io9’s Favorite Replays, Rereads, and Rewatches of 2025

With picks as diverse as 'A Goofy Movie' and 'Turn A Gundam,' here are some shows, movies, and books we couldn't help but pick back up and experience.



Hello, aspiring digital forensics investigators!
Welcome back to our guide on memory analysis!
In the first part, we covered the fundamentals, including processes, dumps, DLLs, handles, and services, using Volatility as our primary tool. We created this series to give you more clarity and help you build confidence in handling memory analysis cases. Digital forensics is a fascinating area of cybersecurity and earning a certification in it can open many doors for you. Once you grasp the key concepts, you’ll find it easier to navigate the field. Ultimately, it all comes down to mastering a core set of commands, along with persistence and curiosity. Governments, companies, law enforcement and federal agencies are all in need of skilled professionals As cyberattacks become more frequent and sophisticated, often with the help of AI, opportunities for digital forensics analysts will only continue to grow.
Now, in part two, we’re building on that to explore more areas that help uncover hidden threats. We’ll look at network info to see connections, registry keys for system changes, files in memory, and some scans like malfind and Yara rules to find malware. Plus, as promised, there are bonuses at the end for quick ways to pull out extra details
As a beginner analyst, you’d run network commands to check for sneaky connections, like if malware is phoning home to hackers. For example, imagine investigating a company’s network after a data breach, these tools could reveal a hidden link to a foreign server stealing customer info, helping you trace the attacker.
‘Netscan‘ scans for all network artifacts, including TCP/UDP. ‘Netstat‘ lists active connections and sockets. In Vol 2, XP/2003-specific ones like ‘connscan‘ and ‘connections‘ focus on TCP, ‘sockscan‘ and ‘sockets‘ on sockets, but they’re old and not present in Vol 3.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> netscan
vol.py -f “/path/to/file” ‑‑profile <profile> netstat
XP/2003 SPECIFIC:
vol.py -f “/path/to/file” ‑‑profile <profile> connscan
vol.py -f “/path/to/file” ‑‑profile <profile> connections
vol.py -f “/path/to/file” ‑‑profile <profile> sockscan
vol.py -f “/path/to/file” ‑‑profile <profile> sockets
Volatility 3:
vol.py -f “/path/to/file” windows.netscan
vol.py -f “/path/to/file” windows.netstat
bash$ > vol -f Windows7.vmem windows.netscan

This output shows network connections with protocols, addresses, and PIDs. Perfect for spotting unusual traffic.
bash$ > vol -f Windows7.vmem windows.netstat

Here, you’ll get a list of active sockets and states, like listening or established links.
Note, the XP/2003 specific plugins are deprecated and therefore not available in Volatility 3, although are still common in the poorly financed government sector.
You’d use hive list commands to find registry hives in memory, which store system settings malware often tweaks these for persistence. Say you’re checking a home computer after suspicious pop-ups. This could show changes to startup keys that launch bad software every boot.
‘hivescan‘ scans for hive structures. ‘hivelist‘ lists them with virtual and physical addresses.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> hivescan
vol.py -f “/path/to/file” ‑‑profile <profile> hivelist
Volatility 3:
vol.py -f “/path/to/file” windows.registry.hivescan
vol.py -f “/path/to/file” windows.registry.hivelist
bash$ > vol -f Windows7.vmem windows.registry.hivelist

This lists the registry hives with their paths and offsets for further digging.
bash$ > vol -f Windows7.vmem windows.registry.hivescan

The scan output highlights hive locations in memory.
Printkey is handy for viewing specific registry keys and values, like checking for malware-added entries. For instance, in a ransomware case, you might look at keys that control file associations to see if they’ve been hijacked.
Without a key, it shows defaults, while -K or –key targets a certain path.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> printkey
vol.py -f “/path/to/file” ‑‑profile <profile> printkey -K “Software\Microsoft\Windows\CurrentVersion”
Volatility 3:
vol.py -f “/path/to/file” windows.registry.printkey
vol.py -f “/path/to/file” windows.registry.printkey ‑‑key “Software\Microsoft\Windows\CurrentVersion”
bash$ > vol -f Windows7.vmem windows.registry.printkey

This gives a broad view of registry keys.
bash$ > vol -f Windows7.vmem windows.registry.printkey –key “Software\Microsoft\Windows\CurrentVersion”

Here, it focuses on the specified key, showing subkeys and values.
Filescan helps list files cached in memory, even deleted ones, great for finding malware files that were run but erased from disk. This can uncover temporary files from the infection.
Both versions scan for file objects in memory pools.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> filescan
Volatility 3:
vol.py -f “/path/to/file” windows.filescan
bash$ > vol -f Windows7.vmem windows.filescan

This output lists file paths, offsets, and access types.
You’d dump files to extract them from memory for closer checks, like pulling a suspicious script. In a corporate espionage probe, dumping a hidden document could reveal leaked secrets.
Without options, it dumps all. With offsets or PID, it targets specific ones. Vol 3 uses virtual or physical addresses.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> dumpfiles ‑‑dump-dir=“/path/to/dir”
vol.py -f “/path/to/file” ‑‑profile <profile> dumpfiles ‑‑dump-dir=“/path/to/dir” -Q <offset>
vol.py -f “/path/to/file” ‑‑profile <profile> dumpfiles ‑‑dump-dir=“/path/to/dir” -p <PID>
Volatility 3:
vol.py -f “/path/to/file” -o “/path/to/dir” windows.dumpfiles
vol.py -f “/path/to/file” -o “/path/to/dir” windows.dumpfiles ‑‑virtaddr <offset>
vol.py -f “/path/to/file” -o “/path/to/dir” windows.dumpfiles ‑‑physaddr <offset>
bash$ > vol -f Windows7.vmem windows.dumpfiles

