HBO Max’s ‘Mad Men’ Vomit Scene Proves ‘Remastered’ Doesn’t Mean ‘Better’


Bitcoin Magazine

Nordic Giant Nordea Opens Crypto Door with Bitcoin-linked ETP
Nordea Bank Abp (Nordea) has announced that it will offer its customers access, from December 2025, to a synthetic exchange-traded product (ETP) whose underlying asset is Bitcoin (BTC).
According to Nordea’s official announcement, the product will be manufactured externally by CoinShares International Limited and made available through Nordea’s execution-only platform.
Under this model, customers may trade the product, but Nordea will not offer advisory services on it.
The bank cites two primary drivers for the move: the maturation of the European regulatory environment for crypto-assets, especially following the implementation of the Markets in Crypto‑Assets Regulation (MiCa) regime across the European Union in December 2024; and growing demand for virtual currencies among retail and institutional investors in the Nordic region.
The ETP in question is described as a “synthetic” product, meaning it provides exposure to Bitcoin via a traditional financial instrument rather than requiring direct custody of BTC.
Nordea emphasises that the offering is aimed at “experienced investors seeking alternative asset exposure.”
Here’s the broader context: ETPs and exchange-traded vehicles tied to cryptocurrencies have been proliferating across European venues, enabling both retail and institutional investors to access digital-asset exposure through familiar channels.
JUST IN: €648 billion Nordea to allow customers to trade #Bitcoin-linked ETP on its platforms.
— Bitcoin Magazine (@BitcoinMagazine) October 30, 2025
Europe is comingpic.twitter.com/L8hhxKscIZ
With Nordea’s move, one of the largest Nordic financial institutions is signalling its readiness to integrate crypto-exposure into its product suite.
At the same time, Nordea remains cautious. In its release, the bank underscores its historic “cautious stance” toward crypto — driven by the absence of investor-protection frameworks, regulatory clarity and supervision in the early days of the digital-asset markets.
For Bitcoin, this development may carry several implications: access broadened into the Nordic regulated-bank channel; increased legitimacy of ETP wrappers as a gateway to exposure; and potentially stronger competition among product issuers aiming to service bank-platform clients under regulated frameworks.
The product’s December launch means it aligns with the current regulatory momentum across Europe.
Still, caveats abound. A synthetic ETP structure carries its own risk profile (as investors are exposed via an issuer product rather than holding the underlying asset directly). Also, the “execution-only” nature means that retail customers may buy without advisory support.
Nordea Bank Abp is the leading financial-services group in the Nordic region. The group offers universal-banking services including personal banking, business banking, large-corporate and institutional banking, and asset & wealth management.
This post Nordic Giant Nordea Opens Crypto Door with Bitcoin-linked ETP first appeared on Bitcoin Magazine and is written by Micah Zimmerman.
Developing and updating software using an agile methodology has become increasingly popular and indeed has benefits compared with a traditional waterfall approach, including productivity efficiencies, flexibility and continuous improvement. But when it comes to validating software security, agile methodology also presents challenges.
With an agile Software Development Life Cycle (SDLC) also comes concurrent workflows, adjusting goals and frequent deliverable changes. Predictable static security testing methods that may have been suitable for a waterfall approach quickly fail to keep pace in a more dynamic agile SDLC.
To meet this challenge, we have partnered with Jira, the leading software development tool used by agile teams, to make continuous security validation an integrated part of the SDLC. Synack continuously tests application security throughout the development and update phases, so vulnerabilities can be discovered earlier in the life cycle even as the projects are frequently changing. Unlike traditional static security testing approaches, which run infrequently and with rigid scope, our security testing runs continuously with dynamic and open scope.
We offer insights and intelligence by delivering reports of exploitable vulnerabilities discovered through our premier security testing platform that seamlessly integrates the adversarial perspective of the world’s elite community of security researchers, the Synack Red Team (SRT), with our continuous scanning technology.
Our approach combines machine intelligence to surface well known and suspected vulnerabilities, with human expertise for open vulnerability discovery and detailed reporting about actual exploitable gaps in application security. The SRT provides specific recommendations to fix vulnerabilities and will retest as the software team applies patches. In this manner, software security posture can be continuously validated and improved throughout the SDLC rather than waiting until vulnerabilities manifest themselves late in the development process or worse yet, after being released to production.
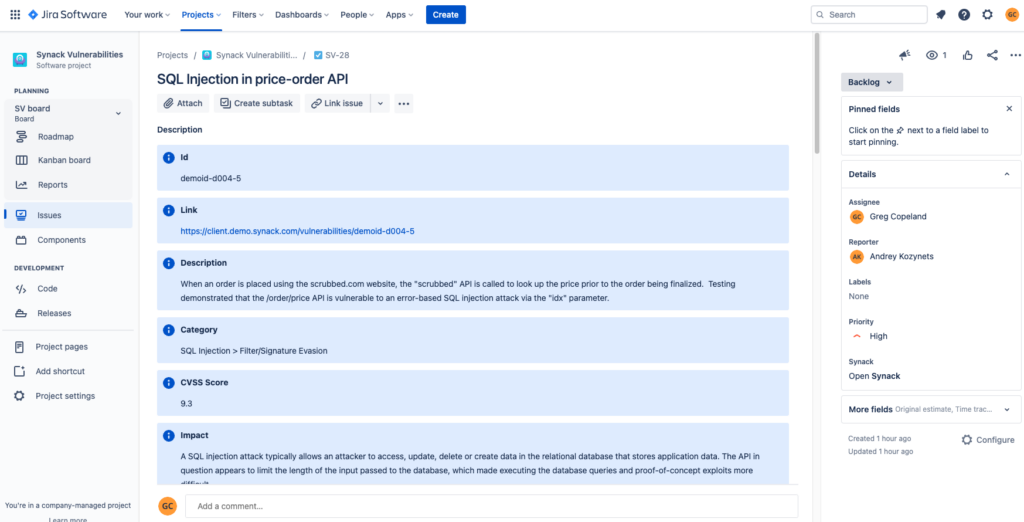
Sample security vulnerability ticket in Jira
The Synack App for Jira integrates Synack vulnerability findings with SDLC workflows so that security issues can be remediated more effectively and efficiently. By integrating Synack and Jira instances, we’ve removed the inefficiencies that come with vulnerability management and software development being independent, unintegrated workflows.
Any time new vulnerability findings are reported by the Synack Platform, it will also populate automatically within the associated Jira Project based on predefined configurations and field mappings. Anytime you make a status update on the Synack Platform or on Jira, the change will be synched to both platforms, allowing your security and development teams to see the same information concurrently and to track progress until the issue has been fixed.
Finally, security comments are synched to the Jira project so that all participants in the SDLC have access to the finding details, even if they don’t have direct access to security tools. Armed with real-time security findings your agile team can make course corrections immediately, before the problems compound and escalate.
