Nokia’s AI Gamble Targets 60% Profit Surge
Finnish firm seeks annual operating profits of €2.7 to €3.2 billion by 2028.
The post Nokia’s AI Gamble Targets 60% Profit Surge appeared first on TechRepublic.
Finnish firm seeks annual operating profits of €2.7 to €3.2 billion by 2028.
The post Nokia’s AI Gamble Targets 60% Profit Surge appeared first on TechRepublic.
Finnish firm seeks annual operating profits of €2.7 to €3.2 billion by 2028.
The post Nokia’s AI Gamble Targets 60% Profit Surge appeared first on TechRepublic.
The Federal Communications Commission is set this week to vote on reversing cybersecurity rules for telecommunications providers that were put forward following the sweeping “Salt Typhoon” hacks.
The FCC’s meeting on Thursday includes plans to consider an order to rescind a ruling and proposed rules published in the waning days of the Biden administration. The January ruling requires telecom operators to secure their networks under Section 105 of the Communications Assistance for Law Enforcement Act.
But current FCC Chairman Brendan Carr argues that ruling “exceeded the agency’s authority and did not present an effective or agile response to the relevant cybersecurity threats.”
The proposed order would rescind the January ruling and withdraw proposed cybersecurity rules for telecom operators.
Instead, the FCC “should instead continue to pursue an agile and collaborative approach to cybersecurity through federal-private partnerships that protect and secure communications networks and more targeted, legally sound rulemaking and enforcement,” according to a factsheet on the order of reconsideration.
The Salt Typhoon campaign was revealed in 2024. It involved penetrating hacks into U.S. telecom networks and others across the globe. The hackers were reportedly able to target the communications of political figures and government officials, including then-candidate Donald Trump and running mate JD Vance.
U.S. officials have said Chinese-government sponsored hackers are behind the campaign. Senate Intelligence Committee Ranking Member Mark Warner (D-Va.) has described it as “the worst telecommunications hack in our nation’s history.”
The Cybersecurity and Infrastructure Security Agency has since said the Salt Typhoon campaign overlapped with global threat activities targeting multiple sectors, including telecommunications, government, transportation, lodging, and military infrastructure networks.
“While these actors focus on large backbone routers of major telecommunications providers, as well as provider edge (PE) and customer edge (CE) routers, they also leverage compromised devices and trusted connections to pivot into other networks,” CISA wrote in a September advisory. “These actors often modify routers to maintain persistent, long-term access to networks.”
In rolling out the January rules, Biden administration officials argued they represented a “critical step to require U.S. telecoms to improve cybersecurity to meet today’s nation state threats, including those from China’s well-resourced and sophisticated offensive cyber program.”
However, the FCC’s current leadership says the rules misinterpreted the law and “unnecessarily raised and purported to resolve issues that were not appropriate for consideration in the absence of public input.” The FCC’s factsheet also references the commission’s “recent engagement with providers and their agreement to take extensive steps to protect national security interests.”
In an October letter to the FCC, lawyers representing several telecom associations argued that the January ruling “would significantly undermine” public-private partnerships. They argued that telecom providers had voluntarily collaborated with federal agencies to investigate Salt Typhoon and adopted stronger cybersecurity measures.
Warner and Sen. Ron Wyden (D-Ore.) are also pressing the Department of Homeland Security to release an unclassified 2022 report on security vulnerabilities in the U.S. telecom sector. They argue that by not releasing the report, DHS is undermining public debate over how to best secure telecom networks in the wake of Salt Typhoon.
“The Salt Typhoon compromise represents one of the most serious espionage campaigns against the communications of U.S. government leaders in history, and highlighted important gaps in our nation’s communications security – in some cases, with providers ignoring basic security precautions such as credential re-use across network appliances and failure to adopt multi-factor authentication for highly privileged network administrator accounts,” Warner and Wyden wrote in a recent letter to DHS and the Office of the Director of National Intelligence.
Meanwhile, the House on Monday passed the “Strengthening Cyber Resilience Against State-Sponsored Threats Act.” The bill would establish a joint interagency task force to address China-linked cyber threats, including Salt Typhoon. The task force would be led by CISA, with involvement from the Justice Department, the FBI and several sector-risk management agencies.
The post FCC to vote on reversing cyber rules adopted after Salt Typhoon hack first appeared on Federal News Network.

