Reading view
AIPentestKit – AI-Augmented Red Team Toolkit for Recon, Fuzzing and Payload Generation
What is a Pentester, and Can They Prevent Data Breaches?
With the cost of data breaches at an all-time high, organizations are working to proactively identify areas of risk on the network. Using pentesters to conduct penetration (pen) testing is becoming more common. To protect themselves, businesses must know their risk areas before hackers find vulnerabilities. Organizations can lower their attack risk by protecting against weaknesses or eliminating them.
The 2022 IBM Cost of a Data Breach found that data breaches cost an average of $4.35 million per breach, an increase of 12.7% from 2020. For many businesses, breaches are becoming a “when”, not an “if” proposition. Of the organizations participating in the study, 83% have experienced more than one data breach — and only 17% said it was their first time.
As a result, many organizations are turning to pen testing to improve their overall security.
What is Penetration Testing?
During pen testing, pentesters determine how secure an app or network is by trying to break into it. Pentesters often use black box testing, where the tester does not know the underlying infrastructure, apps or code. The process allows pentesters to conduct the tests from the perspective of an outside hacker and uses automated processes to test vulnerabilities.
Other forms of pen testing can be used as well. White box pen testing relies on the tester’s knowledge of the infrastructure to quickly test security using specialized tools. Gray box testing blends white box and black box testing as the tester uses personal knowledge of the infrastructure and both manual and automated tools to exploit weaknesses.
Pen testing provides numerous benefits to companies, including infrastructure knowledge and fewer errors. While some companies balk at the initial price, the approach saves significant costs by reducing risk and the likelihood of a breach. Companies regulated by compliance guidelines often turn to pen testing as part of their compliance process.
While penetration testing is similar to ethical hacking, some differences exist. Mainly, penetration testing focuses on breaching specific systems to take over the environment. Ethical hacking, on the other hand, uses all hacking techniques. Ethical hackers are usually not company employees, although some companies hire ethical hackers as full-time employees. Bug bounty programs are a bit similar, but they’re more focused on all types of bugs instead of just breaching a system. Because bug bounty programs are open to the cybersecurity community, external hackers typically participate as well as the occasional internal employee.
Responsibilities of a Pentester
Pentesters who work as contractors are typically responsible for following testing protocols designed by the hiring agency or organization. Full-time pentesters usually start with a goal and then determine which tools and methods will best help them reach it. After completing their tests, pentesters write documentation detailing the results to help make security changes.
In addition to technical skills, pentesters need good written and verbal communication skills. Pentesters often need to collaborate with the IT department to help create solutions based on the results of the tests. Because of the types of attacks happening in the real world and the technology used by cyber criminals, pentesters need to stay on top of the latest trends in the cybersecurity industry.
Pursuing a Career as a Pentester
Some companies require pentesters to have a computer science degree or cybersecurity certificate. However, many others accept on-the-job experience — especially experience in the cybersecurity industry. While some companies may require a bachelor’s degree, others look for candidates with digital badges or certifications.
Some companies hire internal pentesters, especially for white box pen testing. However, contract pentesters hired for specific projects typically conduct black box pen testing to ensure they don’t have prior knowledge of the infrastructure. If you are looking for a job as a pentester, consider looking for both full-time employment and contract gigs.
Pentesters looking for full-time employment often find jobs at non-technical companies that want to ensure their infrastructure is secure. Other testers work for cybersecurity firms that offer services to other companies. With IT spending on cybersecurity increasing as risks escalate, the demand for pentesters will also likely continue to climb.
Overall, pen testing is a great entry-level career for tech workers or people who want to enter the cybersecurity field. While some technical knowledge is needed, many of the tools and techniques are learned on the job.
The post What is a Pentester, and Can They Prevent Data Breaches? appeared first on Security Intelligence.
See Your Cyber Defenses with an Adversarial Perspective Using Red Teaming and Pentesting
The Complementary Benefits of Red Teaming and Pentesting
Deploying Complementary Cybersecurity Tools
In our previous article, we talked about the growing number of cybersecurity tools available on the market and how difficult it can be to choose which ones you need to deploy to protect your information and infrastructure from cyberattack. That article described how Asset Discovery and Management solutions work in concert with Pentesting to ensure that you are testing all of your assets. In this article, we’ll take a look at Red Teaming and how it works together with Pentesting to give you a thorough view of your cybersecurity defenses.