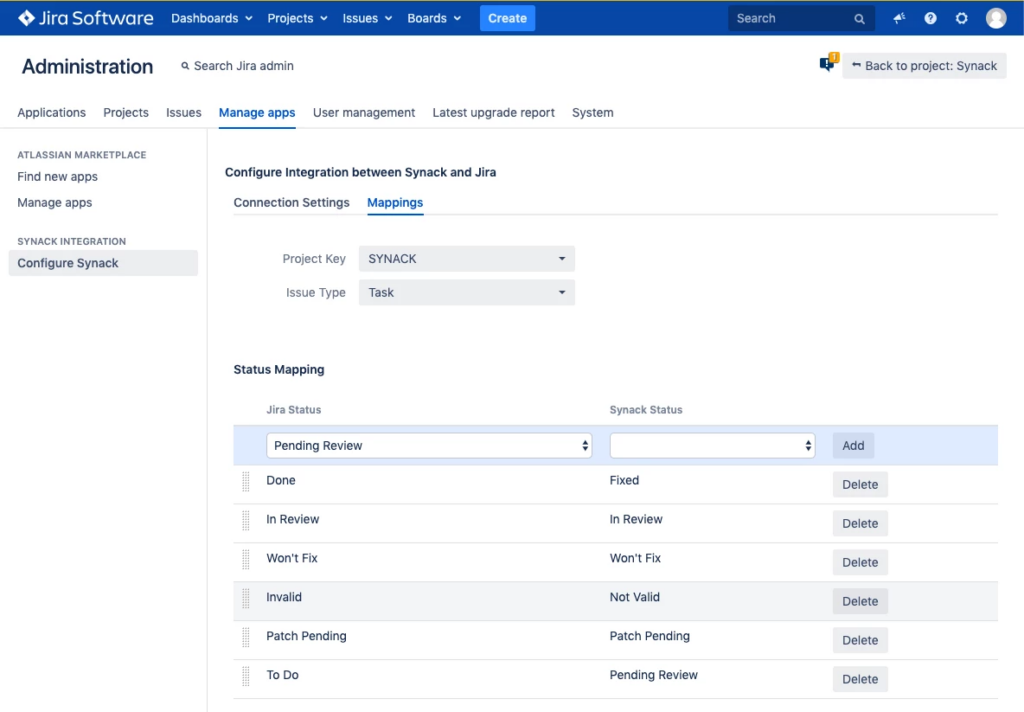
Mapping between status changes in Synack and Jira
You can access Synack’s App for Jira in a free, simple, and easy way. It’s a plug-and-play App that seamlessly installs on your existing Jira subscription and can be configured to work with your Synack Platform subscription within a matter of minutes. The Synack App for Jira is supported for on-premise (server and data center) and cloud instances of Jira.
For more information, see the Atlassian marketplace listing or read our solution brief. Contact our tech alliance team for further information technologypartners@synack.com.
The post Making Security Testing Part of Your Agile Software Development Life Cycle appeared first on Synack.
In your cybersecurity practice, do you ever worry that you’ve left your back door open and an intruder might sneak inside? If you answered yes, you’re not alone. The experience can be a common one, especially for security leaders of large organizations with multiple layers of tech and cross-team collaboration to accomplish live, continuous security workflows.
At Synack, the better way to pentest is one that’s always on, can scale to test for urgent vulnerabilities or compliance needs, and provides transparent, thorough reporting and coverage insight.
With Synack365, our Premier Security Testing Platform, you can find relief in the fact that we’re always checking for unlocked doors. To provide better testing oversight, we maintain reports that list all web assets being tested, which our customers have praised. Customer feedback indicated that adding continuous oversight into host assets would also help to know which host or web assets are being tested, when and where they’re being tested, and how much testing has occurred.
Synack’s expanded Coverage Analytics tells you all that and more for host assets, in addition to our previous coverage details on web applications and API endpoints, all found within the Synack platform. With Coverage Analytics, Synack customers are able to identify which web or host assets have been tested and the nature of the testing performed. This is helpful for auditing purposes and provides proof of testing activity, not just that an asset is in scope. Additionally, Coverage Analytics gives customers an understanding of areas that haven’t been tested as heavily for vulnerabilities and can provide internal red team leaders with direction for supplemental testing and prioritization.
Other forms of security testing are unable to provide the details and information Synack Coverage Analytics does. Bug bounty testing typically goes through the untraceable public internet or via tagged headers, which require security researcher cooperation. The number of researchers and hours that they are testing are not easily trackable via these methods, if at all. Traditional penetration testing doesn’t have direct measurement capabilities. Our LaunchPoint infrastructure stands between the Synack Red Team, our community of 1,500 security researchers, and customer assets, so customers have better visibility of the measurable traffic during a test. More and more frequently, we hear that customers are required to provide this kind of information to their auditors in financial services and other industries.
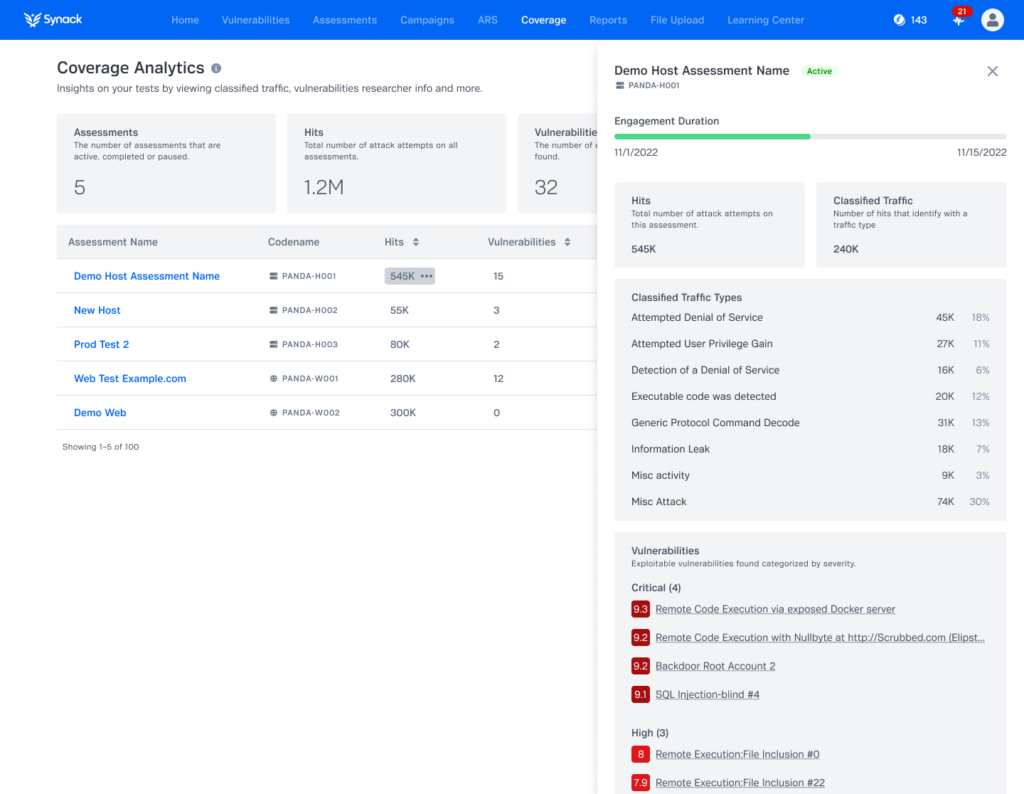
A look at the Classified Traffic & Vulnerabilities view in Synack’s Coverage Analytics. Sample data has been used for illustration purposes.
Starting today, security leaders can reduce their teams’ fears of pentesting in the dark by knowing what’s being tested, where and how much at any time across both web and host assets. Coverage Analytics makes sharing findings with executive leaders, board members or auditors simple and painless.
