Reading view
Police Seize Cryptomixer Domains, Infrastructure and 28M Dollars in Bitcoin
Dark Web Job Market Evolved – Prioritizes Practical Skills Over Formal Education
The underground labor market has undergone a significant transformation. According to new research analyzing 2,225 job-related posts collected from shadow forums between January 2023 and June 2025. The dark web job market now emphasizes practical skills and real-world experience over traditional credentials, marking a notable shift from previous patterns and reflecting broader global employment trends. […]
The post Dark Web Job Market Evolved – Prioritizes Practical Skills Over Formal Education appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

DoD failing to address growing security threats posed by publicly available data
A government watchdog is sounding the alarm about a growing national security threat online. Rather than a traditional cyberattack, however, this one comes from the everyday digital footprints service members and their families leave across the internet.
A new Government Accountability Office report warns that publicly accessible data — from social media posts and location tracking to Defense Department press releases — can be pieced together by malicious actors to identify military personnel, target their families and disrupt military operations.
According to GAO, while the Pentagon has taken some steps to address the threat, its efforts remain scattered, inconsistent and lack coordination.
“We found that the department recognized that there were security issues, but they weren’t necessarily well-prepared to respond to them because it was new, because it didn’t necessarily neatly fit into existing organizational structures or policies or doctrines, and that’s a consistent story with the department,” Joe Kirschbaum, director of the defense capabilities and management team at GAO, told Federal News Network.
To understand the risks posed to DoD personnel and operations that come from the aggregation of publicly accessible digital data, the watchdog conducted its own investigation and built notional threat scenarios showing how that information could be exploited. GAO began by surveying the types of data already available online and also assigned investigators to scour the dark web for information about service members.
In addition to basic social media posts, investigators found data brokers selling personal and even operational information about DoD personnel and their families — information that can be combined with other publicly available data to build a more complete profile.
“Once you start putting some of these things together, potentially, you start to see a pattern — whether it’s looking at individuals, whether it’s the individuals linked to military operational units or operations themselves, family members. Nefarious actors can take these things and build them into a profile that could be used for nefarious purposes,” Kirschbaum said.
One of GAO’s threat scenarios shows how publicly accessible information can expose sensitive military training materials and capabilities. Investigators found that social media posts, online forums and dark-web marketplaces contained everything from military equipment manuals, detailed training materials, and photos of facility and aircraft interiors. When combined, these digital footprints can reveal information about equipment modifications, strategic partnerships or potential vulnerabilities, which can be used to clone products, exploit weaknesses or undermine military operations.
And while DoD has identified the public accessibility of digital data as a “real and growing threat,” GAO found that DoD’s policies and guidance are narrowly focused on social media and email use rather than the full range of potential risks from aggregated digital footprints.
For instance, the DoD chief information officer has prohibited the use of personal email or messaging apps for official business involving controlled unclassified information. But that policy doesn’t address the use of personal accounts on personal devices for unofficial tasks involving unclassified information — such as booking travel, accessing military travel orders, or posting on social media — activities that can pose similar risks once aggregated.
In addition, DoD officials acknowledged that current policies and guidance do not fully address the range of risks created by publicly accessible digital information about DoD and its personnel. They said part of the challenge is that the department has limited authority to regulate actions of DoD personnel and contractors outside of an operational environment.
“In general, except for the operation security folks, the answer was they didn’t really consider this kind of publicly available information in their own sphere. It’s not like they didn’t recognize there’s an issue, but it was more like, ‘Oh yeah, that’s a problem. But I think it’s handled in these other areas.’ Almost like passing the buck. They didn’t understand, necessarily, where it was handled. And the answer was, it should probably be handled collectively amidst this entire structure,” Kirschbaum said.
The officials also said that while they had planned to review current policies and guidance, they “had not collaborated to address digital profile risks because they did not believe the digital profile threat and its associated risks aligned with the Secretary of Defense’s priorities,” including reviving warrior ethos, restoring trust in the military and reestablishing deterrence by defending the homeland.
“One of our perspectives on this is we know we’re not sure where you would put this topic in terms of those priorities. I mean, this is a pretty clear case where it’s a threat to the stability and efficacy of our military forces. That kind of underlines all priorities — you can’t necessarily defend the homeland with forces that have maybe potential operational security weaknesses. So it would seem to kind of undergird all of those priorities,” Kirschbaum said.