This pulls all cached files Windows has in RAM.
Malfind scans for injected code in processes, flagging potential malware.
Vol 2 shows basics like hexdump. Vol 3 adds more details like protection and disassembly.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> malfind
Volatility 3:
vol.py -f “/path/to/file” windows.malfind
bash$ > vol -f Windows7.vmem windows.malfind

This highlights suspicious memory regions with details.
Yara scan uses rules to hunt for malware patterns across memory. It’s like a custom detector. For example, during a widespread attack like WannaCry, a Yara rule could quickly find infected processes.
Vol 2 uses file path. Vol 3 allows inline rules, file, or kernel-wide scan.
Volatility 2:
vol.py -f “/path/to/file” yarascan -y “/path/to/file.yar”
Volatility 3:
vol.py -f “/path/to/file” windows.vadyarascan ‑‑yara-rules <string>
vol.py -f “/path/to/file” windows.vadyarascan ‑‑yara-file “/path/to/file.yar”
vol.py -f “/path/to/file” yarascan.yarascan ‑‑yara-file “/path/to/file.yar”
bash$ > vol -f Windows7.vmem windows.vadyarascan –yara-file yara_fules/Wannacrypt.yar

As you can see we found the malware and all related processes to it with the help of the rule
Using the strings command, you can quickly uncover additional useful details, such as IP addresses, email addresses, and remnants from PowerShell or command prompt activities.
bash$ > strings Windows7.vmem | grep -oE "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,4}\b"

bash$ > strings Windows7.vmem | grep -oE "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,4}\b"

bash$ > strings Windows7.vmem | grep -E "(cmd|powershell|bash)[^\s]+"

By now you should feel comfortable with all the network analysis, file dumps, hives and registries we had to go through. As you practice, your confidence will grow fast. The commands covered here will help you solve most of the cases as they are fundamental. Also, don’t forget that Volatility has a lot more different plugins that you may want to explore. Feel free to come back to this guide anytime you want. Part 1 will remind you how to approach a memory dump, while Part 2 has the commands you need. In this part, we’ve expanded your Volatility toolkit with network scans to track connections, registry tools to check settings, file commands to extract cached items, and miscellaneous scans like malfind for injections and Yara for pattern matching. Together they give you a solid set of steps.
If you want to turn this into a career, our digital forensics courses are built to get you there. Many students use this training to prepare for industry certifications and job interviews. Our focus is on the practical skills that hiring teams look for.
Anyone who spends time on Roblox can see how diverse and creative the platform is. If...
The post 100 Roblox Username Ideas in 2025 appeared first on Fossbytes.


If you’re a fan of the Blue Lock anime series like me, then Roblox’s Meta Lock...
The post Roblox Meta Lock Codes (November 2025) appeared first on Fossbytes.
Inspired by the ever-popular anime series Pokémon, Catch a Monstor is a Roblox adventure game where,...
The post Catch a Monster Codes (November 2025) appeared first on Fossbytes.
Horror games are different. They combine action and storytelling with a sense of dread that instantly...
The post 99 Nights in the Forest Codes (November 2025) appeared first on Fossbytes.
Find the best Black Friday weed deals of 2025. We found the best sales on cannabis products so you can see the top discounts in one place.
The post The best Black Friday weed deals of 2025 appeared first on Leafly.
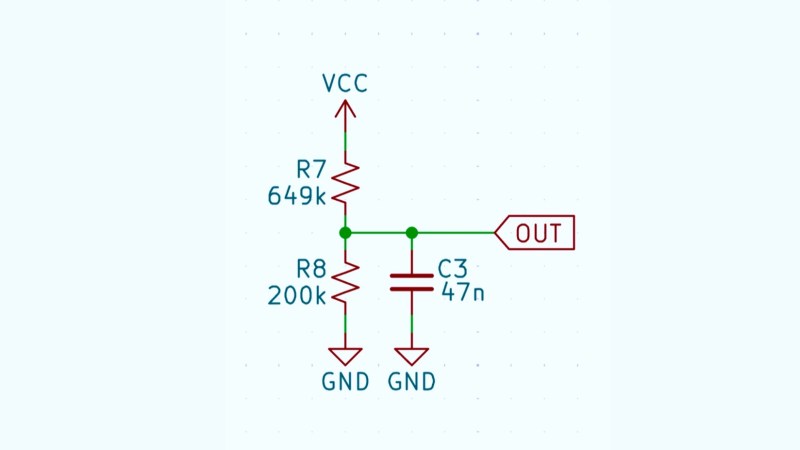
[Andrew Greenberg] has some specific ideas for how open-source hardware hackers could do a better job with their KiCad schematics.
In his work with students at Portland State University, [Andrew] finds his students both reading and creating KiCad schematics, and often these schematics leave a little to be desired.
To help improve the situation he’s compiling a checklist of things to be cognisant of when developing schematics in KiCad, particularly if those schematics are going to be read by others, as is the hope with open-source hardware projects.
In the video and in his checklist he runs us through some of the considerations, covering: visual design best practices; using schematic symbols rather than packages; nominating part values; specific types of circuit gotchas; Design for Test; Design for Fail; electric rule checks (ERC); manufacturer (MFR), part number (MPN), and datasheet annotations for Bill of Materials (BOM); and things to check at the end of a design iteration, including updating the date and version number.
(Side note: in the video he refers to the book The Visual Display of Quantitative Information which we have definitely added to our reading list.)
Have some best practices of your own you would like to see on the checklist? Feel free to add your suggestions!
If you’re interested in KiCad you might like to read about what’s new in version 9 and how to customize your KiCad shortcut keys for productivity.
Choosing the right laptop for work is not that easy. You need something fast, something reliable,...
The post The 5 Best Business Laptops Built for Work In 2025 appeared first on Fossbytes.
Over the last year, ChatGPT has become one of the most utilized tools for writing, research,...
The post 5 ChatGPT Tips You Should Stop Using Right Now appeared first on Fossbytes.
Inspired by the beloved Blue Lock anime series, Blue Lock Rivals is a soccer/football game in which players compete...
The post Blue Lock Rivals Codes (November 2025) appeared first on Fossbytes.