Current Synack customers can log in to the Synack Platform to explore Coverage Analytics today. If you have questions or are interested in learning more about Coverage Analytics, part of Synack’s Better Way to Pentest, don’t hesitate to contact us today!
The post Worry-free Pentesting: Continuous Oversight In Offensive Security Testing appeared first on Synack.
The overall goals of nearly any technology can be summed up by the title of a song by the popular French music duo Daft Punk: “Harder, Better, Faster, Stronger.” New technologies are commonly judged against two or more of these characteristics. Applying this to cybersecurity tools, does it harden my attack resistance? Can it do the job better with less cost or resources? Does it do the job faster? And ultimately are my defenses stronger?
But in the urgency to design and implement the features that will achieve these goals, there is one component that is often overlooked. Reporting. Can I get the right information into the hands of the right people in a form that they can use?
Original cybersecurity pentest reports were descriptions of what was done, what was found and what might be done about it. They were composed for the security team paying for the test and were usually in the form of a data dump. Three or four hundred page reports were commonplace, and why not? What better way to show all the work that you have done, even if the pentests didn’t actually produce any viable results.
Further, those reports were created once for each pentest resulting in a fossilized memento of what was done, usually destined to occupy a few MB of storage on a hard drive, and eventually forgotten in an archive.
Synack decided there had to be a better way to communicate pentesting results. They focused on three key innovations: customizability, scheduling and human components.
In this information age, too much information can be as punishing or painful as too little. Not everyone cares about every component of a pentest. For example, a painstaking regurgitation of the scope of the test may matter to an auditor, but not a developer tasked with patching found vulnerabilities. Synack reports are highly customizable, allowing for purpose-built, audience-customized reports to be created on the fly. Each person can get the report they need, without unnecessary information. And this sort of reporting uses less resources than generating a single report for everyone.
People throughout an organization have different appetites for information. We’ve seen organizations that want weekly reports on Continuous tests, but only for host and network assets. Others want a fresh report every time their web app has a new feature ship, coinciding with the 14-day sprint schedule that drives their CI/CD. Synack can handle all of those scenarios with reporting customization AND a robust role-based access control (RBAC) system. Synack’s RBAC customizable reporting also allows security teams to implement Least Privilege Access so various information needs can be met without the risk of testing data being seen or modified accidentally or by anyone without proper authorization. So testing results get in peoples’ hands without delay.
The most important question you need to ask about any cybersecurity test is, “Why do I care and what do I need to do?” Ultimately, with the thousands of discrete tests performed and vulnerabilities found, Synack decided that a human-written summary was usually what helped customers the most. Every Synack pentest comes with a human-written summary, written by people separate from the actual testing, triage or service delivery to gain maximum benefits from independent thinking. Customers get the actionable information they need to strengthen their cybersecurity defenses. And they get it in a form that is to the point and easy for them to digest.
To see our reporting feature in action, watch this short video.
The post Reporting Can Be the Hero or Villain of Your Cybersecurity Pentesting appeared first on Synack.
Synack, the premier security testing platform, has launched an API pentesting capability powered by its global community of elite security researchers. Organizations can now rely on the Synack platform for continuous pentesting coverage across “headless” API endpoints that lack a user interface and are increasingly exposed to attackers.
“Synack’s human-led, adversarial approach is ideal for testing APIs that form the backbone of society’s digital transformation,” said Synack CTO and co-founder Mark Kuhr, a former National Security Agency cybersecurity expert. “We are thrilled to offer customers a unique, scalable way to secure this growing area of their attack surfaces.”
Gartner estimates API abuses will be the most common source of data breaches in enterprise web applications this year. Synack enables organizations to verify exploitable API vulnerabilities like broken authorization and authentication–noted in the OWASP API top 10–can’t be abused by malicious hackers.
“Many organizations are struggling to find the top-tier cyber talent needed to root out API-specific vulnerabilities,” said Peter Blanks, Chief Product Officer at Synack. “We’re excited to extend our Synack platform to provide human-powered offensive security testing on APIs.”
Synack’s headless API capability builds on years of API pentesting experience through web and mobile applications. The new platform features allow customers to enter API documentation to guide testing scope and coverage. Next, researchers with the Synack Red Team attempt to exploit API endpoints in the way a real external adversary would.
Of the Synack Red Team’s over 1,500 global members, only those with proven API testing skills are activated on API requests, reducing noise. Synack’s Special Projects division led over 100 successful pentests against headless APIs in 2022, providing customers with critical proof-of-coverage reports while validating researchers’ API expertise.
Vulnerability submissions and testing reports are routed through Synack’s Vulnerability Operations team for a rigorous vetting process before being displayed in the platform, minimizing false positives and ensuring high-quality results.
For more information about Synack’s API security testing, visit our Solutions page.
The post Synack Expands Security Platform with Adversarial API Pentesting appeared first on Synack.
An astounding 82% of organizations believe they have experienced at least one data breach due to digital transformation, according to a recent survey. Fast paced cloud migrations have created new risks and challenges that require continuous monitoring of your digital assets. Attackers are now scanning for vulnerable endpoints within 15 minutes. Zero day vulnerabilities like Log4j are more frequent and difficult to address. Though the likelihood of a breach has never been higher, security teams still may be unable to commit to a full year of security testing due to a need for flexibility in developing and implementing a continuous testing strategy.
Synack is now offering Synack90, a 90-day pentest, as a new way for organizations to make meaningful progress toward implementing a continuous pentesting strategy.
Synack90 includes 90 days of Synack Red Team (SRT) open vulnerability discovery (OVD) penetration testing combined with the machine power of SmartScan, a scanner that sniffs out vulnerabilities. The offering also includes access to the Synack Platform for the duration of their contract, which means the ability to launch on-demand security tasks such as OSINT, zero day response and compliance checklists like NIST 800-53 or OWASP at the click of a button.
Synack provides a customer success resource that leads a kick off call. After an initial kickoff call, SRT testing and DAST scanning will kick off for a 90-day period. All SRT vulnerability reports are triaged by our Vulnerability Operations team. Synack provides reporting on actionable, exploitable vulnerabilities in real-time through the client portal, which customers can easily operationalize through the API, RBAC and ticketing integrations. Synack90 also includes patch verification for 90 days, which can drastically reduce time to remediate vulnerabilities during the testing period.
Many security teams are evolving toward a continuous pentesting model. There’s a number of reasons for the shift:
Synack customers are interested in Synack90 for a number of reasons, including testing high priority applications, fulfilling compliance obligations, discovering the value of continuous testing, and testing cloud services. Synack is providing an extra incentive with the launch of Synack90 that includes our Digital Reconnaissance or Web Premium checklist at a 50% discount when purchased with Synack90. Interested in Synack90? Read the full data sheet or contact us.
The post A Flexible Way to Pentest Continuously: Synack90 appeared first on Synack.
By Kim Crawley
The Synack Red Team is made up of hundreds of the best pentesters and tech practitioners in the world, hailing from countries across the globe with a variety of skills, who coordinate their efforts to conduct pentesting engagements and other security tests for Synack’s clientele.
When a large group of ethical hackers work together, they can find more exploits and vulnerabilities than traditional pentesting, which usually consists of two people with two laptops who conduct on-site testing over two weeks.
