Cloudflare Outage Caused by React2Shell Mitigations
The critical React vulnerability has been exploited in the wild by Chinese and other threat actors.
The post Cloudflare Outage Caused by React2Shell Mitigations appeared first on SecurityWeek.
The critical React vulnerability has been exploited in the wild by Chinese and other threat actors.
The post Cloudflare Outage Caused by React2Shell Mitigations appeared first on SecurityWeek.
This latest event follows hot on the heels of Nov. 18, when Cloudflare was hit by a global outage for several hours.
The post Cloudflare Suffers Global Outage appeared first on TechRepublic.
Cloudflare recently mitigated a new record-breaking Aisuru attack that peaked at 14.1 Bpps.
The post Aisuru Botnet Powers Record DDoS Attack Peaking at 29 Tbps appeared first on SecurityWeek.
This latest event follows hot on the heels of Nov. 18, when Cloudflare was hit by a global outage for several hours.
The post Cloudflare Suffers Global Outage appeared first on TechRepublic.
Flare, a layer 1 blockchain known for its interoperability and support for decentralized applications (dApps), is on the brink of a significant transformation.
The network, which allows users to tap into its ecosystem to put XRP to work in decentralized finance, is on the verge of a major network upgrade. Could the Flare (FLR) price explode amid this development?
As noted, Flare is preparing for two pivotal hard forks.
The upgrade has already been successfully activated on the Songbird testnet.
On Wednesday, the Flare team confirmed the mainnet upgrade is set for December 2, 2025, at 12:00 UTC.
FLR price is up amid the successful completion of the Songbird network upgrade and the impending Flare mainnet upgrade.
These upgrades are part of a broader strategy to integrate key components of the Cancun/Dencun fork, promising a more efficient and cost-effective environment for smart contracts.
For investors and enthusiasts, the critical question is what this could mean for FLR.
Notably, the upgrades introduce advanced Ethereum Virtual Machine (EVM) features.
Co-founder Hugo Phillion commented on the development via X.
Flare launched in a bear market. We shipped.
Flare emerged into a bull market. We climbed the MCAP rankings. We shipped.Throw what you will at us.
We will ship and climb.— Hugo Philion (@HugoPhilion) November 25, 2025
The aim is to boost performance, efficiency, and scalability.
Key enhancements include the MCOPY opcode, which accelerates memory operations through chunk-based data transfers.
There’s also TSTORE/TLOAD (Transient Storage), offering cost-effective temporary storage for high-throughput applications.
According to the project, these improvements introduce critical capabilities and enhancements.
Other than supporting a more efficient and scalable dApps ecosystem, it means reduced execution costs and innovative protocols, including modular lending systems.
Additionally, the P-chain will introduce dynamic staking fees based on gas consumption and current gas prices, alongside upgrades to supporting libraries like flarejs.
As a comprehensive overhaul, the upgrade positions Flare for the next generation of dApps.
It also adds to the current traction that includes FXRP.
Historically, significant protocol upgrades have sparked investor optimism.
Often, this has led to price surges due to increased utility and adoption potential.
In this case, the successful Songbird upgrade may serve as a confidence booster, suggesting a smooth transition for the mainnet upgrade.
Enhanced scalability and lower costs could attract more dApp developers.
Potentially, this increases demand for FLR tokens used in transaction fees and governance.
Given the current price has jumped from lows of $0.011 to above $0.015 and seen over 24% gains in the past week, the upgrade could catalyse a short-term price rally.
FLR testing higher resistance levels in the coming months will depend on the next moves and overall price outlook.
The token reached highs of $0.035 in December 2024 and the all-time peak of $0.079 in January 2023.
The post Flare Network’s major upgrade is here: what’s the outlook for FLR price? appeared first on CoinJournal.


This post lays out how we think about incidents like Cloudflare’s outage this week, why pure smart‑contract control planes with timelocks change the failure modes, and where zero‑knowledge proofs fit.
On Nov 18, 2025 at 11:20 UTC, Cloudflare’s edge began returning 5xx for a big slice of traffic. The root trigger wasn’t an attacker; it was a ClickHouse permissions change that made a query return duplicate rows. That query generated a Bot Management “feature file” shipped to every edge box every few minutes.
