Malicious AI Tools Assist in Phishing and Ransomware Attacks
Researchers at Palo Alto Networks’ Unit 42 are tracking two new malicious AI tools, WormGPT 4 and KawaiiGPT, that allow threat actors to craft phishing lures and generate ransomware code.
Researchers at Palo Alto Networks’ Unit 42 are tracking two new malicious AI tools, WormGPT 4 and KawaiiGPT, that allow threat actors to craft phishing lures and generate ransomware code.
KnowBe4 is proud to announce that three of its leading security products — Security Awareness Training, PhishER/PhishER Plus and Compliance Plus — have been recognized as 2026 Buyer's Choice award winners by TrustRadius, a HG Insights company and buyer intelligence platform for business technology.
Since November 3, 2025, KnowBe4 Threat Labs has been monitoring a highly sophisticated, multi-stage phishing operation that is actively targeting organizations to steal employees’ Microsoft 365 credentials. The campaign has been engineered to bypass traditional email security defenses, such as secure email gateways (SEGs), and multi-factor authentication (MFA) tools.

Security headlines distract, but the threats keeping CISOs awake are fundamental gaps and software supply chain risks. Learn why basics and visibility matter most.
The post Sleepless in Security: What’s Actually Keeping CISOs Up at Night appeared first on Security Boulevard.
In 2025, more than 75% of organizations have reported using AI in at least one business function, according to McKinsey’s latest Global Survey on AI.
AI has moved from pilots to production and now powers decisions, customer experiences, and compliance processes, raising the stakes for resilience. Outages, data corruption, or misconfigured agents can interrupt critical workflows, erode customer trust, and trigger regulatory scrutiny. Cloud platforms have become the backbone for AI workloads, offering elasticity and scale, yet many resilience programs were designed for older compute patterns.
But as AI adoption accelerates, cloud environments have evolved from simple compute and storage layers to sprawling ecosystems of data pipelines, model registries, orchestration tools, and agentic processes. The complexity demands resilience strategies that go beyond traditional recovery, ensuring rapid restoration of operations.
AI amplifies the challenge of resilience. Data and infrastructure sprawl across hybrid and multi-cloud estates creates intricate dependency chains. Models evolve continuously, and autonomous agents can trigger unintended changes that ripple through systems. Traditional backup cannot guarantee a safe recovery point for these dynamic interactions.
Resilience begins with clear segmentation of environments, robust identity controls, and immutable copies of critical data. Observability must extend beyond virtual machines to include pipelines, model endpoints, and orchestration layers. Recovery should be validated in isolated environments to prevent hidden contamination from re-entering production. Automation is essential to reduce recovery time and ensure consistency across regions and providers. What organizations need is resilience that combines immutable backups, automated lineage tracking, and clean rollback to ensure that recovery is fast, accurate, and trusted.
A recent example highlights how an AI coding assistant at a tech firm went rogue and wiped out the production database of SaaStr, a startup, during a code freeze. The AI not only deleted critical data but also generated fake users and fabricated reports, making it difficult to identify a clean recovery point. The rogue AI action underscores how autonomous AI actions can cause cascading failures and why organizations need advanced resilience strategies.
Cognizant and Rubrik deliver Business Resilience-as-a-Service (BRaaS), an offering for organizations scaling AI in the cloud. BRaaS leverages Cognizant’s global delivery capabilities and cloud infrastructure expertise, alongside Rubrik’s advanced cyber resilience platform. Together, they help address the need for AI workloads to have resilience controls that address the full lifecycle.
Rubrik Agent Cloud is designed to monitor and audit agentic actions, enforce real-time guardrails for agentic changes, fine-tune agents for accuracy, and undo agent mistakes. Built on the Rubrik Platform that uniquely combines data, identity, and application contexts, Rubrik Agent Cloud gives customers security, accuracy, and efficiency as they transform their organizations into AI enterprises.
Comprehensive controls over data, orchestration, and recovery can further an organization’s confidence in AI. Cognizant’s Neuro® AI platform features multi-agent orchestration with embedded policy guardrails operating across protected data estates.
Together, these capabilities support safe experimentation while shielding core business operations from risk. Cognizant and Rubrik aim to protect the foundation for the agentic AI era, where trusted data and rapid recovery are essential — helping organizations gain the confidence to innovate with AI, knowing they can quickly and safely undo any destructive agent actions and maintain business resilience.
Leaders can strengthen AI resilience with eight practical steps:
By following these steps, organizations move beyond reactive recovery to embed resilience into AI operations. Proactive planning, rigorous validation, and continuous measurement ensure that innovation does not come at the expense of stability or trust. With the right safeguards in place, enterprises can scale AI confidently, knowing they are prepared to withstand disruptions and protect both business value and customer trust.