But when you have security researchers working as a collective, they are smarter, more adept and more creative. As cyber threats become increasingly sophisticated, the Synack Red Team (SRT) has the advantage of a diverse and holistic talent pool to take on the challenge.
Not only do the SRT bring a fresh perspective to pentesting, SRT members also help alleviate the widely felt skills gap in cybersecurity.
>> For an in-depth look at the SRT’s diversity of skills, read our white paper “Solving the Cyber Talent Gap with Diverse Expertise.”
Whether you’re looking to take your organization’s security testing to the next level or a curious thinker who aspires to have a pentesting career, SRT members gave useful advice and explained how it all works.
Özgür Alp, from Turkey, had a lot of pentesting experience prior to joining the SRT, but working with the growing community of 1,500 security researchers taught him the power of collaboration at scale.
“When I started at Synack, I had four years of experience as a pentester in a multi-global company,” Alp said. “After joining Synack and working as a full-time SRT member, I see that here we are focusing not only on the theoretical bugs but also trying to find the critical ones that matter and are exploitable within the real world scenarios.”
The gamification of vulnerability finding that happens on the researcher side of the platform means that you get their full attention and focus on finding vulnerabilities that matter. The more critical the vulnerability, the higher the payouts and recognition Synack rewards them with.
“I’m starting to focus on more complex scenarios, since you have time to work for that. For example, I actually learn what a theoretical bug could really mean in terms of business impact,” Alp said.
Emily Liu, like many SRT members, works on the Synack platform part-time. Many SRT already work in a cybersecurity role and use the opportunity to apply the knowledge they’ve learned from their day-time job to their Synack role and vice-versa.
“It sharpens my skills by allowing me to practice finding different vulnerabilities on real targets,” Liu said. “The whole process of doing work for SRT has taught me to think more creatively and to be more persistent, because you can find bounties so long as you put in the effort.”
But the work of the SRT can only be done with an “adversarial” perspective, from the outside-in. Büşra Turak explained the difference between being an SRT member and an employee or in-house consultant.
“It is usually enough to show the existence of a finding in consultancy firms that provide pentest services. But we don’t do that here,” she said. “We show how much we can increase the impact of the finding or we need to show how the vulnerability is exploited.”
In terms of bug bounties, red teaming and pentesting, Synack’s formula for vetting, monitoring and developing its SRT members puts them in another class of security researcher. SRT members are good at what they do from the start, and they’re also given immediate feedback for continuous improvement.
SRT member Nikhil Srivastava talked about what working with SRT has taught him.
“Initially, my reports were not up to the mark when I had just got into bug bounties. It was sent back to me multiple times for revision,” he said. “But, with the introduction of the Synack Quality Rule, we had to keep challenging ourselves with each new target launch—not only to find vulnerabilities but also to write a quality report that stands out from reports of other SRT members and is clearly understood by the clients. This helped me in leveling up.”
No matter if you’re able to get into the weeds of every vulnerability, a Synack report will thoroughly explain the potential exploit.
“I started reporting vulnerabilities that could precisely illustrate the impact even to a non-technical person and could be easily replicated by them,” Srivastava said.
If you’re curious about what it takes to join the Synack Red Team, start your journey here. To better understand how the SRT can solve your struggle with the cyber talent gap, read our latest white paper.
The post How the 1,500+ Synack Red Team Members Solve Your Most Critical Cybersecurity Vulnerabilities appeared first on Synack.
Vulnerability testing, whether via an automatic scanning program or human-based penetration testing, can find an overwhelming number of vulnerabilities in your system as recent trends would suggest. Since 2017, record numbers of Common Vulnerabilities and Exposures (CVEs) have been reported, with 2022 on track to set a new high.
Sorting through a record number of vulnerabilities to keep your organization secure is a daunting task without additional support and distillation.
The good news is that of all the vulnerabilities that might show up on a traditional vulnerability report, only around 5% of vulnerabilities discovered are ever exploited in the wild. And most of the exploited vulnerabilities are those with the highest CVSS (Common Vulnerability Scoring System) severity score of 9 or 10.
So how do you know which vulnerabilities in your system need to be addressed right now, and which can be put on the back burner? Some vulnerabilities are an immediate risk to the business, while others are highly unlikely to be exploited. Prioritizing critical vulnerabilities can mean the difference between preventing an attack and responding to one.
Finding and triaging critical vulnerabilities is where Synack’s pentesting outperforms traditional models. We continuously prioritize impactful vulns for your organization, surfacing only vulnerabilities that are reproducible and show exploitability.
The Synack Platform is the only solution to harness the best in augmented intelligence for more effective, continuous pentesting. First, the Synack Red Team (SRT), a group of vetted researchers, conducts open vulnerability discovery, while our automated SmartScan provides broad attack surface coverage. Together, they find vulnerabilities across your attack surface.
Next, the Synack Vulnerability Operations team assesses vulnerabilities found by the SRT and SmartScan by using a rigorous vetting process. Noise, such as duplicate submissions by SRT or non-replicable exploits, low-impact vulns, is kept to a minimum during penetration testing and you’re ultimately served vulnerabilities that present a clear risk.
This additional step to triaging is key to faster remediation and minimizing business risk.
The Vulnerability Operations team is a group of seasoned security professionals with hacking expertise. They are full-time Synack employees with extensive vulnerability knowledge–they’ve seen tens of thousands of them. For the most accurate triaging, high impact vulnerabilities are often reviewed by multiple team members. So, when you get a vulnerability report from Synack, you know that it matters.
The Vulnerability Ops team works alongside the SRT 365 days a year to bring order to the thousands of CVEs. When the team receives an initial vulnerability report, they will first validate the vulnerability by replicating it based on details provided in the report. When the vulnerability is confirmed, the Ops team proofreads and formats the report for utility and readability by a development team. Everything needed to reproduce the vulnerability is provided in each report.
After vulnerabilities are deemed exploitable and impactful, and the report has been detailed with steps to reproduce and suggestions on remediation, it will be published to the Synack Platform.
From there, the Synack Platform provides real-time findings on vulnerabilities found–their CVSS score, steps to remediate and evidence of the researcher’s finding. With this information you can address the vulnerabilities that are most important to your organization in a systematic and thorough manner.
Through the Synack Platform, teams are also able to check if their remediation efforts were successful with Patch Verification. Patch Verification can be requested on-demand, and the researcher will provide further communications on the patch efficacy.