“We also respect the fact that as the department’s making tough choices, whether it’s concentrations of policy, financial and things of that nature, they do have to figure out the most immediate ways to apply dollars. For example, we’re asking the department to look across all those security disciplines and more thoroughly incorporate these threats in that existing process. The extent they’re going to have to make investments in those, they do have to figure out what needs to be done first and where this fits in,” he added.
GAO issued 12 recommendations to individual components and agency heads, but at its core, Kirschbaum said, is the need for the department to incorporate the threat of publicly available information into its existing structure.
“In order to do that, we’re asking them to use those existing structures that they do have, like the security enterprise executive committee, as their collaborative mechanism. We want that body to really assess where the department is. And sometimes they’re better able to identify exactly what they need to do, rather than us telling them. We want them to identify what they need to do and conduct those efforts,” he said.
The post DoD failing to address growing security threats posed by publicly available data first appeared on Federal News Network.

© The Associated Press
Dark Web Search Engines in 2025 – Enterprise Monitoring, APIs and IOC Hunting
Initial Access Brokers (IAB) in 2025 – From Dark Web Listings to Supply Chain Ransomware Events
Everest Ransomware Claims AT&T Careers Breach with 576K Records
Dark Web Search Engines in 2025 – Rankings, Risks & Ethical Trade-offs
Darknet Communications in 2025 – From IRC Forums to Telegram Crime Networks
Leveraging OSINT from the Dark Web – A Practical How-To
How the Internet of Things (IoT) became a dark web target – and what to do about it
By Antoinette Hodes, Office of the CTO, Check Point Software Technologies.
The dark web has evolved into a clandestine marketplace where illicit activities flourish under the cloak of anonymity. Due to its restricted accessibility, the dark web exhibits a decentralized structure with minimal enforcement of security controls, making it a common marketplace for malicious activities.
The Internet of Things (IoT), with the interconnected nature of its devices, and its vulnerabilities, has become an attractive target for dark web-based cyber criminals. One weak link – i.e., a compromised IoT device – can jeopardize the entire network’s security. The financial repercussions of a breached device can be extensive, not just in terms of ransom demands, but also in terms of regulatory fines, loss of reputation and the cost of remediation.
With their interconnected nature and inherent vulnerabilities, IoT devices are attractive entry points for cyber criminals. They are highly desirable targets, since they often represent a single point of vulnerability that can impact numerous victims simultaneously.
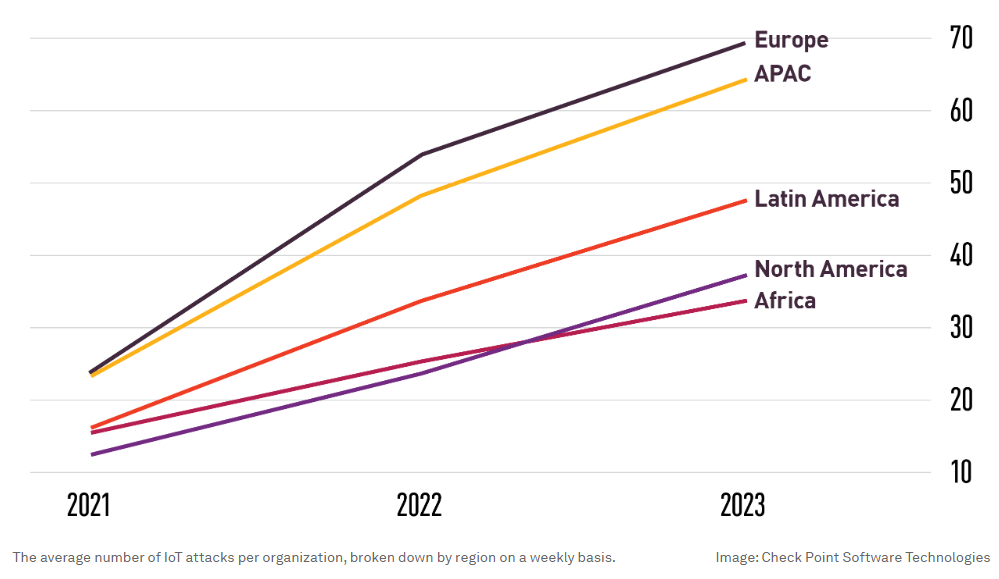
Check Point Research found a sharp increase in cyber attacks targeting IoT devices, observing a trend across all regions and sectors. Europe experiences the highest number of incidents per week: on average, nearly 70 IoT attacks per organization.
