Reading view
CVE attack
Last week I was working on retried HTB machine Optimum. Cool example for simple enumeration with attack using vulnerability for service (web file server), and then privilege escalation using local exploit for unpatched Windows 2012 server. It is example of real case scenario. Great to make
Top 10 Most Critical CVEs Added in 2020
The post Top 10 Most Critical CVEs Added in 2020 appeared first on Detectify Blog.
Detectify security updates for 17 June
The post Detectify security updates for 17 June appeared first on Detectify Blog.
Detectify security updates for 20 February
The post Detectify security updates for 20 February appeared first on Detectify Blog.
See Your Cyber Defenses with an Adversarial Perspective Using Red Teaming and Pentesting
The Complementary Benefits of Red Teaming and Pentesting
Deploying Complementary Cybersecurity Tools
In our previous article, we talked about the growing number of cybersecurity tools available on the market and how difficult it can be to choose which ones you need to deploy to protect your information and infrastructure from cyberattack. That article described how Asset Discovery and Management solutions work in concert with Pentesting to ensure that you are testing all of your assets. In this article, we’ll take a look at Red Teaming and how it works together with Pentesting to give you a thorough view of your cybersecurity defenses.
What is Red Teaming and How Is It Different from Pentesting?
Red Teaming and Pentesting are often confused. Red Teaming is a simulated cyberattack on your software or your organization to test your cyber defenses in a real world situation. On the surface this sounds a lot like Pentesting. They are similar and use many of the same testing techniques. But Red Teaming and Pentesting have different objectives and different testing methodologies.
Pentesting Objectives and Testing
Pentesting focuses on the organization’s total vulnerability picture. With Pentesting, the objective is to find as many cybersecurity vulnerabilities as possible, exploit them and determine their risk levels. It is performed across the entire organization, and in Synack’s case it can be done continuously throughout the year but is usually limited to a two-week period. Pentesting teams are best composed from security researchers external to the organization. Testers are provided with knowledge regarding organization assets as well as existing cybersecurity measures.
Red Team Objectives and Testing
Red Teaming is more like an actual attack. Researchers usually have narrowed objectives, such as accessing a particular folder, exfiltrating specific data or checking vulnerabilities per a specific security guideline. The Red Team’s goal is to test the organization’s detection and response capabilities as well as to exploit defense loopholes.
Red Teaming and Pentesting Work Together
There are a lot of articles floating around the internet describing Pentesting and Red Teaming and offering suggestions on which tool to choose for your organization. The two solutions have different objectives, but they are complementary. Pentesting provides a broad assessment of your cybersecurity defenses while Red Teaming concentrates on a narrow set of attack objectives to provide information on the depth of those defenses. So why not deploy both? A security program that combines Red Teaming with Pentesting gives you a more complete picture of your cyber defenses than either one alone can provide.
Traditionally, Red Teaming and Pentesting have been separate programs carried out by separate groups or teams. But Synack offers programs and solutions that combine both Pentesting and Red Teaming, all performed via one platform and carried out by the Synack Red Team, our diverse and vetted community of experienced security researchers.
With Synack you have complete flexibility to develop a program that meets your security requirements. You can perform a Pentest to provide an overall view of your cybersecurity posture. Then conduct a Red Teaming exercise to check your defenses regarding specific company critical infrastructure or your adherence to security guidelines such as the OWASP (Open Web Application Security Project) Top 10, or the CVE (Common Vulnerabilities and Exposures) Checklist.
But don’t stop there. Your attack surface and applications are constantly changing. You need to have a long-term view of cybersecurity. Synack can help you set up continuous testing, both Pentesting and Red Teaming, to ensure that new cybersecurity gaps are detected and fixed or remediated as quickly as possible.
Learn More About Pentesting and Red Teaming
To learn more about how Synack Pentesting can work with Red Teaming to help protect your organization against cyberattack, contact us.
The post See Your Cyber Defenses with an Adversarial Perspective Using Red Teaming and Pentesting appeared first on Synack.
Preparing for the Next Log4j in the Face of the Cyber Talent Gap
When the Log4j vulnerability emerged in December 2021, Synack and our clients’ security teams immediately sensed its urgency. The Synack Red Team began testing within hours of the initial discovery for our customer base.
Almost a year later, Log4j continues to show up in our pentesting results. Here are some quick stats from our findings:
- 750+ instances of the Log4j (CVE-2021-44228) missions run by SRT researchers since 2021 as part of our zero day response coverage
- 100+ susceptible instances found so far as part of Synack Penetration Testing
- Over 2 million IPs checked to date
Log4j Is “Endemic,” Says Federal Cyber Board
The Cyber Safety Review Board (CSRB) called Log4j (CVE-2021-44228) an “endemic” vulnerability in the board’s first published report. The group of public and private sector cybersecurity leaders stated that the vulnerability is expected to continue to be a prominent threat for “a decade or longer.”
The CSRB’s consideration of Log4j as a persistent threat points to the critical nature of such zero days. They are not something to be solved in the week they appear, with security teams “working through the weekend” and then moving on. They highlight the larger need for readily available talent and emergency response processes across a longer span of time.
Luckily, there have been no successful Log4j-based attacks to critical infrastructure, according to the CSRB. However, the board urges organizations to continue to mitigate risk related to Log4j and prepare for future zero day vulnerabilities of similar criticality.