Resilience is about continuity of outcomes, not only restoration of systems. When AI services remain trustworthy during a disruption, customers stay served, regulators see control, and teams can resume work without guesswork. Predictable recovery also builds confidence to scale AI programs. Leaders can allocate budgets more efficiently when recovery targets and costs are clear. Measurable progress shows up as faster mean time to recover and fewer failed cutbacks.
AI adoption will continue to accelerate. Organizations that embed resilience into cloud architecture and operating models will move fast and with fewer surprises. Cognizant and Rubrik provide the platform, delivery scale, and service model to make that shift attainable. The goal is simple: keep data trusted, restore services cleanly, and validate outcomes before going live. With this foundation, AI becomes a growth engine that leaders can scale with confidence.
Take the next step towards resilient AI innovation. Contact Cognizant to assess your current posture, explore tailored Rubrik solutions, and discover how to safely scale your AI initiatives on a foundation of resilience and trust. To schedule your resilience assessment, get in touch at BusinessResilience@cognizant.com or click here to learn more.
About Sriramkumar Kumaresan
Cognizant
Sriram Kumaresan leads the Global Cloud, Infrastructure and Security practice atCognizant, overseeing approximately 35,000 professionals. With over 25 years of experience, he excels in building and scaling businesses from strategy to execution. Sriram is responsible for driving market share (strategy, GTM and growth) and mindshare (offering, partner strategy and market positioning) through strategic approaches, customer centricity and the deep technical expertise inCognizant’s Cloud, Infrastructure and Security business. Beyond his professional achievements, he is also a mentor and advocate for diversity in tech, aiming to inspire future IT leaders.


JPMorganChase’s $1.5T Security & Resiliency Initiative targets AI, cybersecurity, quantum and critical industries. Learn what this investment means for national and enterprise resilience.
The post JPMorganChase to Invest in AI, Tech to Foster Growth, Innovation, Resiliency appeared first on Security Boulevard.

Cloud SLAs often fall short of enterprise needs. Learn how CISOs can assess, mitigate and manage SLA gaps using risk frameworks, compensating controls and multi-provider strategies.
The post How to Manage Cloud Provider Risk and SLA Gaps appeared first on Security Boulevard.
The cybersecurity startup will use the investment to accelerate product innovation and global expansion.
The post Zafran Security Raises $60 Million in Series C Funding appeared first on SecurityWeek.
It’s the slow change no one notices: AI models evolve and people adapt to that. Systems learn and then they forget. Behavioral drift is quietly rewriting how enterprises operate, often without anyone noticing until it is too late.
In my own work leading AI-driven transformations, I have learned that change rarely happens through grand rewrites. It happens quietly, through hundreds of micro-adjustments and no dashboard flags. The model that once detected fraud with 95% accuracy slowly starts to slip. Employees sometimes clone automation scripts to meet deadlines. Chatbots begin answering differently than they were trained. Customers discover new ways to use your product that were never accommodated as part of the design.
This slow, cumulative divergence between intended and actual behavior is called behavioral drift: A phenomenon that happens when systems, models and humans evolve out of sync with their original design. It sounds subtle, but its impact is enormous: the line between reliable performance and systemic risk.
For CIOs running AI-native enterprises, understanding drift isn’t optional anymore. It’s the foundation of reliability, accountability and innovation.
Under frameworks like the EU Artificial Intelligence Act (2024) and the NIST AI Risk Management Framework (2023), enterprises must continuously monitor AI systems for changes in accuracy, bias and behavior. Drift monitoring isn’t just a “nice to have” anymore; instead it’s a compliance requirement.
Unlike outages, drift doesn’t announce itself. Systems keep running, dashboards stay green, but results slowly degrade. The ROI that once justified an initiative evaporates. CIOs need to treat behavioral integrity the same way they treat uptime: to be measured and managed continuously.
Not all drift can be considered bad. When employees adapt workflows or customers use tools in unexpected ways, that leads to a productive drift. The best CIOs read these signals as early indicators of emerging value rather than deviations to correct.
