Does Carbon Fiber PLA Make Sense?
Carbon fiber (CF) has attained somewhat of a near-mystical appeal in consumer marketing, with it being praised for being stronger than steel while simultaneously being extremely lightweight. This mostly refers to weaved fibers combined with resin into a composite material that is used for everything from car bodies to bike frames. This CF look is so sexy that the typical carbon-fiber composite weave pattern and coloring have been added to products as a purely cosmetic accent.
More recently, chopped carbon fiber (CCF) has been added to the thermoplastics we extrude from our 3D printers. Despite lacking clear evidence of this providing material improvements, the same kind of mysticism persists here as well. Even as evidence emerges of poor integration of these chopped fibers into the thermoplastic matrix, the marketing claims continue unabated.
As with most things, there’s a right way and a wrong way to do it. A recent paper by Sameh Dabees et al. in Composites for example covered the CF surface modifications required for thermoplastic integration with CF.
Carbon Fibers
There are a number of ways to produce CF, often using polyacrylonitrile, rayon, or pitch as the feedstock. After spinning this precursor into a suitable filament, heating induces carbonization and produces the carbon fiber.
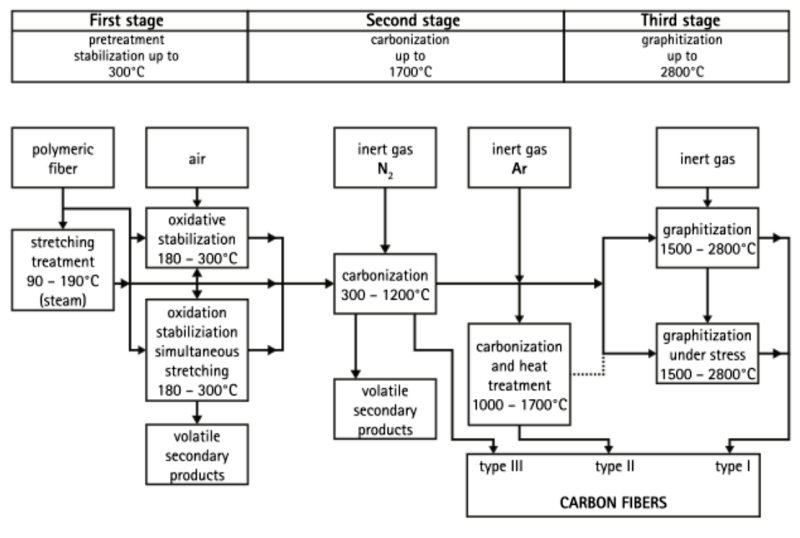
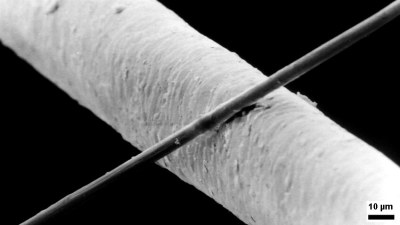
Following this process, the CF is typically in the form of a few micrometer-thick fiber that is essentially pure carbon. To create a structural interface between the CF and the polymer of a composite material, some kind of process has to take place that creates this interface.
The fundamental difference between thermoset and thermoplastic polymers is that thermoset polymers are reacting in the mold as it sets, providing an environment in which the epoxy precursor and hardener can interact with the normally not chemically very reactive CF to form covalent bonds.
In comparison, thermoplastic polymers are already finalized, with covalent bonds between thermoplastics and CF unlikely. This means that the focus with CF-reinforced thermoplastics is mostly on weaker, non-covalent interactions, such as Van der Waals forces, pi-interactions and hydrogen bonds. Each of these interactions is further dependent on whether the thermoplastic is compatible, such as the presence of aromatic rings for pi-interactions.
Making It Stick
With those challenges in mind, how can thermoplastics be coaxed into forming a significant interface with CF? As noted in the earlier cited work by Sameh Dabees et al., there is no single surface treatment for CF that would work for every thermoplastic polymer, as a logical result of the limitations imposed by the available non-covalent interactions.
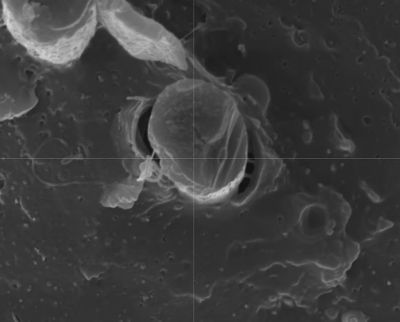
One way to prepare the CF is by apply a coating to the fiber, called a sizing. By applying a sizing to the fiber that is compatible with the target thermoplastic, the interface with the bulk material is expected to improve. In one cited study involving a polyamide-acid sizing for polyimide bulk material, this coating created an approximately 85 nm interface, with an interfacial shear strength increased by 32.3%. In another study targeting CF-PEEK, this had a polyimide-based, water-soluble sizing applied that also significantly improved the shear strength.