Log4j and the Cyber Talent Gap – Surge Capacity
Nearly two in three organizations say they are understaffed in cybersecurity. But even for those that report having enough cyber talent on hand, the surge demand needed to respond to a vulnerability like Log4j can still be taxing. The CSRB report states:
“Perhaps most significantly, the force exerted on the urgent response and the challenges in managing risk also contributed to professional “burnout” among defenders that may, compounded with the generally intense pace of many cybersecurity jobs, have a long-term impact on the availability of cybersecurity talent.”
Chris Hallenbeck writes for VentureBeat about lessons learned in the face of Log4j, including the fact that the “skills shortage is an existential threat.” If organizations are to effectively prepare for future CVEs and zero days, they must consider their hiring strategies in the face of the cyber talent shortage, while also considering how to deal with potential burnout and stress from surge demand in the face of emergency.
Preparing for Zero Day Response with Human Talent
The CSRB issued recommendations to mitigate zero day risks, including the documentation of a vulnerability management and response program, and consideration of “cultural shifts” that are “necessary to solve for the nation’s digital security.”
Synack believes that the most effective way to test for a zero day vulnerability is with human expertise. Scanners are not able to detect zero day vulnerabilities until they are updated with a signature for the vulnerability.
In the face of the cybersecurity talent gap, testing with humans to meet the surge demand of a zero day can be challenging. That’s why on-demand access to a community of researchers is paramount. Synack provides access to such a community, the Synack Red Team, through a SaaS platform, for on-demand zero day response. This talent augmentation can be a key cultural shift for companies struggling to hire or retain cyber talent, and can help prevent an in-house team from experiencing the severe burnout alluded to above.
Within the Synack Platform is a catalog of CVEs that can be tested on-demand by skilled SRT researchers. When Log4j first emerged, it was added to the catalog within hours, and top researchers began testing and collaborating on methodologies.
After only a few days, Synack had checked over half a million IP addresses confirming the status of thousands of CVE-2021-44228 checks and providing detailed reports containing proof of work and methodologies.
Contact us today for a conversation about how we can help you mitigate Log4j risk or prepare for future zero days.
The post Preparing for the Next Log4j in the Face of the Cyber Talent Gap appeared first on Synack.
Researchers Uncover Record Number of Zero-Days. That’s Actually Good News.
By Kim Crawley
The latest research from zero-day hunters at Google shows that reporting and detection tools are improving.
Google researchers uncovered more than double the number in-the-wild zero-days last year than any other period since it started tracking these dangerous software vulnerabilities in 2014.
“Is it that software security is getting worse? Or is it that attackers are using 0-day exploits more? Or has our ability to detect and disclose 0-days increased? When looking at the significant uptick from 2020 to 2021, we think it’s mostly explained by the latter,” according to Maddie Stone, a security researcher at Google Project Zero, the company’s team that tracks zero-days.
In a recent blog post detailing the 2021 findings, the group detailed the 58 zero-days that it detected as well as trends, attack patterns and techniques they were able to identify last year, too. Even though the group uncovered more than double the number of the previous high in 2015 (28 found), attacker techniques haven’t significantly evolved.
“With this record number of in-the-wild 0-days to analyze, we saw that attacker methodology hasn’t actually had to change much from previous years. Attackers are having success using the same bug patterns and exploitation techniques and going after the same attack surfaces,” wrote Stone.
It’s tough enough for organizations to manage and mitigate known vulnerabilities, but zero-day exploits pose a unique challenge to all organizations. They are often the attackers’ most powerful tool and when executed against businesses, organizations and individuals can have devastating consequences. As Google noted, there were many reports of zero-day exploits used against journalists, human rights groups and government officials last year.
Key findings from Google’s Project Zero report:
- The exploits detected in 2021 are very similar to the exploits Google Project Zero detected in previous years. There are new CVE records, but the nature of the vulnerabilities and how they’re exploited are all fairly typical relative to previous trends.
- Sixty-seven percent (or 39) of the zero-days found in 2021 were memory corruption vulnerabilities. How memory is being used is the main vector for zero-day exploits. They include four buffer overflows, four integer overflows, six out-of-bounds read and writes, and 17 use-after-frees. Maybe the Project is getting better at monitoring memory, or maybe volatile data is more ripe for zero-day exploitation than data in storage.
- Nearly all of the 58 zero-days detected in 2021 follow familiar patterns. But there’s one outlier, CVE-2021-30860, which is an integer overflow vulnerability in the CoreGraphics PDF decoder in iOS 14.8 and iPadOS 14.8, macOS Big Sur 11.6 and watchOS 7.6.2. Security researchers Samuel Groß and Ian Beer noted how unusual the exploit is: “The bootstrapping operations for the sandbox escape exploit are written to run on this logic circuit and the whole thing runs in this weird, emulated environment created out of a single decompression pass through a JBIG2 stream. It’s pretty incredible, and at the same time, pretty terrifying.” Indeed, Google Project Zero said it hopes this is a trend of attackers having to work harder to successfully execute a zero-day exploit.