Memecoins have evolved far beyond viral internet jokes. What started as light-hearted experiments like Dogecoin or Shiba Inu has transformed into a serious market segment that commands billions in market capitalization. As of early 2025, the combined value of leading memecoins has surpassed $60 billion, reflecting a 400% increase from two years ago. This explosive growth isn’t just about speculation anymoreit’s about community culture, shared humor, and decentralized participation driving real digital economies. In this era, memecoins aren’t merely entertainment tokens; they represent community ownership, social engagement, and brand-driven creativity inside Web3.
2026 marks a golden window for launching your own custom memecoin. The infrastructure is more robust than everwith no-code token generators, instant DEX listings, and decentralized launchpads simplifying what once took months. On top of that, a new wave of investors and creators are seeking fun, story-driven tokens that also deliver transparency and long-term engagement. Whether you’re a developer, brand, or crypto enthusiast, this checklist walks you through everything you need from defining your concept and tokenomics to marketing, compliance, and sustainability to make your custom memecoin stand out in 2025’s booming crypto scene.
∘ Define Your Vision and Theme
∘ Pick the Right Blockchain and Tech Stack
∘ Design Strong Tokenomics
∘ Build Pre-Launch Hype and Community
∘ Execute a Seamless Launch
∘ Ensure Post-Launch Growth and Longevity
∘ Stay Compliant and Transparent
∘ Conclusion
Before you even touch a line of code or open a token generator, you need a clear vision. Every successful memecoin begins with a story that captures attention, humor, and emotion. Your concept is the soul of your coin, it’s what makes people care enough to buy, share, and meme it into existence. In 2025, with over 10,000 new tokens launched monthly, the ones that stand out have more than funny namesthey have a cultural spark that resonates with a loyal community. Launch your custom memecoin in 2025 with strategy, community, and long-term impact.
Choose a Memorable Concept
Your concept sets the tone for everything marketing, branding, and community engagement. Think about what makes people laugh, relate, or feel included. Whether it’s inspired by internet culture, a trending meme, or a parody of serious crypto projects, the idea should connect instantly. Pick something that feels alive in online spacesReddit threads, Twitter memes, or niche Discord servers. The goal? To build something people don’t just trade but talk about.
Establish Brand Identity
A strong brand identity turns your token from “just another coin” into a movement. Choose a catchy name and ticker that rolls off the tongue something that can go viral as a hashtag or meme caption. Design a simple yet iconic logo and choose colors that pop in feeds and profile pictures. You can even create a mascot or 3D character to represent your token’s personality. Visuals fuel viralityso make your design recognizable at a glance.
Set Purpose and Goals
Every memecoin needs a “why.” Is it purely for fun? A community challenge? A long-term ecosystem with staking or NFT tie-ins? Clarity here builds credibility. Outline short-term goals like your launch strategy, exchange listings, and initial community size and long-term goals such as partnerships, utilities, or DAO governance. Setting clear intentions helps prevent your project from being labeled another pump-and-dump and instead positions it as a sustainable, purpose-driven coin that can thrive in the 2025 crypto landscape.
Once you’ve nailed your concept, it’s time to bring your memecoin to life with the right technical foundation. The blockchain you choose will determine your coin’s transaction costs, scalability, and visibilityall of which directly impact community growth and adoption. In 2026, launching a token has never been easier, but choosing where and how to build it can make or break your project’s success. A solid tech stack ensures your memecoin runs smoothly, trades seamlessly, and stays secure even under heavy demand.
Choose Your Chain Wisely
Your blockchain is the home of your memecoin, so pick it like you’d pick a real estate location with growth, accessibility, and cost in mind. Each chain offers unique advantages:
Compare speed, gas efficiency, and ecosystem strength. For memecoins aiming for mass participation, transaction cost matters as much as the meme itself. If your holders spend more in gas than they do on the coin, your virality dies early. Pick a chain that matches your audience’s vibe Solana for fast movers, Ethereum for credibility, or BNB Chain for accessibility.
Smart Contract Setup
Your smart contract is the backbone of your memecoin. It defines supply, functions, and transparency. Whether you’re coding from scratch using Solidity or Rust, or using a no-code token generator, ensure your contract is auditable and tamper-proof. Security builds trustand in 2025’s cautious market, that’s everything.Here are key smart contract features worth adding:
A quick audit from a verified firm or open-source review on platforms like GitHub can enhance investor confidence before your launch. Remember trust is the new meme.
Wallets and Infrastructure
Before going live, set up a clean wallet infrastructure that separates development, marketing, and treasury operations. This prevents confusion and maintains fund transparency. Use one wallet strictly for deploying the contract, another for marketing and giveaways, and a secure, multi-signature wallet for treasury and liquidity reserves.Test everythingfrom token transfers to staking (if applicable)in a testnet environment before mainnet deployment. Simulate real trading conditions to catch bugs early. Also, make sure your holders have access to compatible wallets (like MetaMask, Phantom, or Trust Wallet) for seamless interaction. A flawless transaction experience on day one sets the tone for long-term adoption.
Tokenomics isn’t just about numbers, it’s about building trust, sustainability, and excitement around your memecoin. In 2025, investors have grown smarter. They don’t just buy for hype; they look for fair launches, transparent allocation, and clear value flow. Strong tokenomics gives your memecoin structure and purpose making it more than just a viral trend. It determines how your token circulates, who benefits, and how long your community stays engaged.

