How to Deploy Strategic Pentesting in Your Vulnerability Management Program
Test to Find the Exploitable Vulnerabilities and Their Root Causes
Vulnerability Management in Your Cybersecurity Program
Today’s complex software systems often include code that leaves them vulnerable to attack by hackers who are always looking for a way to break in. And even with a system with no inherent vulnerabilities, a misconfiguration or careless deployment of credentials handling can afford hackers an opportunity for infiltration. A record 26,448 software security flaws were reported in 2022, with the number of critical vulnerabilities up 59% on 2021. So a good cybersecurity program should include a program for vulnerability management.
Tactical vs. Strategic Penetration Testing in Vulnerability Management
Vulnerability management is the process of identifying and remediating weaknesses in your systems, including your applications, infrastructure and security processes. And a key component of that program should be penetration testing, actively probing your system to identify vulnerabilities so they can be analyzed, prioritized and remediated.
As companies move to agile models for software development, the release of new features or products becomes more frequent. And that code can introduce vulnerabilities. Similarly, more systems are being deployed in the cloud. And cloud assets can fall out of compliance or become susceptible to attacks after a single update.
Traditionally, pentesting has been performed on a tactical, one-time basis. But the most thorough penetration test, even if repeated periodically, is only a snapshot in time. While one-time pentesting can be an essential part of any vulnerability management program, this tactical approach is most appropriate for obtaining a picture of your security posture. Identify your vulnerabilities and address them as needed. It is also useful in testing for and proving compliance in regard to security standards such as OWASP, PCI and NIST.
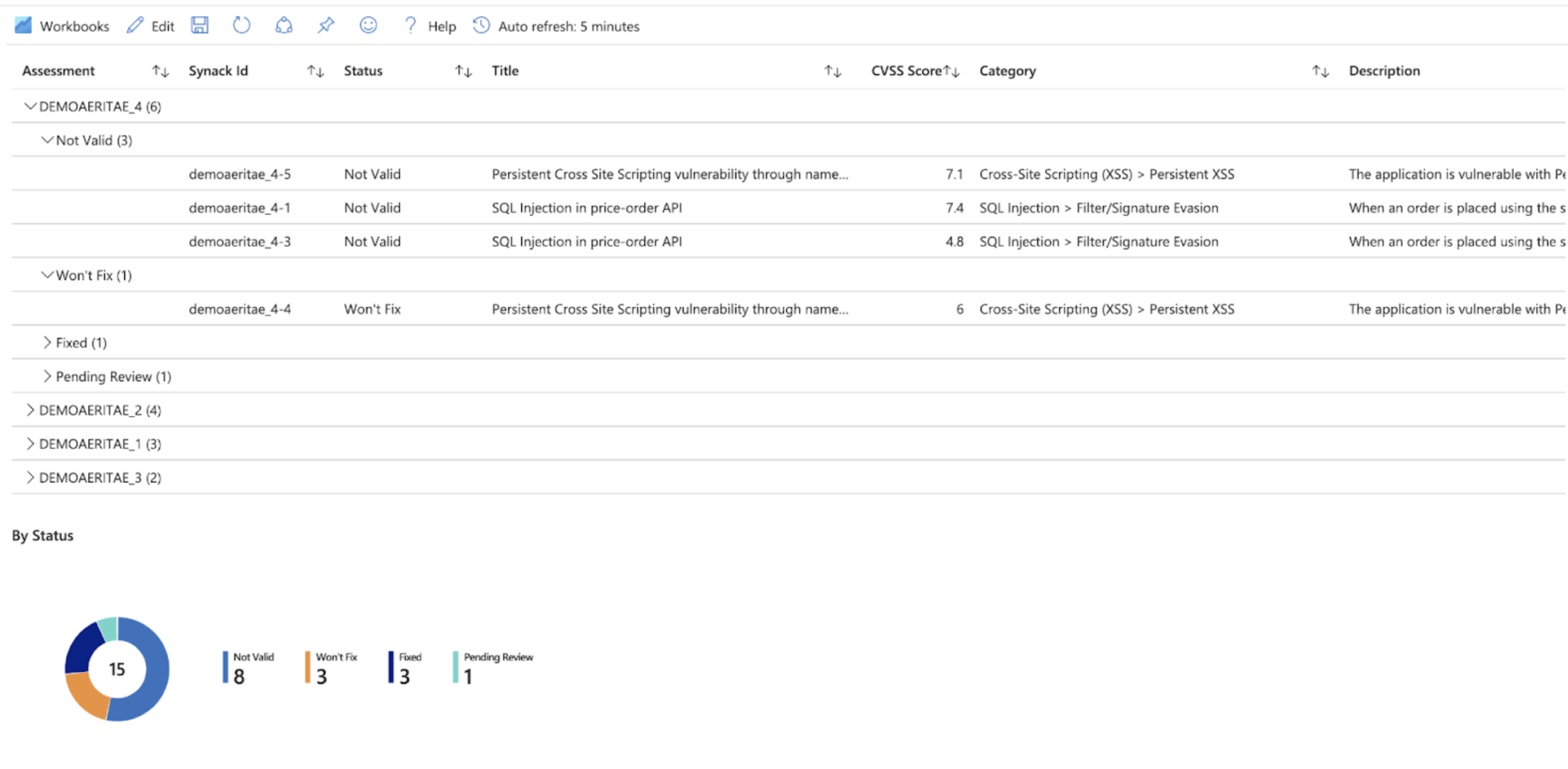
Comprehensive cybersecurity requires more strategic thinking, going beyond the concept of a snapshot. You need to leverage test results for operational purposes, track changes over time, understand performance across the organization, analyze root cause, and communicate your security posture. And to accomplish this you need to have a program of continuous pentesting like those available through Synack. Synack can pentest agile development output at multiple stages of development and assist developer and QA teams with quick remediation through real-time reporting and patch verification. Continuous testing is also best for cloud assets. To facilitate cloud security testing, Synack has integrations with AWS, Azure and GCP that enable detection of changes that could cause problems.