- Some of the exploits involve classic cyberattack techniques, such as phishing and fingerprinting. CVE-2021-21166 and CVE-2021-30551 are great examples. Google Project Zero’s Maddie Stone and Clement Lecigne wrote: “Both of these 0-days were delivered as one-time links sent by email to the targets, all of whom we believe were in Armenia. The links led to attacker-controlled domains that mimicked legitimate websites related to the targeted users. When a target clicked the link, they were redirected to a webpage that would fingerprint their device, collect system information about the client and generate ECDH keys to encrypt the exploits, and then send this data back to the exploit server. The information collected from the fingerprinting phase included screen resolution, timezone, languages, browser plugins and available MIME types.”
Essentially, Google wants to make it harder for attackers to carry out zero-days. And there’s some evidence in its research that might be happening. While there’s progress in terms of discovering and disclosing zero-days, Project Zero does say there is still a lot of room for improvement. Specifically, they call on companies to disclose more, share more exploit samples and details of attacker techniques and to work harder to reduce memory corruption vulnerabilities.
It’s also important that once organizations know about a zero-day, they act quickly to find and fix that vulnerability. That requires vigilance and the right approach to testing with an offensive mindset to ensure an organization’s entire attack surface is hardened against the most sophisticated attackers.
Get in touch today to learn how Synack can help.
The post Researchers Uncover Record Number of Zero-Days. That’s Actually Good News. appeared first on Synack.
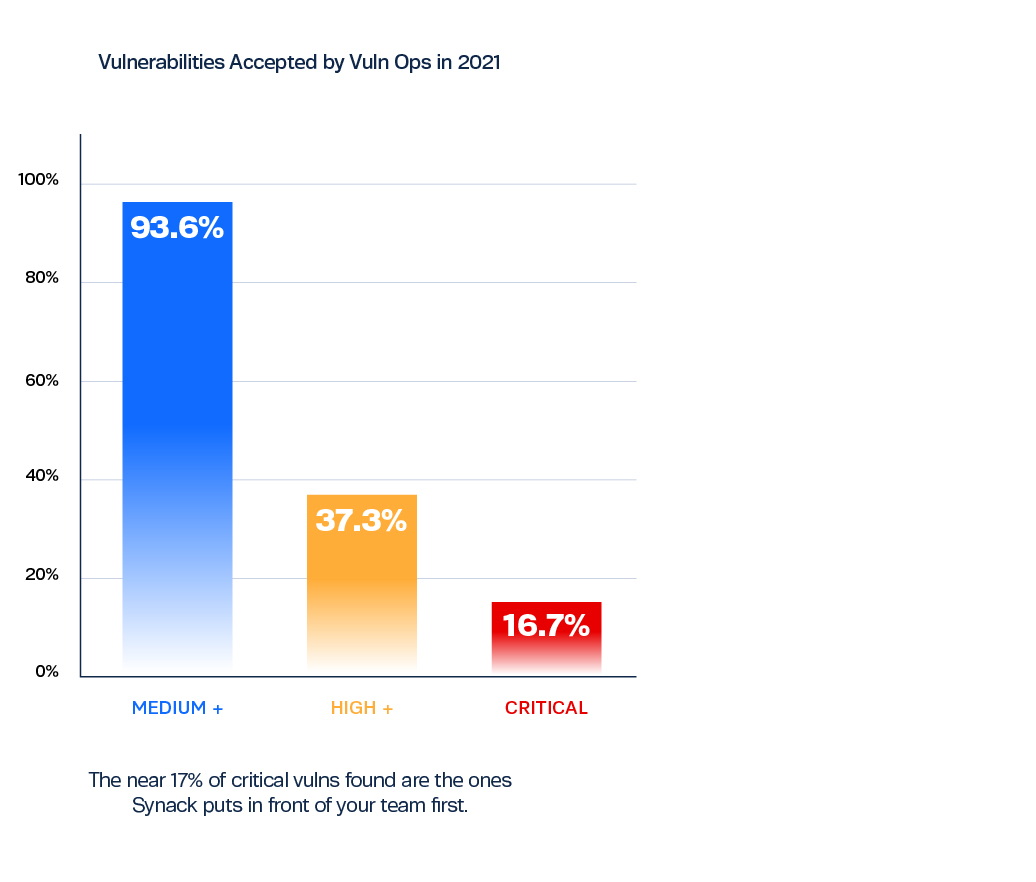
Synack Triaging Prioritizes the Vulnerabilities that Matter
Putting the Most Critical Vulnerabilities First
Vulnerability testing, whether via an automatic scanning program or human-based penetration testing, can find an overwhelming number of vulnerabilities in your system as recent trends would suggest. Since 2017, record numbers of Common Vulnerabilities and Exposures (CVEs) have been reported, with 2022 on track to set a new high.
Sorting through a record number of vulnerabilities to keep your organization secure is a daunting task without additional support and distillation.
The good news is that of all the vulnerabilities that might show up on a traditional vulnerability report, only around 5% of vulnerabilities discovered are ever exploited in the wild. And most of the exploited vulnerabilities are those with the highest CVSS (Common Vulnerability Scoring System) severity score of 9 or 10.
So how do you know which vulnerabilities in your system need to be addressed right now, and which can be put on the back burner? Some vulnerabilities are an immediate risk to the business, while others are highly unlikely to be exploited. Prioritizing critical vulnerabilities can mean the difference between preventing an attack and responding to one.
Finding and triaging critical vulnerabilities is where Synack’s pentesting outperforms traditional models. We continuously prioritize impactful vulns for your organization, surfacing only vulnerabilities that are reproducible and show exploitability.
