accountability, and provides air cover for standardization decisions that may challenge entrenched agency preferences.
The FCB prevents the “paving cow paths” phenomenon by rigorously protecting the standard process baseline.
The ARB enforces discipline on engineering choices and protects the system from fragmentation.
Federal HR IT modernization presents a rare opportunity to reshape not just systems, but the business of human capital management across government. The technology exists. The challenge — and the opportunity — lies in governance.
The path to modernization will not be defined by the software implemented, but by the discipline, authority, and insight of the governance structure that guides it.
Steve Krauss is a principal with SLK Executive Advisory. He spent the last decade working for GSA and OPM, including as the Senior Executive Service (SES) director of the HR Quality Service Management Office (QSMO).
The post Governing the future: A strategic framework for federal HR IT modernization first appeared on Federal News Network.

© Getty Images/iStockphoto/metamorworks
A third-party arbitrator is ordering the Department of Health and Human Services to walk back its return-to-office mandate for thousands of employees represented by one of its unions.
Arbitrator Michael J. Falvo ruled on Monday that HHS must “rescind the return-to-office directive,” and must immediately reinstate remote work and telework agreements for members of the National Treasury Employees Union.
HHS rescinded those workplace flexibility agreements early last year, after President Donald Trump ordered federal employees to return to the office full-time.
Falvo found that HHS committed an unfair labor practice by unilaterally terminating telework and remote agreements, without regard to its five-year collective bargaining agreement with NTEU. The labor contract, which covers 2023 through 2028, states the agency can only terminate telework and remote work agreements “for cause.” That includes emergency situations and cases when an employee falls short of a “fully satisfactory” performance rating.
The ruling will impact thousands of HHS employees represented by NTEU. Its members include employees at the Food and Drug Administration, the Substance Abuse and Mental Health Services Administration, the Administration for Children and Families, the Administration on Community Living, the Health Resources and Services Administration, the National Center for Health Statistics and the HHS Office of the Secretary.
Falvo is also ordering HHS to post a signed notice, “admitting that the agency violated the statute by repudiating the collective bargaining agreement.” The arbitrator wrote that his ruling does not limit NTEU from “seeking additional remedies to the extent permitted by law.”
HHS officials argued that Trump’s return-to-office presidential memorandum supersedes the collective bargaining agreement. But the 1978 Federal Services Labor-Management Relations Statute makes it an unfair labor practice for an agency “to enforce any rule or regulation … which is in conflict with any applicable collective bargaining agreement if the agreement was in effect before the rule or regulation was prescribed.”
According to Falvo, the Federal Labor Relations Authority set a precedent in previous labor disputes that a presidential memorandum “is not a governmentwide rule or regulation that the employer is obligated by law to implement immediately upon issuance.”
“These cases compel the conclusion that the agency breached the agreement and violated the statute,” he wrote.
The arbitrator decided Trump’s return-to-office memo does not override telework and remote work protections outlined in NTEU’s collective bargaining agreement. HHS did not respond to a request for comment. NTEU declined to comment.
NTEU Chapter 282, which covers FDA headquarters employees, told members in an email that HHS is likely to appeal the arbitrator’s decision and has 30 days to do so. The union’s message states, “NTEU will push the agency to accept the ruling and restore your rights without delay.”
“This is a significant win that reaffirms that telework and remote work rights negotiated in a term contract cannot be unilaterally taken away,” NTEU Chapter 282 told members.
More than a year into the second Trump administration, several recent exceptions to its return-to-office policy have emerged.
The Labor Department’s Office of Workers’ Compensation Programs recently told employees that some of its employees will be eligible for remote work, because the agency is “extremely challenged” covering rent expenses for a fully in-office workforce.
Meanwhile, a second arbitrator ruled that the Centers for Medicare and Medicaid Services “violated statutory obligations” to bargain with the American Federation of Government Employees over implementation of the administration’s return-to-office directive.