Define Supply and Allocation
Your supply strategy defines the DNA of your memecoin. Whether you go with a capped supply (like 1 billion tokens) or a hyper-deflationary model with burns, it should fit your project’s vibe. If scarcity drives your meme’s narrative, a limited supply makes sense. If your goal is accessibility and community reach, a larger supply can fuel more engagement. Now, let’s talk distribution because fairness fuels trust. Allocate your tokens wisely across categories such as:
The key is balance. Over-allocating to the team or marketing wallet can trigger skepticism. Make your token distribution public and verifiable that’s how you build credibility from day one.
Create Vesting and Locking Mechanisms
Nothing kills community confidence faster than sudden dumps from insiders. A smart vesting plan ensures that founders and early investors can’t cash out too soon. Typically, team tokens are locked for 6–12 months, then released gradually over time. This signals long-term commitment and shows you’re in it for the visionnot the quick gains.You should also lock liquidity for a fixed duration through trusted protocols. This prevents “rug-pull” fears and reassures traders that their investments are safe. Add multi-signature access for treasury funds to strengthen governance and transparency. In memecoin culture, trust is the real currency and vesting mechanisms are how you earn it.
Utility and Rewards
Even though memecoins thrive on humor, adding real utility can extend their lifespan. A coin that does something stands out from the flood of copycats. Think about what value your holders get besides price action:
To sustain long-term value, introduce token sinks mechanisms that reduce circulating supply, like burns, upgrade fees, or exclusive buy-ins. This keeps your token’s demand higher than supply, maintaining excitement and price stability.
Before your memecoin hits the blockchain, it needs to hit the internet. The pre-launch phase is where your token’s identity turns into a movementwhere memes, hype, and curiosity come together to create demand before trading even begins. In 2025, no memecoin succeeds without a strong online community. It’s not just about posting links; it’s about storytelling, excitement, and giving people a reason to belong. The bigger and more engaged your community is at launch, the faster your project takes off.
Create Your Digital Presence
Your digital presence is your coin’s first impressionmake it count. Start by launching an official website that’s clean, fast, and loaded with essential info: token details, roadmap, and whitepaper. Think of it as your coin’s digital home where potential investors and meme lovers can instantly grasp your project’s personality and vision.Next, set up social profiles across all major platformsX (Twitter), Telegram, and Discord are non-negotiable. Consistency is key: use the same name, logo, and tone everywhere. This makes your brand recognizable and builds trust. If possible, include a linktree or single hub that connects all your channels.And don’t forget your whitepaper or one-pagerkeep it short, clear, and visually appealing. You’re not pitching a DeFi protocol here; you’re inviting people into a culture. Use humor, energy, and clarity to make readers feel like they’re part of something viral before it even launches.
Community Engagement Strategy
The heart of every successful memecoin lies in its community. Building engagement means transforming followers into fansand fans into holders. Here’s how you make it happen:
The key is to make participation fun, not forced. Encourage users to share, react, and co-create content. A meme that spreads organically does more than paid ads ever could. By launch day, your followers shouldn’t just be waiting they should be rooting for your coin to moon.
Influencer and KOL Marketing
Let’s face it in 2026, influencers are the rocket fuel of memecoin launches. Partnering with credible Web3 creators, YouTubers, or meme accounts can multiply your visibility overnight. But here’s the catch: authenticity wins. Pick influencers who genuinely match your project’s humor, energy, and values.Work with KOLs (Key Opinion Leaders) to share your story through viral threads, memes, and short-form videos. Instead of traditional ads, focus on creative storytellinglike a meme evolution series, “how it started vs. how it’s going,” or parody posts about your coin.You can also organize cross-promotions with NFT projects or other tokens, tapping into existing audiences that align with your meme culture. The trick is to make your launch feel like an event everyone wants to talk aboutnot a paid campaign. When influencers and communities rally behind your coin organically, the hype becomes self-sustaining.
The moment of truthyour memecoin is ready to go live. This is where months of preparation meet the excitement of execution. A flawless launch isn’t just about flipping a switch; it’s about ensuring every piecefrom your contract to your communityruns like clockwork. A smooth, transparent, and exciting launch builds instant trust and helps your project stand out in a sea of new tokens hitting the blockchain daily. Let’s break down how to make your memecoin launch as seamless as it is viral.
Token Deployment
Deploying your token is your official entry into the blockchain world. Before you go live, double-check every detail in your smart contractfrom supply numbers to tax functionsbecause one overlooked line of code can create chaos later. Once verified, publish your contract on-chain through a trusted explorer like Etherscan, BscScan, or Solscan so users can view it transparently. Verification isn’t optional; it’s how you prove your project’s legitimacy. Next, add liquidity pools on your chosen DEX, whether it’s Uniswap, PancakeSwap, or Raydium. Liquidity ensures your holders can buy and sell without slippage nightmares. Consider locking part of that liquidity for a set period (like 6–12 months) to signal commitment and prevent rug-pull fears. The goal is simple: make it easy, safe, and seamless for anyone to trade your memecoin the second it launches.
Exchange Listing and Visibility
Once your token is live, it’s time to spread it across the crypto universe. Start by listing your memecoin on decentralized exchanges (DEXs) where users can trade freely. Later, aim for smaller centralized exchanges (CEXs) to boost exposurethese listings often bring credibility and higher liquidity.Right after launch, get your coin tracked on CoinMarketCap and CoinGecko. These platforms serve as discovery enginesappearing there instantly increases visibility among traders and analysts. Don’t forget your secret weapon: your community. Encourage holders to share their trades, post memes, and celebrate milestones across social platforms. Every tweet, meme, and post contributes to the viral loop that defines successful memecoins.
Initial Post-Launch Events
Your launch doesn’t end at deploymentit starts there. Keep momentum alive with a series of high-energy post-launch events that keep your community buzzing.
These activities keep your coin trending and your audience emotionally invested. Every small celebration from your first 1,000 holders to your first CEX listingis a marketing opportunity in itself.
Launching your memecoin is just the beginning the real game starts after the hype settles. Post-launch growth is about keeping the spark alive, turning early excitement into sustained engagement, and building an ecosystem that lasts. The memecoin landscape in 2025 is fast-paced and crowded, but the ones that thrive are those that continuously evolve, innovate, and nurture their community. Longevity doesn’t happen by luck it’s built through consistency, transparency, and smart expansion.