The Synack Difference—The Vulnerability Operations Team
The Synack Platform is the only solution to harness the best in augmented intelligence for more effective, continuous pentesting. First, the Synack Red Team (SRT), a group of vetted researchers, conducts open vulnerability discovery, while our automated SmartScan provides broad attack surface coverage. Together, they find vulnerabilities across your attack surface.
Next, the Synack Vulnerability Operations team assesses vulnerabilities found by the SRT and SmartScan by using a rigorous vetting process. Noise, such as duplicate submissions by SRT or non-replicable exploits, low-impact vulns, is kept to a minimum during penetration testing and you’re ultimately served vulnerabilities that present a clear risk.
This additional step to triaging is key to faster remediation and minimizing business risk.
The Vulnerability Operations team is a group of seasoned security professionals with hacking expertise. They are full-time Synack employees with extensive vulnerability knowledge–they’ve seen tens of thousands of them. For the most accurate triaging, high impact vulnerabilities are often reviewed by multiple team members. So, when you get a vulnerability report from Synack, you know that it matters.
Remediating Exploitable Vulnerabilities with True Business Impact
The Vulnerability Ops team works alongside the SRT 365 days a year to bring order to the thousands of CVEs. When the team receives an initial vulnerability report, they will first validate the vulnerability by replicating it based on details provided in the report. When the vulnerability is confirmed, the Ops team proofreads and formats the report for utility and readability by a development team. Everything needed to reproduce the vulnerability is provided in each report.
After vulnerabilities are deemed exploitable and impactful, and the report has been detailed with steps to reproduce and suggestions on remediation, it will be published to the Synack Platform.
From there, the Synack Platform provides real-time findings on vulnerabilities found–their CVSS score, steps to remediate and evidence of the researcher’s finding. With this information you can address the vulnerabilities that are most important to your organization in a systematic and thorough manner.
Through the Synack Platform, teams are also able to check if their remediation efforts were successful with Patch Verification. Patch Verification can be requested on-demand, and the researcher will provide further communications on the patch efficacy.
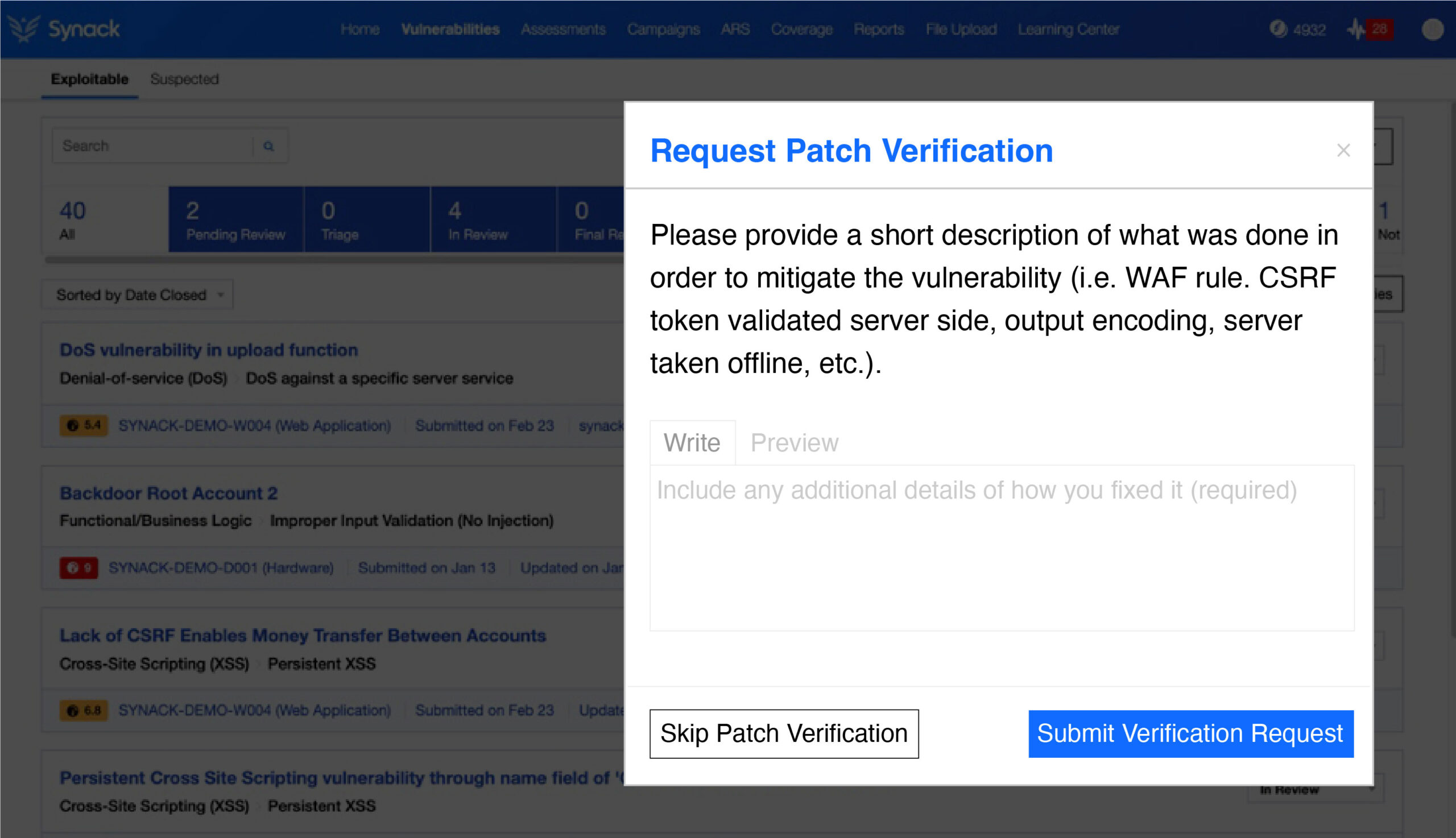
The Synack Platform facilitates delivery of vulnerabilities and
actions like submitting patch verification requests.