What is Red Teaming and How Is It Different from Pentesting?
Red Teaming and Pentesting are often confused. Red Teaming is a simulated cyberattack on your software or your organization to test your cyber defenses in a real world situation. On the surface this sounds a lot like Pentesting. They are similar and use many of the same testing techniques. But Red Teaming and Pentesting have different objectives and different testing methodologies.
Pentesting Objectives and Testing
Pentesting focuses on the organization’s total vulnerability picture. With Pentesting, the objective is to find as many cybersecurity vulnerabilities as possible, exploit them and determine their risk levels. It is performed across the entire organization, and in Synack’s case it can be done continuously throughout the year but is usually limited to a two-week period. Pentesting teams are best composed from security researchers external to the organization. Testers are provided with knowledge regarding organization assets as well as existing cybersecurity measures.
Red Team Objectives and Testing
Red Teaming is more like an actual attack. Researchers usually have narrowed objectives, such as accessing a particular folder, exfiltrating specific data or checking vulnerabilities per a specific security guideline. The Red Team’s goal is to test the organization’s detection and response capabilities as well as to exploit defense loopholes.
Red Teaming and Pentesting Work Together
There are a lot of articles floating around the internet describing Pentesting and Red Teaming and offering suggestions on which tool to choose for your organization. The two solutions have different objectives, but they are complementary. Pentesting provides a broad assessment of your cybersecurity defenses while Red Teaming concentrates on a narrow set of attack objectives to provide information on the depth of those defenses. So why not deploy both? A security program that combines Red Teaming with Pentesting gives you a more complete picture of your cyber defenses than either one alone can provide.
Traditionally, Red Teaming and Pentesting have been separate programs carried out by separate groups or teams. But Synack offers programs and solutions that combine both Pentesting and Red Teaming, all performed via one platform and carried out by the Synack Red Team, our diverse and vetted community of experienced security researchers.
With Synack you have complete flexibility to develop a program that meets your security requirements. You can perform a Pentest to provide an overall view of your cybersecurity posture. Then conduct a Red Teaming exercise to check your defenses regarding specific company critical infrastructure or your adherence to security guidelines such as the OWASP (Open Web Application Security Project) Top 10, or the CVE (Common Vulnerabilities and Exposures) Checklist.
But don’t stop there. Your attack surface and applications are constantly changing. You need to have a long-term view of cybersecurity. Synack can help you set up continuous testing, both Pentesting and Red Teaming, to ensure that new cybersecurity gaps are detected and fixed or remediated as quickly as possible.
Learn More About Pentesting and Red Teaming
To learn more about how Synack Pentesting can work with Red Teaming to help protect your organization against cyberattack, contact us.
The post See Your Cyber Defenses with an Adversarial Perspective Using Red Teaming and Pentesting appeared first on Synack.
Five Big Takeaways from Verizon’s 2022 Data Breach Investigations Report
By Kim Crawley
The annual Verizon Data Breach Investigations Report is a wealth of valuable information about the state of cybersecurity today.
Of course, data breaches remain one of the biggest problems in cybersecurity. Many of the worst breaches expose financial data, authentication credentials, and sensitive legal and medical information. In the wrong hands, this data can help cybercriminals access organizations’ and individuals’ most sensitive data and valuable networks.
Ransomware that targets enterprises is also growing. In fact, ransomware incidents are up 13 percent from the previous year, a larger increase than the previous five years combined. Another data breach vulnerability trend is an increase in human exploitation, whether by phishing, stolen credentials or user errors.
The DBIR is a massive report that resulted from Verizon analyzing a large number of data breaches, which they’ve also verified directly for authenticity. Here’s how Verizon determines which breaches to include:
“The incident must have at least seven enumerations (e.g., threat actor variety, threat action category, variety of integrity loss, et al.) across 34 fields or be a DDoS attack. Exceptions are given to confirmed data breaches with less than seven enumerations. The incident must have at least one known VERIS threat action category (hacking, malware, etc.).”