The arbitrator in this dispute determined CMS wasn’t required to negotiate with the union over the administration’s return-to-office mandate, but did have an obligation to ensure implementation complied with its collective bargaining agreement with AFGE.
The arbitrator ordered CMS to meet and negotiate with AFGE over the “effects of the implementation of the directive on work/life balance of employees.”
Trump touted his return-to-office mandate at a White House press briefing on Tuesday, where he looked back on the accomplishments of his first year in office.. Trump told reporters that when he took office last year, “we had so many of our federal workers who wouldn’t come into work.”
“We don’t want them sitting in their home, on their bed, working. We want them in an office that we’re paying for in Washington, D.C., or wherever it may be. And we’ve largely taken care of that mess,” Trump said. “I guarantee you they’re out on the ballfields. I guarantee you they’re out playing golf. And you can’t run a country or a company that way.”
Trump’s presidential memorandum directed agencies to terminate remote work and telework agreements, but also stated that the return-to-office mandate must be “implemented consistent with applicable law.”
“Reasonable persons could have different notions whether a presidential memorandum (or an executive order) is such a ‘rule or regulation’ under ‘applicable law.’ On January 20, 2025, what ‘applicable law’ required was not a matter of first impression,” Falvo wrote.
NTEU filed a grievance against HHS last February, after the agency issued a directive requiring all bargaining unit employees to report to the office on a full-time basis.
Union officials argued that HHS refused to negotiate with NTEU before the return-to-office memo took effect, and would agree to “post-implementation bargaining.”
HHS officials denied the grievance and told the union that an agency head “retains the statutory right to determine overall telework levels and to exclude positions from telework eligibility.”
Christina Ballance, the executive director of the agency’s National Labor and Employee Relations Office, told the arbitrator that HHS “was obligated to comply with the presidential memorandum.”
“Ultimately, the president is our chief, and if he directs that employees return to offices in person, the agency is required to do so,” Ballance said in her testimony.
HHS officials rejected NTEU’s claims that it terminated all telework and remote work agreements. They said the agency still allows situational and ad-hoc telework, as well as workplace flexibilities for military spouses and reasonable accommodations for employees with disabilities.
But Federal News Network first reported last month that a new HHS policy restricts employees with disabilities from using telework as an interim accommodation, while the agency processes their reasonable accommodation request.
HHS is also centralizing the processing of reasonable accommodation requests on behalf of its component agencies. As a result, it is inheriting a backlog of requests that HHS officials expect will take about six to eight months to review.
The post Trump’s return-to-office memo doesn’t override telework protections in union contract, arbitrator tells HHS first appeared on Federal News Network.

© AP Photo/Mark Schiefelbein
Authors, Creators & Presenters: Zhuo Chen (Zhejiang University), Yufeng Hu (Zhejiang University), Bowen He (Zhejiang University), Dong Luo (Zhejiang University), Lei Wu (Zhejiang University), Yajin Zhou (Zhejiang University)
PAPER
Dissecting Payload-Based Transaction Phishing On Ethereum
In recent years, a more advanced form of phishing has arisen on Ethereum, surpassing early-stage, simple transaction phishing. This new form, which we refer to as payload-based transaction phishing (PTXPHISH), manipulates smart contract interactions through the execution of malicious payloads to deceive users. PTXPHISH has rapidly emerged as a significant threat, leading to incidents that caused losses exceeding $70 million in 2023 reports. Despite its substantial impact, no previous studies have systematically explored PTXPHISH. In this paper, we present the first comprehensive study of the PTXPHISH on Ethereum. Firstly, we conduct a long-term data collection and put considerable effort into establishing the first ground-truth PTXPHISH dataset, consisting of 5,000 phishing transactions. Based on the dataset, we dissect PTXPHISH, categorizing phishing tactics into four primary categories and eleven sub-categories. Secondly, we propose a rule-based multi-dimensional detection approach to identify PTXPHISH, achieving an F1-score of over 99% and processing each block in an average of 390 ms. Finally, we conduct a large-scale detection spanning 300 days and discover a total of 130,637 phishing transactions on Ethereum, resulting in losses exceeding $341.9 million. Our in-depth analysis of these phishing transactions yielded valuable and insightful findings. Scammers consume approximately 13.4 ETH daily, which accounts for 12.5% of the total Ethereum gas, to propagate address poisoning scams. Additionally, our analysis reveals patterns in the cash-out process employed by phishing scammers, and we find that the top five phishing organizations are responsible for 40.7% of all losses. Furthermore, our work has made significant contributions to mitigating real-world threats. We have reported 1,726 phishing addresses to the community, accounting for 42.7% of total community contributions during the same period. Additionally, we have sent 2,539 on-chain alert messages, assisting 1,980 victims. This research serves as a valuable reference in combating the emerging PTXPHISH and safeguarding users' assets.