Gateways to the dark web
Based on research from PSAcertified, the average cost of a successful attack on an IoT device exceeds $330,000. Another analyst report reveals that 34% of enterprises that fell victim to a breach via IoT devices faced higher cumulative breach costs than those who fell victim to a cyber attack on non-IoT devices; the cost of which ranged between $5 million and $10 million.
Other examples of IoT-based attacks include botnet infections, turning devices into zombies so that they can participate in distributed denial-of-service (DDoS), ransomware and propagation attacks, as well as crypto-mining and exploitation of IoT devices as proxies for the dark web.
The dark web relies on an arsenal of tools and associated services to facilitate illicit activities. Extensive research has revealed a thriving underground economy operating within the dark web. This economy is largely centered around services associated with IoT. In particular, there seems to be a huge demand for DDoS attacks that are orchestrated through IoT botnets: During the first half of 2023, Kaspersky identified over 700 advertisements for DDoS attack services across various dark web forums.
IoT devices themselves have become valuable assets in this underworld marketplace. On the dark web, the value of a compromised device is often greater than the retail price of the device itself. Upon examining one of the numerous Telegram channels used for trading dark web products and services, one can come across scam pages, tutorials covering various malicious activities, harmful configuration files with “how-to’s”, SSH crackers, and more. Essentially, a complete assortment of tools, from hacking resources to anonymization services, for the purpose of capitalizing on compromised devices can be found on the dark web. Furthermore, vast quantities of sensitive data are bought and sold there everyday.
AI’s dark capabilities
Adversarial machine learning can be used to attack, deceive and bypass machine learning systems. The combination of IoT and AI has driven dark web-originated attacks to unprecedented levels. This is what we are seeing:
- Automated exploitation: AI algorithms automate the process of scanning for vulnerabilities and security flaws with subsequent exploitation methods. This opens doors to large-scale attacks with zero human interaction.
- Adaptive attacks: With AI, attackers can now adjust their strategies in real-time by analyzing the responses and defenses encountered during an attack. This ability to adapt poses a significant challenge for traditional security measures in effectively detecting and mitigating IoT threats.
- Behavioral analysis: AI-driven analytics enables the examination of IoT devices and user behavior, allowing for the identification of patterns, anomalies, and vulnerabilities. Malicious actors can utilize this capability to profile IoT devices, exploit their weaknesses, and evade detection from security systems.
- Adversarial attacks: Adversarial attacks can be used to trick AI models and IoT devices into making incorrect or unintended decisions, potentially leading to security breaches. These attacks aim to exploit weaknesses in the system’s algorithms or vulnerabilities.
Zero-tolerance security
The convergence of IoT and AI brings numerous advantages, but it also presents fresh challenges. To enhance IoT security and device resilience while safeguarding sensitive data, across the entire IoT supply chain, organizations must implement comprehensive security measures based on zero-tolerance principles.
Factors such as data security, device security, secure communication, confidentiality, privacy, and other non-functional requirements like maintainability, reliability, usability and scalability highlight the critical need for security controls within IoT devices. Security controls should include elements like secure communication, access controls, encryption, software patches, device hardening, etc. As part of the security process, the focus should be on industry standards, such as “secure by design” and “secure by default”, along with the average number of IoT attacks per organization, as broken down by region every week.