Keep the Community Active
Your community isn’t just your audience it’s your project’s heartbeat. Once your memecoin is live, the key is to keep that energy alive through constant engagement and transparent communication. Share updates regularly about development progress, new listings, partnerships, and roadmap milestones. A silent team quickly loses community trust, so stay vocal and authentic.
Interactive engagement also works wonders. Introduce polls, governance votes, and meme competitions to make holders feel involved in the project’s direction. People love having a voiceespecially in the memecoin world, where personality drives loyalty. Weekly contests, leaderboard shoutouts, or “Meme of the Week” events can keep your social channels buzzing. The more your holders feel like stakeholders, the longer they’ll stick around.
Expand Utility and Partnerships
To stay relevant beyond the hype cycle, your memecoin needs to evolve. Start by adding utility-based features like staking, yield rewards, or NFT integrations. For example, allow holders to stake their coins for rewards or unlock exclusive NFTs tied to your meme culture. This transforms your coin from a speculative asset into an interactive experience.
Strategic partnerships can also accelerate growth. Collaborate with dApps, DAOs, metaverse projects, or influencer collectives that align with your vision. A cross-brand meme drop or in-game token utility can drive waves of new users. In 2025’s interconnected Web3 landscape, alliances fuel credibility and utility. When your coin becomes part of a larger digital ecosystem, it turns into more than a memeit becomes a movement.
Monitor Performance
Growth without data is just guesswork. Keep an eye on your coin’s performance metricstrading volume, holder count, token distribution, and social sentiment. Tools like DEXTools, LunarCrush, or GeckoTerminal can give you real-time insights. Identify what’s working and what’s not. Did engagement dip after a certain campaign? Did trading spike after an influencer collaboration? Use those insights to fine-tune your strategy.
Listening to your community is equally important. Gather feedback through Discord polls or AMA sessions and act on it. This shows your team cares, which in turn builds loyalty. Remember, your project’s adaptability is its biggest strength. The memecoins that survive market cycles are the ones that listen, iterate, and keep evolving based on data and community trust.
As the crypto market matures, compliance and transparency have become non-negotiable even for memecoins. What once started as a joke now falls under serious regulatory attention, especially in 2025, when global frameworks like MiCA (EU), SEC (US), VARA (Dubai), and MAS (Singapore) are shaping how tokens operate. Staying compliant isn’t just about avoiding finesit’s about building long-term credibility. A transparent, well-regulated memecoin attracts genuine investors, earns media trust, and stands out in a market full of short-lived hype.
Legal and Regulatory Readiness
Before launching your custom memecoin, you need to understand how it fits into emerging crypto classification frameworks. Is it a utility token, a governance token, or could it be viewed as a security under certain jurisdictions? Getting this wrong can land you in regulatory hot water.
Work with legal advisors familiar with blockchain law to navigate compliance across different regions. Draft a clear token disclaimer that explicitly states your coin’s purpose, limitations, and lack of investment guarantees. Avoid promising profits or using misleading marketing language that implies guaranteed returns. Transparency builds investor trust and shields your project from potential lawsuits or enforcement actions.Being proactive here pays offas 2025 regulators crack down on unregistered tokens, compliant projects will be the ones that survive and thrive.
Security and Audits
Security is the backbone of credibility. Even the most viral memecoin can crash overnight if users suspect vulnerabilities or shady handling of funds. That’s why every project should undergo independent third-party audits from reputable firms. Publish your audit reports publicly to show you have nothing to hide.
Go a step further by implementing liquidity locks, ensuring that team members can’t drain liquidity pools post-launch. Use multi-signature wallets to manage treasury and admin privileges this adds an extra layer of accountability and reduces the risk of insider exploits.
In 2025’s crypto environment, security is more than technicalit’s psychological. A well-audited, fully transparent token contract signals that your project respects its investors and plays by the rules.
Ethical Responsibility
Memecoins thrive on hype, but ethics should guide how you build and promote your token. Be honest about your project’s intent and roadmap, even if it’s a humor-driven or experimental coin. Overpromising or using manipulative tactics might pump your price short-term, but it destroys trust long-term.
Protect your community from common pitfalls scams, fake airdrops, insider dumps, or deceptive influencer promotions. Establish clear communication guidelines for moderators and partners to keep messaging consistent and truthful. If your project ever makes mistakes (and every project does), own up to them quickly and transparently.
At the end of the day, memecoin culture is about fun, creativity, and community. By blending those values with ethical leadership and transparency, you can turn what started as a meme into a respected brand that lasts beyond the next hype cycle.