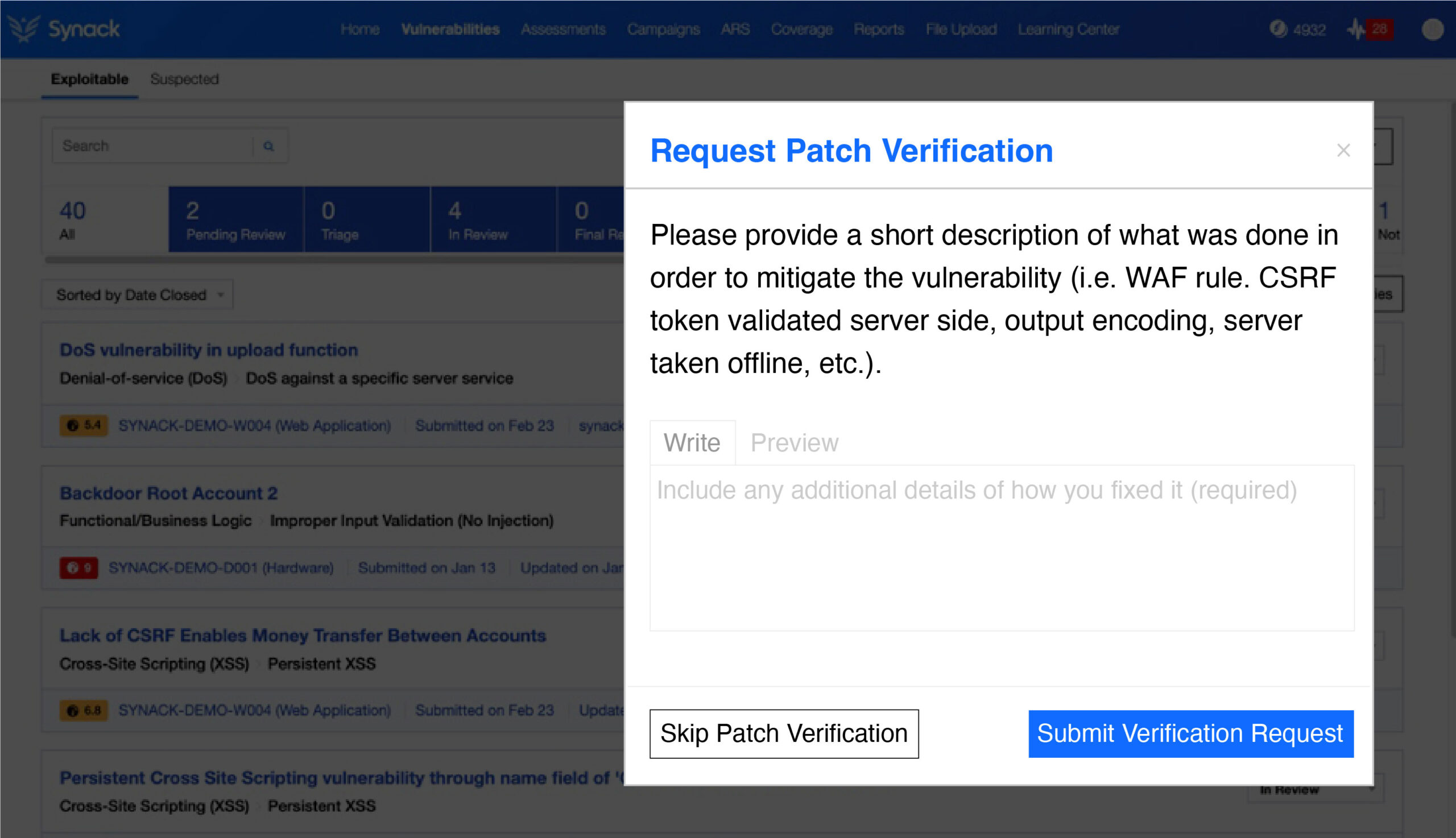
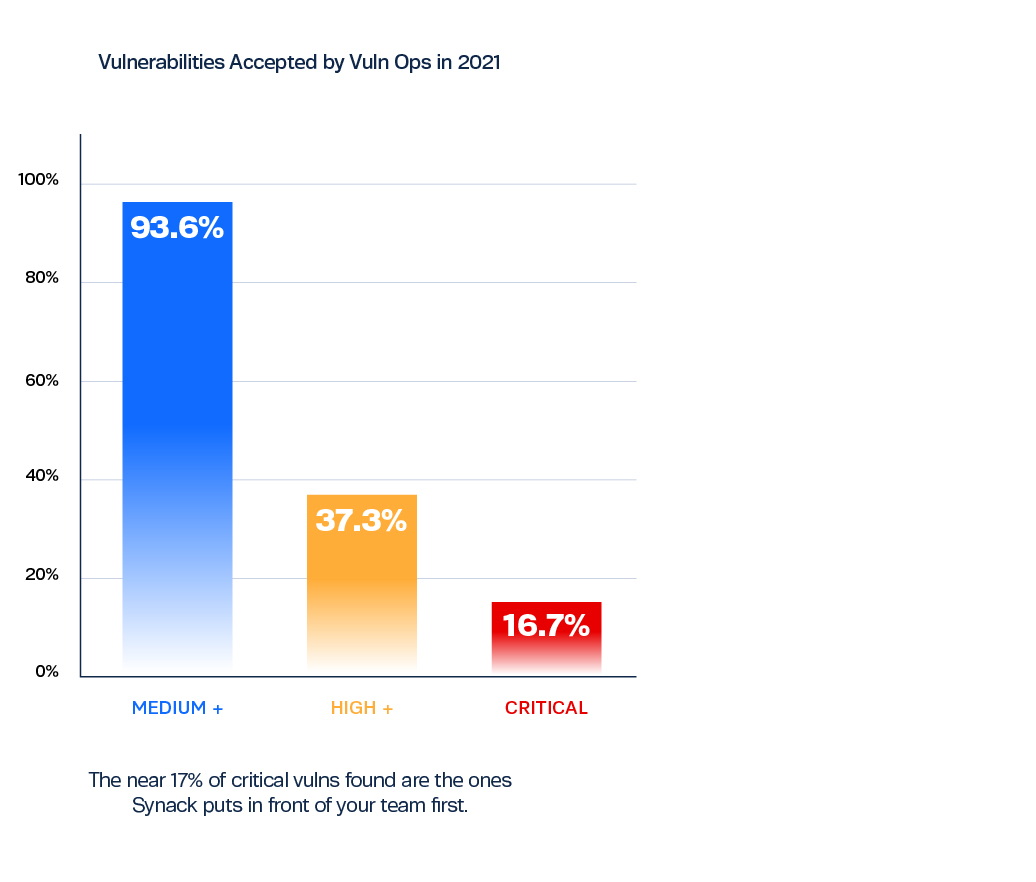
Most organizations don’t have the resources to go chasing every vulnerability reported from initial testing. To further safeguard your organization, someone needs to determine which are true vulnerabilities and which of those are exploitable and at what level of criticality. That process is noise reduction, and it is essential for any cybersecurity operation to shoot for the highest level of noise reduction before proceeding to remediation. Synack, through the Vulnerability Operations, team can take on this task for you.
Using Synack’s unique approach to continuous pentesting, your team will be able to proceed with confidence that their remediation efforts are critical to keeping the organization secure. Get started with Synack penetration testing today.
The post Synack Triaging Prioritizes the Vulnerabilities that Matter appeared first on Synack.
Kim Crawley
NVIDIA. Samsung. Microsoft. Okta. Globant. At least one of these Lapsus$ targets could be in your company’s tech supply chain. Regardless, these high-profile attacks highlight how interconnected and dependent IT systems become as companies grow and innovate, and the need to secure your supply chain.
Lapsus$, a global cybercrime group, has a tendency to go deep into a major tech vendor’s networks, find sensitive data and leak it. The breached data so far has included authentication credentials and encryption keys.
In the case of Lapsus$, they used a smaller vendor as a means of compromising a bigger target, like Okta, which then created a domino effect of having access to hundreds or thousands more credentials of those companies that contract with the bigger company. We saw a similar strategy with SolarWinds, wherein SolarWinds was breached and a vulnerability was pushed to its customers within a software update, leading to additional breaches. The risk of a breach is on both entry and exit: which vendors might lead to a breach within your network and which of your customers might then be breached?