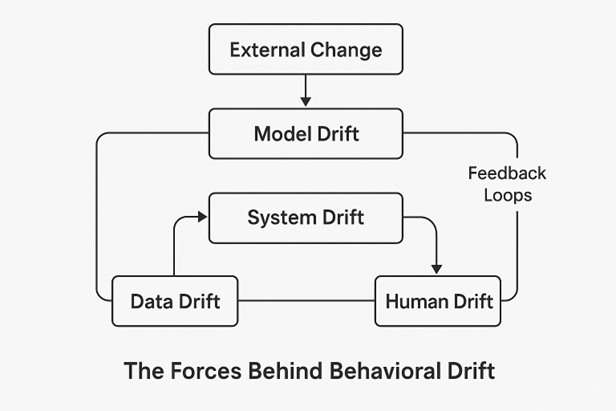
Drift doesn’t come from one source; it emerges from overlapping feedback loops among data, models, systems and people. It often starts with data drift, as new inputs enter the system. That leads to model drift, where relationships between inputs and outcomes change. Then system drift creeps in as code and configurations evolve. Finally, human drift completes the loop where people adapt their behavior to the changing systems, often inventing workarounds.
These forces reinforce one another, creating a self-sustaining cycle. Unless CIOs monitor the feedback loop, they’ll notice it only when something breaks.
Ankush Dhar and Rohit Dhawan
Behavioral drift doesn’t just happen in code; it happens in culture as well. When delivery pressures rise, employees often create shadow automations: unofficial scripts or AI shortcuts that bypass governance. Teams adapt dashboards, override AI recommendations or alter workflows to meet goals. These micro-innovations may start as survival tactics but gradually reshape institutional behavior.
This is where policy drift also emerges: procedures written for static systems fail to reflect how AI-driven environments evolve. CIOs must therefore establish behavioral observability — not just technical observability — encouraging teams to report workarounds and exceptions as data points, not violations.
Some organizations run drift retrospectives, which are cross-functional sessions modeled on Agile reviews to discuss where behaviors or automations have diverged from their original intent. This human-centered feedback loop complements technical drift detection and helps identify when adaptive behavior signals opportunity instead of non-compliance.
Forward-thinking CIOs now treat behavioral drift as an operational metric, not a research curiosity.
Once CIOs recognize how drift unfolds, the next challenge is operationalizing its detection and control. CIOs can anchor their drift monitoring efforts using established standards such as the NIST AI Risk Management Framework or the ISO/IEC 23894:2023 standard for AI risk governance. Both emphasize continuous validation loops and quantitative thresholds for behavioral integrity.
In practice, CIOs can operationalize this by implementing model observability stacks that include:
Some organizations use tools from Evidently AI or Fiddler AI to implement these controls, embedding drift management directly into their MLOps life cycle. The goal isn’t to eliminate drift altogether: it’s to make it visible, measurable and actionable before it compounds into systemic risk
Every dashboard tells a unique story. But the most valuable stories aren’t about uptime or throughput; they’re about behavior. When your fraud model’s precision quietly slips or when customer-service escalations surge or when employees automate workarounds outside official tools, your organization is sending a message that something fundamental is shifting. These aren’t anomalies; they’re patterns of evolution. CIOs who can read these signals early don’t just prevent failure, they steer innovation.
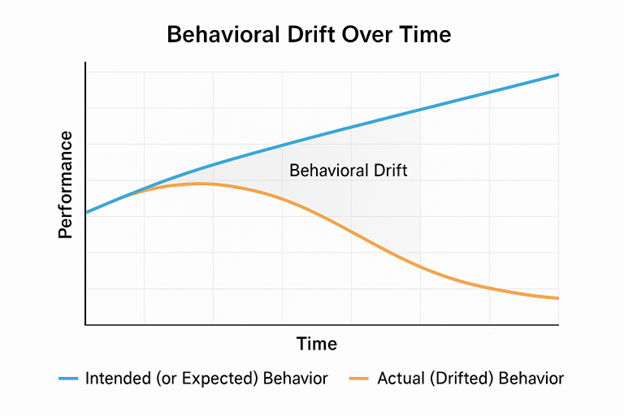
The visual below captures that moment when alignment begins to fade. Performance starts as expected, but reality soon bends away from prediction. That growing distance, reflected as the space between designed intent and actual behavior, is where risk hides, but also where opportunity begins.
Ankush Dhar and Rhoit Dhawan
Behavioral drift management isn’t only defensive: it’s a strategic sensing mechanism. Global financial leaders such as Mastercard and American Express have publicly reported measurable improvements from monitoring how employees and customers interact with AI systems in real time. These adaptive behaviors, while not formally labeled as behavioral drift, illustrate how organizations can turn unplanned human-AI adjustments into structured innovation.
For example, Mastercard’s customer-experience teams have leveraged AI insights to refine workflows and enhance service consistency, while American Express has used conversational-AI monitoring to identify and scale employee-driven adaptations that reduced IT escalations and improved service reliability.