Verizon acknowledges that many data breaches still go undetected. Nonetheless, as organizations improve their systems for detecting indications of compromise (IOCs), there’s a lot of useful data to be analyzed.
Here are five key findings:
- Web application “hacking” and denial of service attacks are the most common actions that threat actors perform in order to unlawfully access sensitive data in networks. For the sake of the report, hacking is defined as “attempts to intentionally access or harm information assets without (or exceeding) authorization by circumventing or thwarting logical security mechanisms.”
- Seventy percent of breaches involve web application hacking, 45 percent involve denial of service, 15 percent involve backdoor malware, 15 percent involve ransomware and 10 percent involve email.
- Malicious access to credentials led to just under 50 percent of breaches, phishing in a bit under 20 percent and vulnerability exploits about 10 percent.
- Data breaches are mainly caused by external threat actors, but internal threat actors are still a significant risk, too. About 80 percent of threat actors are external to the targeted organization, and 20 percent are internal—an organization’s own employees, contractors and other insiders.
- Even though internal threat actors conduct fewer attacks, internal attacks expose the most records and therefore lead to more destructive data breaches. External threat actor breaches expose a median of 30,000 records, internal threat actor breaches expose a median of 375,000 records, and threat actors with a partnership relationship (often in the supply chain) expose a median of 187,500 records.
Whenever organizations are testing to see how vulnerable they are to a data breach, it’s important to simulate internal, external and supply chain attacks. Web application pentesting is also more important than ever. As DBIR makes clear, it’s critical that every organization test for unauthorized credential exploitation and phishing attacks, too.
Thank you Verizon for helping our industry better understand data breach threats! For more information about how Synack can help organizations prevent data breaches, get in touch here.
The post Five Big Takeaways from Verizon’s 2022 Data Breach Investigations Report appeared first on Synack.
How Synack Is Disrupting Pentesting To Find Vulnerabilities Faster
Traditional Pentesting Is a Static Solution To a Dynamic Problem
Recently, Microsoft disclosed four zero-day vulnerabilities in Microsoft Exchange Servers. A Research Director from Palo Alto Networks claimed that adversaries were scanning for vulnerabilities within 25 minutes of vulnerabilities being released. Synack customers discovered the critical Apache Log4j vulnerability (CVE-2021-44228) within hours of its disclosure through a Synack CVE check offering. Scanning traffic for the vulnerability piqued just five days after the disclosure and has continued. There has never been a higher need for fast reporting and remediation timelines on high-priority vulnerabilities.
In the 1970s, James P. Anderson invented point-in-time pentests as a public policy and technical innovation to secure communication systems and other networks from malicious hackers. But the threat landscape and the sophistication of digital threats have changed vastly since then, having a significant impact on pentesting. Other major factors include increased attacker sophistication and vulnerabilities, new DevSecOps workflows and collaboration/security software (Splunk, Jira, Slack, SOAR, etc.), and growing adoption of cloud services, infrastructure, and storage. With these macro changes, the traditional way of doing pentesting is too slow, disruptive, and ineffective. The good news is that Synack has heard these customer challenges and developed an on-demand pentest that’s continuous, performance-driven, and intelligent.
Cloud Services & Providers Are Dynamic
Point-in-time pentesting cannot keep pace with agile cloud services, which are often spun up around specific projects. On average, large organizations add 3.5 new publicly accessible cloud services per day. Remote code vulnerabilities or external misconfigurations can occur at any time and leave organizations’ public and private assets vulnerable.
New DevSecOps Workflows & Security Software Stack
The average security team now uses about 45 cybersecurity-related tools on their network. Collaboration tools have replaced email. Typically, most security, ops, and development teams communicate using Splunk, Slack, Jira, or ServiceNow. Code releases are constant. It’s important to have a DevSecOps process that automates a lot of the work across these platforms, or risk spending time on administrative processes that distract from securing your organization.