The duplicates doubled the file and bumped the feature count over 200. The bot module had a hard cap and a unwrap() that panicked on overflow. As nodes alternated between “old-good” and “new-bad” outputs every five minutes, the fleet oscillated until all shards were updated and stayed bad.
Cloudflare halted the publisher at 14:24, shipped a last‑known‑good file at 14:30, and reported full recovery at 17:06. The follow‑ups they listed: harden ingestion of internal config, add global kill switches, and review failure modes across modules.
See Cloudflare’s own postmortem for the full timeline and code snippets.
There are two separate problems in that story:
You still fix (2) in code reviews. But (1) is where blockchains shine: as a tamper‑evident, programmable gate in front of rollouts.
If you compress the idea to one sentence: no config becomes “current” unless a smart contract says so, and the contract only flips that flag after a timelock and a proof that the artifact obeys invariants. That one sentence implies a complete architecture.
Turns out public blockchains, especially built on Ethereum, the EVM chains running the Ethereum Virtual Machine and consensus layer, offer a good solution to that problem.
Latency fit. Ethereum finalizes in epochs, but L2s confirm in seconds (OP Stack targets ~2s; zkSync ~1s; many systems expose fast attestation). It’s good enough for five‑minute control‑plane cadences, see for instance the OP block time discussion or Circle’s attestation timings).
Attach a succinct proof with every artifact and verify it on chain. That’s exactly what we do for our Chainwall protocol, although for a different kind of data!
The core goal is to prove basic properties: row_count <= 200, sorted + unique by key, schema matches regex and type rules, filesize <= N. You can either fit the whole logic onchain, or rely on Plonk/Groth circuits for larger expressions. For instance, a zk‑VM guest can parse CSV/Parquet/JSON and emits a SNARK. You don’t have to reveal the contents, only the commitment. Both research and production systems for regex in ZK exist (e.g., Reef and related zk‑regex work), which makes schema checks realistic.
There’s two practical paths:
Edges poll the registry and only adopt artifacts that are green‑lit on chain. To avoid trusting a third‑party RPC, run a light client in your control plane (e.g., Helios) or plan for the Portal Network. That way, edges verify headers and inclusion proofs locally before they accept any “new current” state.
Kill switch & rollback are just bits in the contract, honored by the edge. Cloudflare explicitly called out the need for stronger global kill switches; putting that switch in a small, audited contract gives you a single source of truth under stress.
CloudFlare event was not an attack, but they initially thought so and that was indeed likely! As we’ve seen in crypto security: attackers don’t just chase keys; they coerce the control plane.
Our position: control of digital assets must live in smart contracts guarded by timelocks and multisigs, not in private credentials, CI tokens, cloud ACLs, or admin dashboards. If your deploy or “change owner” action must traverse a contract’s schedule() and execute() path, even a rootkit on a developer laptop can’t jump the queue. The time delay is a circuit breaker you can count on, and the on‑chain audit trail is objective. That only leaves the “what if the thing we’re promoting is malformed?” question, which is exactly what “proof‑carrying config” answers.
We also believe there’s a considerable market for trust-minimized applications. We’re only building the right foundations now for a first, well-defined use case at OKcontract Labs.
When a Feature File Tripped the Internet was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.
When a Cloudflare outage disrupted large numbers of websites and online services yesterday, the company initially thought it was hit by a “hyper-scale” DDoS (distributed denial-of-service) attack.
“I worry this is the big botnet flexing,” Cloudflare co-founder and CEO Matthew Prince wrote in an internal chat room yesterday, while he and others discussed whether Cloudflare was being hit by attacks from the prolific Aisuru botnet. But upon further investigation, Cloudflare staff realized the problem had an internal cause: an important file had unexpectedly doubled in size and propagated across the network.
This caused trouble for software that needs to read the file to maintain the Cloudflare bot management system that uses a machine learning model to protect against security threats. Cloudflare’s core CDN, security services, and several other services were affected.