The City of London police arrested several individuals who are alleged to be members of Lapsus$. But Lapsus$ struck Globant after the arrests, which indicates there may be many members who are continuing to execute cyber attacks.
Lapsus$ isn’t the first cybercrime group to wreak havoc upon vendor supply chains, and they definitely won’t be the last. Unfortunately, security researchers know that the proliferation of critical vulnerabilities is growing rapidly, and so too are the number of cyber attackers exploiting them. According to the CVE database, 18,325 vulnerabilities were added in 2020, and 20,149 in 2021. More than 6,000 vulnerabilities have been added in the first quarter of 2022. If this year continues at that rate, we’ll end 2022 with over 24,000 new vulnerabilities.
Traditional, point-in-time pentesting can’t keep up with the pace. When you add the complexity of cloud networks and diverse supply chains to the mix, it’s inevitable to lose visibility into your network’s security.
Cloud networks have been a boon for business, allowing companies to scale IT systems quickly and efficiently. But this also means that companies can add publicly accessible cloud services at will, with little oversight from the security team. Then factor in all of your vendors that provide services and infrastructure beyond security. Their vulnerabilities are also your company’s vulnerabilities. When cybercrime groups like Lapsus$ attack them, they’re also attacking your business up the chain.
You need a solution that will empower your security team to quickly find vulnerabilities wherever they emerge in your supply chain and remediate them with ease.
Synack combines an automated scanner, SmartScan, with the human intelligence of more than 1,500 carefully vetted security researchers from the Synack Red Team to find critical vulnerabilities across your network and tech supply chain. That combination of automation and human intelligence is at the core of the Synack Platform’s ability to bring you a better way to pentest. Within the Synack Platform, you can also request on-demand checks for specific vulns, like the OWASP top 10, or new critical CVEs when they appear, such as log4j.
It’s the most efficient and thorough way to conduct on-demand pentests in today’s complex computer. A few point-in-time pentests per year conducted by just a few people, simply to meet compliance, doesn’t cut it anymore. With densely networked supply chains and rapidly multiplying cloud services, new vulnerabilities are implemented faster than ever before. Whether Lapsus$ strikes one of your vendors, or one of many cybercrime groups that will inevitably emerge, your organization will be ready to defend against the evolving cyber threat landscape.
The post The Lapsus$ Threat Reinforces Critical Need to Secure Your Supply Chain appeared first on Synack.
Cybersecurity for web apps has never been more important than it is today. Websites and online applications are under constant attack by people and groups looking to penetrate systems to cause damage or steal vital information. And it’s not just criminals and mischief-makers; government-sponsored attackers are at work as well. Consider these cybersecurity statistics compiled by Patchstack:
Even more, telling is a 2019 report that found that 47% of all hacked websites contained at least one backdoor, allowing hackers access to the website. And the costs associated with data breaches continue to climb. The average cost of a data breach among companies surveyed in a 2021 IBM report reached $4.24 million per incident, the highest in 17 years.
Security personnel has a number of tools at their disposal to thwart cyberattacks. One of the most valuable is pentesting — checking for vulnerabilities that could give a hacker access to the system. But although not as reactive as remediating a breach that has already occurred, traditional pentesting is still somewhat reactive in nature. You’re being proactive in checking for vulnerabilities that could potentially be used by an attacker, but the vulnerabilities already exist. It’s like calling in a plumber to check for leaks in your pipes that could potentially cause water damage. The leaks are expected to already be there and be found, just as the vulnerabilities are in a pentest. So, although a valuable tool, pentesting only takes you part of the way to a truly security-hardened organization.
What you need is a way to check your security posture for conditions that might lead to a future vulnerability and remediate those issues as well. Only then can you consider your site truly security-hardened. It’s like that plumber fixing all the leaks in your pipes, then going back and making a systematic check of your pipes for conditions that could lead to a leak, such as rusting, pipes located in places where they are likely to freeze or improperly connected pipes.
ASVS provides for this by listing security conditions analogous to those that might lead to leaky pipes. This is how ASVS benchmarks enable proactive security.
The Application Security Verification Standard (ASVS) was developed by the Open Web Application Security Project (OWASP) to help organizations examine the state of their cybersecurity. The primary aim of the ASVS Project was to normalize the range in the coverage and level of rigor available in the market when it comes to performing Web application security verification using a commercially-workable open standard. The standard provides a basis for testing application technical security controls and technical security controls in the environment that protect against vulnerabilities such as Cross-Site Scripting (XSS) and SQL injection.
The ASVS benchmark provides a compilation of security controls that are expected to be in place in a well-secured application. It also provides developers with a list of requirements for secure development. The ASVS does not provide a framework to check for vulnerabilities. Rather, it provides a framework to check for controls that prevent, and conditions that could lead to, exploitable vulnerabilities. Synack recommends performing ASVS benchmark testing as part of an ongoing security process for maximum cybersecurity.
OWASP lists the following as objectives achieved by ASVS:
The ASVS framework is best suited for organizations that are relatively mature in their security posture. Since the tests don’t actually check for vulnerabilities, it is most appropriate to run ASVS tests after you have examined your system for existing vulnerabilities and remediated them through continuous and effective penetration testing. Once existing vulnerabilities have been discovered and remediated or resolved, then it is time to check your security controls for best practice implementations. Running the ASVS benchmark can then help the organization create a better defense in depth posture.
There are three levels of ASVS benchmarks available in the Synack Catalog – Basic, Standard, and Advanced. You choose the Synack ASVS Campaign to run based on the level that is appropriate for the organization. Across levels, an ASVS Campaign can ensure that an application follows best practices to protect user data and prevent exploitation by adversaries. An ASVS Campaign does this while respecting the appropriate level of security for an application, one that thoroughly protects the application, while not hampering user experience or business needs.
This process to engage Synack to prevent vulnerabilities before they occur is unique. Testing the ASVS framework lets us look for and proactively address the systemic issues that let the vulnerabilities come to an exploitable state and unlock the door for an attacker.
With an ASVS benchmark test, you will receive a detailed report from a researcher on the Synack Red Team, our community of global ethical hackers, regarding their findings on the security posture of your assets. Their mission is to evaluate your assets relative to the ASVS framework. The goal of this assessment is to determine if your security controls are adequate for the application use case your organization has.
This report can offer guidance on where efforts would be best applied to further harden and future-proof assets. It can also be used to show a year-over-year improvement in the asset hardness, and can help quantify the effectiveness with both the ASVS metrics and a reduction in vulnerability findings. Long-term, the ASVS campaign can help support a multi-year effort to reduce the attack surface and improve the controls in assets against flaws.
Completing an ASVS assessment for your organization is easy with Synack Campaigns. The ASVS campaigns are listed in the Security Benchmark section of the Catalog. Once credits are purchased, you can activate your campaign on-demand any time in the Synack Platform.
Synack researchers complete the missions specified by the ASVS benchmark tests. After completing them, your team can leverage Synack’s Custom Report feature for audit-ready reports that will provide you with a view of security issues discovered by our testing.
When you are comfortable that pentesting and resulting remediation has moved your site to a sufficiently secure security posture, evidenced by pentesting not finding a significant number of new vulnerabilities, then you can move on to running the Synack ASVS Campaign. After completing the ASVS Campaign and remediating any discovered issues, it’s time to set up a plan for periodic testing going forward. Then you can be assured that you have applied the most comprehensive security testing to protect your assets.