© AP Photo/Andrew Harnik

Auger, a startup building logistics and supply chain software, announced Yuqing Sun as its chief data and AI enablement officer. Sun joins the Bellevue, Wash.-based company from Johnson & Johnson where she has worked for nearly 20 years in a variety of supply chain, analytics and data science roles.
“Yuqing brings the rare combo of deep technical chops, operational scar tissue, and the calm that only comes from having seen every kind of supply-chain fire drill,” said Dave Clark, Auger’s founder and CEO and a former Amazon executive.
Clark noted on LinkedIn that while at Johnson & Johnson, Sun worked to modernize “one of the most complex supply chains on the planet through data and AI innovations. She built and scaled more than 30 AI-driven products across optimization, simulation, IoT, machine learning, computer vision — you name it.”
Last month Auger appointed Justine Hastings as chief AI economist. The company, ranked No. 48 on the GeekWire 200 list of top Pacific Northwest startups, raised a $100 million Series A round last December.

— Amy Harris is the new public policy and government relations director for the Washington Technology Industry Association (WTIA).
For the past nine years, Harris has been a principal for Red Strategies, which bills itself as providing “fundraising consulting and event planning for right of center candidates and organizations.” She has also worked as an executive assistant for two members of Congress.
Randa Minkarah, CEO of the WTIA consortium, praised Harris’ “deep experience in bipartisan coalition-building, strategic advocacy, and navigating complex political landscapes,” noting the skills will be instrumental in working in Washington state and the nation’s capitol.
— Marc Brown, a former corporate vice president at Microsoft who helped lead the acquisition of companies including LinkedIn, GitHub and Minecraft, has joined the board of directors for Syncro, a software platform for IT professionals.
Seattle-based Brown was with Microsoft for more than two decades, managing more than 185 acquisitions and 80 equity investments.

— Pyramid Communications, a longtime Seattle-area public relations firm, named Emily Ryan as its first CEO. Ryan was with Pyramid for nearly 14 years before taking a year-long role as chief communications officer for Our Children’s Trust in 2024.
“During a tumultuous period in the world, Pyramid is doubling down on our commitment to support changemakers leading bold action for a better world,” the company posted on LinkedIn. “Emily’s trusted, creative leadership will sustain our team and our clients as we continue to work alongside all of you…”
— Carbon Direct, a carbon management firm based in New York and Seattle, announced two leadership hires as a result of its recent acquisition of climate tech startup Pachama.

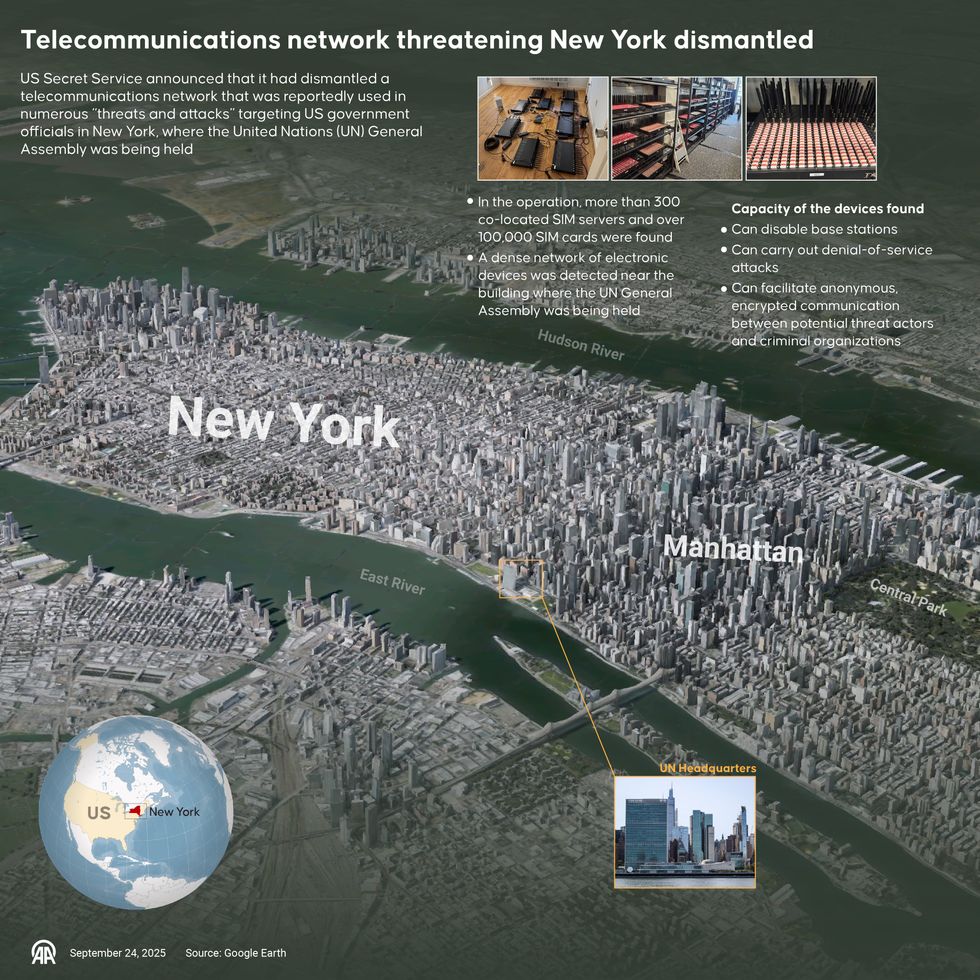
DEEP DIVE — When Secret Service agents swept into an inconspicuous building near the United Nations General Assembly late last month, they weren’t tracking guns or explosives. Instead, they dismantled a clandestine telecommunications hub that investigators say was capable of crippling cellular networks and concealing hostile communications.