For strategic vulnerability management Synack provides continuous pentesting in 90- and 365-day increments (Synack90 and Synack365) to address a wide range of use cases. Both programs help you catch vulnerabilities as they are introduced, and track your security posture across the organization and over time.
Automated Scanning and Pentesting: A One-Two Punch For Identifying and Remediating Vulnerabilities
Two of the tools in the Synack platform, whether they are deployed tactically or strategically, that provide an effective one-two punch for identifying and remediating exploitable vulnerabilities are Synack SmartScan and Synack’s transformational penetration testing. Deploying these two tools can help you cut through the noise, taking automated vulnerability testing results and applying human intelligence to improve the vulnerability management workflow. You can address the problems that really matter.
Deploy SmartScan for Low-Importance Assets
Vulnerability scanning is most appropriate for low-importance assets. Traditional vulnerability scanners are good at identifying known vulnerabilities. But they typically treat all assets the same and are not able to distinguish exploitable vulnerabilities from the noise. They require expert reviews and triage. Synack SmartScan takes the scanning idea to another level. SmartScan is an automated set of scanning tools that continuously watch for changes in your environment to identify and triage security vulnerabilities. SmartScan identifies potential vulnerabilities and engages the Synack Red Team (SRT) to evaluate the results. The SRT along with Synack Operations generates a vulnerability report, including steps to reproduce and remediate the vulnerability. SmartScan enables rather than burdening your security and operations teams.
Deploy Pentesting for High-Importance Assets
Pentesting gives you the more accurate and complete vulnerability information that high-importance assets require. To pentest your organization Synack calls on a vetted community of security researchers to actively probe your assets for exploitable vulnerabilities, much like a hacker would. You get top-tier talent to find and fix exploitable vulnerabilities, and confirm remediation efforts across your external attack surface.
Deploy Synack Stand-Alone or in Partnership with Other Security Platforms
With Synack’s flexibility, you can integrate automated scanning and pentesting into your existing workflow, or deploy them as a new process. Either way you get comprehensive end-to-end offensive testing, taking you from discovery through to remediation. And Synack tools can be deployed as an add-on to larger security systems such as Splunk’s data platform or Microsoft’s Sentinel security information and event manager (SIEM).
Learn How Synack Can Help Protect Your Organization
For the most comprehensive vulnerability management, deploy continuous scanning and pentesting to help you identify and remediate vulnerabilities across your entire asset base.
The post How to Deploy Strategic Pentesting in Your Vulnerability Management Program appeared first on Synack.