Launching a custom memecoin in 2025 is no longer just about humor or hype, it’s about building a cultural phenomenon with strategy, trust, and community at its core. From crafting a viral concept and solid tokenomics to ensuring compliance, security, and ongoing engagement, every step in your checklist plays a crucial role in shaping success. The projects that win this year will be the ones that blend creativity with credibilityfun with function. Whether your goal is to spark laughter, unite a community, or pioneer the next viral digital asset, a well-planned, transparent, and community-driven approach will turn your meme into a lasting movement in the evolving world of crypto.
The Ultimate Checklist for Launching Your Custom Memecoin in 2026 was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.
Welcome back, aspiring DFIR investigators!
If you’re diving into digital forensics, memory analysis is one of the most exciting and useful skills you can pick up. Essentially, you take a snapshot of what’s happening inside a computer’s brain right at that moment and analyze it. Unlike checking files on a hard drive, which shows what was saved before, memory tells you about live actions. Things like running programs or hidden threats that might disappear when the machine shuts down. This makes it super helpful for solving cyber incidents, especially when bad guys try to cover their tracks.
In this guide, we’re starting with the basics of memory analysis using a tool called Volatility. We’ll cover why it’s so important, how to get started, and some key commands to make you feel confident. This is part one, where we focus on the foundations and give instructions. Stick around for part two, where we’ll keep exploring Volatility and dive into network details, registry keys, files, and scans like malfind and Yara rules. Plus, if you make it through part two, there are some bonuses waiting to help you extract even more insights quickly.
Memory analysis captures stuff that disk forensics might miss. For example, after a cyber attack, malware could delete its own files or run without saving anything to the disk at all. That leaves you with nothing to find on the hard drive. But in memory, you can spot remnants like active connections or secret codes. Even law enforcement grabs memory dumps from suspects’ computers before powering them off. Once it’s off, the RAM clears out, and booting back up might be tricky if the hacker sets traps. Hackers often use tricks like USB drives that trigger wipes of sensitive data on shutdown, cleaning everything in seconds so authorities find nothing. We’re not diving into those tricks here, but they show why memory comes first in many investigations.
Lucky for us, Volatility makes working with these memory captures straightforward. It started evolving, and in 2019, Volatility 3 arrived with better syntax and easier to remember commands. We’ll look at both Volatility 2 and 3, sharing commands to get you comfortable. These should cover what most analysts need.
Below is some valuable data you can find in RAM for investigations:
1. Network connections
2. File handles and open files
3. Open registry keys
4. Running processes on the system
5. Loaded modules
6. Loaded device drivers
7. Command history and console sessions
8. Kernel data structures
9. User and credential information
10. Malware artifacts
11. System configuration
12. Process memory regions
Keep in mind, sometimes key data like encryption keys hides in memory. Memory forensics can pull this out, which might be a game-changer for a case.
In this section we will describe a structured method for conducting memory forensics, designed to support investigations of data in memory. It is based on the six-step process from SANS for analyzing memory.
Start by listing all processes that are currently running. Harmful programs can pretend to be normal ones, often using names that are very similar to trick people. To handle this:
1. List every active process.
2. Find out where each one comes from in the operating system.
3. Compare them to lists of known safe processes.
4. Note any differences or odd names that stand out.
After spotting processes that might be problematic, look closely at the related dynamic link libraries (DLLs) and resources they use. Bad software can hide by misusing DLLs. Key steps include:
1. Review the DLLs connected to the questionable process.
2. Look for any that are not approved or seem harmful.
3. Check for evidence of DLLs being inserted or taken over improperly.
A lot of malware needs to connect to the internet, such as to contact control servers or send out stolen information. To find these activities:
1. Check the open and closed network links stored in memory.
2. Record any outside IP addresses and related web domains.
3. Figure out what the connection is for and why it’s happening.
4. Confirm if the process is genuine.
5. See if it usually needs network access.
6. Track it back to the process that started it.
7. Judge if its actions make sense.
Skilled attackers may use methods like replacing a process’s code or working in hidden memory areas. To detect this:
1. Apply tools for memory analysis to spot unusual patterns or signs of these tactics.
2. Point out processes that use strange memory locations or act in unexpected ways.
Attackers often aim for long-term access and hiding. Rootkits bury themselves deep in the system, giving high-level control while staying out of sight. To address them:
1. Search for indicators of rootkit presence or major changes to the OS.
2. Spot any processes or drivers with extra privileges or hidden traits.
Once suspicious processes, drivers, or files are identified, pull them out for further study. This means:
1. Extract the questionable parts from memory.
2. Save them safely for detailed review with forensic software.