ABOUT NDSS
The Network and Distributed System Security Symposium (NDSS) fosters information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
Our thanks to the Network and Distributed System Security (NDSS) Symposium for publishing their Creators, Authors and Presenter’s superb NDSS Symposium 2025 Conference content on the Organizations' YouTube Channel.
The post NDSS 2025 – Dissecting Payload-Based Transaction Phishing On Ethereum appeared first on Security Boulevard.
Harriet Rees from Starling Bank and Dr Rohit Dhawan from Lloyds Banking Group will spearhead AI adoption.
The post UK Appoints AI Champions to Boost Financial Services appeared first on TechRepublic.
Samsung’s 2025 was filled with new foldables, an ultra-thin new form factor and the launch of Google's XR platform. After making some announcements at CES 2026, the company is expected to host its first Galaxy Unpacked of the year in February to introduce the Galaxy S26 lineup.
Engadget will be covering Galaxy Unpacked live, and we'll most likely have hands-on coverage of Samsung's new smartphones soon after they're announced. While we wait for an official invite, here's everything we expect Samsung will introduce at the first Galaxy Unpacked event of 2026.

Samsung's restrained approach to updating its phones will likely continue with the Galaxy S26. Based on leaked images of the new lineup, the company is not expected to radically reinvent the look of the Galaxy S26, Galaxy S26+ or Galaxy S26 Ultra, and instead will stick with a similar design to what it used on the Galaxy S25. The phones will have a flat front screen and frame, with rounded corners and cameras housed in a vertical pill-shaped plateau on the back. Unlike Apple's move from the iPhone 16 Pro to the iPhone 17 Pro, the biggest difference here will likely be internal components like the screens, chips and camera sensors Samsung uses.
Qualcomm's new Snapdragon 8 Elite Gen 5 chip is expected to be in all Samsung Galaxy S26 phones, though Korean news site Yonhap News reports Samsung's relatively new Exynos 2600 chip could be used in some phones in the lineup depending on the region, a strategy Samsung has deployed in the past. Either way the new phones should be more performant than the previous generation, and in the case of the models with the Snapdragon 8 Elite Gen 5, particularly good at on-device AI processing.
I have compiled the most accurate comprehensive parameter comparison of Galaxy S25, S25+ and Galaxy S26、 S26+. Which one do you want to buy? pic.twitter.com/aQpoSvYjOz
— Ice Universe (@UniverseIce) November 29, 2025
One notable difference between the Galaxy S26 and the Galaxy S25 could be the phone's screen. The new phone will reportedly feature a 6.3-inch FHD+ display according to specs shared by leaker Ice Universe, which makes it ever so slightly larger than the 6.2-inch display used on the Galaxy S25. The S26 will also allegedly come with 12GB of RAM, either 256GB or 512GB of storage and a slightly larger 4,300mAh battery. Samsung isn't changing the cameras on the entry-level phone, though: leaks suggest it'll feature the same 50-megapixel main camera, 12-megapixel ultrawide, 10-megapixel 3x telephoto and 12-megapixel selfie camera as the previous generation. Changes appear to be even more minor on the Galaxy S26+. Other than the new Snapdragon chip, the phone will reportedly feature the same 6.7-inch FHD+ screen, 4,900mAh battery, 12GB of RAM and the same camera array used on the base Galaxy S26.