According to federal officials, the operation seized more than 300 devices tied to roughly 100,000 SIM cards — an arsenal of network-manipulating tools that could disrupt the cellular backbone of New York City at a moment of geopolitical tension. The discovery, officials stressed, was not just a one-off bust but a warning sign of a much broader national security vulnerability.
The devices were designed to create what experts call a “SIM farm,” an industrial-scale operation where hundreds or thousands of SIM cards can be manipulated simultaneously. These setups are typically associated with financial fraud or bulk messaging scams. Still, the Secret Service warned that they can also be used to flood telecom networks, disable cell towers, and obscure the origin of communications.
In the shadow of the UN, where global leaders convene and security tensions are high, the proximity of such a system raised immediate questions about intent, attribution, and preparedness.
“(SIM farms) could jam cell and text services, block emergency calls, target first responders with fake messages, spread disinformation, or steal login codes,” Jake Braun, Executive Director of the Cyber Policy Initiative at the University of Chicago and former White House Acting Principal Deputy National Cyber Director, tells The Cipher Brief. “In short, they could cripple communications just when they’re needed most.”
Sign up for the Cyber Initiatives Group Sunday newsletter, delivering expert-level insights on the cyber and tech stories of the day – directly to your inbox. Sign up for the CIG newsletter today.
How SIM Farms Work
At their core, SIM farms exploit the fundamental architecture of mobile networks. Each SIM card represents a unique identity on the global communications grid. By cycling through SIMs at high speed, operators can generate massive volumes of calls, texts, or data requests that overwhelm cellular infrastructure. Such floods can mimic the effects of a distributed denial-of-service (DDoS) attack, except the assault comes through legitimate carrier channels rather than obvious malicious traffic.
“SIM farms are essentially racks of modems that cycle through thousands of SIM cards,” Dave Chronister, CEO of Parameter Security, tells The Cipher Brief. “Operators constantly swap SIM cards and device identifiers so traffic appears spread out rather than coming from a single source.”
That makes them extremely difficult to detect.
“They can mimic legitimate business texts and calls, hide behind residential internet connections, or scatter equipment across ordinary locations so there’s no single, obvious signal to flag,” Chronister continued. “Because SIM farms make it hard to tie a number back to a real person, they’re useful to drug cartels, human-trafficking rings and other organized crime, and the same concealment features could also be attractive to terrorists.”
That ability to blend in, experts highlight, is what makes SIM farms more than just a criminal nuisance.
While SIM farms may initially be used for financial fraud, their architecture can be easily repurposed for coordinated cyber-physical attacks. That dual-use nature makes them especially appealing to both transnational criminal groups and state-backed intelligence services.
Who Might Be Behind It?
