Cloudflare Suffers Global Outage
This latest event follows hot on the heels of Nov. 18, when Cloudflare was hit by a global outage for several hours.
The post Cloudflare Suffers Global Outage appeared first on TechRepublic.
This latest event follows hot on the heels of Nov. 18, when Cloudflare was hit by a global outage for several hours.
The post Cloudflare Suffers Global Outage appeared first on TechRepublic.
This latest event follows hot on the heels of Nov. 18, when Cloudflare was hit by a global outage for several hours.
The post Cloudflare Suffers Global Outage appeared first on TechRepublic.
Handing over your personal information to sign up for a mobile carrier is expected, but what if it didn’t have to be that way? If you’re tired of your data being misused by the company that keeps you connected, then a new startup wireless service might be right up your alley.

Are you using a VPN and wondering why your internet connection feels slower than it used to? I wondered the same thing, so I set out to measure just how much a VPN affected my internet speed at home.

Home Assistant is amazing because it’s free, but it’s not always the easiest platform in the world to use. Though you can choose to pay for remote access by signing up to Home Assistant Cloud or go it alone with VPN access, there’s actually another easy way to add remote access to your smart home.

Home Assistant is a free, open-source, and independent smart home platform, but did you know there’s a company called Nabu Casa chipping in behind the scenes? If you want to pay to make remote access and cloud backup as easy as possible, that’s where your money goes.

Progress bars are everywhere, but we hardly ever give them a second thought. They have a little bit of mystery to them though. You might have noticed that downloads or file transfers sometimes get stuck at 99%. At times, they jump or stall. Sometimes they even fail at 99%. It happens because progress bars always lie, a little bit.

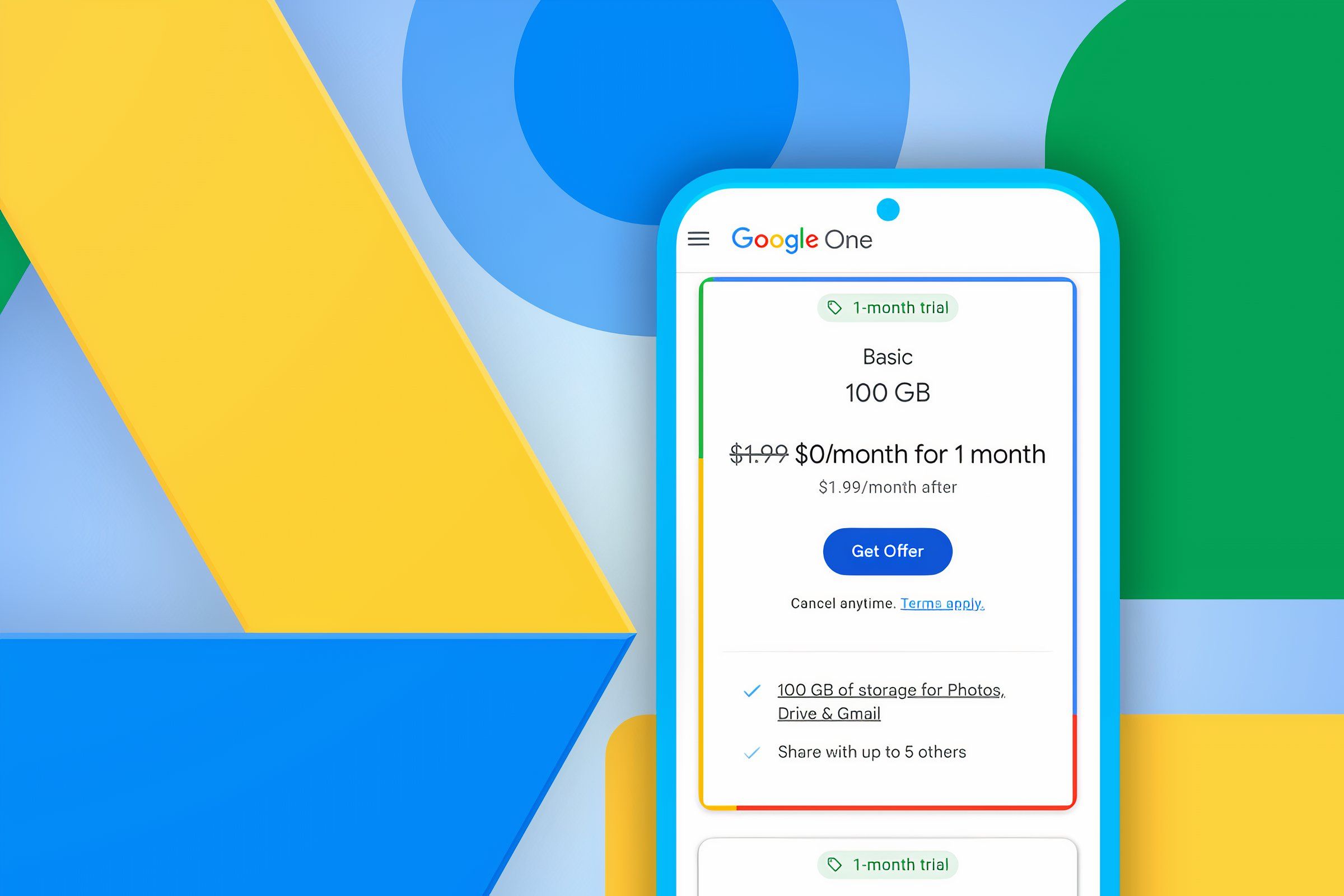
Google Drive is a storage solution, but most of us treat it like a digital junk drawer. Files end up in random folders, duplicates stack up, and finding anything becomes a pain. The good news? With a bit of cleanup, you can sort out the clutter and tidy up your storage in just one afternoon.
Google is adding 6GHz and 2.4+6GHz hotspot modes to Android, giving users faster tethering while keeping older devices connected.
The post Your Android hotspot is about to get much faster appeared first on Digital Trends.