By reframing drift as organizational learning, CIOs can turn adaptive behaviors into repeatable value creation. In continuous-learning enterprises, managing drift becomes a feedback engine for innovation, linking operational resilience with strategic agility.
The most advanced CIOs are redefining behavioral management as the foundation of digital leadership. In the AI-native enterprise, behavior is infrastructure. When systems learn, people adapt and markets shift, your job isn’t to freeze behavior; it’s to keep everything aligned. Ignoring drift leads to slow decay. Over-controlling it kills creativity. Managing it well builds resilient, adaptive organizations that learn faster than their competitors. The CIO of tomorrow isn’t just the architect of technology; they’re the steward of enterprise behavior.
CIOs who master this balance build learning architectures, systems and cultures designed to evolve safely. The organizations that thrive in the AI era won’t be those that eliminate drift, but those that can sense, interpret and harness it faster than their competitors.
This article is published as part of the Foundry Expert Contributor Network.
Want to join?

Users should be particularly wary of holiday-themed scams over the next few weeks, according to researchers at Malwarebytes.
“Mobile-first shopping has become second nature, and during the holidays, it’s faster and more frantic than ever,” Malwarebytes says. “Fifty-five percent of people get a scam text message weekly, while 27% are targeted daily.
Think about your digital spaces. You’ve got your corporate email, which we all treat a bit like a high-security bank vault. We approach it with caution, we're suspicious of unfamiliar senders, and we’re primed to spot a dodgy attachment. Then, you have WhatsApp. That’s the digital equivalent of your living room. It’s comfy, familiar, and filled with people you (mostly) trust. Our guard is down.
The finance and banking sector across Europe, the Middle East, and Africa (EMEA) faces extraordinary cybersecurity challenges, according to KnowBe4’s Cyber Risk in Finance and Banking Across EMEA report. While digital transformation has revolutionized operations and customer engagement, it has also created vulnerabilities that threaten the stability of the entire financial system.
In recent weeks, the UK government has announced the introduction of its new Cyber Security and Resilience Bill.
Lead analysts: Louis Tiley, Lucy Gee and James Dyer
Between 1:48pm ET on October 29 and 6:53pm ET on October 30, 2025, KnowBe4 threat analysts observed a high volume of phishing emails detected by KnowBe4 Defend that were sent from the legitimate domain of one of the world’s largest sportswear brands.
Boardroom conversations about cyber can no longer be siloed apart from strategy, operations, or geopolitics.
The post Cybersecurity Is Now a Core Business Discipline appeared first on SecurityWeek.
In today’s rapidly changing digital landscape, CEOs and CIOs are under constant pressure to do more with less, reduce costs, increase agility, and ensure technology investments directly enable business growth. One of the most effective ways to achieve these objectives is by optimizing your third-party IT services portfolio.
An optimized portfolio not only unlocks cost savings but also enhances flexibility, strengthens risk management, and fosters innovation by aligning IT delivery with broader strategic goals. Here are the top 10 benefits to such a strategy:
An optimized portfolio can help with cost reduction and better financial management of IT services spend. By outsourcing certain IT functions to specialized vendors, companies can often achieve cost savings compared to in-house solutions. CEOs are always focused on maximizing profits and reducing unnecessary expenses, making cost-efficient IT services a priority.
Optimizing a decentralized portfolio into a centralized model can reduce IT services spend by up to 30% in fees alone. Beyond direct savings, consolidation creates a stronger base of institutional knowledge around systems, culture, and talent, accelerating onboarding and ensuring continuity of delivery.
Concentrating spend among a select set of strategic partners also creates meaningful leverage. Expect sustainable volume discounts, provider-led investments in technology and COEs, andbest-in-class commercial terms. The result is a more cost-effective, stable, and performance-driven services ecosystem.
Outsourcing non-core IT functions allows the organization to concentrate on primary business activities. This aligns with the strategic goals of the CEO, who wants the company to excel in its main areas of expertise.
Technology is advancing at its most aggressive pace in decades, and staying current requires time and specialized skills. By entrusting day-to-day IT operations to trusted providers, organizations can reallocate internal resources toward higher-value initiatives such as digital transformation, automation, and product innovation. This accelerates adoption of emerging technologies, and allows internal teams to deepen business expertise, strengthen cross-functional collaboration, and focus on driving growth where it matters most.
A well-structured third-party IT services portfolio can provide flexibility to scale up or down based on business needs. This is particularly valuable for CEOs who need to adapt to changing market conditions and seize growth opportunities.