The Secret Service, however, has not publicly attributed the network near the UN to any specific individual or entity. Investigators are weighing several possibilities: a transnational fraud ring exploiting the chaos of UN week to run large-scale scams, or a more concerning scenario where a state-backed group positioned the SIM farm as a contingency tool for disrupting communications in New York.
Officials noted that the operation’s sophistication suggested it was not a low-level criminal endeavor. The hardware was capable of sustained operations against multiple carriers, and its sheer scale — 100,000 SIM cards — far exceeded the typical scale of fraud schemes. That raised the specter of hostile governments probing U.S. vulnerabilities ahead of potential hybrid conflict scenarios.
Analysts note that Russia, China, and Iran have all been implicated in blending criminal infrastructure with state-directed cyber operations. Yet, these setups serve both criminals and nation-states, and attribution requires more details than are publicly available.
“Criminal groups use SIM farms to make money with scams and spam,” said Braun. “State actors can use them on a bigger scale to spy, spread disinformation, or disrupt communications — and sometimes they piggyback on criminal networks.”
One source in the U.S. intelligence community, who spoke on background, described that overlap as “hybrid infrastructure by design.”
“It can sit dormant as a criminal enterprise for years until a foreign government needs it. That’s what makes it so insidious,” the source tells The Cipher Brief.
From Chronister’s purview, the “likely explanation is that it’s a sophisticated criminal enterprise.”
“SIM-farm infrastructure is commonly run for profit and can be rented or resold. However, the criminal ecosystem is fluid: nation-states, terrorist groups, or hybrid actors can and do co-opt criminal capabilities when it suits them, and some state-linked groups cultivate close ties with criminal networks,” he said.
The Broader National Security Blind Spot
The incident during the United Nations General Assembly also underscores a growing blind spot in U.S. protective intelligence: telecommunications networks as contested terrain. For decades, federal resources have focused heavily on cybersecurity, counterterrorism, and physical threats. At the same time, the connective tissue of modern communications has often been treated as a commercial domain, monitored by carriers rather than security agencies.
The Midtown bust suggests that assumption no longer holds. The Secret Service itself framed the incident as a wake-up call.
“The potential for disruption to our country’s telecommunications posed by this network of devices cannot be overstated,” stated U.S. Secret Service Director Sean Curran. “The U.S. Secret Service’s protective mission is all about prevention, and this investigation makes it clear to potential bad actors that imminent threats to our protectees will be immediately investigated, tracked down and dismantled.”
However, experts warn that U.S. defenses remain fragmented. Carriers focus on fraud prevention, intelligence agencies monitor foreign adversaries, and law enforcement investigates domestic crime. The seams between those missions are precisely where SIM farms thrive.
The Cipher Brief brings expert-level context to national and global security stories. It’s never been more important to understand what’s happening in the world. Upgrade your access to exclusive content by becoming a subscriber.
Hybrid Warfare and the Next Front Line
The rise of SIM farms reflects the evolution of hybrid warfare, where the boundary between criminal activity and state action blurs, and adversaries exploit commercial infrastructure as a means of attack. Just as ransomware gangs can moonlight as proxies for hostile intelligence services, telecom fraud networks may double as latent disruption tools for foreign adversaries.
Additionally, the threat mirrors patterns observed abroad. In Ukraine, officials have reported Russian operations targeting cellular networks to disrupt battlefield communications and sow panic among civilians. In parts of Africa and Southeast Asia, SIM farms have been linked to both organized crime syndicates and intelligence-linked influence campaigns.
That same playbook, experts caution, could be devastating if applied in the heart of a global city.
“If activated during a crisis, such networks could flood phone lines, including 911 and embassy hotlines, to sow confusion and delay coordination. They can also blast fake alerts or disinformation to trigger panic or misdirect first responders, making it much harder for authorities to manage an already volatile situation,” Chronister said. “Because these setups are relatively cheap and scalable, they are an inexpensive but effective way to complicate emergency response, government decision-making, and even protective details.”
Looking Ahead
The dismantling of the clandestine telecom network in New York may have prevented an imminent crisis, but experts caution that it is unlikely to be the last of its kind. SIM farms are inexpensive to set up, scalable across borders, and often hidden in plain sight. They represent a convergence of cyber, criminal, and national security threats that the U.S. is only beginning to treat as a unified challenge.