2021 Vulnerability Highlights
The six most popular types of vulnerabilities delivered to organizations were:
- Cross-site Request Forgery (XSRF)
- Authentication Permission
- Information Disclosure
- SQL Injection (SQLi)
- Functional Business Logic
- Authentication Session
Making the Most of Vulnerability Testing
Most organizations don’t have the resources to go chasing every vulnerability reported from initial testing. To further safeguard your organization, someone needs to determine which are true vulnerabilities and which of those are exploitable and at what level of criticality. That process is noise reduction, and it is essential for any cybersecurity operation to shoot for the highest level of noise reduction before proceeding to remediation. Synack, through the Vulnerability Operations, team can take on this task for you.
Using Synack’s unique approach to continuous pentesting, your team will be able to proceed with confidence that their remediation efforts are critical to keeping the organization secure. Get started with Synack penetration testing today.
The post Synack Triaging Prioritizes the Vulnerabilities that Matter appeared first on Synack.
3 Signs You Deserve Better Pentesting
By Kim Crawley
If your organization is pentesting like it’s 2004, you’re missing most of the ways attackers are attempting to exploit your network in 2022.
Stale, outdated pentesting practices are putting enterprises, in all industries and of all sizes, at considerable risk. In today’s rapidly evolving cyber threat landscape, malicious hackers are breaching companies and cyber criminals are infecting them with ransomware at an unprecedented rate that even the most seasoned security teams haven’t experienced.
In the words of Roman Medina, CISO at Jefferson Bank in Texas, “I do think we may miss critical issues or vulnerabilities if we stick to the same annual pentest year after year. The way we pentest has to evolve. I am looking at starting a continuous pentest service next year.”
Let’s examine the issues with traditional pentesting.
It’s slow and static
Traditional pentesting methodologies and procedures were designed for the computer networks of 15 to 20 years ago. That’s when organizations typically hosted networks on premise. Those networks changed gradually. IT teams updated operating systems and applications infrequently and added new data assets only every so often. For a deeper dive on traditional pentesting flaws check out our white paper: Traditional Pentesting: a Turtle Chasing a Cheetah
Today, cloud providers have made it much easier for enterprises to leverage fully scalable and flexible networks. Containerization and virtualization make it possible for data assets to be added or subtracted on a dime. According to research from Palo Alto Networks, organizations can, and did add as many as 693 cloud services in a day.
Unfortunately, the new paradigm of enterprise computing means the old ways to pentest won’t cut it anymore.
Pentesting annually or according to compliance requirements is too slow and too infrequent to get an accurate understanding of your organization’s vulnerabilities day to day. In 2017, the number of CVEs (common vulnerabilities and exposures) spiked significantly. Since then, each year has been a record year for the number of CVEs discovered and reported. The pace is unrelenting.
It’s disruptive
Once a traditional pentest is conducted, which can be disruptive in its own way, a physical report is delivered with results. This report doesn’t plug in to the existing ticketing tools your team might have, and it doesn’t give you clear steps for remediation. The pentest results become the elephant in the room. When is your overworked, overburdened security team going to be able to take action on pentest results?
Let’s say your team does begin to tackle the issues presented by the pentest. They’re making headway through the results, but some issues need to be retested. Patches or other fixes issued need to be verified that they were an effective remediation measure.
Leaders in charge of approving pentests likely won’t be keen on the idea of having the two guys, two laptops, two weeks repeated again. Without verification that the issues were resolved, was the original pentest of much use?
Security teams should be searching for a pentesting solution that a) provides immediate value with actionable results and b) is easy to implement so retesting and remediation verification are easy to do.
It’s ineffective
Scanners used in traditional pentests surface noisy results, distracting from critical vulnerabilities.
Network and application vulnerability scanners can spit out massive amounts of vulnerability data but without much triaging or prioritization. Much like a doctor walking into a hospital and being told every single patient is a top priority, a vulnerability manager or other security practitioner needs additional context to know which vulnerabilities to tackle first. No amount of medical schooling, or security chops, can help you decide which issues to prioritize without going back to review every case. It’s not feasible.
In short, traditional pentesting has hardly grown with the needs of the industry. It’s time to start looking for new, innovative solutions to testing your digital environment for vulnerabilities. To learn more about the burgeoning list of issues with traditional pentesting, download our white paper.
The post 3 Signs You Deserve Better Pentesting appeared first on Synack.
4 Effective Vulnerability Management Tips for Security Leaders
From the SolarWinds Orion hack to the Kaseya ransomware attack, recent incidents have proven that a single vulnerability in a company’s product or supply chain can have a massive business and brand impact—potentially even posing a national security threat. Security leaders are under more pressure than ever to improve the speed, efficiency, and effectiveness of their incident response.