Increase In Sheer Number of Vulnerabilities & More Sophisticated Adversaries
Security researchers have found an increasing number of vulnerabilities in recent years. In fact, the number of new vulnerabilities increased by 127% from 2017-2018 compared to single digit growth rates in previous years. An average of roughly 17,416 new vulnerabilities are added each year and point in time pentests can’t keep up. Attackers are more efficient than ever with some popular exploitable vulnerabilities pursued within a hours of when a patch is released (i.e. Microsoft Exchange CVE-2021-26855, Apache Log4j CVE-2021-44228)
What Pentesting Challenges Are Security Leaders Facing Today?
Speed
Typically, in a traditional pentest model an organization seeks out an established consulting firm to do the work. As the complexity of assets has increased, pentesters specialize; they vary in attack types (reverse engineering, password cracking, etc.), and focus on certain asset types (IoT, mobile, web, IaaS). Hiring enough skilled personnel is a top challenge to implementing and maintaining a pentest program. As a result, pentesters with sought-after skill sets may need to be scheduled months in advance. Scheduling a new program, or launching a new test can take weeks or even months, especially if the team needs to work on site.
Disruption
Too often, security teams do not receive sufficient support to effectively communicate results. Vendors send pentest reports in PDFs or Excel via email. A security team member needs to copy and paste information into ticketing tools like Jira or ServiceNow, or collaboration tools (i.e. Slack). Reports are written in a way that’s not accessible to other key teams like legal, operations, IT or development. If they have questions, security teams can’t easily communicate with researchers that surface the vulnerabilities. Finally, once a vulnerability is closed, it’s not possible to re-test the vulnerability in a standard pentest. Vulnerabilities can fall between the cracks and take months or years to remediate.
Effectiveness
One of the most frustrating aspects of penetration testing is the inability to see meaningful progress over time. How can you create a benchmark for your defenses? What security metrics should you consider to take stock of your various assets besides the CVSS score or quantity of vulnerabilities? Traditional pentesting does not provide holistic risk scores at the asset or company level.
In response to these challenges, Synack offers a continuous, intelligent, and performance-driven on-demand pentest to improve your organization’s security posture overtime.
Synack Provides a Better Way to Pentest
Harness the Best Talent Globally On-Demand