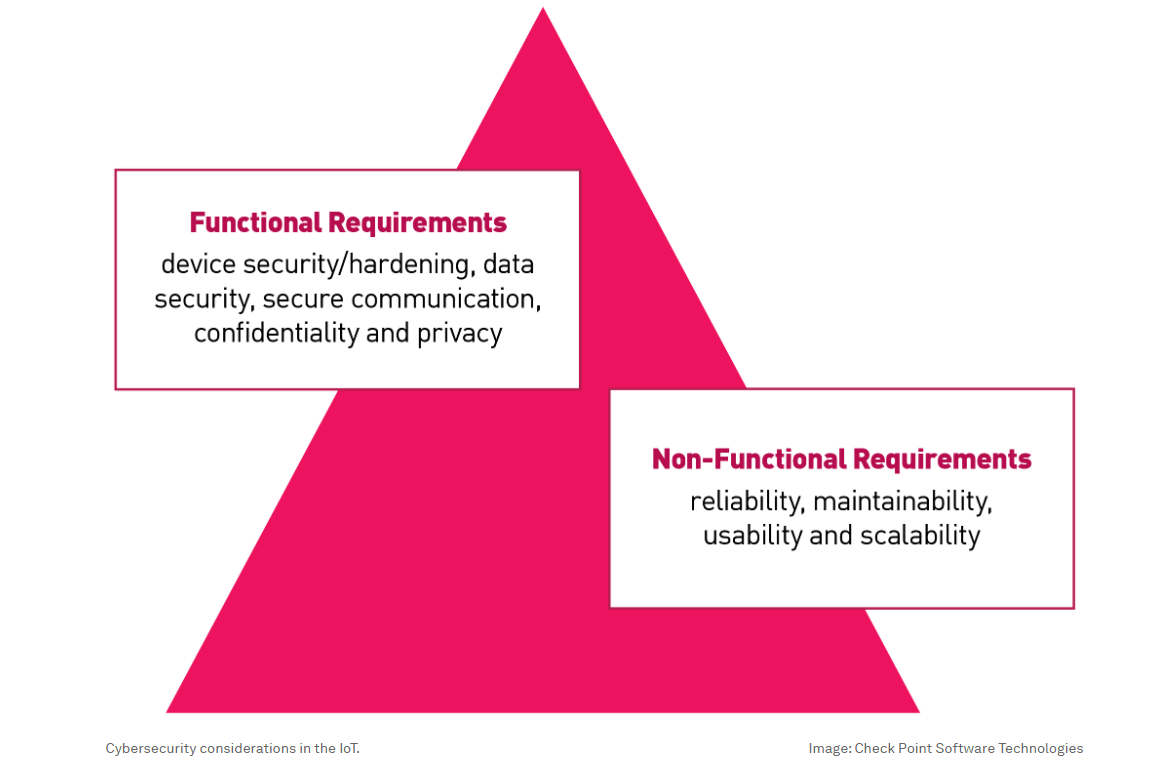
Collaborations and alliances within the industry are critical in developing standardized IoT security practices and establishing industry-wide security standards. By integrating dedicated IoT security, organizations can enhance their overall value proposition and ensure compliance with regulatory obligations.
In today’s cyber threat landscape, numerous geographic regions demand adherence to stringent security standards; both during product sales and while responding to Request for Information and Request for Proposal solicitations. IoT manufacturers with robust, ideally on-device security capabilities can showcase a distinct advantage, setting them apart from their competitors. Furthermore, incorporating dedicated IoT security controls enables seamless, scalable and efficient operations, reducing the need for emergency software updates.
IoT security plays a crucial role in enhancing the Overall Equipment Effectiveness (a measurement of manufacturing productivity, defined as availability x performance x quality), as well as facilitating early bug detection in IoT firmware before official release. Additionally, it demonstrates a solid commitment to prevention and security measures.
By prioritizing dedicated IoT security, we actively contribute to the establishment of secure and reliable IoT ecosystems, which serve to raise awareness, educate stakeholders, foster trust and cultivate long-term customer loyalty. Ultimately, they enhance credibility and reputation in the market. Ensuring IoT device security is essential in preventing IoT devices from falling into the hands of the dark web army.
This article was originally published via the World Economic Forum and has been reprinted with permission.
For more Cyber Talk insights from Antoinette Hodes, please click here. Lastly, to receive stellar cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
The post How the Internet of Things (IoT) became a dark web target – and what to do about it appeared first on CyberTalk.
Ransomware gang Hunters International says it’s shutting down
Bitsight buys dark web security specialist Cybersixgill for $115M
I visited the dark web, and all I got was…
The IRS is sending four investigators across the world to fight cybercrime
What is the Dark Web?

The dark web. The name raises all kinds of questions. What is the dark web, really? Where is it? Can anyone use it?
Answering these questions can help you stay safer online.
The story of the dark web is a complicated one. It’s a small and highly anonymous portion of the internet. As a result, it has a reputation for harboring criminal activity. We often mention the dark web in our blogs, typically when the conversation turns to identity theft, data breaches, and stolen personal info. Rightfully so. Plenty of cybercrime can be traced right back to the dark web.
Yet cybercriminals didn’t create the dark web. And they’re far from the only people who use it. News outlets like the BBC and the New York Times have a presence there, as does the U.S. Central Intelligence Agency (CIA). Journalists, activists, and everyday citizens use it as well, often to work around oppressive censorship. Even Facebook is there, providing people access to the social media site in regions where it’s blocked.