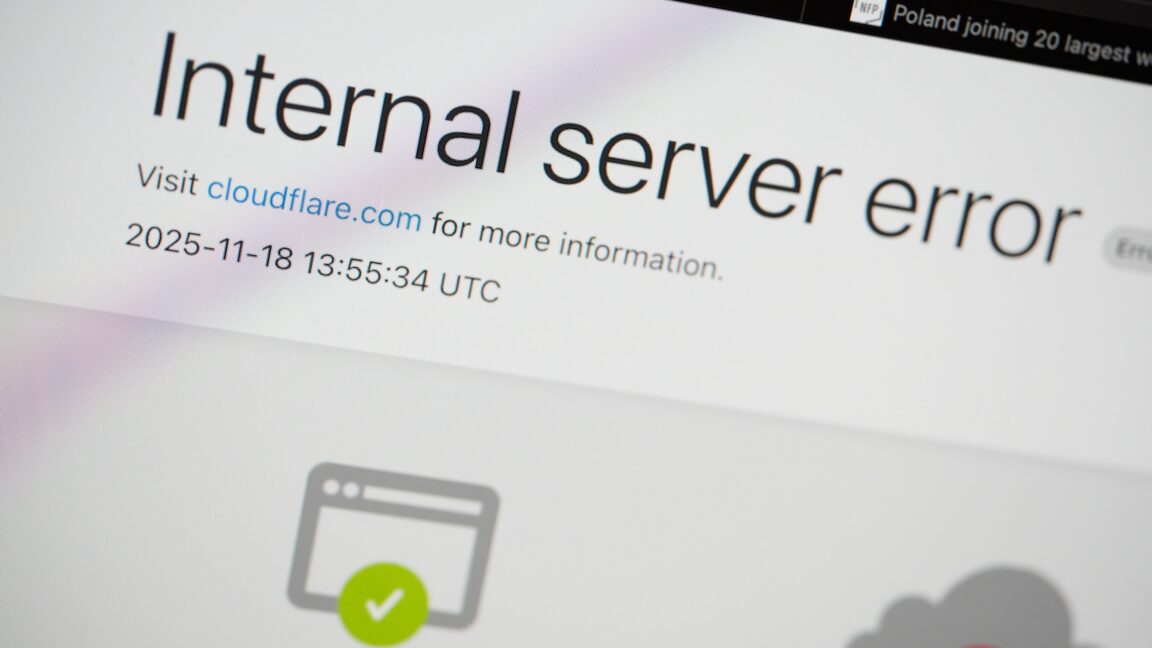
© Getty Images | NurPhoto
Major online services such as ChatGPT, X, and Shopify were disrupted in a global Cloudflare outage on Nov. 18th, as well as transit and city services.
The post Cloudflare Outage Not Caused by Cyberattack appeared first on SecurityWeek.
A Cloudflare outage caused large chunks of the Internet to go dark Tuesday morning, temporarily impacting big platforms like X and ChatGPT.
“A fix has been implemented and we believe the incident is now resolved. We are continuing to monitor for errors to ensure all services are back to normal,” Cloudflare’s status page said. “Some customers may be still experiencing issues logging into or using the Cloudflare dashboard.”
The company initially attributed the widespread outages to “an internal service degradation” and provided updates as it sought a fix over the past two hours.


© NurPhoto / Contributor | NurPhoto
High-profile services affected include ChatGPT, Sora, Shopify, and Elon Musk’s social media platform X.
The post Cloudflare Outage Hits Major Websites appeared first on TechRepublic.
High-profile services affected include ChatGPT, Sora, Shopify, and Elon Musk’s social media platform X.
The post Cloudflare Outage Hits Major Websites appeared first on TechRepublic.
The company plans to advance its identity exposure management capabilities and pursue M&A opportunities.
The post Flare Raises $30 Million for Threat Exposure Management Platform appeared first on SecurityWeek.
Recently, Cloudflare and Perplexity came at odds recently as the former alleged Perplexity of stealth…
Cloudflare Blames Perplexity Of Stealth Data Scraping – Perplexity Refutes on Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses.
You may or may not remember my article Mount Synology NAS in Linux. Being the lucky owner of a Synology DS720+, I sometimes do some interesting things on it besides the standard stuff. And since this site is also my online notebook, I have collected all the things I have configured on my NAS in this article.