To help investigate how security leaders on the front lines are handling the challenge, Synack sat down with Justin Anderson, Head of Vulnerability Management at LinkedIn, for a talk entitled, “Best Practices for Fast & Effective Vulnerability Management” on Dec. 8, 2021. Justin has years of technical experience in a wide range of contexts from the U.S. Air Force to LinkedIn, giving him a unique perspective that’s valuable for any executive or security leader dealing with vulnerability management issues. He spoke alongside Synack Product Analyst, Charlie Waterhouse. Charlie has years of experience conceptualizing security test methodologies that address vulnerability management concerns.
In fact, many of the problems that Justin has addressed in his role are similar to those Synack is looking to solve with its Campaigns product offering. Read on to learn more!
No. 1: Use Human Talent and Time Wisely
As security leaders build out their teams, the cyber talent gap continues to be a significant hurdle. The Biden administration has recognized a need to fill 600,000 cybersecurity jobs. Additionally, engineering talent, especially in Silicon Valley, is expensive and in incredibly high demand.
As a security leader, it does not make sense to hire specialized, in-house security talent. Synack supplies researchers with a variety of skill sets combined with a catalog of on-demand security products that can reduce a team’s workload from months to hours or days. Synack’s researchers’ expertise spans cloud environments such as AWS, Azure and GCP to APIs and mobile applications. Whether security teams are testing for compliance, M&A or a new product launch, Synack’s “App Store”-like experience provides a flexible array of on-demand testing and tasks, with many serving established security frameworks like OWASP Top 10 and NIST 800-53.
No. 2: Balance User Needs and Security
In the words of Charlie Waterhouse, Security Analyst at Synack, “There is some internal tension between security and user experience.” Security is increasingly part of the development process, but when does it start to hinder instead of help growth? Justin from LinkedIn added, “We live in a world where we don’t have fantastic metrics on risk reduction. We also lack metrics on user experience. Security can be a greater threat than any attacker could be. An opaque and lengthy process can slow down an entire business.”
Synack has taken this into account by providing Synack Campaigns such as those based on the Open Web Application Security Project (OWASP) Application Security Verification Standard (ASVS). The three levels of ASVS Campaigns provide flexibility, so security teams can decide the level of security they need based on whether or not the application provides access to sensitive data.
No. 3: Prioritize Across a Growing List of Vulnerabilities and Risks—Don’t Panic
Security teams face a rapidly growing attack surface. The key to managing it is maintaining a balance between addressing tech debt and responding to new threats.
The first priority is often taking an inventory of the assets and cleaning up “tech debt.” Regularly updating software has never been more important. To go a step further and try to prioritize, Justin recommends compliance scoring. “A higher critical vulnerability should be the priority. We don’t go into the nuance of how this particular vulnerability may have an exploit. An exploit is likely to develop soon, but we try to get in the habit of regular cycle updates.”
Another priority may come from rapid response to news events such as the recent Apache Log4j vulnerability. This can distract security and IT teams—leading to panic. As Justin stated, “Sometimes, news cycles drive patching for things that are not that risky. As a security professional, it’s your job to explain why it’s not necessarily that risky and keep people from overreacting to something that’s not impactful. The other side of that is some vulnerabilities that have not been exploited, yet it seems like someone is going to find an exploit soon. The goal is to prevent any third-party attackers from getting access to the data.”
Synack offers checks for specific CVEs via Synack Campaigns. After researchers revealed the Log4j vulnerability, Synack responded immediately and provided an in-product check for the vulnerability in the form of a CVE Campaign. Within hours, Synack Researchers executed the Campaign, checking for the CVE, collaborating on the most efficient methods for detecting log4j, and providing customers with a risk assessment. Synack presents the information in a digestible, actionable way in order to save teams time and answer important questions via a report generated by running the Campaign.
No. 4: Effectively Communicate Vulnerability Risks To Leadership Teams
The leadership in some organizations may be more tech-savvy than in others. That being said, one principle that holds true across all these interactions is that the best way to convey a message as a security leader is to become an expert on that specific vulnerability or security risk and its implications for your organization.
Synack provides a reporting feature for Campaigns that compiles all the information necessary for leadership, legal, ops, or IT teams. The reports contain information like the severity of vulnerabilities found, whether certain task list items are “pass” or “fail,” evidence, and steps to reproduce findings. These reports are invaluable tools to communicate technical information to a non-technical audience, as well as for showing proof of work.
We hope that this information is useful for your organization as you consider different options. The cyber talent gap is only increasing. Security teams need on-demand solutions, automation, and specialized skills to address the growing workload. Vulnerability management leaders need products that improve security but not at the expense of user experience. There is a growing need to prioritize as vulnerabilities increase every year and attackers become more efficient. Lastly, security leaders need to fully immerse themselves in the nuance of new vulnerabilities and understand their potential impact. When security leaders communicate with executives, they should know the organization’s asset inventory, the extent of the vulnerability’s impact, and actions taken (or not taken) to mitigate its impact. All of these problems are front and center today for vulnerability management leaders, which is why we have developed a new product targeted at these pain points.
If you are interested in learning more about Campaigns, check out our dedicated webpage, or request a demo.