The difference between the Galaxy S26 Ultra and Galaxy S25 Ultra is reportedly a bit clearer. According to Android Headlines, the new phone's cameras will be slightly more raised, and stand out thanks to a new metallic finish. Samsung may also switch back to using an aluminum frame on the Galaxy S26 Ultra, after using titanium frames on both the Galaxy S24 and S25 Ultras. Most importantly, to make the phone actually support Qi2 rather than only technically work with the standard when a case is attached, rumors suggest Samsung will remove the S Pen digitizer layer in the phone and adopt a new method for accepting stylus input. It's not clear what that new method will actually be, but it could let the Galaxy S26 Ultra more easily work with Qi2 accessories without losing its stylus.

Samsung released the Galaxy Buds 3 and 3 Pro in 2024, with a major redesign that brought them much more in line with Apple's AirPods. The Galaxy Buds 4 and Buds 4 Pro Samsung is rumored to be announcing soon won't necessarily change that, though they will feature a more compact case and less angular stems, according to leaked images from the Samsung Tips app.
Support for head gestures to accept and decline calls, a feature Apple includes on the AirPods Pro 3 and AirPods 4, is also rumored to work on both versions of the new Galaxy Buds. SamMobile reports the Galaxy Buds 4 and 4 Pro may also ship with a new Ultra Wideband chip that will make them easier to find with Google's Find Hub network.
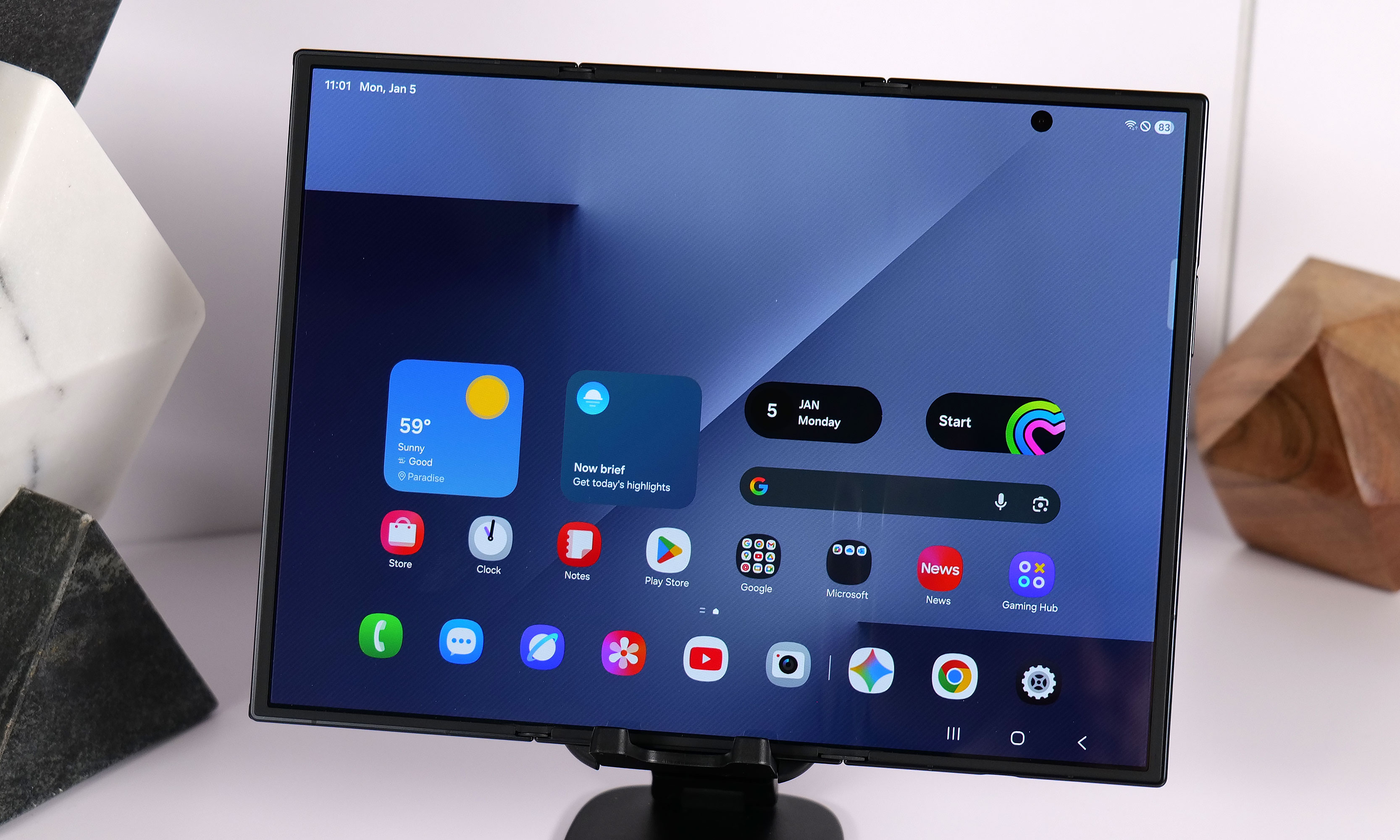
Samsung announced the Galaxy Z TriFold in late 2025 without firm details of when the new smartphone-that-folds-into-a-tablet would be available in North America. Considering the company had the new device available for hands-on demos at CES 2026, it seems possible it could share more information about when the Galaxy Z TriFold will be widely available at Galaxy Unpacked.