To learn more about Synack ASVS Campaigns and how it can expose conditions that could lead to exploitable vulnerabilities, contact Synack at sales@synack.com.
The post Get Ahead of Vulnerabilities With Proactive ASVS Benchmark Pentesting appeared first on Synack.
By Dan Mulvey, Regional Vice President, Federal
Synack has paved the way as a trusted leader in Cybersecurity testing and vulnerability disclosure management. Now, Synack is raising the bar even higher by achieving the FedRAMP Moderate “In Process” milestone, helping to make federal data secure. Synack’s sponsoring agency for FedRAMP is the U.S. Department of Health & Human Services (HHS). Synack’s Discover, Certify, Synack365 and Synack Campaigns offerings are now available on the FedRAMP Marketplace.
The Federal Risk and Authorization Management Program (FedRAMP) is a U.S. government-wide program that provides a standardized approach to security assessment, authorization and monitoring for cloud services. As part of its FedRAMP designation, Synack will be implementing 325 controls across 17 NIST 800-53 control families. Not only will this greatly enhance current protections for federal customer data, but it will also provide assurance to all our customers that Synack is reducing risk and providing government-grade data privacy protections.
Organizations spend on average $1.3M per year on erroneous or inaccurate alerts, and sadly, while the average company gets 1 million alerts per year, only 4% are ever investigated. During a time when attacks are at an all-time high, it’s more important than ever to have security protections in place with results you can trust. Synack’s new FedRAMP Moderate “In Process” designation underlines the company’s commitment to providing a high level of security across the board and quality results, speeding vulnerability management efforts and reducing risks to government assets.
Federal agencies have already been engaged with crowdsourced security testing solutions since such solutions were endorsed by the 2020 National Defense Authorization Act (NDAA), the National Cyber Strategy, and the Cybersecurity and Infrastructure Agency Binding Operational Directive (BOD) 20-01. Notably, as part of BOD 20-01, agencies are now required to develop vulnerability disclosure programs (VDPs).
Through partnering with Synack and leveraging Synack’s FedRAMP Moderate “In Process” designation, agencies can be reassured that their data is in safe hands. Synack will now provide the following benefits to federal agencies:
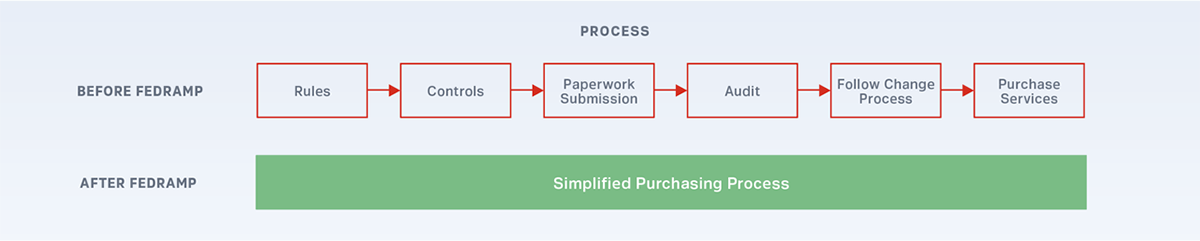
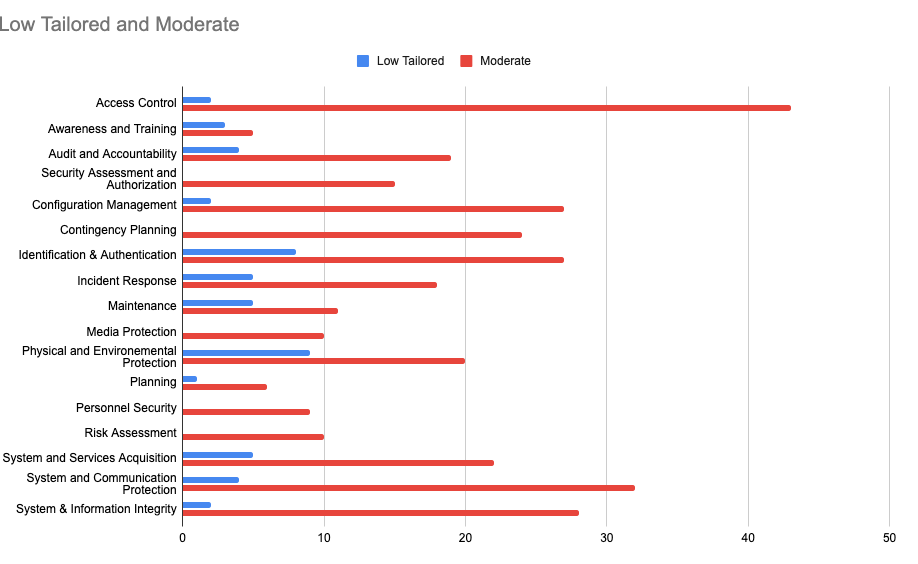
Synack is the only crowdsourced security company that has achieved the “In Process” status at the Moderate level. FedRAMP levels vary across the number of controls required, the sensitivity of the information, and the network access for government applications. Cloud service providers (CSPs) are granted authorizations at four impact levels: LI-SaaS (Low Impact Software-as-a-Service), Low, Moderate and High.
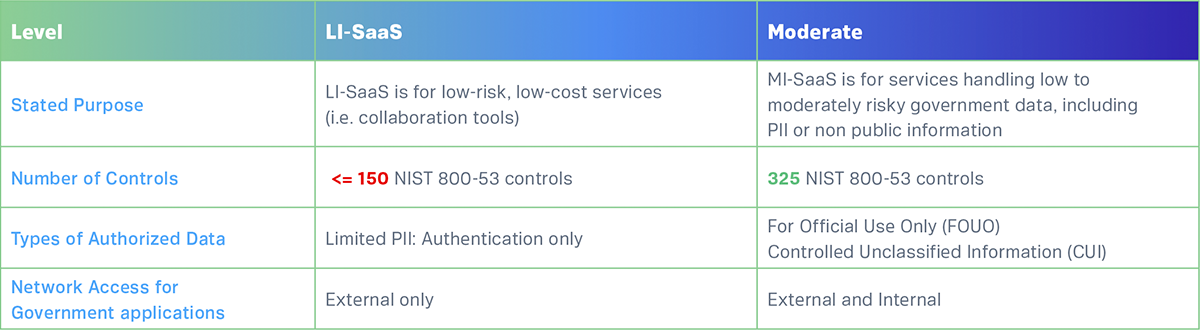
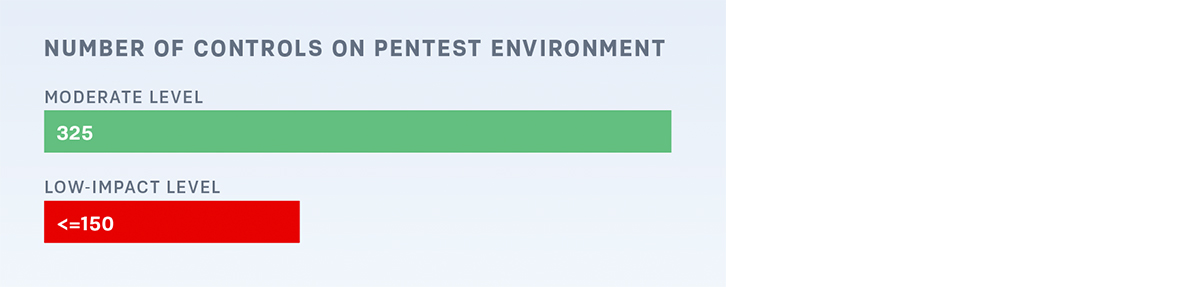
The stark difference in the control required is particularly apparent when you compare each of the 17 NIST 800-53 control families side by side. There are drastically more requirements for certain control families like access control, identification and authentication, and system and information integrity. These additional controls that Synack is adhering to ensure that your government assets—whether external or internal—stay secure.