The post 4 Effective Vulnerability Management Tips for Security Leaders appeared first on Synack.
Providing On-Demand Testing for CVE-2021-44228 (Log4j) with Synack Testing
Testing for CVE-2021044228 (Log4j) with Synack
Since Friday, December 10, 2021, researchers from the Synack Red Team (SRT) have been solving customer needs related to CVE-2021-44228—the CVE that details a critical log4j vulnerability with wide-reaching implications across industries.
Responding to the Critical Vulnerability with Synack Testing
By 8 A.M. PST, when its magnitude and implications became clear to Synack operations, a new CVE entry was created in the Synack Platform to address CVE-2021-44228. Log4j immediately became available for customers to launch, long before most of the world read about the vulnerability in headlines and social feeds.
Synack CVE Checks connect an organization to SRT researchers capable of accomplishing specific security tasks. In this case, organizations can select CVE-2021-44228 within the Synack Platform and have a researcher check for the vulnerability on-demand.
Testing with the Best Researchers on the Planet
Over 30 SRT members assembled to cultivate ideas and improve the entire community’s efficiency and effectiveness. Together, they are bringing a diverse spectrum of perspectives from different backgrounds, ranging from military and government to academia and tech. This collaboration of top researchers allows Synack to improve the quality of testing for all customers with better processes, tools, and payloads.
The SRT often shares best practices within the community to help each other level up and make the entire internet safer. Compared to traditional testers or automated scanning tools, the SRT brings these sorts of advantages: human collaboration, diversity and creativity.
The Landscape of CVE-2021-44228 Across Industries
Since Friday morning, Synack has checked over half a million IP addresses across our customer base, confirming the status of thousands of CVE-2021-44228 checks and providing detailed reports containing proof of work and methodologies. With a combination of human intelligence and automated tools, Synack is addressing the vulnerability at an unprecedented scale and pace.
Vulnerable instances span across countries and industries and exist both in the government and private sectors. The urgency of the vulnerability has not been overstated by news outlets and social media – Synack recommends that customers activate the CVE check as soon as possible.
Checking for CVE 2021-44228 On-Demand—The Advantages of Synack Campaigns
Since the weekend that followed the CVE’s publication, Synack customers have utilized the Synack Platform to activate hundreds of checks from researchers around the world.
Synack beats other models to the punch. Scanners do not yet have the vulnerability’s signature, traditional pentesting engagements take significant time to spin up, and other bug bounty models do not provide the immediacy or certainty of a vulnerability as this one requires. The model provides on-demand services relevant to CVEs today and prepares organizations for the next 0day like CVE-2021-44228. Reach out to a Synack representative today to explore existing CVE checks, as well as other offerings available in the Synack Catalog.
The CVE-2021-44228 testing provided by Synack provides immediate results and reporting. The researcher will provide a clear yes/no answer on an asset’s vulnerability status, as well as details about their methodology, screenshots, and general proof of work.
Activate the Synack CVE-2021-44228 Test Today
Reach out to your Synack representative to activate the CVE-2021-44228 test today. If you’re new to the Synack Platform, reach out to us here and learn how to get started with Synack’s on-demand security platform and pentesting.
Update: Synack was asked whether our systems are vulnerable to Log4j. Synack does not use Log4j and has determined that we are not vulnerable to exploitation. In response to increased attack traffic attempting to exploit the vulnerability, we have taken additional steps to block the malicious traffic accordingly.
The post Providing On-Demand Testing for CVE-2021-44228 (Log4j) with Synack Testing appeared first on Synack.
The Synack Platform Expands to Confront the Cyber Skills Gap
At Synack, we’re truly committed to making the world a safer place. We’re doing that by helping organizations defend themselves against an onslaught of cyberattacks. We’re harnessing the tremendous power of the Synack Red Team, our community of the most skilled and trusted ethical hackers in the world, and through the most-advanced security tools available today to deliver continuous penetration testing (and more) with actionable, prioritized results.
Now, the Synack Platform is expanding to help organizations globally overcome the worldwide cybersecurity talent gap. I am excited to announce the launch of Synack Campaigns to provide on-demand access to the SRT, who will be available 24/7 to execute specific and unique cybersecurity tasks whenever you need them — and deliver results within hours. This new approach to executing targeted security operations tasks will fundamentally change organizations’ approach to cybersecurity by providing on-demand access to this highly skilled community of security researchers.
During my time at Synack, I’ve seen firsthand how the Synack Operations and Customer Success teams creatively engage with the SRT to address a growing range of clients’ security operations tasks, in addition to our traditional vulnerability discovery and penetration testing services.
Now, we are making these targeted security activities directly available to every organization in the form of Synack Campaigns, available through the new Synack Catalog, also launching today on the Synack Client Platform.