When the Galaxy S25 Edge was announced in 2025, it seemed possible that Samsung could replace its "Plus" smartphone with a unique form factor, just like Apple has opted to do with the iPhone Air. There have been conflicting reports on the matter, but it seems like Samsung will not be doing that with the Galaxy S26 Edge.
Instead, the smartphone will reportedly remain another option, much like foldables are for customers not swayed by Samsung's traditional smartphones. The Galaxy S26 Edge is rumored to feature a slightly different design than last year's model, according to Android Headlines, with a large rectangular camera plateau that's reminiscent of Google's Pixel phones, and the raised oval Apple used on the iPhone Air. Beyond that, the phone is also expected to be ever so slightly thinner at 5.5mm than the 5.8mm Galaxy S25 Edge.
Samsung already acts as a first place Google can show off new AI features for Android, but the company is reportedly exploring other AI partnerships, too. In June 2025, Bloomberg reported that Samsung was nearing a deal with Perplexity to integrate its AI-powered search engine across OneUI and its homegrown mobile browser. Perplexity already has a deal with Motorola on its Razr phones, so the only thing that would make a deal with Samsung unusual is the close relationship the company already has with Google.
The company also accidentally announced a new version of its Bixby AI assistant, which will likely also be integrated with Perplexity and could serve as an alternative to Google Gemini. Both a new Bixby and a deeper integration with Perplexity seem like natural new software features to show off at Galaxy Unpacked.
This article originally appeared on Engadget at https://www.engadget.com/mobile/smartphones/what-to-expect-at-samsung-galaxy-unpacked-2026-130000003.html?src=rss©
Harriet Rees from Starling Bank and Dr Rohit Dhawan from Lloyds Banking Group will spearhead AI adoption.
The post UK Appoints AI Champions to Boost Financial Services appeared first on TechRepublic.
Think you don’t use blockchain?
Think again… You’re using it every single day — without even realizing it.