When it comes to what needs to be done next, Braun emphasized the importance of “improving information sharing between carriers and government, investing in better tools to spot hidden farms, and moving away from SMS for sensitive logins.”
“Treat SIM farms as a national security threat, not just telecom fraud. Limit access to SIM farm hardware and punish abuse. Help smaller carriers strengthen defenses,” he continued. “And streamline legal steps so takedowns happen faster.”
Chronister acknowledged that while “carriers are much better than they were five or ten years ago, as they’ve invested in spam filtering and fraud analytics, attackers can still get through when they rotate SIMs quickly, use eSIM provisioning, or spread activity across jurisdictions.”
“Law enforcement and intelligence have powerful tools, but legal, technical, and cross-border constraints mean detection often outpaces confident attribution and rapid takedown. Make it harder to buy and cycle through SIMs in bulk and strengthen identity verification for phone numbers,” he added. “Require faster, real-time information-sharing between carriers and government during traffic spikes, improve authentication for public alerts, and run regular stress-tests and red-team exercises against telecom infrastructure. Finally, build joint takedown and mutual-assistance arrangements with allies so attackers can’t simply reconstitute operations in another country.”
Are you Subscribed to The Cipher Brief’s Digital Channel on YouTube? There is no better place to get clear perspectives from deeply experienced national security experts.
Read more expert-driven national security insights, perspective and analysis in The Cipher Brief because National Security is Everyone’s Business.

Hello, folks, and welcome back to your favorite Friday roundup of all the space news fit to print. This week we’ve got experimental rocket engines, a gigantic map, and galaxies galore. The James Webb Space Telescope found hydrogen in a galaxy more than eight billion light years away, and the coldest ice ever, but it’s currently down due to a software glitch.
Closer to home, Rocket Lab launched their Electron rocket from US soil for the first time. NASA came together for a day of remembrance that somehow managed to be both somber and ineffably sweet.
If you wish to make an apple pie from scratch, you must first invent the universe. And somewhere along the way, you’ll need one of the ancient molecular clouds of dust and ice from which stars and habitable planets like Earth are born. This week, Webb scientists announced that the telescope has spotted just such a place. It’s a stellar nursery called the Chamaeleon I cloud, loaded with these primordial crystals. That’s the tableau you’re seeing in the image above — you can tell it’s from Webb by those iconic six-pointed stars. The ice contains traces of sulfur and ammonia, along with simple organic molecules like methanol. And at just ten degrees above absolute zero, it’s the coldest ice ever found.
“We simply couldn’t have observed these ices without Webb,” said Klaus Pontoppidan, a Webb project scientist involved in the research. “The ices show up as dips against a continuum of background starlight. In regions that are this cold and dense, much of the light from the background star is blocked, and Webb’s exquisite sensitivity was necessary to detect the starlight and therefore identify the ices in the molecular cloud.”
Late Wednesday evening, aerospace startup Rocket Lab successfully launched its Electron rocket from NASA’s Wallops Flight Facility in Virginia. This was the 33rd launch of the Electron, but its first launch from American soil.
Electron is a 59-foot, two-stage, light-duty kerosene rocket. It’s powered by nine Rutherford engines, which my colleague Ryan Whitwam notes are semi-famous in aerospace for being largely 3D printed.
The Electron isn’t reusable — but in 2021, Rocket Lab announced the Neutron. Designed for reusability, the Neutron will have about a third of the lift capacity of a Falcon 9.
Speaking of 3D-printed rocket engines: NASA announced this week that it has successfully validated a next-gen rocket engine it hopes will revolutionize rocket design. The new engine generates thrust “using a supersonic combustion phenomenon known as a detonation.” And this is no experimental error — their full-scale alpha build produced more than 4,000 pounds of thrust at full throttle.
These engines get their name (rotating detonation rocket engine, or RDRE) from the unique way they produce thrust. Detonation waves echo around a circular chamber, wringing out every bit of energy from the rocket fuel. It’s great for efficiency, but it puts the whole system under extreme pressure. Undaunted, NASA turned to an advanced additive manufacturing process, even developing its own bespoke metal alloy for the task.
According to the agency, the RDRE incorporates the agency’s GRCop-42 copper alloy into a powder bed fusion (PBF) additive manufacturing process. PBF uses a laser or particle beam to seamlessly fuse ultra-fine particles. It’s a lot like the sintering process used to make the space shuttle rocket engines — and even they had to be actively cooled by the rockets’ own cryofuel, in order to withstand the unearthly temperatures and pressures of takeoff. If the design holds up, NASA intends to use RDRE in its efforts to establish a long-term presence off-planet.