More than 1,500 vetted security researchers from across the globe are actively working with the Synack Red Team, hunting for vulnerabilities around the clock. The SRT is second to none when it comes to skills and trust, thanks to rigorous vetting and assessment of researcher expertise in the application process. Synack Ops can launch new pentests in as little as 3–5 days and start on-demand security tasks such as asset discovery in seconds.
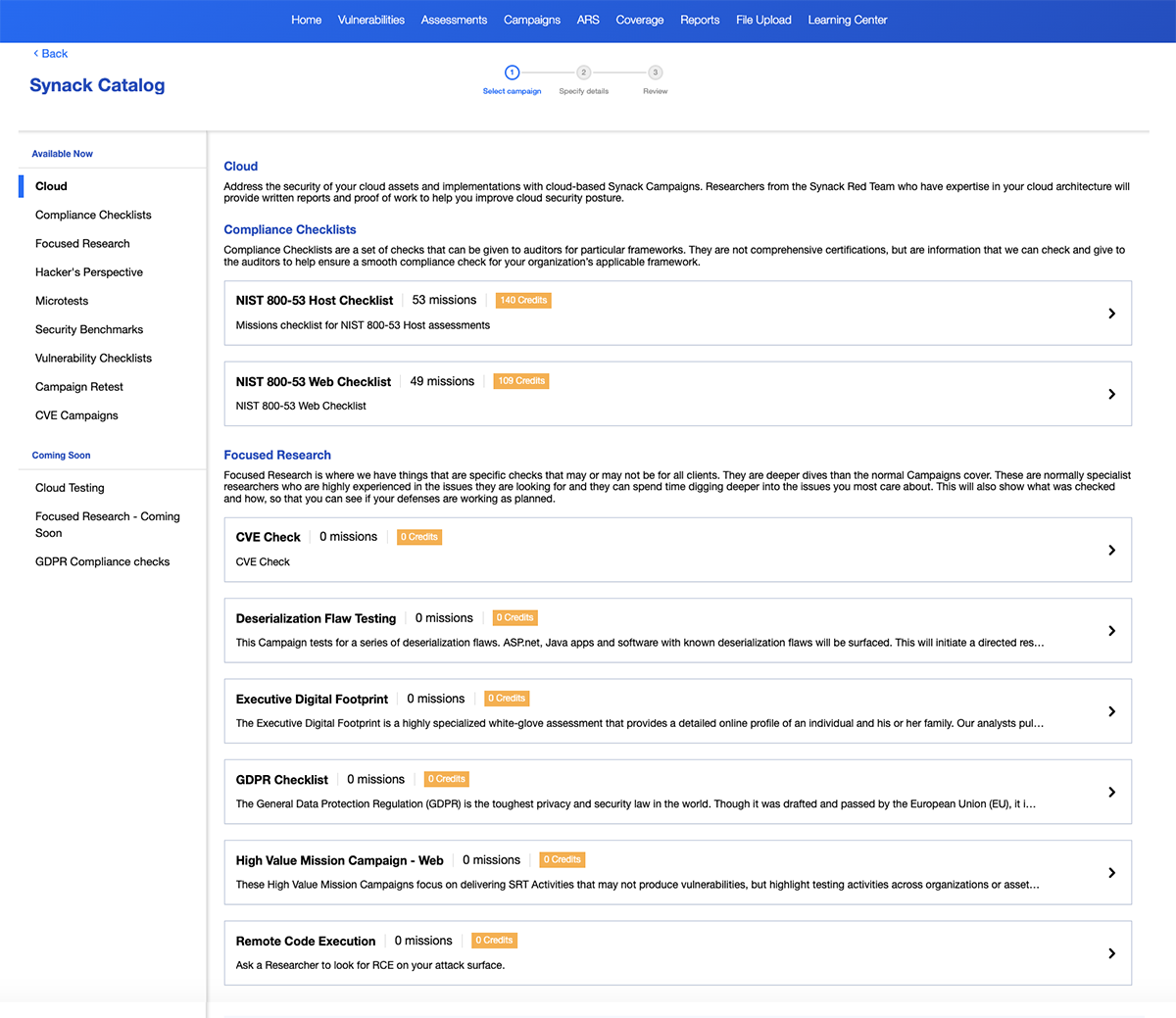
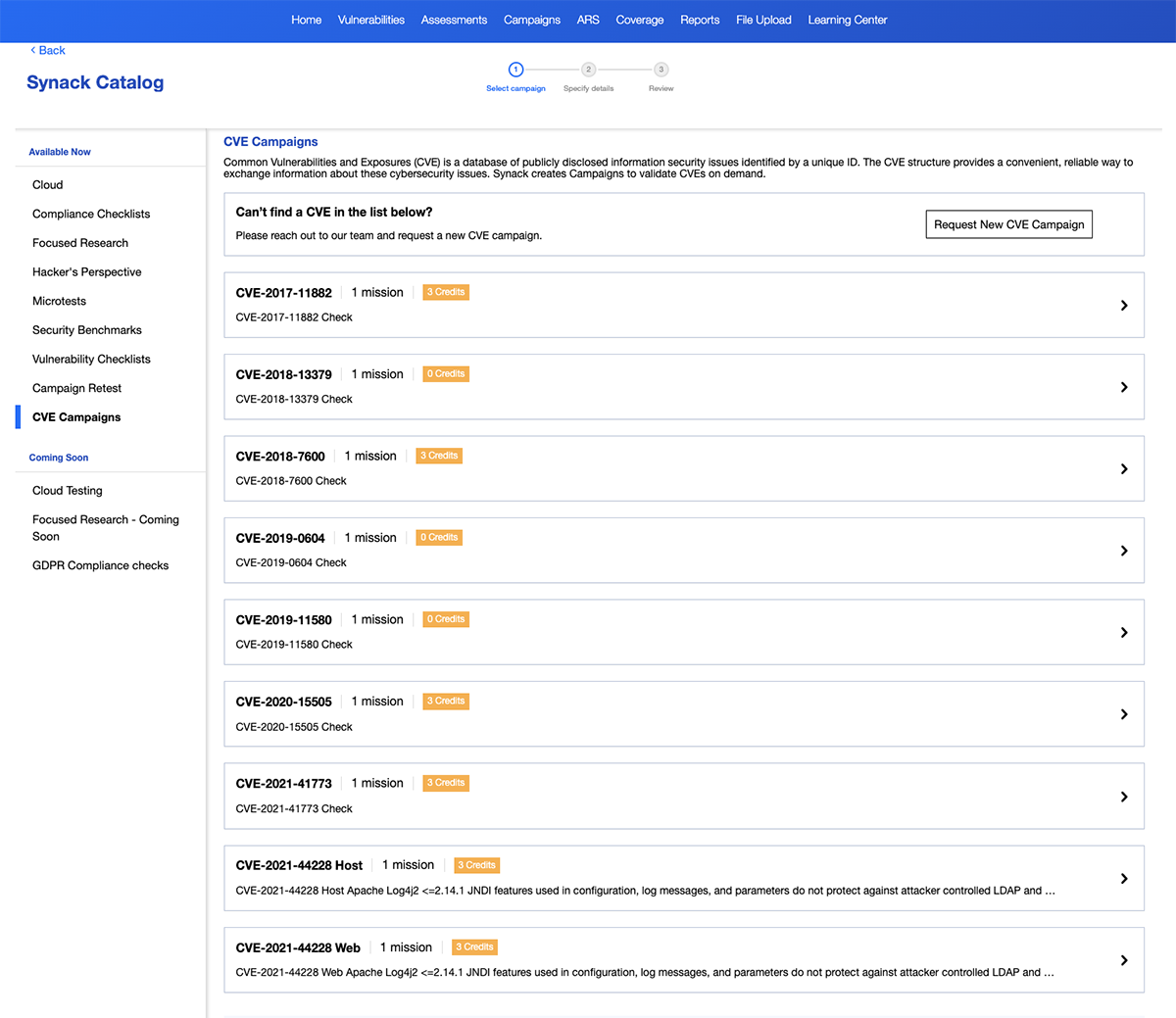
Test for Cloud Misconfigurations, New Vulnerabilities, and Dynamic Host Changes
Organizations need to be wary of new vulnerabilities like Log4J or SolarWinds Orion. It’s never been more important to continually test public and private cloud assets. Synack offers configuration reviews of Azure environments, CVE checks, and testing for dynamic internal and external hosts. Synack integrates with numerous cloud providers (AWS, Azure and GCP). Additionally, our API pulls from major cloud providers daily to help detect any changes to external hosts when Synack is testing.
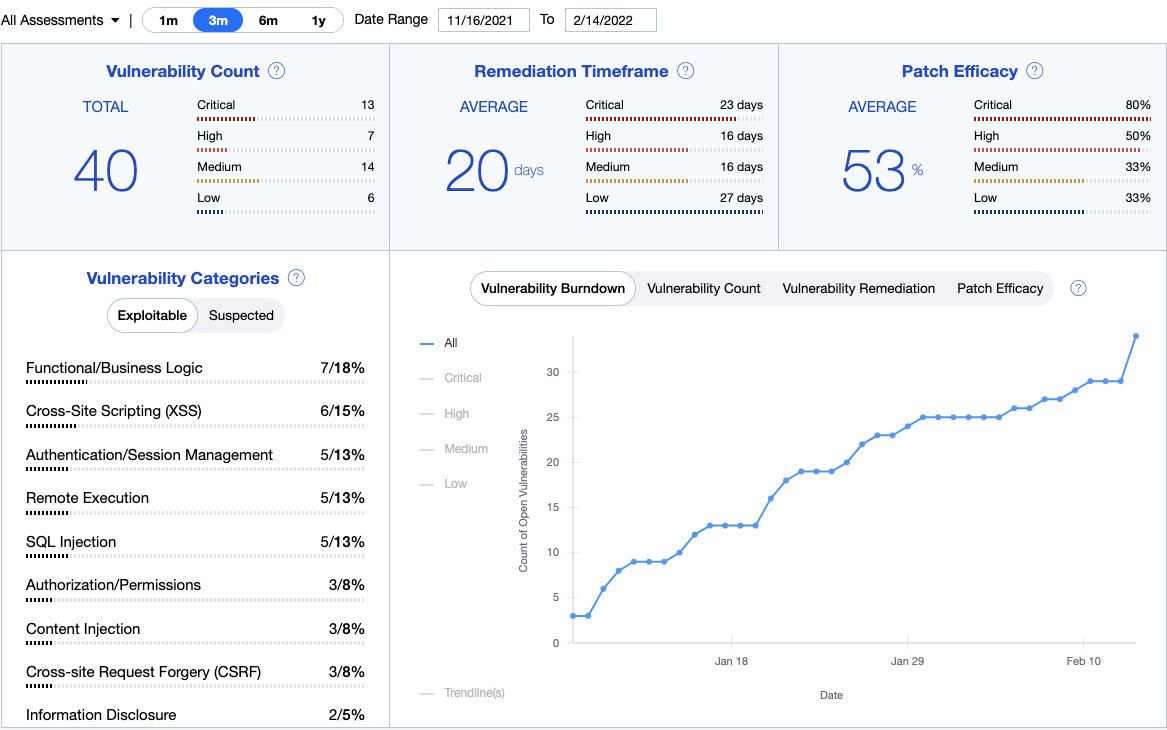
Measure Performance Overtime with Metrics on Remediation, Patch Efficacy, and Risk Scoring