Anonymity reigns on the dark web. It was designed to work that way. With that, it’s home to a mixed bag of activity, legitimate and illicit alike. Yet that anonymity doesn’t stop us from putting a face onto the dark web — from understanding what it is, where it is, and what happens there.
That starts with a look at the internet and the two primary layers that make it up.
The layers of the internet: The surface web and the deep web
If you visualize the internet as an ocean, you’ll find it populated with websites and collections of data at all depths. Yet, the typical internet user only has access to the first few feet, a layer of the internet known as the surface web.
The sights you’ll see within the surface web will look familiar. It’s all the blogs, shops, social media sites, and so on that you visit regularly. And it’s easy to get to. You only need to fire up your browser and go. All the sites are public-facing. With a quick search, you can find them.
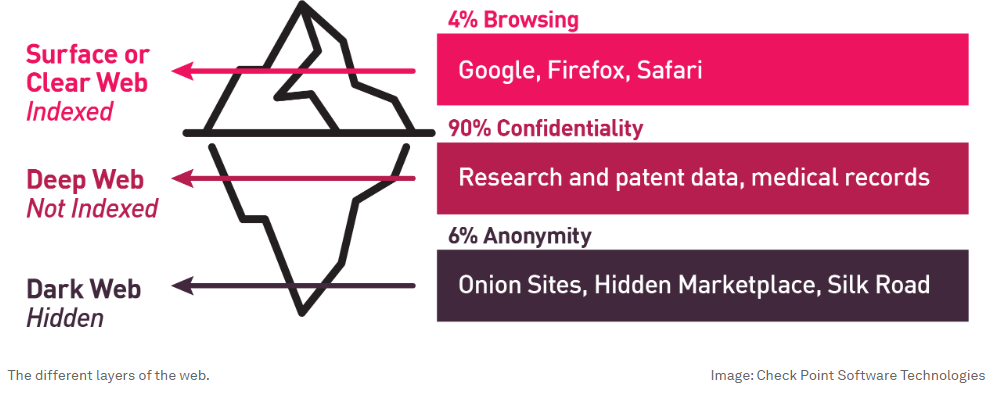
In all, the surface web contains any destination you can reach through search. To put it more precisely, the surface web accounts for areas of the internet that search engines can “crawl” and index for search. Estimates vary, yet the surface web accounts for roughly 4 to 5% of the internet.
Now, enter the deep web, the next 95% of the internet that is not searchable. Yet, that’s not to say that you don’t travel down into its depths from time to time. In fact, you likely do it daily. Any time you go through a paywall or use a password to access internet content, you’re entering the deep web. The content found there is hidden from search. Examples include logging into your bank account, accessing medical records through your healthcare provider, or using corporate web pages as part of your workday. Even streaming a show can involve a trip to the deep web. None of that content is searchable.
As such, the overwhelming majority of activity within the deep web is legitimate. So while this layer of the internet runs deep, it isn’t necessarily dark. The dark web is something altogether different.
What is the dark web?
The dark web lives within the deep web. Like the other depths of the deep web, it’s not searchable from the surface web. The people behind the sites and repositories on the dark web keep themselves anonymous. And the reasons vary. Some of them are entirely legitimate, others questionable, and several are outright illegal in nature.
Its origins go back to the 1990s when the U.S. Department of Defense developed the dark web as a means of sending anonymous and encrypted communications. That story might sound familiar. It’s quite like the origin story for the broader internet. That had its roots in the Department of Defense as well. So, just as the broader internet eventually became available to the public, so too did the dark web.
Getting there calls for a special browser because the protocols for the dark web differ from the surface web. Moreover, these browsers strip web traffic of identifiable info, encrypt it, and send it through a series of server jumps. The browsing traffic will appear to go through a server in one country, then a different server in another, and then another.
These steps make it highly difficult to identify the person using the browser. On the flip side, it also makes it difficult to identify the people hosting the sites and services on the dark web.
Without question, privacy is everything on the dark web. For good and for bad.
Legitimate uses of the dark web
While the notion of the dark web typically gets raised in the context of cybercrime and other illegal activity, it has legitimate uses. Some of these use cases include:
Circumventing censorship
Well-regarded news outlets such as the BBC and Pro Publica maintain a presence on the dark web to ensure that anyone can access their reporting. This includes people in nations and regions where certain news sources are censored.