Astronomers have created a gargantuan map of the Milky Way, using a telescope built to detect dark energy. Featuring more than three billion stars, it focuses on the galaxy’s orbital plane — a region notoriously difficult to study.
Earth’s atmosphere scatters starlight so that points of light turn into point clouds. So, the astronomers just dove right in. To isolate different stars and celestial objects, the group used some extra-snazzy math to get rid of noise. This allowed them to “paint in” the proper background, letting them tell one star from another.

Astronomers have released a gargantuan survey of the galactic plane of the Milky Way. The new dataset contains a staggering 3.32 billion celestial objects — arguably the largest such catalog so far. The data for this unprecedented survey were taken with the US Department of Energy-fabricated Dark Energy Camera at the NSF’s Cerro Tololo Inter-American Observatory in Chile, a Program of NOIRLab. Credit: Saydjari et al., via NoirLab
“One of the main reasons for the success of DECaPS2 is that we simply pointed at a region with an extraordinarily high density of stars and were careful about identifying sources that appear nearly on top of each other,” said Andrew Saydjari, lead author on the (open-access!) paper accompanying the gigantic map. “Doing so allowed us to produce the largest such catalog ever from a single camera, in terms of the number of objects observed.”
The history of astronomy has been all about recognizing that our place in the universe isn’t all that special. We’ve gone from the center of all existence to just another planet orbiting an average star in one of billions and billions of galaxies. However, a new simulation hints that there might be something special about the Milky Way after all.

Yepun, one of the four Unit Telescopes of the Very Large Telescope (VLT) at the European Southern Observatory, studies the center of the Milky Way. Yepun’s laser beam creates an artificial “guide star” to calibrate the telescope’s adaptive optics. Image: ESO/Yuri Beletsky
The model suggests that the Milky Way is far larger than it should be, based on the scale of the “cosmological wall”: an incomprehensibly huge semi-planar structure occupied by the Milky Way and other galaxies in the Local Group.
An international team of astronomers announces the discovery of cold atomic hydrogen, more than eight billion light-years from Earth. Cooler than ionized plasma but warmer than molecular hydrogen gas, atomic hydrogen is the raw fuel of coalescing stars. The researchers used gravitational lensing to spot the telltale — but deeply redshifted — 21cm line.
Named for the daughter of Apollo, Chariklo is a centaur: a Kuiper belt object that orbits out past Saturn. It’s the first of its kind ever found with a confirmed ring system. The thing really is tiny; it’s about 160 miles in diameter and has less than two percent the mass of Earth. But a new report from Webb shows even that much mass is enough to sustain two slender rings, for a time.
In a remarkable stroke of scientific luck, the telescope was pointed just right to catch Chariklo as it passed in front of a star. When it did, the star’s light fluttered in a way that betrayed the presence of the rings.
Chariklo has two thin rings — the first rings ever detected (in 2013) around a small Solar System object. When Webb observed the occultation, scientists measured dips in the brightness of the star. These dips corresponded exactly as predicted to the shadows of Chariklo’s rings. pic.twitter.com/sqH08v1lOB
— NASA Webb Telescope (@NASAWebb) January 25, 2023
Nothing less than delighted, the astronomers report that Chariklo’s rings are two and four miles wide, respectively. But the asteroid actually has something in common with the Chamaeleon I cloud. Chariklo’s surface is covered in exotic phases of water ice that only Webb can see.
Principal investigator Dean Hines added, “Because high-energy particles transform ice from crystalline into amorphous states, detection of crystalline ice indicates that the Chariklo system experiences continuous micro-collisions that either expose pristine material or trigger crystallization processes.” It’ll be up to the JWST to find out more.
Unfortunately, observations of Chariklo and other celestial bodies will have to wait a while. The JWST had a software glitch this week. Per NASA, the telescope’s Near Infrared Imager and Slitless Spectrograph (NIRISS) “experienced a communications delay within the instrument, causing its flight software to time out.” Unfortunately, this led to a software gridlock.