With traditional pentesting, there are not a lot of great metrics for measuring your security status overtime. Number of vulnerabilities found can be a helpful benchmark, but often don’t include other critical stats such as vulnerability remediation timelines. Synack provides a security risk score that takes a holistic approach based on metrics like attacker cost, severity of findings, and remediation efficiency.
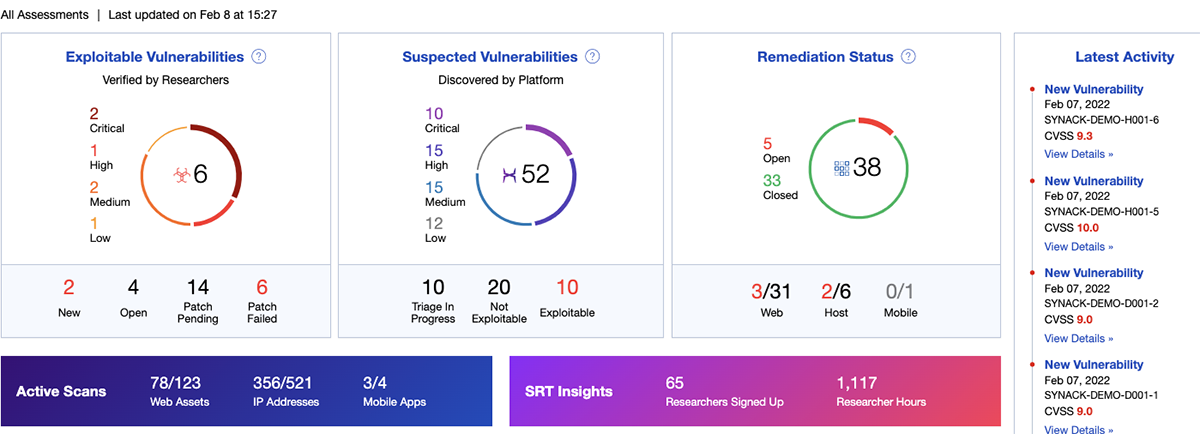
Scale Testing with a Technology Platform
Synack offers 43% more coverage of your assets than a traditional pentest with SmartScan, a scanner that you can use on your medium priority assets to surface vulnerabilities. These “suspected vulnerabilities” are triaged by the researchers in order to provide you with actionable results.
Compliance (PCI-DSS, FISMA, HIPAA) Ready Reports & Actionable Results
Traditional pentests are built for your organization’s compliance objectives, but lack the agility necessary for digital transformation. Synack provides easily readable and compliance-ready reports on a wide range of metrics (i.e. vulnerability severity, vulnerability status, steps to reproduce, recommended fixes, remediation status) for legal, policy and leadership teams as well as real-time metrics on exploitable vulnerabilities that are the top priority for security, ops and development teams. Synack also integrates with Jira, ServiceNow, Splunk, and offers an API to facilitate faster DevSecOps processes.