Private communication
For the particularly privacy-conscious, the dark web hosts several resources for encrypted communication. That includes email clients, internet chat, and even social media sites.
Whistleblowing
Anonymous tips are a part of national security, law enforcement, and journalism as well. The private nature of the dark web confers an added degree of anonymity to tipsters.
The dark web isn’t a place everyday internet users will need, or even want, to go. It’s far more complicated than the surface web—and going in without taking several security measures can make the trip a risky one.
The dark web as a marketplace for cybercrime
This is where the rubber meets the road from an online protection standpoint. The dark web is also a marketplace for hackers and bad actors. In several ways — as a place to buy or rent malware, a repository for stolen info, and a place to communicate and coordinate attacks.
For starters, the dark web is populated with dark marketplaces. And difficult-to-trace cryptocurrency is the coin of the realm. With dark web stores stocked with ready-made malware kits, bad actors can launch attacks with little technical expertise. Others have done the work for them.
Cybercrime groups of all sizes prop up these shops, which they also use to rent out other services for attacks. For example, a small-time bad actor could easily lease a botnet to wage an attack that slows a targeted website to a crawl. Some cybercrime groups will provide hackers who can run attacks on someone else’s behalf, creating a mercenary “hacker for hire” gig economy.
Likewise, info stolen from a data breach can end up in dark web marketplaces as well. The personal info posted in these marketplaces can range anywhere from emails and passwords to in-depth info like tax ID numbers, health info, and driver’s license numbers.
Some of it goes up for sale. Some of it gets dumped there for free. With the right info in hand, cybercriminals can commit acts of identity theft. That includes claiming unemployment benefits and tax refunds in someone else’s name. In extreme cases, it can lead to bad actors outright impersonating their victims, racking up debts and criminal records along the way.
In all, if it’s hackable and has value, it’s likely for sale on the dark web.
Protect yourself from hackers and bad actors on the dark web
With all this shady activity on the dark web, you might wonder how you can protect yourself. In fact, you can take several steps to help prevent your info from finding its way there. And you also can take other steps if your info, unfortunately, ends up on the dark web.
Installing online protection software is the first step. Online protection software can help prevent many of the attacks that bad actors can buy on the dark web. It protects against ransomware, adware, spyware, and all manner of malware, whether it’s pre-existing or entirely new.
Yet today’s online protection goes far beyond antivirus. Comprehensive protection like ours protects your privacy and identity as well. It can keep tabs on your identity and credit, create strong passwords, and clean up your personal info online.
Monitor your identity:
An identity monitoring service can actively scan the dark web for personal info like your date of birth, email addresses, credit card numbers, personal identification numbers, and much more. In the event you fall victim to identity theft, our identity theft coverage and restoration can provide up to $1 million in coverage to cover the costs. Plus, it provides the services of a recovery expert with limited power of attorney to help you repair the damage done.
Keep an eye on your credit:
If you spot unusual or unfamiliar charges or transactions in your account, bank, or debit card statements, follow up at once. In general, banks, credit card companies, and many businesses have countermeasures to deal with fraud. Moreover, they have customer support teams that can help you file a claim if needed.
Given all the accounts you likely have a credit monitoring service can help. McAfee’s credit monitoring service can help you keep an eye on changes to your credit score, report, and accounts with prompt notifications and provide guidance so you can tackle identity theft.
Create strong, unique passwords:
With the high number of accounts you need to protect, creating strong, unique passwords for each one can get time consuming. Further, updating them regularly can become a time-consuming task. That’s where a password manager comes in.
A password manager does the work of creating strong, unique passwords for your accounts. These will take the form of a string of random numbers, letters, and characters. They will not be memorable, but the manager does the memorizing for you. You only need to remember a single password to access the tools of your manager.
Close old, risky accounts:
The more online accounts you keep, the greater the exposure you have to data breaches. Each account will have varying degrees of personal and financial info linked to it. And that means each one carries a varying degree of risk if it gets breached. Moreover, some sites and services protect data better than others, which adds another dimension of risk. Closing old and particularly risky accounts can decrease the risk of your personal and financial info winding up in the hands of an identity thief.
With security and savings in mind, McAfee created Online Account Cleanup. It finds and requests the deletion of unused accounts and protects your personal data from data breaches as a result. Monthly scans across your online accounts show a risk level for each account and help you decide which ones to delete.