When was the last time you upgraded your Wi-Fi router? If you can't remember because you've had your router for many years, there's a good chance that it's time for an upgrade.

You've heard that the world's infrastructure runs on Linux, and how important Free and Open Source (FOSS) software is to just about all the technology we enjoy every day, but there are some (to bring out the old cliché) unsung heroes of FOSS without which your stuff just wouldn't work—and you should at least know their names.

Read more of this story at Slashdot.
Google and Amazon are particularly good at selling the smart home vision, but these platforms have some big drawbacks, too. Consider switching to or starting out with a more capable and reliable alternative, which will save you money and frustration in the long run.

Read more of this story at Slashdot.
Read more of this story at Slashdot.

This post lays out how we think about incidents like Cloudflare’s outage this week, why pure smart‑contract control planes with timelocks change the failure modes, and where zero‑knowledge proofs fit.
On Nov 18, 2025 at 11:20 UTC, Cloudflare’s edge began returning 5xx for a big slice of traffic. The root trigger wasn’t an attacker; it was a ClickHouse permissions change that made a query return duplicate rows. That query generated a Bot Management “feature file” shipped to every edge box every few minutes.
The duplicates doubled the file and bumped the feature count over 200. The bot module had a hard cap and a unwrap() that panicked on overflow. As nodes alternated between “old-good” and “new-bad” outputs every five minutes, the fleet oscillated until all shards were updated and stayed bad.
Cloudflare halted the publisher at 14:24, shipped a last‑known‑good file at 14:30, and reported full recovery at 17:06. The follow‑ups they listed: harden ingestion of internal config, add global kill switches, and review failure modes across modules.
See Cloudflare’s own postmortem for the full timeline and code snippets.
There are two separate problems in that story:
You still fix (2) in code reviews. But (1) is where blockchains shine: as a tamper‑evident, programmable gate in front of rollouts.
If you compress the idea to one sentence: no config becomes “current” unless a smart contract says so, and the contract only flips that flag after a timelock and a proof that the artifact obeys invariants. That one sentence implies a complete architecture.
Turns out public blockchains, especially built on Ethereum, the EVM chains running the Ethereum Virtual Machine and consensus layer, offer a good solution to that problem.
Latency fit. Ethereum finalizes in epochs, but L2s confirm in seconds (OP Stack targets ~2s; zkSync ~1s; many systems expose fast attestation). It’s good enough for five‑minute control‑plane cadences, see for instance the OP block time discussion or Circle’s attestation timings).
Attach a succinct proof with every artifact and verify it on chain. That’s exactly what we do for our Chainwall protocol, although for a different kind of data!
The core goal is to prove basic properties: row_count <= 200, sorted + unique by key, schema matches regex and type rules, filesize <= N. You can either fit the whole logic onchain, or rely on Plonk/Groth circuits for larger expressions. For instance, a zk‑VM guest can parse CSV/Parquet/JSON and emits a SNARK. You don’t have to reveal the contents, only the commitment. Both research and production systems for regex in ZK exist (e.g., Reef and related zk‑regex work), which makes schema checks realistic.
There’s two practical paths:
Edges poll the registry and only adopt artifacts that are green‑lit on chain. To avoid trusting a third‑party RPC, run a light client in your control plane (e.g., Helios) or plan for the Portal Network. That way, edges verify headers and inclusion proofs locally before they accept any “new current” state.
Kill switch & rollback are just bits in the contract, honored by the edge. Cloudflare explicitly called out the need for stronger global kill switches; putting that switch in a small, audited contract gives you a single source of truth under stress.
CloudFlare event was not an attack, but they initially thought so and that was indeed likely! As we’ve seen in crypto security: attackers don’t just chase keys; they coerce the control plane.
Our position: control of digital assets must live in smart contracts guarded by timelocks and multisigs, not in private credentials, CI tokens, cloud ACLs, or admin dashboards. If your deploy or “change owner” action must traverse a contract’s schedule() and execute() path, even a rootkit on a developer laptop can’t jump the queue. The time delay is a circuit breaker you can count on, and the on‑chain audit trail is objective. That only leaves the “what if the thing we’re promoting is malformed?” question, which is exactly what “proof‑carrying config” answers.
We also believe there’s a considerable market for trust-minimized applications. We’re only building the right foundations now for a first, well-defined use case at OKcontract Labs.
When a Feature File Tripped the Internet was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.


High-profile services affected include ChatGPT, Sora, Shopify, and Elon Musk’s social media platform X.
The post Cloudflare Outage Hits Major Websites appeared first on TechRepublic.
High-profile services affected include ChatGPT, Sora, Shopify, and Elon Musk’s social media platform X.
The post Cloudflare Outage Hits Major Websites appeared first on TechRepublic.