Attackers are more vigilant than ever. Security teams need to be one step ahead of their adversaries to help make sure they are keeping their organizations’ environments safe. The choice is clear. Synack provides 159% more ROI than a traditional pentest.
Change your pentest provider today and schedule a demo with our team, or download a solutions overview of Synack 365—our continuous pentest offering.
The post How Synack Is Disrupting Pentesting To Find Vulnerabilities Faster appeared first on Synack.
Synack Partners with Microsoft to Help Customers Improve Their Microsoft Azure Security Posture
Synack works with Microsoft to provide a one-stop shop for Microsoft Azure-based cloud security.
Microsoft Azure comes equipped with all the right security controls, but effective deployment and management of these controls is an ongoing process, driven by evolution and risk tolerance . Proper implementation of cloud rollouts and ongoing maintenance can be a challenge, even for large organizations, leading to a lack of protections such as least privilege for access controls. And attacks on the cloud appear to be growing. Verizon’s 2021 Data Breach Investigations Report found that “external cloud assets were more common than on-premises assets in both incidents and breaches.”
Security teams are left responsible for not only securing cloud assets, but also for ongoing cyber hygiene training and developing common sense policies to protect an organization’s assets. It can be an overwhelming task. Based on an increase in cloud misconfiguration vulnerabilities reported by the Synack Red Team in 2020, it is clear the existing solutions and frameworks are fragmented—leaving ample room for malicious exploits.
But now, finally, there is a better way!
By combining the power of Synack, the premier crowdsourced platform for on-demand security expertise, with Microsoft’s Azure Security Modernization (ASM) solution, enterprise and government organizations now have a scalable solution for cloud security planning, management, and improvement.
Per a Microsoft Blog Post from earlier this year, Microsoft Azure applications and infrastructure deployments have grown at leaps and bounds for nearly 20 years. In parallel, Microsoft has emerged as a cybersecurity leader—recently announcing a whopping $10 billion in revenue for its security business over the past 12 months. This represents more than 40 percent year-over-year growth (Vasu Jakkal, 2021). Microsoft security experts have deployed Microsoft services and solutions to secure 400,000 customers across 120 countries, including 90 of the Fortune 100. Integrations such as the one with Synack amplify Microsoft’s ability to continue to grow and innovate across all types of organizations.
Microsoft ASM solution helps its clients stay ahead of adversaries. It deploys a Microsoft Azure-centric, continuous approach to security (see chart below), led by Microsoft security experts, and powered by the Synack Platform. ASM includes a four-phase continuous security model: Plan, Develop, Deliver, and Measure which programs, implements, and tests Microsoft Azure security requirements and controls.
Synack’s unique combination of a continuous, crowdsourced platform and smart vulnerability detection technology makes the discovery of security vulnerabilities easy, fast, and actionable! Synack-found vulnerabilities are reported and fed into ASM’s “Measure” phase to enable future “Planning” phases with real-world security testing data. Synack’s controlled and 24/7 testing, alongside its Azure integrations, ensures the changing boundaries and assets of today’s dynamic environments are tested safely and comprehensively.
“Thanks to our integration with Synack, we can now go beyond reviewing security configurations against recommended practices to include real time scanning of an environment against known security vulnerabilities. This allows us to help our customers further reduce risk by having a more comprehensive and tailored remediation plan fit to their needs.” says Heath Aubin, Director of Business Program Management, Security Strategy and Solutions at Microsoft Corp.
Synack’s cloud integrations allow for quick deployment of a variety of pentesting methodologies within a Microsoft Azure environment based on an organization’s goals and requirements. The first is open vulnerability discovery to uncover and report exploitable issues within a Microsoft Azure environment. The second includes targeted, offensive assessments aligned to the Microsoft Azure Security Benchmark.
Synack designed these targeted tests alongside the ASM Solution Owners for an on-demand mechanism to quickly highlight areas of weakness within a Microsoft Azure environment.
Leveraging the integration between Synack and ASM customers can experience a comprehensive testing and mitigation sequence to support compliance, asset management and planning, and expert level insight into the security of their Azure assets.
To find out more, download our datasheet here.
The post Synack Partners with Microsoft to Help Customers Improve Their Microsoft Azure Security Posture appeared first on Synack.