💳 ATM withdrawals rely on secure, ledger-based systems to protect your money
📦 Online order tracking depends on tamper-proof records to ensure delivery accuracy
📝 Digital document verification uses automated validation to prevent fraud
The smartest systems don’t announce themselves.
They work quietly behind the scenes, ensuring security, transparency, and trust.
At Duredev, we design blockchain-powered digital systems that users rarely notice — but businesses rely on every single day.

Blockchain is no longer limited to cryptocurrency. Today, blockchain development services are becoming core infrastructure for businesses that handle sensitive data, transactions, and multi-party processes.
Companies now look for solutions that:
That’s why demand for a reliable blockchain development company has increased across industries like finance, logistics, and enterprise platforms.
Every business has different workflows. Off-the-shelf solutions often fail to match real operational needs.
With custom blockchain development services, businesses can design systems tailored to:
At Duredev, custom blockchain solutions are built with scalability, security, and long-term adaptability in mind — not short-term experimentation.
Smart contracts are one of the most powerful blockchain innovations for businesses.
Using smart contract development services, companies can automate:
The result is faster execution, fewer errors, and reduced operational costs. Duredev focuses on smart contracts that are secure, auditable, and aligned with real business logic.
Finance is one of the biggest adopters of blockchain technology.
With blockchain for finance and lending, platforms can offer:
Businesses building blockchain-based financial platforms gain higher user trust and operational efficiency. At Duredev, finance-focused blockchain solutions are designed to meet compliance and scalability requirements from day one.
Supply chains involve multiple stakeholders, which often leads to delays, disputes, and data mismatches.
Blockchain supply chain solutions solve this by creating a single, immutable source of truth. Businesses can:
Through blockchain solutions for logistics, Duredev helps companies build transparent and reliable supply chain ecosystems.
Large organizations need systems that work reliably under high volume and complexity.
With enterprise blockchain development, businesses can modernize legacy systems while maintaining performance and security. These solutions support:
This is where blockchain infrastructure development becomes a strategic investment rather than an experiment.
The most effective blockchain systems are invisible to end users.
Whether it’s blockchain application development or blockchain integration services, the goal is simple:
Let the technology handle trust — while users focus on experience.
At Duredev, this philosophy guides every project, ensuring blockchain adds value without adding complexity.
Choosing a blockchain partner is not just a technical decision — it’s a business decision.
Companies work with Duredev because we focus on:
As a trusted blockchain development company, Duredev helps businesses move from idea to implementation with confidence.
Blockchain is no longer futuristic — it’s already embedded in modern digital systems.
From decentralized business applications to blockchain-powered digital systems, companies that invest in the right infrastructure today gain long-term advantages in trust, efficiency, and scalability.
If you’re planning to build or upgrade a secure digital platform, exploring blockchain consulting services early can save time, cost, and complexity later.
And that’s where Duredev helps businesses build systems that work — quietly, reliably, and every day.
🚨 Think You Don’t Use Blockchain? Think Again… was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.
Yes, leftover boiled potatoes work well as long as they are firm and not mushy. Slice them gently before cooking.
You can skip hing if needed, but it adds a subtle flavor. If you are gluten-sensitive, make sure to use gluten-free hing or omit it.
This dish is mildly spicy. You can reduce or increase the number of green chilies based on your taste.
It tastes best when served fresh, but you can prepare it a few hours ahead and gently reheat it in a pan before serving.
Fresh cilantro is highly recommended for the best flavor. Dried cilantro will not give the same freshness.
You can serve it as a side dish, enjoy it as a snack, or roll it into a roti for a quick and satisfying meal.
The post New Spicy Potato with Cilantro and Ginger appeared first on Manjula's Kitchen.

UK MPs warn regulators’ hands-off stance on AI in finance risks consumer harm, fraud, and systemic shocks as adoption outpaces oversight.
The post Lawmakers Raise Concerns Over Unchecked AI Use in UK Finance appeared first on TechRepublic.