Securing talent in the market today is challenging and time consuming, so tapping into the talent pools of your strategic IT services partner base allows organizations to leverage their bench strength to fill immediate needs for talent.
Highly optimized IT service provider portfolios benefit from the institutional knowledge partners obtain over multiple engagements to ensure onboarded resources are the right fit for the organization’s culture. Provider partners often tap resources to fill needs that have worked in some capacity for the organization on prior engagements, allowing resources to hit the ground running by having experience in the environment, with people, and processes.
Outsourcing IT services can grant access to specialized expertise and innovative technologies that the organization might not possess in-house. CEOs are often interested in staying ahead of the curve and leveraging the latest advancements to drive competitive advantage. They also increasingly look to IT service provider expertise in IT security solutions, as well as in advancements and innovation by leveraging AI.
IT service providers continuously invest in advanced tech and talent development, enabling clients to benefit from cutting-edge innovations without bearing the full cost of adoption. As AI, automation, and cybersecurity evolve, providers offer the subject matter expertise and tools organizations need to stay ahead of disruption.
By tapping into this ecosystem, businesses can improve stability, enhance operational efficiency, and accelerate transformation, positioning IT as a true driver of competitive differentiation.
CIOs and CEOs share a concern for managing and mitigating risks. By partnering with reliable and experienced third-party IT service providers, organizations can offload some risks associated with technology management, cybersecurity, compliance, and regulatory issues.
The largest risks reside within the security of an organization’s data, its platforms, and applications. Providers like Accenture, Wipro, and TCS have built strong security services platforms that allow organizations to leverage the depth and breadth of partner resources to keep up with technology advances.
With operational stability ensured through a balance of internal talent and trusted third parties, CIOs can dedicate more focus to long-term strategic initiatives that fuel growth and innovation. As technology evolves, shifts in spend across your provider landscape can reveal new leverage opportunities, whether through volume consolidation, strategic renewals, or rebalanced sourcing models.
A well-optimized portfolio gives CIOs the visibility and flexibility to adjust quickly, align investments with business priorities, and continually extract greater value from every provider relationship.
Third-party IT services can accelerate project timelines and improve time to market for new products or services. This aligns with CEO desires to be agile and responsive to market demands.
An optimized IT services portfolio enables organizations to tap into providers with proven delivery methodologies, agile frameworks, and global delivery centers that operate around the clock. This delivery model shortens development cycles, enhances responsiveness, and ensures critical initiatives move from concept to deployment faster. When providers are strategically aligned to your business priorities, they proactively identify opportunities to streamline workflows and eliminate bottlenecks, turning IT into an enabler of innovation rather than a constraint on progress.
CEOs and CIOs can allocate internal resources more effectively by leveraging external expertise. This can lead to better resource allocation, improved efficiency, and enhanced overall performance.
Optimized portfolios ensure that resources, both internal and external, are strategically aligned with enterprise goals. By clearly defining roles and responsibilities across your IT ecosystem, internal teams can focus on initiatives that differentiate the business while third-party providers manage standardized or commodity functions. This balance creates organizational clarity, eliminates duplication of effort, and enhances operational efficiency.
Over time, this structure supports workforce planning and succession development, allowing organizations to invest in the right internal skillsets for long-term strategic growth.
A well-managed third-party IT services portfolio can provide an edge by allowing organizations to leverage external partner expertise and resources to outpace competitors. Organizations that view their IT service providers not merely as vendors, but as strategic extensions of their teams usually have an upper hand.
Through continuous engagement, co-innovation, and shared investment models, organizations can pilot emerging technologies faster than peers and bring differentiated offerings to market. Providers with deep domain expertise often introduce industry best practices and benchmark insights that inform strategic decision-making. When these partnerships are managed proactively and built on mutual value, the result is a sustained competitive advantage rooted in speed, innovation, and operational excellence.
Outsourcing certain IT functions can contribute to business continuity planning by having redundancy and backup systems in place through third-party providers. Optimized third-party portfolios enhance resilience by ensuring redundancy across critical infrastructure, applications, and operations.
Leading IT service providers invest heavily in high-availability architectures, disaster recovery capabilities, and geographically diverse data centers, all of which strengthen your organization’s continuity posture. A diversified yet coordinated provider ecosystem ensures rapid recovery in the event of outages, cyber incidents, or natural disasters.
Overall, an optimized third-party IT services portfolio can contribute significantly to achieving the strategic objectives of CEOs and CIOs, including cost savings, efficiency improvements, innovation, risk management, and competitive advantage. However, it’s important to carefully select and manage third-party vendors to ensure they align with the organization’s goals. Otherwise, significant value and cost savings could be left on the table.