The telescope is unavailable for science observations because NASA and the Canadian Space Agency are doing root-cause analysis to figure out and fix the problem. But NASA emphasizes that the telescope is fine. There’s no damage and no indication of any danger. If it’s a software problem, it may well be a software fix.
Now that it’s been on Mars for a while, the Perseverance rover has filed an authoritative report on Martian weather. The number one takeaway: It’s cold on the Red Planet! The average surface temperature is -67C.
It’s also windy on Mars. Since Mars has an atmosphere, it has surface weather. It also has an axial tilt, so it has seasons, just like Earth. Dust storms can envelop Mars’ entire northern hemisphere.

Plumes of darker, subsurface dust waft to the surface when the sun warms Martian sands beneath transparent sheets of ice. Mars’ shifting winds then blow these plumes of dust into V-shaped patterns. Astronomers are using the plumes to learn more about Mars’ weather and surface climate. Image: NASA
Perseverance is covered in a suite of sensors that constantly monitor wind speed and direction, atmospheric pressure, temperature, humidity, and dust. Together, they make the rover’s Mars Environmental Dynamics Analyzer (MEDA).
“The dust devils are more abundant at Jezero than elsewhere on Mars and can be very large, forming whirlwinds more than 100 meters in diameter. With MEDA we have been able to characterize not only their general aspects (size and abundance) but also to unravel how these whirlwinds function,” says Ricardo Hueso, of the MEDA team.
Perseverance has captured numerous dust devils as they sweep through Jezero Crater. However, to get that data, MEDA’s exposed sensors also face damage from the harsh radiation environment, extreme temperature swings, and the ever-present Martian dust. A dust devil in January of last year kicked up enough debris that it damaged one of MEDA’s wind instruments. Still, the rover perseveres.
Every year, NASA holds a memorial for staff, astronauts, and alumni who have died. 2023’s Day of Remembrance holds a somber significance, as Feb. 1 is the 20th anniversary of the Columbia disaster. Unfortunately, this year’s fallen also included Apollo 7 pilot Walt Cunningham, who passed earlier this month. Cunningham was the last surviving member of the Apollo 7 crew.

Photo Credit: NASA/Aubrey Gemignani via NASA HQ Flickr
As in years past, NASA staff gathered this week at space centers and labs around the country, to honor the sacrifices of those who have given their lives in pursuit of exploration and discovery. But they did it in a way only NASA could do. They held nationwide town-hall safety meetings, to reflect on and improve NASA’s aerospace safety culture.

Ask not for whom the safety alarm tolls; it tolls for thee. NASA safety-culture town hall meeting at its Washington headquarters after the Arlington memorial service. Image: NASA/Keegan Barber via NASA HQ Flickr
What a fitting way to honor lives lost, while still reaching for the stars. Town-hall safety culture meetings. We love you guys. Never change.
Steady as she goes: After a year’s delay and a missed launch window, NASA’s Psyche mission team is getting the spacecraft in shape to launch this year. In a blog post, the agency said, “After a one-year delay to complete critical testing, the Psyche project is targeting an October 2023 launch on a SpaceX Falcon Heavy rocket.”
When it launches, Psyche will carry a technology demo for NASA’s shiny new Deep Space Optical Communications (DSOC) network. DSOC systems will use lasers for high-bandwidth communications between Earth and the Moon, Mars, and beyond. Beyond a deluge of scientific data, NASA expects that the network will be able to handle high-def images and video.
Comet C/2022 E3 (ZTF) is a long-period comet that last visited Earth in the time of the Neanderthals. Now it’s back for another close approach. And although we didn’t know this when we found it last year, it turns out the comet’s tail glows pale green, like a luna moth under a streetlight.

The robin’s-egg glow of Comet C/2022 E3 (ZTF)’s tail shines against its twin tails. Image: Dan Bartlett/NASA
At first, astronomers thought it might require binoculars to catch a glimpse of the thing. However, as ExtremeTech’s Adrianna Nine writes, the comet is now visible to the naked eye in places across much of the Northern Hemisphere.
Our verdant visitor will continue its brightening trend while it sails toward Earth. It will make its closest approach to us on February 2: perhaps too soon for a Valentine’s Day spectacular, but right on time for Imbolc, Candlemas, and Groundhog Day.
Cyber security researchers recently found that hospitals are leaving millions of private medical images electronically accessible by way of insecure storage practices. Over 45 million medical images from scans such as X-rays, MRIs, and CT scans are stored on unsecured servers and storage devices.