A widely recommended option for memory forensics is Volatility. This is a prominent open-source framework used in the field. Its main component is a Python script called Volatility, which relies on various plugins to carefully analyze memory dumps. Since it is built on Python, it can run on any system that supports Python.
Volatility’s modules, also known as plugins, are additional features that expand the framework’s capabilities. They help pull out particular details or carry out targeted examinations on memory files.
Here are some modules that are often used:
pslist: Shows the active processes.
cmdline: Reveals the command-line parameters for processes.
netscan: Checks for network links and available ports.
malfind: Looks for possible harmful code added to processes.
handles: Examines open resources.
svcscan: Displays services in Windows.
dlllist: Lists the dynamic-link libraries loaded in a process.
hivelist: Identifies registry hives stored in memory.
You can find documentation on Volatility here:
Volatility v2: https://github.com/volatilityfoundation/volatility/wiki/Command-Reference
Volatility v3: https://volatility3.readthedocs.io/en/latest/index.html
Installing Volatility 3 is quite easy and will require a separate virtual environment to keep things organized. Create it first before proceeding with the rest:
bash$ > python3 -m venv ~/venvs/vol3
bash$ > source ~/venvs/vol3
Now you are ready to install it:
bash$ > pip install volatility3

Since we are going to cover Yara rules in Part 2, we will need to install some dependencies:
bash$ > sudo apt install -y build-essential pkg-config libtool automake libpcre3-dev libjansson-dev libssl-dev libyara-dev python3-dev
bash$ > pip install yara-python pycryptodome

Yara rules are important and they help you automate half the analysis. There are hundreds of these rules available on Github, so you can download and use them each time you analyze the dump. While these rules can find a lot of things, there is always a chance that malware can fly under the radar, as attackers change tactics and rewrite payloads.
Now we are ready to work with Volatility 3.
Volatility comes with multiple plugins. To list all the available plugins do this:
bash$ > vol -h

Each of these plugins has a separate help menu with a description of what it does.
Imagine you’re an analyst investigating a hacked computer. You start with image information because it tells you basics like the OS version and architecture. This helps Volatility pick the right settings to read the memory dump correctly. Without it, your analysis could go wrong. For example, if a company got hit by ransomware, knowing the exact Windows version from the dump lets you spot if the malware targeted a specific weakness.
In Volatility 2, ‘imageinfo‘ scans for profiles, and ‘kdbgscan‘ digs deeper for kernel debug info if needed. Volatility 3’s ‘windows.info‘ combines this, showing 32/64-bit, OS versions, and kernel details all in one and it’s quicker.
bash$ > vol -f Windows.vmem windows.info

Here’s what the output looks like, showing key system details to guide your next steps.
As a beginner analyst, you’d run process commands to list what’s running on the system, like spotting a fake “explorer.exe” that might be malware stealing data. Say you’re checking a bank employee’s machine after a phishing attack, these commands can tell you if suspicious programs are active, and help you trace the breach.
‘pslist‘ shows active processes via kernel structures. ‘psscan‘ scans memory for hidden ones (good for rootkits). ‘pstree‘ displays parent-child relationships like a family tree. ‘psxview‘ in Vol 2 compares lists to find hidden processes.
Note that Volatility 2 wants you to specify the profile. You can find out the profile while gathering the image info.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> pslist
vol.py -f “/path/to/file” ‑‑profile <profile> psscan
vol.py -f “/path/to/file” ‑‑profile <profile> pstree
vol.py -f “/path/to/file” ‑‑profile <profile> psxview
Volatility 3:
vol.py -f “/path/to/file” windows.pslist
vol.py -f “/path/to/file” windows.psscan
vol.py -f “/path/to/file” windows.pstree
Now let’s see what we get:
bash$ > vol -f Windows7.vmem windows.pslist

This output lists processes with PIDs, names, and start times. Great for spotting outliers.
bash$ > vol -f Windows.vmem windows.psscan