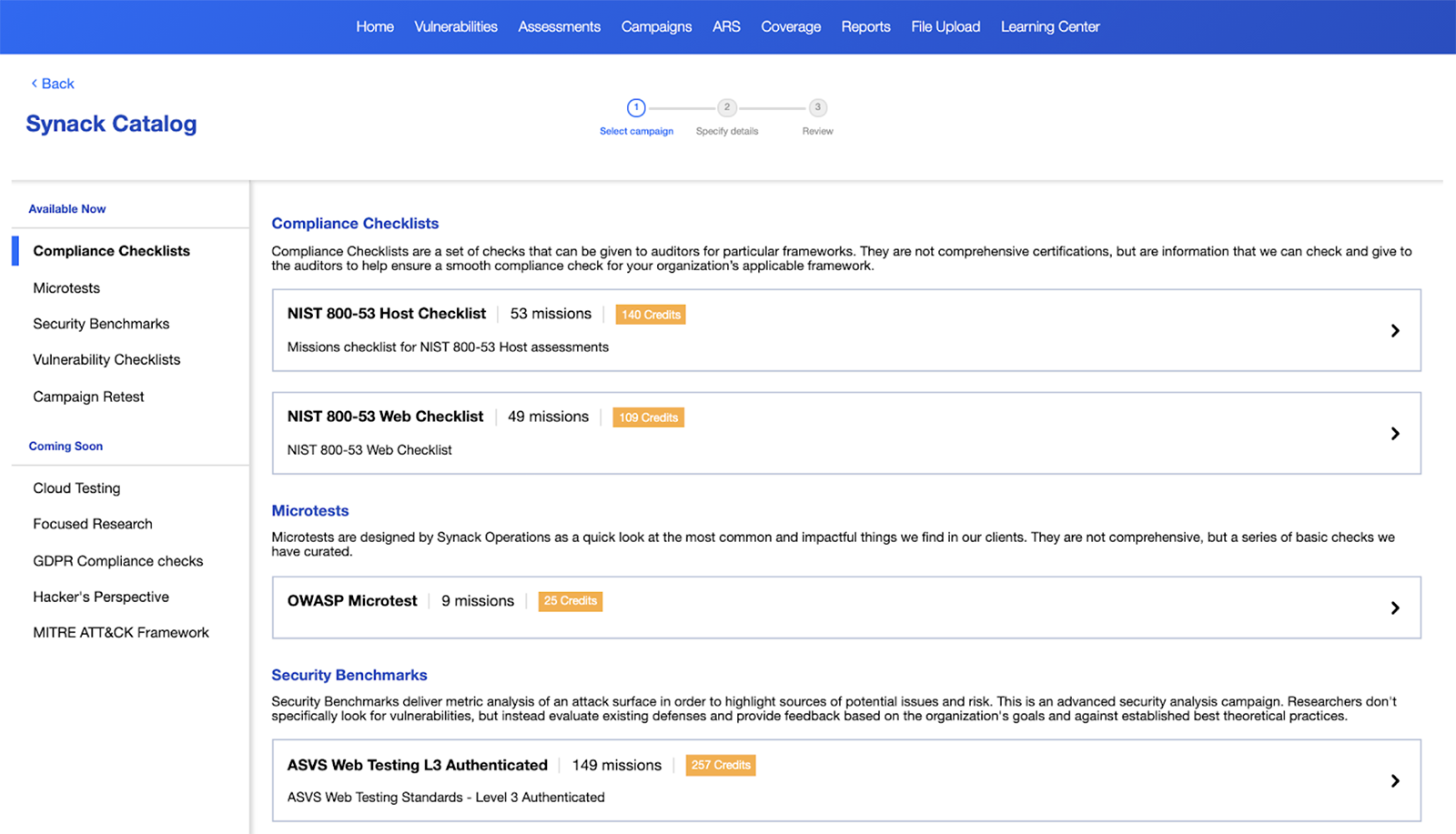
The new Synack Catalog, where customers can discover, configure, purchase and launch Synack Campaigns is available now on the Synack Client Portal. Please speak with your CSM to have this feature enabled for your organization.
I know from speaking to our clients across multiple industries that security teams are struggling to keep pace with the speed of product development. At the same time, they are trying to scale defenses to meet the complexity and magnitude of today’s threats. Our customers ascribe challenges with their growing backlog of security tasks such as CVE checks and cloud configuration reviews. On top of all of that, there’s the need to implement industry best-practice frameworks such as OWASP & Mitre Att&ck. Essentially, customer security teams are struggling with demanding workloads and have asked us for assistance in a number of areas:
- On-demand access to talented Synack Red Team members who are available 24/7 and capable of completing diverse security operations activities across a growing range of assets.
- A flexible security solution that can be configured to meet their specific needs in one centralized platform with their existing pentesting insights.
- A security solution that delivers results quickly (hours and days, not weeks or months) and is aligned with their agile development processes.
Synack Campaigns expands the core capabilities of the Synack Platform, including our trusted community of researchers, an extensive set of workflows, payment services, secure access controls and intelligent skills-based task-routing to provide customers with the ability to execute a growing catalog of cybersecurity operations.
With Synack Campaigns our researchers can augment internal security teams by performing targeted security checks such as:
- CVE and OWASP Top 10 vulnerability checks
- Cloud Configuration Checks
- Compliance Testing (NIST, PCI, GDPR, etc.)
- ASVS Checks
Synack Campaigns are built to complement our vulnerability management and pentesting services, and help customers achieve long-term security objectives, such as Application Security, M&A Due Diligence, and Vulnerability Management.
I’m excited for you to learn more about Synack Campaigns and to hear how you and your teams would like to leverage our on-demand community of researchers to address your organization’s growing operational security needs.
Peter Blanks is Synack’s Chief Product Officer.
The post The Synack Platform Expands to Confront the Cyber Skills Gap appeared first on Synack.