Use two-factor authentication:
Two-factor authentication is an extra layer of defense on top of your username and password. It adds a one-time-use code to access your login procedure, typically sent to your smartphone by text or call. Together, that makes it tougher for a crook to hack your account if they get hold of your username and password. If any of your accounts support two-factor authentication, the few extra seconds it takes to set up is more than worth the big boost in protection you’ll get.
Protect yourself from cybercriminals on the dark web
The “dark” in the dark web stands for anonymity. And with anonymity, all kinds of activity follow. Good and bad.
From a security standpoint, the dark web is a haven for all manner of cybercriminals. Understanding how they use the dark web can help you protect yourself from their activities. You have tools for prevention, and you have resources available if your info ends up there or leads to identity theft.
By putting a face on the dark web, you put a face on cybercrime and can help reduce the risk of it happening to you.
The post What is the Dark Web? appeared first on McAfee Blog.
Russians Offered Ready-made Crypto Exchange Accounts Amid Restrictions
Russian crypto traders have been looking to obtain unrestricted accounts for global exchanges as their access to such platforms is limited. Over the past year, the offering of such accounts on the dark web has increased significantly, cybersecurity experts told the Russian press.
Supply of Crypto Exchange Accounts for Russian Users Doubles in a Year of Sanctions
More and more ready-to-use accounts for cryptocurrency exchanges are being sold to Russian residents. While this is not a new phenomenon — such accounts are often employed by fraudsters and money launderers — the current growth in supply has been attributed to the restrictions imposed by the trading platforms on customers from Russia, as a result of compliance with sanctions over the war in Ukraine.
Russian residents have been buying these accounts despite the dangers, including the risk that whoever created them could maintain access after the sale, the Kommersant reported. But they are inexpensive and offers on darknet markets have doubled since early 2022, Nikolay Chursin from the Positive Technologies information security threat analysis group told the business daily.
According to Peter Mareichev, an analyst at Kaspersky Digital Footprint Intelligence, the number of new ads for ready-made and verified wallets on various exchanges reached 400 in December. Proposals to prepare fake documents for passing know-your-customer procedures also rose, the newspaper revealed in an earlier article last month.
Simple login data, username and password, is typically priced at around $50, Chursin added. And for a fully set up account, including the documents with which it was registered, a buyer would have to pay an average of $300. Dmitry Bogachev from digital threat analysis firm Jet Infosystems explained that the price depends on factors such as the country and date of registration as well as the activity history. Older accounts are more expensive.
Sergey Mendeleev, CEO of defi banking platform Indefibank, pointed out that there are two categories of buyers — Russians that have no other choice as they need an account for everyday work and those who use these accounts for criminal purposes. Igor Sergienko, director of development at cybersecurity services provider RTK-Solar, is convinced that demand is largely due to crypto exchanges blocking Russian accounts or withdrawals to Russian bank cards in recent months.
Major crypto service providers, including leading digital asset exchanges, have complied with financial restrictions introduced by the West in response to Russia’s invasion of Ukraine. Last year, the world’s largest crypto trading platform, Binance, indicated that, while restricting sanctioned individuals and entities, it was not banning all Russians.
However, since the end of 2022, a number of Russian users of Binance have complained about having their accounts blocked without explanation, as reported by Forklog. Many experienced problems for weeks, including suspended withdrawals amid prolonged checks, affected customers said. The company told the crypto news outlet that the blocking of users from Eastern Europe and the Commonwealth of Independent States was related to the case with the seized crypto exchange Bitzlato.
Do you think the restrictions will push more Russians towards buying ready-made accounts for cryptocurrency exchanges? Share your thoughts on the subject in the comments section below.
Man arrested in France for laundering money of drug trafficker
A 29-year-old man suspected of laundering the proceeds of drug trafficking was arrested in Neufs (France).
According to the information provided, the defendant created a cryptocurrency mixer at the request of a drug dealer “Drugsource” who made a profit by selling drugs through the “dark web”. It is known that Drugsource has fulfilled more than 3000 orders worth more than USD 1.5 million during its operation.
The investigation into the drug trafficker’s activities began in early September 2020. Law enforcement agencies made a control purchase and were able to obtain the address of the trafficker’s wallet. After analyzing the blockchain, the police came across a 29-year-old man whose account had been used for 14 transactions by the drug dealer. The police were able to find and arrest the accused in September 2022.