Here, you’ll see a broader scan that might catch processes trying to hide.
bash$ > vol -f Windows7.vmem windows.pstree

This tree view helps trace how processes relate, like if a browser spawned something shady.
Displaying the entire process tree will look messy, so we recommend a more targeted approach with –pid
You’d use process dump when you spot a suspicious process and want to extract its executable for closer inspection, like with antivirus tools. For instance, if you’re analyzing a system after a data leak, dumping a weird process could reveal it is spyware sending info to hackers.
Vol 2’s ‘procdump‘ pulls the exe for a PID. Vol 3’s ‘dumpfiles‘ grabs the exe plus related DLLs, giving more context.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> procdump -p <PID> ‑‑dump-dir=“/path/to/dir”
Volatility 3:
vol.py -f “/path/to/file” -o “/path/to/dir” windows.dumpfiles ‑‑pid <PID>
We already have a process we are interested in:
bash$ > vol -f Windows.vmem windows.dumpfiles --pid 504

After the dump, check the output and analyze it further.
Memdump is key for pulling the full memory of a process, which might hold passwords or code snippets. Imagine investigating insider theft, dumping memory from an email app could show unsent drafts with stolen data.
Vol 2’s ‘memdump’ extracts raw memory for a PID. Vol 3’s ‘memmap’ with –dump maps and dumps regions, useful for detailed forensics.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> memdump -p <PID> ‑‑dump-dir=“/path/to/dir”
Volatility 3:
vol.py -f “/path/to/file” -o “/path/to/dir” windows.memmap ‑‑dump ‑‑pid <PID>
Let’s see the output for our process:
bash$ > vol -f Windows7.vmem windows.memmap --dump --pid 504

This shows the memory map and dumps files for deep dives.
Listing DLLs helps spot injected code, like malware hiding in legit processes. Unusual DLLs might point to infection.
Both versions list loaded DLLs for a PID, but Vol 3 is profile-free and faster.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> dlllist -p <PID>
Volatility 3:
vol.py -f “/path/to/file” windows.dlllist ‑‑pid <PID>
Let’s see the DLLs loaded in our memory dump:
bash$ > vol -f Windows7.vmem windows.dlllist --pid 504

Here you see all loaded DLLs of this process. You already know how to dump processes with their DLLs for a more thorough analysis.
Handles show what a process is accessing, like files or keys crucial for seeing if malware is tampering with system parts. In a ransomware case, handles might reveal encrypted files being held open or encryption keys used to encrypt data.
Both commands list handles for a PID. Similar outputs, but Vol 3 is streamlined.
Volatility 2:
vol.py -f “/path/to/file” ‑‑profile <profile> handles -p <PID>
Volatility 3:
vol.py -f “/path/to/file” windows.handles ‑‑pid <PID>
Let’s see the handles our process used:
bash$ > vol -f Windows.vmem windows.handles --pid 504

It gave us details, types and names for clues.
Services scan lists background programs, helping find persistent malware disguised as services. If you’re probing a server breach, this could uncover a backdoor service.
Use | more to page through long lists. Outputs are similar, showing service names and states.
Volatility 2:
vol -f “/path/to/file” ‑‑profile <profile> svcscan | more
Volatility 3:
vol -f “/path/to/file” windows.svcscan | more
Since this technique is often abused, a lot can be discovered here:
bash$ > vol -f Windows7.vmem windows.svcscan

Give it a closer look and spend enough time here. It’s good to familiarize yourself with native services and their locations
We’ve covered the essentials of memory analysis with Volatility, from why it’s vital to key commands for processes, dumps, DLLs, handles, and services. Apart from the commands, now you know how to approach memory forensics and what actions you should take. As we progress, more articles will be coming where we practice with different cases. We already have a memory dump of a machine that suffered a ransomware attack, which we analyzed with you recently. In part two, you will build on this knowledge by exploring network info, registry, files, and advanced scans like malfind and Yara rules. And for those who finish part two, some handy bonuses await to speed up your work even more. Stay tuned!
The post Digital Forensics: Volatility – Memory Analysis Guide, Part 1 first appeared on Hackers Arise.
Find the best kitchen picks of 2025 for people who love weed, food & weed food. Find reviews of cooking tools & decor picks.
The post The best kitchen picks for a cannabis friendly home 2025 appeared first on Leafly.
Wordle is the super fun game from the NYT, where you put your vocabulary to the...
The post Wordle Hints & Answer For Today: December 6 appeared first on Fossbytes.
Find the best grow tents of 2025. Leafly reviewed popular grow tents and chose the top picks for different size needs and budgets.
The post Leafly’s top 5 grow tents of 2025 appeared first on Leafly.
Being a tech journalist is a tough gig in 2025 since it means handling about fifteen...
The post After Trying 100s of PDF Editors, I’ve Finally Found The Best One appeared first on Fossbytes.
Snag the best weed products for halloween 2025 for a hazy spooky season. Costumes aren’t required, but they are encouraged.
The post The best weed products for Halloween 2025 appeared first on Leafly.
We underestimate just how beautiful ornamental grasses can be in the garden. They can be statement plants, the ... Read More
The post Growing Ornamental Grass Like a Pro: Unique Picks and Easy Care Tips appeared first on Garden Therapy.