Of course, this sizing has to actually adhere to the CF, lest it simply vanishes into the bulk thermoplastic material. This is a problem that is easily observable in FDM-printed thermoplastic polymers as distinct voids around the CF where the bulk polymer pulled away during crystallization, and no interface formed. Obviously, these voids create a weak point instead of strengthening the material.
Fiber Modding
Although CF is often confused with carbon nanotubes, it does not have the rigidly ordered structure that they do. Instead it has a graphite structure, owing to the way that they are produced, meaning sheets of graphite placed together in a disordered fashion. Despite this, the external surface is still smooth, which is where the chemical inertness comes from. Combined with the lack of reactivity from the side of thermoplastics, this highlights the need for something to bridge the gap.
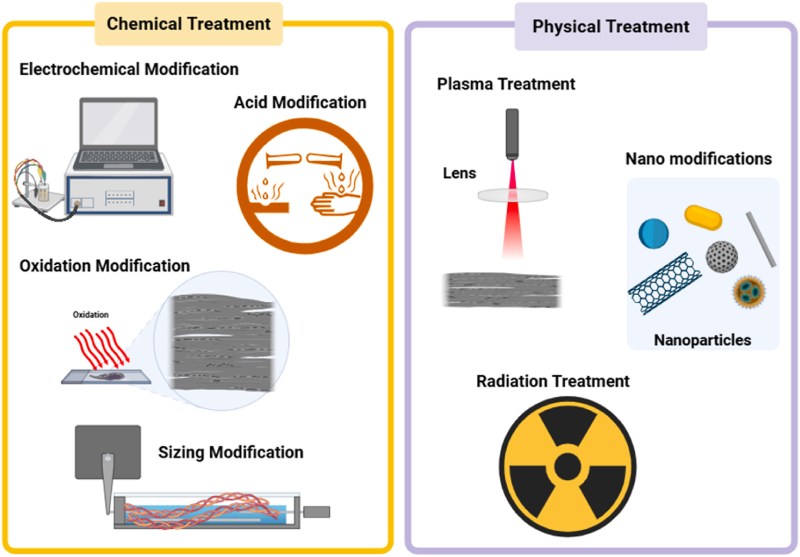
The review paper by Dabees et al. covers the most common types of surface treatments, with the above graphic providing a summary of the methods. Perhaps one of the most straightforward methods is the coating of the CF with an epoxy, thus shifting the interface from CF-thermoplastic to thermoset-thermoplastic. This kind of hybrid approach shows promising results, but is also cumbersome and not a universal fix.
Note that virtually all research here is focused on thermoplastic polymers like polycarbonate and PEEK, as these are most commonly used in industrial and medical settings. Yet even within that more limited scope the understanding of the exact effects of these modifications remains poorly investigated. Much of this is due to how hard it is to characterize the effects of one treatment when you take all other variables into account.
Perhaps most frustrating of all is how hard it is to research this topic considering the scale of the CF surface and the miniscule thickness of the CF-polymer interface. Relying on purely mechanical tests to quantify the impact is then tempting, but ultimately leaves us without a real understanding of why one method seems to work better than another.
Vibes Vs Science
The overall conclusion that we draw from this particular review paper is that although we know that composite materials can often provide improvements, in the case of thermoplastic-CF composites we realize that our understanding of the fundamentals is still rather lacking.
Outside of the less mainstream world of industrial and medical settings, CF is now widely being added to thermoplastic polymers, primarily in the form of filaments for FDM 3D printers. Without detailed information on whether the manufacturers of these filaments perform any kind of CF surface modification, it is very hard to even compare different CF-polymer filaments like this, even before taking into account individual FDM printer configurations and testing scenarios.
Considering that CF has for a few years now been identified as a potential carcinogen akin to asbestos, this raises the question of whether we really want to put CF and particularly the very small chopped carbon fibers into everything around us and thermoplastics in particular. When the empirical evidence available to us today shows that any mechanical improvements are not due to a solid CF-polymer interface, and any potential carcinogenic risks still years into the future of becoming clear, then the logical choice would be to hold back on CF-thermoplastics until we gain a better understanding of the benefits and risks.



 As detailed by [Ali Clarkson], one method involves creating loops out of bike spokes, with a custom jig and some brazing. Then a length of rope is passed through the hub and a special hitch is used to keep it in place. Two loops are made in the ends of this length of rope and passed through the spoke ends made earlier. Finally everything is brought up to tension and trued much like a normal wheelset. The front wheel ended up weighing around 700g, a rather impressive feat for a 24 inch downhill wheel.
As detailed by [Ali Clarkson], one method involves creating loops out of bike spokes, with a custom jig and some brazing. Then a length of rope is passed through the hub and a special hitch is used to keep it in place. Two loops are made in the ends of this length of rope and passed through the spoke ends made earlier. Finally everything is brought up to tension and trued much like a normal wheelset. The front wheel ended up weighing around 700g, a rather impressive feat for a 24 inch downhill wheel.







![[nanofix] and his assortment of tweezers](https://hackaday.com/wp-content/uploads/2026/01/nanofix-tweezers-banner.jpg?w=800)