The hearing in the case of the 29-year-old defendant was scheduled for January 2023. The defendant claimed responsibility for creating the bitcoin tumbler for Drugsource, but he denied any involvement in drug sales. The court nevertheless acquitted him of drug trafficking charges, but he was facing imprisonment for money laundering on a large scale.
USD 500,000 was confiscated from the offender’s cryptocurrency and bank accounts, and his apartment in Dubai was also seized. The defendant is awaiting sentencing in February 2023 on charges of money laundering obtained from the sale of drugs.
The Italian police have detained criminals who were supplying counterfeit money across Europe
Italian law enforcement agencies have detained a group of people who sold counterfeit money through a “DarkWeb”.
With the assistance of the Italian Public Prosecutor’s Office, eight criminals were detained in Naples who manufactured and distributed counterfeit euros across Europe. To sell their goods, the criminals used “DarkWeb” shops and sent counterfeit money by mail. In July 2018, an investigation was launched against a group of people accused of manufacturing and selling counterfeit banknotes worth more than 120 thousand euros. The counterfeiters had accomplices in many countries of the European Union, which greatly simplified their work.
The criminals acted according to a fairly simple scheme: they placed ads for the sale of counterfeit euros of various denominations on “DarkWeb” resources, and after receiving the order, they sent their invoice to pay for the goods in bitcoins. To deliver the parcels, they chose international mail, through which they sent toys and various vintage items with banknotes of different denominations hidden in them. During the investigation, European border guards intercepted about 50 packages in total. The total amount of money earned by the criminals in the period from 2012 to 2023 is almost 150 thousand euros. In addition to the counterfeiters, the police detained more than 30 buyers and identified fifty accomplices.
The investigation resulted in the arrest of a group of counterfeiters and the liquidation of their printing plant in Naples.
The cryptocurrency exchange that helped to “launder” dirty money from the Hydra marketplace has been closed
U.S. law enforcement agencies, with the help of international colleagues, have shut down the Chinese exchange Bitzlato Limited and arrested its entire top management.
Bitzlato Limited was established in 2016, and its founder is Anatoly Legkodymov, who is a citizen of the Russian Federation. From the first day of its operation, the exchange attracted a large number of people who were not entirely legitimate business, and this was facilitated by the company’s policy and lack of control over “dirty” money. First of all, the exchange attracted the attention of various criminals, and most of all it attracted the attention of users of “dark” Internet markets.
The investigation showed that most of the Bitzlato exchange users were also active users of Hydra Market. Customers and sellers from the Hydra resource immediately fell in love with the Chinese exchange because they did not have any questions about the legality of their finances when making illegal transactions through it. The blockchain analysis showed that in the period from May 2018 to April 2022, about $300 million was credited to Bitzlato accounts from Hydra users. Also, more than $200 million was sent to Hydra accounts from the exchange. Also, thanks to the analysis, it became known that almost $20 million was transferred to the exchange’s accounts from accounts that were used for ransomware crimes.
If you think that Bitzlato employees somehow fought against illegal transactions, you are mistaken. Exchange employees sometimes blocked users who were suspected of illegal activity, but in most cases they themselves deliberately helped to transfer money to Hydra accounts. The analysis of exchange users’ correspondence with the support service showed that the employees directly answered that funds from the exchange could be transferred to any address, regardless of the purpose of the transactions. The employees of the exchange were well aware that most of their customers used accounts registered under other names to make purchases on Hydra Market, and even knowing all the schemes of transferring funds, they did not react in any way.
The marketing director of the exchange prepared a report titled “Competitor Analysis” in which he pointed out that the rejection of illegal money transfers would hit the company’s finances, and he also highlighted the disadvantages of the exchange, which he attributed to “a large number of fraudsters among the users of the resource” and “a large amount of dirty money on the company’s accounts”.
Despite the fact that the exchange was not officially registered in the United States, it advertised its services among clients of the American market. As it later became known, about 1.5 thousand US clients transferred more than USD 2 million to Bitzlato’s account.
The founder of the exchange did not even worry about being held accountable for his activities. As of October 2022, he was living in Miami, from where he had unimpeded access to the exchange’s servers. It all ended on January 17, 2023, when US law enforcement agencies in partnership with several European countries arrested Legkodymov and confiscated all of his company’s cryptocurrency assets.