Utopia Developer Responds on 3rd Party Audit
Utopia is one of it’s kind decentralized communication application which takes anonymity and privacy very seriously even Utopia authors are anonymous. A step which has been greatly questioned by the community but every now and then it shows wisdom in their approach, as the news of Samurai Wallet developers being arrested is just one example where anonymity for the users is as important as it is for developers.
This raises a question about the safety of the developers who are working on Monero,Railgun and Aztec or even so many privacy wallets, If a developer is responsible for the actions of a user it leads to only two options. Either developers will stop working on such projects or adopt another approach where their anonymity is preserved.
Utopia developers may have understood this issue and thus opted for a route which doesn’t make them vulnerable which in return may make the platform vulnerable. I have discussed about team anonymity in this article and other aspects which may put off new users and what may be their counter argument.
Why No 3rd Party Audit
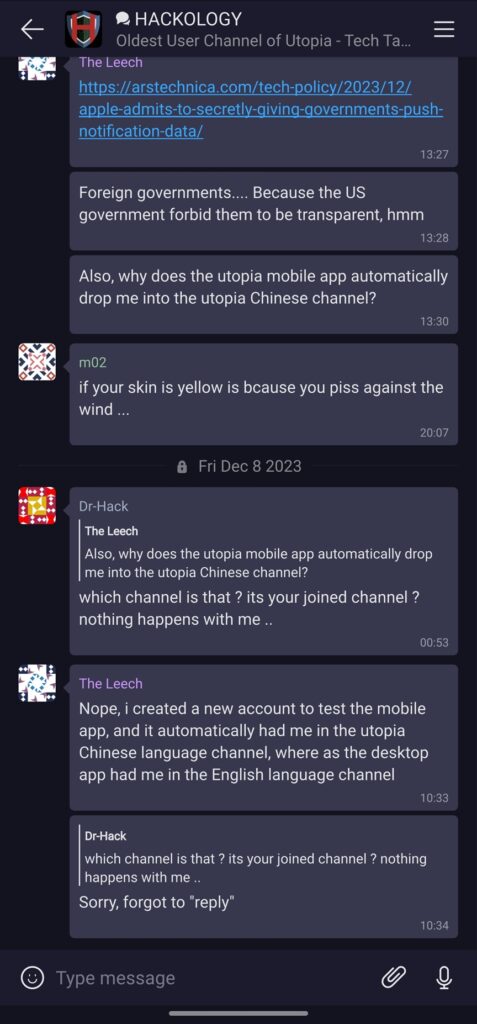
Recently I interacted with the team again and asked the evergreen question : Why no 3rd party audit.
It has been brought up in past aswell, as crp is a privacy coin and it’s listing on tier 1 CEXes is very difficult due to compliance and regulatory reasons , a 3rd party audit will bring trust as anonymity + privacy usually attract hardcore users + activists while the ordinary users do not care about such things. and a platform trusted and preferably endorsed by the right audience will bring in the casual users aswell.
I always probe this question to the developers of Utopia as in my personal opinion it is very important to get this aspect taken care off , as an independent 3rd party audit will greatly help the cause and make it easy for new and old users to trust the platform which gives us total anonymity and privacy.
Utopia Team Responds
I seeked permission from the Utopia team to publicly share it for everyone’s read and will breakdown their response and insert my personal arguments where deemed necessary.
The development of Utopia has been carried out in full secrecy for more than 12 years. Since its creation, the team has deliberately chosen not to disclose the identities of its founders or core developers. This decision was not accidental, but a well-calculated measure aimed at protecting both the project and its global community of users. By preserving anonymity, we have eliminated one of the most critical points of failure: the risk of putting pressure on specific individuals to compromise the principles of Utopia. The true guarantee of stability lies in the system itself, not in people who could be forced or influenced.
I strongly agree to this statement as highlighted earlier Team anonymity is of paramount important as we have seen over the years and the risk may just increase in future.
At the heart of our philosophy lie two equally important priorities: protection of intellectual property and preservation of ecosystem
stability.Utopia’s ecosystem is a unique organism of a 12-year strategic investment of time, knowledge, and resources. During this period, our team has developed technologies and architectural solutions that have no direct analogy in the crypto industry. To disclose our source code would be to hand over these technological breakthroughs to competitors, reducing more than a decade of innovation to a freely available template. This would undermine not only the uniqueness of Utopia but also the enormous intellectual effort invested in creating it.
I am sure there must be a 3rd party audit company / team which will respect the code and not copy / share / disclose a code after completing the code audit of Utopia Ecosystem. Moreover there are various ways of getting the audit done, which may not include a complete handover of the source code. If possible even an inhouse audit can be done too where the auditors may not be allowed to take the code off-site.
Equally critical is the security of our users. Open-source distribution of the Utopia code would create additional attack vectors against the ecosystem. Malicious actors could create counterfeit clients, fake applications, or entire hostile forks of the protocol designed to conduct surveillance, steal user data, or destabilize the network. Worse, sophisticated tools for spam, flooding, or exploitation of vulnerabilities would spread rapidly, forcing us to spend resources fighting endless attacks instead of strengthening and evolving the project. It is our duty to prevent such risks. A secure environment is possible only when control over the integrity of the technology remains with its creators, who know every line of its architecture. There is also a risk of false positives: if forks of the code or modifications of the network engine are used to create botnets, the entire ecosystem may be perceived as unsafe. In such a case, the broader adoption of Utopia could be significantly hindered.
Unlike many open-source crypto solutions, which often fragment into dozens of forks and parallel incompatible implementations, Utopia has chosen another path – stability, unity, and protection against fragmentation. For us, decentralization is about eliminating control by states and corporations, not about giving away the keys of the ecosystem to anyone who wishes to exploit it. We firmly believe that keeping Utopia’s code proprietary is the only way to guarantee the continuity, resilience, and trustworthiness of the network for years to come.
The fragmentation of current privacy and anonymity tools is rightly highlighted as all privacy coins including Crypton can not be listed on any CEX and their wallets are quickly tracked and inbound transactions are blocked by Tier 1/2 exchanges just to save themselves from any legal implications thus impacting the anonymity.
Utopia was not conceived as a short-term experiment. It was envisioned and continues to evolve &mdash as a long-term foundation for free, secure, and anonymous communication and financial interaction. After 12 years of relentless work, we cannot and will not put that foundation at risk. The combination of a closed-source codebase, anonymous development model, and the ecosystem’s decentralized peer-to-peer architecture ensures not only protection of our intellectual property but also the safety and confidence of all who place their trust in Utopia.
Conclusion
While Utopia developers / team has never talked about crypton price since day one and they have never shilled like so many projects we see in the crypto world but it is natural that internet find a projects worth by the worth of it’s token and those who are indifferent about price of a coin need some assurances so that they can trust a project which is responsible for the anonymity and their privacy. Since the stakes are high, I have always requested the developers of Utopia to find a mechanism which may work in the favour of both sides i.e. Developers/Project and the users. I understand the concerns highlighted by the team but it is imperative that this concern is somehow addressed which will only do good for the Utopia ecosystem in the long term. Let see how things develop in the future and hoping to see more development and use case for Utopia ecosystem which is a true decentralized and private platform which is certainly not fragmented. If you have not experienced the ecosystem, check it out by visiting Utopia Official Website and do share your feedback through their support website.
The post Utopia Developer Responds on 3rd Party Audit first appeared on Internet Security Blog - Hackology.