On top of patient privacy concerns, cybercriminals could steal the data on these systems to blackmail individuals. Hackers could also leverage these under-secured servers to execute ransomware attacks on healthcare facilities.
In the past few months, we’ve seen an alarming increase in the number of healthcare groups hit with ransomware attacks. A key US healthcare system recently enacted EHR downtime procedures after falling victim to a ransomware related ruse. A string of strikes has shut down a variety of health focused organizations across the past few months, impacting over 60 providers and more than 500 facilities.
These millions of medical files may be needed for clinical decision-making purposes. Without on-demand access, people may receive sub-standard healthcare and may suffer through serious consequences.
Medical groups may be using outdated technologies that leave patients and their data vulnerable. Healthcare security budgets are often stretched thin and organizations may resist purchasing new equipment or even investing in better security.
In one recent example, 45 million unique cases of Digital Imaging and Communications in Medicine (DICOM) exposed. Further, researchers found malicious scripts on several servers, indicating that malicious actors had already accessed the unsecured devices.
It goes without saying, cyber security in the healthcare sector needs to be a top priority, especially as these organizations are at the frontline of this global pandemic.
The US Cybersecurity and Infrastructure Security Agency recommends following best practices, from proper segmentation to explicit access rules. For additional insights into securing the healthcare sector, check out Cyber Talk’s healthcare-focused whitepapers and solutions briefs.
The post Millions of medical images on the move across the web appeared first on CyberTalk.
Newly released documents show U.S. immigration authorities have used a secretive cell phone snooping technology hundreds of times across the U.S. in the past three years.
The documents, obtained through a public records lawsuit by the American Civil Liberties Union and seen by TechCrunch, show that U.S. Immigration and Customs Enforcement (ICE) deployed cell site simulators — known as stingrays — at least 466 times between 2017 and 2019, which led to dozens of arrests and apprehensions. Previously obtained figures showed ICE used stingrays more than 1,885 times over a four-year period between 2013 and 2017.
The documents say that stingrays were not deployed for civil immigration investigations, like removals or deportations.
Although the numbers offer a rare insight into how often ICE uses this secretive and controversial technology, the documents don’t say how many Americans also had their phones inadvertently ensnared by these surveillance devices.
“We are all harmed by government practices that violate the Constitution and undermine civil liberties,” said Alexia Ramirez, a fellow with the ACLU’s Speech, Privacy, and Technology Project. “ICE’s use of cell site simulators affects all people, regardless of their immigration status.”
“When cell site simulators search for an individual, they necessarily also sweep in sensitive, private information about innocent bystanders,” said Ramirez. “This is part of the reason courts have said there are serious Fourth Amendment concerns with this technology.”

A letter from Harris Corp., which builds cell site simulators — known as “stingrays,” describing the non-disclosure terms for its Crossbow cell site simulator. (Source: ACLU)
Stingrays impersonate cell towers and capture the calls, messages, location and in some cases data of every cell phone in their range. Developed by Harris Corp., stingrays are sold exclusively to law enforcement. But their purchase and use are covered under strict non-disclosure agreements that prevent police from discussing how the technology works. These agreements are notoriously prohibitive; prosecutors have dropped court cases rather than disclose details about the stingrays.
The newly released documents are heavily redacted and offer little more about what we know of how stingrays work. One document did, however, reveal for the first time the existence of Harris’ most recent stingray, Crossbow. An email from 2012 refers to Crossbow as the “latest, most technologically up-to-date version of a Stingray system.”
But the civil liberties group said its public records lawsuit is not over. Customs and Border Protection (CBP), which was also named in the suit, has not yet turned over any documents sought by the ACLU, despite spending $2.5 million on buying at least 33 stingrays, according to a 2016 congressional oversight report.
“We are deeply skeptical of CBP’s assertion that they do not possess records about cell site simulators,” said Ramirez. “Given public information, the agency’s claim just doesn’t pass the sniff test.”
CBP has until June 12 to respond to the ACLU’s latest motion.
When reached, a spokesperson for CBP was unable to comment by our deadline. ICE did not respond to a request for comment.
ICE used ‘stingray’ cell phone snooping tech hundreds of times since 2017 by Zack Whittaker originally published on TechCrunch