If you’d like to learn more about Synack’s FedRAMP environment or solutions for your Federal SOC, click here to book a meeting with a Synack representative.
The post Synack Achieves FedRAMP Moderate In Process Milestone appeared first on Synack.
At Synack, we’re truly committed to making the world a safer place. We’re doing that by helping organizations defend themselves against an onslaught of cyberattacks. We’re harnessing the tremendous power of the Synack Red Team, our community of the most skilled and trusted ethical hackers in the world, and through the most-advanced security tools available today to deliver continuous penetration testing (and more) with actionable, prioritized results.
Now, the Synack Platform is expanding to help organizations globally overcome the worldwide cybersecurity talent gap. I am excited to announce the launch of Synack Campaigns to provide on-demand access to the SRT, who will be available 24/7 to execute specific and unique cybersecurity tasks whenever you need them — and deliver results within hours. This new approach to executing targeted security operations tasks will fundamentally change organizations’ approach to cybersecurity by providing on-demand access to this highly skilled community of security researchers.
During my time at Synack, I’ve seen firsthand how the Synack Operations and Customer Success teams creatively engage with the SRT to address a growing range of clients’ security operations tasks, in addition to our traditional vulnerability discovery and penetration testing services.
Now, we are making these targeted security activities directly available to every organization in the form of Synack Campaigns, available through the new Synack Catalog, also launching today on the Synack Client Platform.
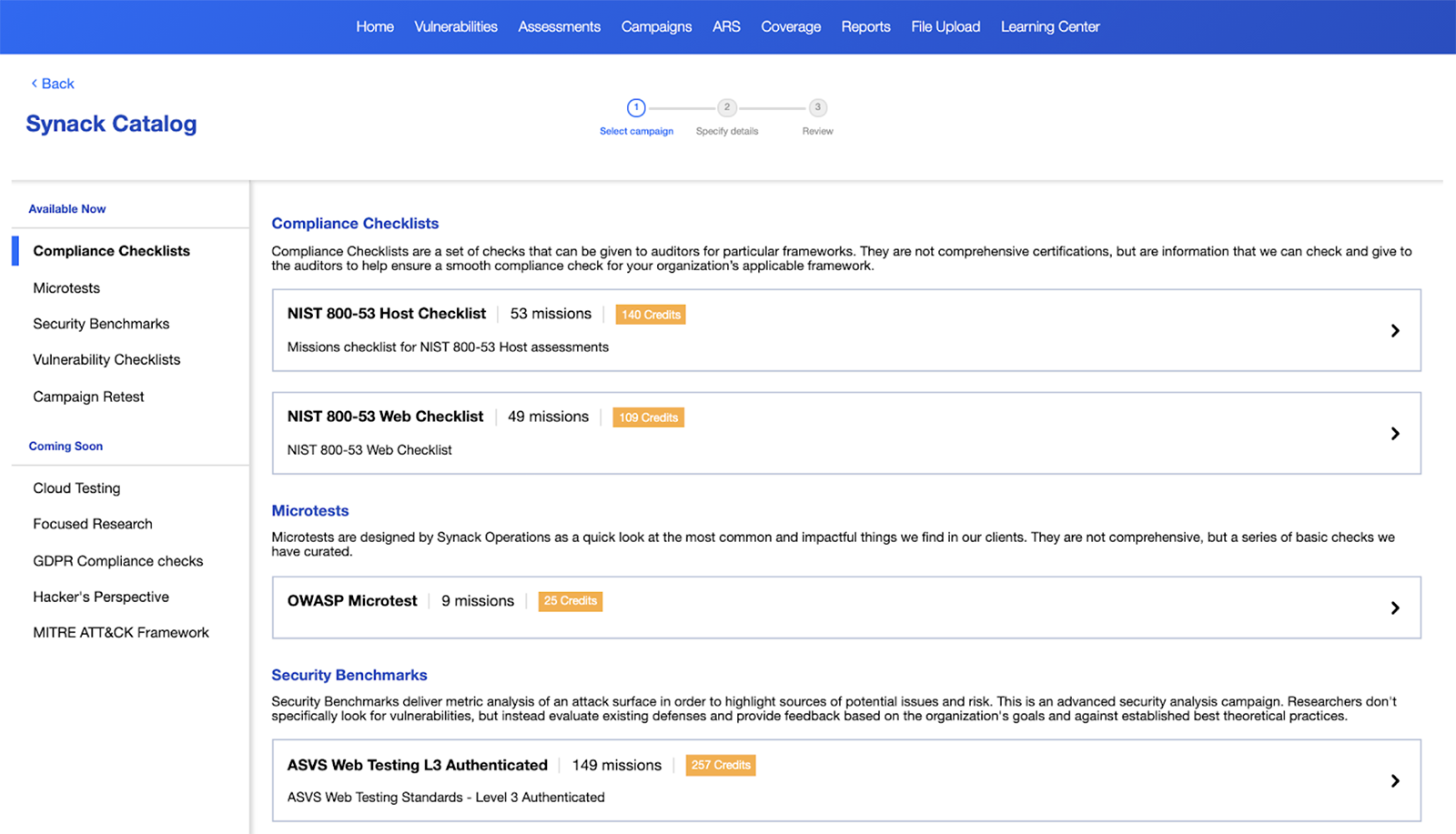
I know from speaking to our clients across multiple industries that security teams are struggling to keep pace with the speed of product development. At the same time, they are trying to scale defenses to meet the complexity and magnitude of today’s threats. Our customers ascribe challenges with their growing backlog of security tasks such as CVE checks and cloud configuration reviews. On top of all of that, there’s the need to implement industry best-practice frameworks such as OWASP & Mitre Att&ck. Essentially, customer security teams are struggling with demanding workloads and have asked us for assistance in a number of areas:
Synack Campaigns expands the core capabilities of the Synack Platform, including our trusted community of researchers, an extensive set of workflows, payment services, secure access controls and intelligent skills-based task-routing to provide customers with the ability to execute a growing catalog of cybersecurity operations.
With Synack Campaigns our researchers can augment internal security teams by performing targeted security checks such as:
Synack Campaigns are built to complement our vulnerability management and pentesting services, and help customers achieve long-term security objectives, such as Application Security, M&A Due Diligence, and Vulnerability Management.
I’m excited for you to learn more about Synack Campaigns and to hear how you and your teams would like to leverage our on-demand community of researchers to address your organization’s growing operational security needs.
Peter Blanks is Synack’s Chief Product Officer.
The post The Synack Platform Expands to Confront the Cyber Skills Gap appeared first on Synack.